Last updated on January 7, 2026
AES is a widely used symmetric encryption algorithm, while RSA is a well-known asymmetric encryption algorithm. Although people often mention “AES encryption” and “RSA encryption” in the same breath, they serve different purposes and operate in fundamentally different ways. This article will help you understand the differences between AES vs. RSA encryption.
What is Encryption?
Encryption is the process of converting readable data into an unreadable format to protect it from unauthorized access. There are two main types of encryption: symmetric encryption, where the same key is used for both encryption and decryption, and asymmetric encryption, which utilizes a pair of keys, of which one is public and one is private.
What is AES?
AES (Advanced Encryption Standard) is a symmetric encryption algorithm that uses the same key for both encryption and decryption. It is widely used for securing data at rest and in transit due to its speed and strong security.
What is RSA?
RSA (Rivest–Shamir–Adleman) is an asymmetric encryption algorithm that uses a public key to encrypt data and a private key to decrypt it. It is commonly used for secure key exchange, digital signatures, and encrypting small amounts of sensitive data.
AES vs. RSA: What’s the Difference?
The main difference between AES and RSA lies in their encryption methodology. AES is a symmetric encryption algorithm, meaning it uses the same key for both encryption and decryption. On the other hand, RSA is an asymmetric encryption algorithm that uses a pair of keys—a public key for encryption and a private key for decryption.
AES vs. RSA: Differences Table
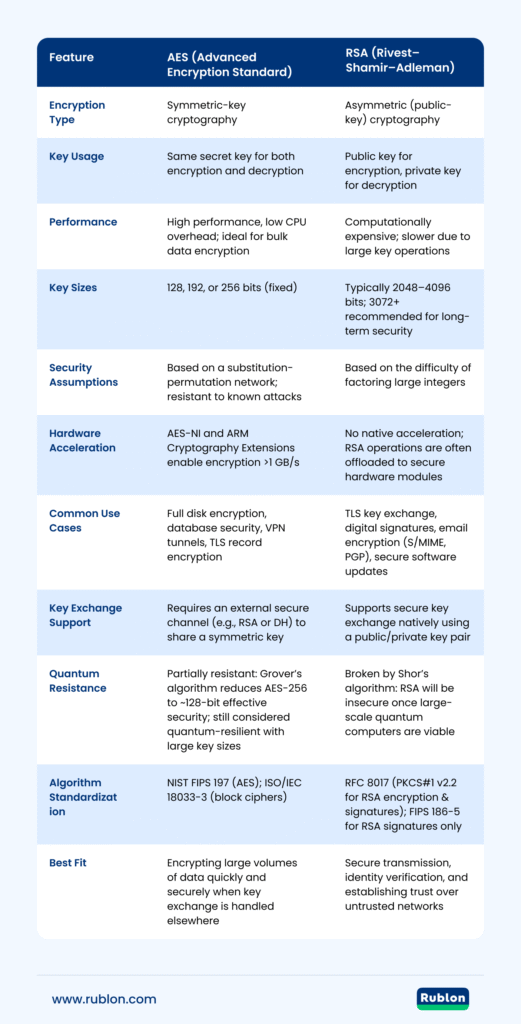
| Feature | AES (Advanced Encryption Standard) | RSA (Rivest–Shamir–Adleman) |
|---|---|---|
| Encryption Type | Symmetric-key cryptography | Asymmetric (public-key) cryptography |
| Key Usage | Same secret key for both encryption and decryption | Public key for encryption, private key for decryption |
| Performance | High performance, low CPU overhead; ideal for bulk data encryption | Computationally expensive; slower due to large key operations |
| Key Sizes | 128, 192, or 256 bits (fixed) | Typically 2048–4096 bits; 3072+ recommended for long-term security |
| Security Assumptions | Based on a substitution-permutation network | Based on the difficulty of factoring large integers |
| Hardware Acceleration | AES-NI and ARM Cryptography Extensions enable encryption >1 GB/s | No native acceleration; RSA operations are often offloaded to secure hardware modules |
| Common Use Cases | Full disk encryption, database security, VPN tunnels, TLS record encryption | TLS key exchange, digital signatures, email encryption (S/MIME, PGP), secure software updates |
| Key Exchange Support | Requires an external secure channel (e.g., RSA or DH) to share a symmetric key | Supports secure key exchange natively using a public/private key pair |
| Quantum Resistance | Partially resistant: Grover’s algorithm reduces AES-256 to ~128-bit effective security; still considered quantum-resilient with large key sizes | Broken by Shor’s algorithm: RSA will be insecure once large-scale quantum computers are viable |
| Algorithm Standardization | NIST FIPS 197 (AES); ISO/IEC 18033-3 (block ciphers) | RFC 8017 (PKCS#1 v2.2 for RSA encryption & signatures); FIPS 186-5 for RSA signatures only |
| Best Fit | Encrypting large volumes of data quickly and securely when key exchange is handled elsewhere | Secure transmission, identity verification, and establishing trust over untrusted networks |
Practical Examples of AES and RSA
To better understand the differences, let’s look at practical examples.
AES in Action:
- Encrypting files on a hard drive to protect against unauthorized access.
- Securing data transmitted over Wi-Fi networks.
- Protecting sensitive data in online transactions.
RSA in Action:
- Establishing a secure connection between a web browser and a server via HTTPS.
- Sending encrypted emails that can only be decrypted by the intended recipient.
- Generating key components (e.g., large primes) that are foundational for cryptographic operations in multi-factor authentication (MFA).
Advantages of AES over RSA
- Speed and Efficiency: AES is faster and requires less computational power, making it ideal for encrypting large amounts of data.
- Simplicity: Uses a single key for encryption and decryption, simplifying the encryption process.
- Strong Security for Data at Rest: Excellent for encrypting stored data to prevent unauthorized access.
Advantages of RSA over AES
- Secure Key Exchange: Enables secure transmission of data without sharing the private key.
- Digital Signatures: Supports authentication through digital signatures, verifying the sender’s identity.
- Data Integrity: Ensures that the data has not been tampered with during transmission.
Mitigate phishing. Sign up for a Free 30-Day Rublon Trial →
Which Should You Choose?
That depends on your use case:
- Choose AES if you need fast, efficient encryption for large volumes of data, such as securing files, databases, VPN traffic, or full-disk encryption. It’s ideal when both sender and recipient can securely share the same key.
- Choose RSA when secure key exchange, digital signatures, or identity verification is required, especially in scenarios like HTTPS/TLS connections, encrypted email, or digital certificate infrastructure, where public-key cryptography is essential.
Conclusion
AES and RSA serve different but complementary roles in modern cryptography. AES offers speed and efficiency for encrypting large datasets, while RSA provides secure mechanisms for key exchange and authentication. Understanding their strengths will help you choose the right encryption approach for your specific security and performance requirements.
Start Free Rublon MFA Trial Today
To fully protect your organization, you need more than strong encryption. You need to ensure that only the right people get access in the first place.
This is where multi-factor authentication (MFA) comes in.
Try Rublon MFA free for 30 days to secure employee logins, roll out FIDO2 security keys and passkeys in minutes, and quickly strengthen your organization’s security posture.
To begin your Free Trial, click the button below.