Last updated on January 7, 2026
Two-factor authentication (2FA) is a security mechanism that requires two different forms of identity verification. This makes it significantly more difficult for unauthorized individuals to gain access to a user’s account. 2FA is a “two-step verification,” verifying that you really are who you claim to be.
- Why 2FA Matters (Key Benefits)
- What is 2FA? Definition and Differences from MFA
- One more example – 2FA and MFA explained visually
- Why Use 2FA? Research-Based Summary
- Barriers to 2FA Adoption (SMBs)
- How 2FA Works
- How to enable 2FA? Step by step
- Advantages and Disadvantages of Two-Factor Authentication (2FA)
- Regulations and Compliance Standards – Why 2FA is Now a Requirement
- FAQ – Frequently Asked Questions
Why 2FA Matters (Key Benefits)
- Security Above All: Using 2FA blocks the vast majority of account compromise attempts, even if a password is stolen or guessed.
- Effectiveness confirmed by research: The American federal agency CISA emphasizes that the use of MFA (including 2FA) reduces the risk of hacking by as much as 99%.
- Second Line of Defense: Attackers must compromise or possess both factors to gain access.
- Regulatory Compliance: Regulations and security standards in the U.S. and EU are pushing for strong authentication (often via 2FA) as a requirement to protect sensitive data.
What is 2FA? Definition and Differences from MFA
2FA Explained
Two-factor authentication (2FA) is a method of securing access to accounts and resources by requiring exactly two different forms of identity confirmation, or two “factors of authentication.”
In addition to a password (something you know), the user must confirm their identity with a second element: for example, a code from an app, a hardware key, or biometrics (something you have or are). This solution significantly increases security because even if the password is stolen, access remains protected. This makes access much more difficult for an unauthorized person, even if the password is stolen.
What is two-factor verification (2FA verification, two-step login, two-step authentication, two-step verification)?
Two-factor verification—also known as 2FA verification, two-step login, two-step authentication, two-step verification—is synonymous with 2FA. The terms are often used interchangeably to refer to the same process. However, not all two-step authentication is technically two-factor authentication.
Two-factor authentication (2FA) is also known as:
- Two‑factor verification
- Two‑step verification
- Two‑step login
- Dual‑factor authentication
- Two‑level authentication
All these names mean the same mechanism – the need to use two independent factors when logging in.
How 2FA Differs From MFA
- 2FA always involves exactly two authentication factors, for example, a password + a one-time code.
- Multi-factor authentication (MFA) is a broader term that refers to authentication requiring two or more factors. In practice, this means that all 2FA is a form of MFA, but not all MFA is 2FA.
For example:
- 2FA: password + code from SMS
- 2FA: password + code from the Rublon Authenticator app.
- MFA and 3FA (but not 2FA): password + hardware
When to Use 2FA and When to Move on to 3FA?
- Two-factor verification provides robust protection and is quick to implement, often sufficient for the security of corporate employees and personal users in social media and non-critical applications.
- Three-factor authentication (3FA) is best used in environments where security must be at its highest, such as public institutions, medical systems, or companies processing sensitive data. In these cases, adding an extra factor (e.g., biometrics) significantly increases the level of protection.
