Last updated on December 15, 2025
With Kaseya announcing the end-of-life for Passly (formerly AuthAnvil) by December 31, 2025, Managed Service Providers (MSPs) are seeking robust, MSP-friendly alternatives that match or exceed Passly’s capabilities. Rublon Multi-Factor Authentication (MFA) emerges as a modern solution that matches Passly’s key features while improving on them in several ways.
You deserve the best.
That’s why we recommend Rublon MFA as a Kaseya Passly alternative.
Rublon has everything you need and more.
Rublon is fast, cost-effective, and easy to use.
Why Consider Rublon MFA as a Passly Replacement?
- Comprehensive Feature Set: Rublon offers a suite of MFA features comparable to Passly, ensuring a seamless transition.
- Enhanced User Experience: With intuitive interfaces and flexible authentication methods, Rublon prioritizes user convenience.
- EU Data Residency: Hosted on AWS in Ireland, Rublon ensures compliance with GDPR and other regional regulations.
Feature Comparison: Rublon MFA vs. Kaseya Passly
| Feature | Passly | Rublon MFA |
| SSO Portal (Tile-Based Launchpad) | ✅ | ✅ |
| SAML 2.0 SSO Support | ✅ | ✅ |
| Windows Login MFA | ✅ | ✅ |
| Entra ID and Active Directory User Synchronization | ✅ | ✅ |
| Active Directory Integration | ✅ | ✅ |
| Flexible MFA Methods (Push, TOTP, FIDO security keys) | ✅ | ✅ |
| Shared MFA / Multiple Devices Per User | ⚠️* | ✅ |
| Policy-Based Access Control | ✅ | ✅ (Granular) |
| EU-Hosted Cloud | ✅ | ✅ (AWS Ireland) |
| Authentication/Audit Log Export | ✅ | ✅ |
* Passly’s standard workflow pairs one authenticator per user account; multi-token scenarios require extra steps and are not emphasized.
Key Feature Highlights
1. Single Sign-On (SSO) Capabilities
- ✅ Unified Tile-Based Launchpad: The Rublon Access Gateway provides a centralized portal for all SAML-connected applications, mirroring Passly’s Launchpad.
- ✅ Flexible Authentication: Users can choose their preferred authentication method, with options to remember devices and enroll new authenticators.
- ✅ Directory Integration: Supports RADIUS and LDAP server credentials (e.g., Active Directory) for seamless user authentication.
2. Windows Logon and RDP MFA
- ✅ Easy Deployment: Rublon offers a lightweight connector approach, eliminating the need for complex configurations.
- ✅ Remote Connection Support: Extends MFA protection to both local and remote Windows logins.
- ✅ Directory Authentication: Seamlessly integrates with Active Directory and Entra ID credentials for efficient user authentication while also supporting local user accounts.
3. Directory Synchronization
- ✅ Convenient User Sync: Synchronize users from Entra ID (Azure AD) or on-premises Active Directory directly into Rublon.
- ✅ Group-Based Management: Synchronizes user groups, which allows for easy policy assignment and user onboarding.
- ✅ Automatic and Manual Syncs: Synchronizations occur twice a day, with an option to manually sync at any time.

4. Shared MFA
- ✅ Shared Accounts: Supports multi-user access to a shared MFA-protected account.
- ✅ Multiple devices: Organizations can enable multiple users to log in to the same account by adding multiple authentication devices.
- ✅ Bypass Codes: Administrators can generate time-limited one-use access codes for a specific user who needs to access the shared account.
Free Trial of Phishing-Proof Rublon MFA Authentication →
5. Multi-Device Enrollment
- ✅ Flexible Authenticator Enrollment: Assign multiple authenticators (phones, phone numbers, FIDO keys) to a single user account.
- ✅ Enhanced Accountability: Each device is named, ensuring clear tracking and management.
- ✅ Self-Enrollment: Allow users to enroll their devices, reducing administrative overhead.
6. Diverse Authentication Methods
- ✅ Comprehensive Options: Rublon MFA supports multiple authentication methods:
- ✅ User Choice: Users can select their preferred authentication method during login, enhancing flexibility.
- ✅ Trusted Devices: Users can choose to add a device as remembered so that they bypass MFA on that device for a defined time.
7. EU-Hosted Cloud Infrastructure
- ✅ Data Residency Compliance: Hosted on AWS in Ireland, Rublon ensures adherence to GDPR and other regional data protection regulations.
- ✅ High Availability: Leverages AWS’s robust infrastructure for optimal performance and reliability.