See 2FA in Action – Push Authentication Demo
The video below demonstrates the 2FA process using push login. It’s a classic, fast, intuitive, and secure type of two-factor authentication (2FA). Mobile notifications are a prime example of modern 2FA:
One more example – 2FA and MFA explained visually
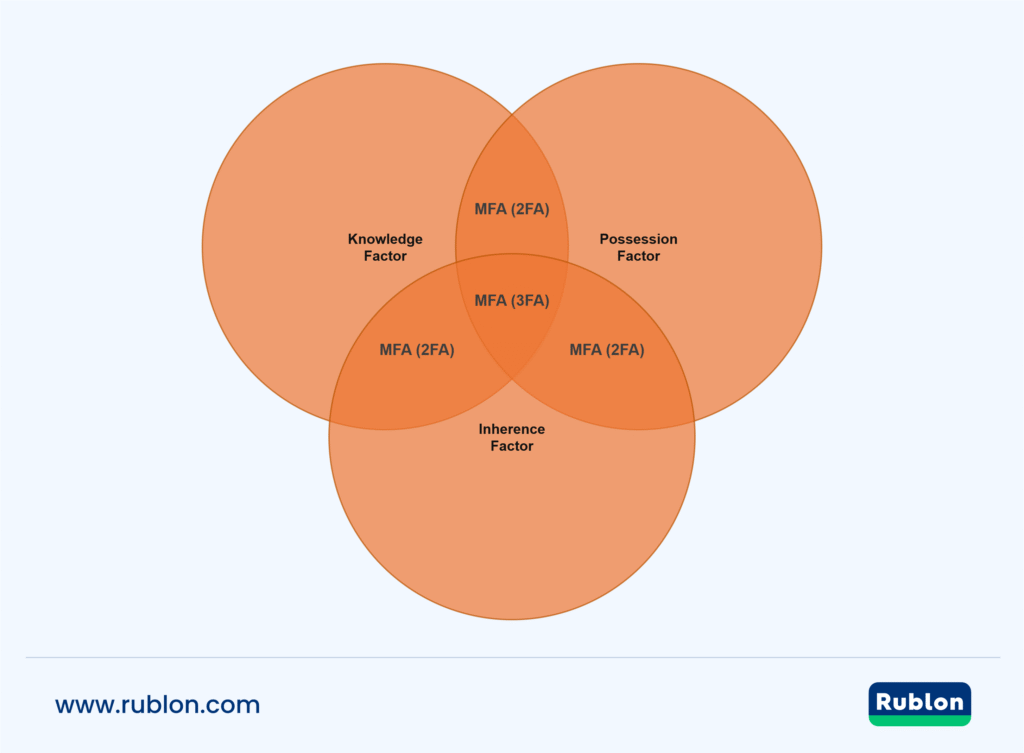
Why Use 2FA? Research-Based Summary
1) Huge Increase in Security – 99% Less Risk of Hacking
The US cybersecurity agency CISA (Cybersecurity and Infrastructure Security Agency) clearly states that using 2FA reduces the risk of hacking by as much as 99%. Two-factor authentication is a powerful protective barrier, especially when passwords are weak or have been compromised.
2) Protection Results: Over 99.99% of Accounts Remain Safe
A detailed study conducted by Lucas Augusto Meyer, Sergio Romero, and others in the Azure AD environment showed that:
- Over 99.99% of accounts with 2FA enabled remain secure,
- and the risk of account takeover is reduced by 99.22% for the entire population and by 98.56% for password leaks.
It’s worth noting that authenticator apps (e.g., Microsoft Authenticator, Rublon Authenticator) are more effective than SMS. However, the most secure are phishing-resistant FIDO2 hardware keys.
3) 2FA Blocks Up to 99.9% of Automated Attacks
A Microsoft report shows that 2FA blocks up to 99.9% of automated attacks, providing powerful support for everyday account protection.
4) 2FA Adoption is Increasing Worldwide
The 2FA authentication industry is growing. In 2024, two-factor methods accounted for 46.4% of MFA market revenue, while software-based solutions held 48.3%. This confirms that 2FA remains the leading security standard.
5) Global Regulatory & Adoption Trends
Around the world, governments and standard‑setting bodies are progressively mandating or recommending stronger authentication, including forms of 2FA or MFA. For example:
- In the European Union, regulations such as NIS2, DORA, and PSD2 require strong authentication, including the use of two or more authentication factors.
- In the United States, bodies such as NIST (National Institute of Standards and Technology) issue guidelines (e.g., NIST SP 800‑63) which explicitly define levels of assurance, where 2FA or MFA is required for higher assurance.
- In India, initiatives like the Digital Personal Data Protection Bill and various cybersecurity frameworks encourage or mandate stronger protections for critical services.
- Adoption by large tech companies and platforms (Google, Microsoft, Facebook, etc.) also helps set expectations: when major platforms make 2FA the default or strongly recommended, users’ exposure to risk decreases.
6) Balancing Usability and Security
While some older studies have pointed to usability issues with 2FA, more recent analyses show positive results. More and more organizations and users are implementing 2FA, which reduces the risk of compromise, especially in an era of increasing cyber threats.
Barriers to 2FA Adoption (SMBs)
According to a report by the Cyber Readiness Institute:
- As many as 65% of small and medium-sized businesses worldwide do not use MFA or 2FA and have no plans to implement it.
- 58% of them are unaware of the benefits of MFA.
- 85% of companies do not require MFA from their customers or suppliers.
- The biggest barrier is the cost of implementation (44% of responses).
However, inaction carries real risks.
According to Verizon’s 2025 Data Breach Investigations Report (DBIR), ransomware was present in 44% of all breaches, but it hit small and medium-sized businesses the hardest. Ransomware was present in 88% of breaches in this group, compared to only 39% in large organizations.