Protect Yourself Against Phishing
Strengthen your organization’s security by implementing state-of-the-art, phishing-resistant multi-factor authentication with FIDO security keys and passkeys.
8. Granular Policy-Based Access Control
- ✅ Customizable Policies: Define customizable policies and assign them on a per-application and per-user group basis.
- ✅ Controlling Available Methods: Control which methods are available to users using the Authentication Methods Policy.
- ✅ Controlling Trusted Devices: Control if and for how long users can remember their devices using the Remembered Devices Policy.
- ✅ Bypass MFA Based on IP: Control which IP ranges should bypass MFA using the Authorized Networks Policy.
9. Centralized Management and Logging
- ✅ Centralized Management: Manage all your applications, users, policies, and settings from one intuitive Rublon Admin Console.
- ✅ Comprehensive Logging: View and export authentication, audit, and phone logs for compliance and reporting purposes.
10. Built-In Offline TOTP Code Generator
- ✅ Offline Access: The Rublon Authenticator app generates time-based one-time passwords (TOTP), ensuring access even without internet connectivity.
- ✅ Standard Compliance: Adheres to industry-standard algorithms (RFC 6238) for secure code generation.
- ✅ Support for Third-Party OTP Apps and hardware tokens: Rublon supports third-party mobile and desktop apps (Google/Microsoft Authenticator, WinAuth, OTPClient), as well as hardware tokens (OATH-compliant).
How Rublon Can Replace Kaseya Passly: An In-Depth Look
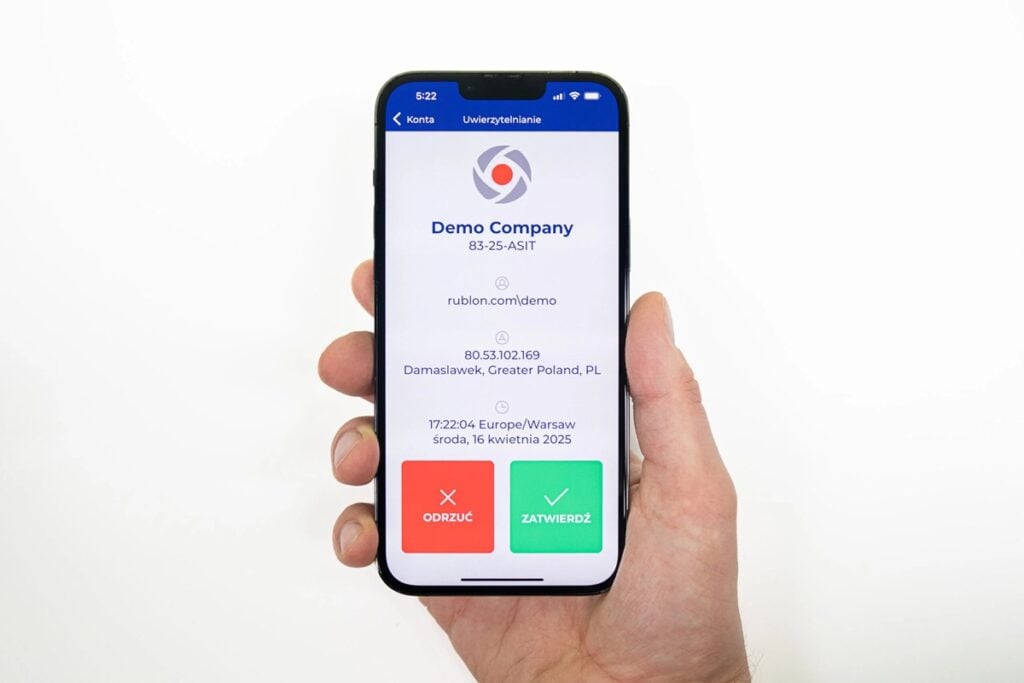
1. Single Sign-On (SSO)
SSO Portal
Passly provided an SSO Launchpad where users could access third-party cloud applications with one click after a single login. This launchpad displayed all integrated apps for a user, simplifying access to cloud applications without repeated sign-ins. In Rublon, this concept is realized through the SSO Portal available within the Rublon Access Gateway, which presents a tile-based interface as a unified launchpad for all applications. Users log in once to the Rublon SSO Portal and can then click on tiles for their apps to be signed in automatically after only completing the second factor.
SAML Integration
Both Passly and Rublon use standard SAML 2.0 protocols to enable SSO. Passly acted as a SAML Identity Provider (IdP), supporting both IdP-initiated logins (from its Launchpad) and Service-Provider-initiated SSO. The Rublon Access Gateway similarly supports SAML 2.0 for cloud apps, including IdP-initiated flows via its portal and SP-initiated flows from the application side. Additionally, Rublon can work in conjunction with RADIUS or LDAP for primary authentication, effectively allowing passthrough authentication from your existing directory: users can log into the SSO portal with their AD credentials, which Rublon then uses to initiate SAML SSO to cloud apps. This means Rublon can serve as a drop-in IdP like Passly did, but with the flexibility to leverage existing authentication sources.
User Experience
Once a user is authenticated to the Rublon SSO Portal, launching integrated apps is seamless. When an app is selected, Rublon handles the SAML exchange to log the user in. If an additional MFA step is required at that moment, the Rublon Prompt will appear, allowing the user to choose an authentication method to confirm their identity (for example, approving a push notification or entering a TOTP code). The overall experience is comparable to Passly’s one-click Launchpad access, ensuring end-users continue to enjoy convenient SSO access to all their business applications.
A few words from a happy Rublon customer:
Very easy to set up even for me who is not professional. You can also manage everything you need with even eyes closed:-) we tested a trial version, it was very easy to set up. we got the pricing immediately. other suppliers did not even replied to my email yet and i already implemented Rublon

Mihail B.
Logistics Manager2. MFA for Windows Logins
Windows Login MFA
One of Passly’s strengths was extending MFA to local Windows account logins. It supported two-factor authentication for Windows 8 through 11 workstations and Windows Server editions (2012–2022) by installing an agent or credential provider on the machine. This meant an additional verification (such as an AuthAnvil/Passly mobile approval or code) was required when users logged into Windows, adding a vital layer of security for on-premises Windows Logons and RDP sessions.
Rublon MFA provides the same protection for Windows logins and does so with a lightweight connector approach. Instead of a heavy agent, the Rublon for Windows connector integrates at the system level to prompt for MFA during Windows sign-ins without complex pre-configurations. Rublon supports all modern Windows client and server OS versions and can secure Remote Desktop (RDP) access.
Seamless Windows Logins
In practice, once Rublon’s Windows Login connector is enabled, a user logging into a protected Windows machine will enter their AD/Entra ID/domain credentials as usual, then be prompted to approve via Rublon MFA (e.g., a push notification on their phone or a FIDO security key) before the desktop unlocks. This mirrors the security Passly provided for Windows logins, ensuring that stolen passwords alone cannot grant access.
Integration with Active Directory and Entra ID
Notably, both Passly and Rublon’s endpoint MFA tie into directory credentials. Passly’s Windows agent worked with AD domain and Azure AD credentials. The Rublon for Windows Logon and RDP connector also integrates with Active Directory and Entra ID, so the primary username/password is validated against AD/Entra ID, and then Rublon adds MFA on top. This design simplifies deployment because there’s no need to manage separate credentials or heavy agents on each machine. If the machine is domain-joined or otherwise connected to the directory, Rublon enforces MFA at login. Overall, Rublon ensures that whether employees are logging into servers via RDP or locally to Windows, the login is secured by MFA in a way that’s as seamless as Passly’s approach, if not more streamlined.

3. Directory Synchronization: Entra ID & Active Directory
Directory Synchronization
Both Passly and Rublon excel in integrating with existing user directories, which is crucial for easy user onboarding and management. Passly offered synchronization of users from on-premises Active Directory. This just-in-time provisioning meant administrators didn’t have to manually recreate or update users in the system.
Rublon provides the same convenience. Rublon allows you to sync Active Directory and Entra ID users, pulling them into the Rublon Admin Console automatically. Once synced, these users can use their Azure AD credentials to log in and will be subject to Rublon’s MFA policies. This makes migrating from Passly straightforward since all your users and groups are imported without hassle.
Ongoing User Management
With Directory Sync enabled, Rublon will continuously reflect changes from AD or Entra ID. For example, if an employee is deactivated in AD, their Rublon account will be automatically removed. Group memberships can also sync, which ties in nicely with Rublon’s policy management (you can assign MFA policies to AD & Entra ID user groups). Essentially, Rublon becomes an extension of your existing identity store, just as Passly was, so you don’t have to manage a separate silo of users. For MSPs, this is critical: whether you manage a single tenant’s AD or multiple directories across clients, Rublon can connect to each to unify identity management with strong authentication.