The main barriers to implementing MFA (including 2FA) in small and medium-sized enterprises (SMEs), according to the CRI 2024 Global Report. The most noteworthy are low awareness of the benefits (58%), lack of implementation plans (65%), and costs as the biggest obstacle (44%).
How 2FA Works
2FA (two-factor authentication) involves combining two separate identity verification factors from the following categories:
- Knowledge (something you know, e.g., password, PIN),
- Possession (something you have, e.g., token, phone),
- Biometrics (something you are, e.g., fingerprint, facial scan).
This model provides a higher level of security because an attacker must overcome two independent layers of security.
Main 2FA methods:
- SMS codes – easy, but susceptible to SIM swap attacks;
- OTP apps – generate offline codes, more secure;
- Push notifications – fast and convenient;
- Hardware keys (FIDO2 / U2F) – most secure, phishing-resistant;
- Biometrics – convenient, but requires appropriate hardware.
Want to learn more about how each of these methods works – their advantages, disadvantages, and recommendations for use? Check out the dedicated post: Multi-Factor Authentication (MFA/2FA) Methods: Pros, Cons, and Use Cases.
What happens when you enable 2FA?
After activating two-factor authentication, every login process becomes more transparent and secure:
- Besides a password, the system requires a second factor, such as a code, key, phone, or biometric verification.
- Additionally, the service can automatically suggest adding the device to a trusted list (known as “remembered devices”), reducing the frequency of 2FA requests.
- With workforce 2FA, organizations get access to centralized management tools, dashboards for security teams to review and revoke devices, authentication and audit login histories, and access policies, giving admins greater visibility and control over access across all user accounts and endpoints.
How to enable 2FA? Step by step
Universal Rules for Enabling 2FA
Most online services allow you to activate 2FA. This option is usually found in the “Security” or “Login” section of your account settings. It’s a simple process: after logging in, you select a method (SMS, app, key), confirm, and voila: your account gains an additional layer of protection. It’s a good idea to start with your most important account, such as email, and gradually secure other services.
Step by Step: How to Enable 2FA for Google Account (Gmail)
- Log in to your Google account and go to “Security.”
- Find the “2-Step Verification” section and click “Get Started.”
- Select your preferred method, such as push notifications (default), SMS, an authenticator app, or even a hardware key.
- Scan the QR code with your phone or confirm your chosen method.
- Once setup is complete, 2FA is enabled. You can now use two-factor authentication, enhancing your account security.
How to Deploy 2FA in Your Company? A Practical Guide
Introducing two-factor authentication in your organization not only increases security but also meets regulatory compliance requirements, reduces the risk of data loss, and ensures business continuity. A sound implementation strategy minimizes user resistance and ensures effective adoption.
Key Deployment Steps
- Security Needs Assessment: Identify systems and data requiring special protection (admin logins, VPNs, critical resources). This will allow you to select the appropriate level of authentication.
- Selecting a 2FA method and provider: Choose a solution that is compliant with regulations and scalable. Ensure the provider supports anti-phishing protection and offers flexible options (e.g., push, tokens, FIDO2 hardware keys).
- Pilot (test implementation): Start with a smaller department or group, gathering feedback and eliminating potential issues before a broader rollout.
- Training and Communication: Conduct an information campaign: why 2FA, how it works, and how to use it. This ensures better employee acceptance.
- Full Implementation: Launch gradually across the organization, guided by security policies and work culture.
- Monitoring and Optimization: Monitor adoption and deployment effectiveness. Regularly check that 2FA methods are working correctly and for any vulnerabilities (e.g., reported push errors, lost keys).
Streamline your 2FA rollout with our Guide to Rublon Deployment Best Practices, which walks you through every stage of two-factor authentication deployment, from pilot testing and team training to production launch and IT support.
Advantages and Disadvantages of Two-Factor Authentication (2FA)
Advantages of 2FA
- Significantly higher level of cybersecurity: Two-factor authentication (2FA) requires two independent identity confirmations, drastically reducing the risk of unauthorized access, even if the password is compromised.
- Identity theft protection: Even if a cybercriminal obtains the password, access is impossible without the second factor, providing an effective security barrier.
- Accessibility and flexibility of authentication methods: Users can choose between SMS, authentication apps, hardware keys, and biometrics, allowing them to tailor the method to the needs and capabilities of the organization.
- Enhanced operational security: 2FA is becoming the standard for protection in sensitive systems (e.g., banking, social media), improving the overall security culture within companies.
- Transparency and visibility of logins: When 2FA is enabled, users know exactly what is happening during login: the process requires two steps, increasing control and security awareness. If an access attempt is made from an unauthorized source, e.g., another device or location, the 2FA system may block access or require additional verification, which constitutes a real barrier for an attacker.
Disadvantages and Limitations of 2FA
- Additional time and effort for users: The need to use two factors can be perceived as a nuisance, especially in everyday activities, which can impact acceptance of the solution.
- Hardware dependency and technical support: Losing a phone, token, or hardware key can be disorganizing and require advanced IT support. This is a costly, though rare, scenario.
- Infrastructure implementation and maintenance costs: Hardware-based solutions (U2F/FIDO2 keys) involve one-time purchases, distribution logistics, and technical support.
- Bypassability with poor implementation: Some 2FA methods, especially SMS-based ones, are vulnerable to SS7, SIM-swap, and man-in-the-middle attacks.
- Advanced phishing tools that attack 2FA: Criminals use phishing techniques to trick users into entering a code or using a token on a fake website, even though 2FA is enabled.
How a Well-Chosen 2FA Provider Can Mitigate These Challenges
- Phishing resistance – solutions supporting the FIDO2 standard and passkeys, such as Rublon MFA, are virtually impossible to compromise through phishing attacks thanks to the strong origin binding between the user, device, and service.
- Ease of implementation and broad adaptability – platforms that offer “no-code” implementation, self-service for users, and support for various protocols (LDAP, RADIUS, SAML, etc.) minimize resistance from IT teams and end users.
- Technical support and local context – the availability of a local language support team and market-specific knowledge (e.g., EU, NIS2, ISO 27001) increases acceptance and transparency throughout the process.
Regulations and Compliance Standards – Why 2FA is Now a Requirement
- The NIS2 Directive, effective from October 2024, extends cybersecurity obligations to a broader range of sectors, requiring the implementation of effective access control mechanisms, such as two-factor authentication, as part of appropriate technical protection measures.
- ENISA (the European Cybersecurity Agency) recommends the use of secure authentication methods, including 2FA, biometrics, FIDO2 keys, tokens, and SSO in its technical guidance on NIS2.
- The DORA Regulation (concerning the operational resilience of financial institutions) and other compliance frameworks, such as PSD2 and PCI DSS, as well as US regulations (FTC Safeguards Rule, CJIS, Executive Order 14028, NYDFS), also include 2FA as a key security element.
FAQ – Frequently Asked Questions
What are 2FA codes and how are they generated?
2FA codes are one‑time passwords (OTP) generated either by an authenticator app (using TOTP/HOTP standards), via SMS or email, or by a hardware token/security key. They’re valid only for a short time (e.g., 30‑60 seconds for TOTP), and generated based on a shared secret between your device/app and the service.
Can 2FA be hacked or bypassed?
Yes. While 2FA greatly increases security, there are known attack vectors. Examples include tricking users into giving up codes or intercepting them via phishing, using backup codes (if not stored securely) to bypass 2FA, and utilizing SIM-swap attacks.
Are 2FA apps secure? What should I look for?
Yes. Most 2FA apps are quite secure, especially when they follow modern best practices. To pick a secure app, look for features such as offline TOTP code generation, biometric lock, push notifications, and QR code scanning (both for registration and log in).
What is the most common two-factor authentication?
The most widely used form of 2FA is via a code sent to your phone by SMS or a one-time password app (TOTP). Among services that support 2FA, SMS‑based verification and authenticator apps are still the most common options. They are popular because they are relatively easy to set up, familiar to users, and supported by many platforms.
Which accounts should I protect with 2FA?
You should enable 2FA on any account that holds sensitive personal information, financial data, or access to other services. That includes email, cloud storage, social media, banking and payment apps, your work accounts (VPN, internal dashboards), and any account that could be a gateway to other accounts (e.g., password managers). Securing them with 2FA greatly limits damage in case your password is stolen.
What happens if you lose your 2FA phone?
If you lose your 2FA device, you’ll usually still be able to recover access using backup codes, a secondary email address or phone number, or by going through the account provider’s recovery process. Some services also allow transferring your phone number or re‑assigning authentication to a new device if you’ve prepared in advance. For account safety, always store recovery options securely before you lose access.
How to disable 2FA?
Yes, most services allow you to disable 2FA, but it’s highly discouraged as it significantly reduces your account’s security. The process varies by service. Typically, you’ll need to go to Account Settings → Security → and find the option to disable 2FA. For example, Google, Facebook, and Microsoft offer this option in the “Security” or “Login” sections.