We were able to get Rublon MFA installed, tested, and in use in under a day across all offices. We were prepared to train all users, but all we had to do was send an email with the install instructions of the app, and they installed it on their mobile devices easily, logged in, and started without us having to provide training to one user. That’s rare in IT!

Ethan M.
Hospital & Health Care4. Shared Account MFA (Just-in-Time Access for Multiple Users)
Shared Accounts
In real-world scenarios, some accounts (especially administrative or shared accounts) might be used by more than one person. Traditionally, MFA solutions assume a one-user-one-device model, which makes it challenging if, say, two technicians need to log in with a shared admin account that has MFA. Passly’s MFA was primarily designed for individual user accounts (each user enrolls their own authenticator). If two people shared an account, they likely had to also share the MFA token or device – a security no-no and a logistical headache.
Rublon addresses this shared account use case with a more flexible approach. It is possible to enroll multiple authentication devices for a single account, meaning each person who needs to use a shared login can have their own MFA method tied to that account. For example, if three people all use the same account, each person can have their own phone enrolled to receive push notifications when logging in with that account. Rublon allows adding additional authenticators to an account, and each device can be named (e.g., “Alice’s phone”, “Bob’s token”) for clarity.
Bypass Codes
Rublon also provides a secure and auditable solution for shared accounts through time-limited one-use access codes. These bypass codes are generated by administrators for users who require emergency or temporary access to a shared account. Each code can be configured to expire after a certain time or after a given number of uses, reducing risk while maintaining operational flexibility. This feature is a more secure and flexible alternative to just enrolling multiple devices on the same account.
Just-in-Time (JIT) access
Rublon’s support of shared accounts effectively provides Just-in-Time (JIT) access: only authorized team members with enrolled MFA devices or Bypass Codes can use the account, and they’ll be challenged each time, so you maintain accountability. It’s a balanced approach between security and practicality. While it’s always ideal to give each user a unique account, MSPs know that certain legacy systems or emergency accounts get shared. Rublon ensures you don’t lose MFA protection in those cases. Passly did not emphasize this scenario, so Rublon’s support for multi-user MFA on one account is a welcome enhancement, achieved without compromising security (since every access is MFA-verified and logged).

6. Flexible Authentication Methods
Diverse Options
Both Passly and Rublon understand that one size does not fit all when it comes to authentication methods. Passly offered a variety of MFA methods: a mobile authenticator app (Passly Mobile) for push approvals and one-time codes (though Passly’s own app was eventually retired in favor of standard apps) and hardware tokens. This gave end-users and admins flexibility – for instance, if a user didn’t have a smartphone, they might use a hardware token, or if they had poor cell service, they could fall back to a code.
Rublon MFA provides even more authentication options than Passly. The centerpiece is the Rublon Authenticator mobile app, which supports one-tap push authentication (the user gets a push notification and taps “Approve”) as well as generating TOTP codes (called “Passcodes” in Rublon) and scanning QR Codes. In addition, Rublon supports third-party TOTP apps – users can scan a QR code and use Google Authenticator, Microsoft Authenticator, etc., to generate login codes if they prefer. For users who want or need physical tokens, Rublon supports hardware OTP tokens (such as Token2 or other OATH-compliant tokens) and WebAuthn/U2F security keys like YubiKeys for phishing-resistant MFA. Rublon’s compatibility list extends to methods like SMS Passcodes, SMS Links, Phone Calls, and Email Links as well, ensuring that even if a user has no smartphone or token on hand, there are alternative ways to get a second factor.
Convenient Method Selection
All authentication methods available in Rublon MFA are presented to the user through the Rublon Prompt view during login. One of Rublon’s user experience advantages is that it allows users to choose their preferred method each time (or default to the admin-selected method). For instance, when logging in, the Rublon Prompt can show options like “Mobile Push”, “Passcode”, “SMS Code”, etc., and the user simply selects one to proceed. This is especially useful if one method is unavailable – say, the user’s phone has no internet for push, they can switch to TOTP code, which works offline.
Rublon is a pleasure to use and administer. It’s got basically everything we need to provide MFA to our customers and doesn’t require you to jump through crazy hoops like Azure. You create your account and do a bit of setup, install the agent on your workstation or server, and quickly you can get MFA for remote desktop. Not much more work for various popular VPNs with their RADIUS proxy. Lots of options on the app and you don’t even need to use it if you go with SMS.

Michael R.
Partner7. Secure EU-Hosted Cloud
Data Residency
A significant consideration for many organizations today is data residency and compliance with regional regulations (like GDPR). EU-based MSPs might be concerned about having identity data stored solely in US data centers.
Rublon offers an advantage here by hosting its cloud platform in the European Union (specifically, in Ireland). Rublon’s infrastructure is hosted on Amazon Web Services in the AWS eu-west-1 (Ireland) region. This means that all user authentication data, logs, and administrative information in Rublon are stored within EU borders, which can simplify compliance with EU data protection laws and ease client concerns about data sovereignty. Rublon’s service is also monitored 24/7 by a certified AWS partner to ensure security and uptime.
For MSPs with European clients or those who must adhere to strict data localization policies, Rublon’s EU-based cloud is a reassuring feature. It delivers high availability and performance. By choosing Rublon as a Passly replacement, MSPs gain a platform that is built with global security standards and offers EU hosting by default. This can be highlighted as a value-add when communicating with customers about the switch.

8. Policy-Based Access Control with Rublon Policies
Passly allowed administrators to define authentication policies, for example, requiring MFA for certain applications or users, and it integrated with Kaseya’s Policy Manager for some aspects. Rublon takes a similar approach with a robust Policy-Based Access Control (PBAC) system. Rublon Policies let you create custom rules that govern when and how MFA is applied.
With Rublon Policies, an administrator can, for instance, set a policy that bypasses MFA for a specific IP range (like the office network) but enforces MFA from elsewhere. Using policies with applications and user groups allows administrators to create and fulfill advanced user cases where MFA requires a higher-trust method (like a FIDO security key) for administrators who log in to a critical application, but allows regular users to use any method. Policies can be assigned to applications or globally, and they can be tied to user groups imported from Active Directory and Entra ID.
9. Centralized Management & Exporting Logs
Centralized Management
Rublon provides a single pane-of-glass Admin Console where administrators can oversee all users, applications, and policies under their management. Within the console, you can do everything – add users (manually or via Directory Sync), configure applications, set policies, change settings, and view logs. The interface is modern and straightforward, similar in spirit to Passly’s dashboard but updated for 2025 expectations. Rublon also offers role-based admin controls, so you can delegate certain management tasks to client IT staff while keeping overall control.
Audit and Authentication Logs
Both Passly and Rublon log the important events. Rublon maintains Authentication Logs (each MFA attempt, including the user, app, method used, success/failure, timestamp, and location/IP) as well as Audit Logs (administrative actions like policy changes, user additions, etc.). Rublon’s commitment to transparency is evident – administrators can easily review these logs for suspicious activities or compliance reporting.
Additionally, Rublon’s logging covers not just user login attempts but also the second-factor delivery (“Phone Logs”). If any OTP SMS or phone call authentication is used, those events are recorded too, and they can be audited. This level of detail helps MSPs troubleshoot authentication issues (e.g., “Did the user receive the code?”) and demonstrate compliance with security policies.
Exporting Logs
Rublon enables you to export logs to CSV with a single click. This is extremely useful for MSPs who might want to consolidate logs in a SIEM, archive them, or provide reports to customers. For example, you can download a full authentication log report for the past quarter and deliver it as part of a security review. (In Passly, there was no built-in log export for some data, which made retention more difficult; Rublon addresses that by allowing full export and even has an Admin API for pulling logs programmatically.)

10. Built-In MFA Code Generator (TOTP in Rublon Authenticator)
Offline Authentication
One of the handy features for any MFA solution is the ability to generate one-time passcodes on the user’s device that work even when the device is offline. Passly’s mobile app (when it existed) and its compatibility with apps like Google Auth meant users could always fall back to a TOTP code if push notifications or connectivity failed. Rublon provides this capability natively via the Rublon Authenticator app, which has a built-in TOTP code generator for each account.
Rublon’s app generates a new 6-digit Passcode (TOTP) every 30 seconds. This happens entirely offline – even if your phone is in airplane mode, you can open Rublon Authenticator and see the current one-time code for your account. The TOTP codes follow industry-standard algorithms (RFC 6238). This feature is extremely useful for cases like VPN or Windows login, when the phone might not have internet access to receive a push. Users are not left stranded; the code shown in the app can be entered to satisfy the MFA requirement.
Conclusion
Rublon MFA stands out as a comprehensive and flexible alternative to Kaseya Passly, offering feature parity and enhancements in key areas such as shared account access, policy-based controls, and EU-based hosting. Its user-friendly interface, diverse authentication methods, and centralized management make it a compelling choice for organizations seeking a robust MFA solution in 2025 and beyond.