Last updated on January 7, 2026
Google Authenticator and YubiKey both help protect user accounts. Yet, each works differently. Some top-ranking articles focus on the basic differences without covering important aspects. These gaps often leave IT administrators and security leaders looking for more concrete answers. In this guide, you will learn about the differences between Google Authenticator vs. YubiKey, including what many other articles miss.
Overview: Software vs. Hardware
Google Authenticator is a software-based one-time password generator. It runs on smartphones, creating time-based codes to verify a user’s identity. In contrast, YubiKey is a hardware security key. Users physically insert the key or hold it against the NCF reader to authenticate.
Many organizations use both solutions to authenticate logins for employees and customers. Both options are available in popular MFA platforms like Rublon MFA, which streamlines secure access across corporate systems using robust multi-factor authentication.
Google Authenticator vs. YubiKey: What’s the Difference?
The main difference lies in their form and cost. Google Authenticator is free software for mobile devices, while YubiKey is a physical key you must buy that plugs in or connects wirelessly. But there are more differences than just that.
Here’s a handy table comparing both.
Google Authenticator vs. YubiKey: Differences Table
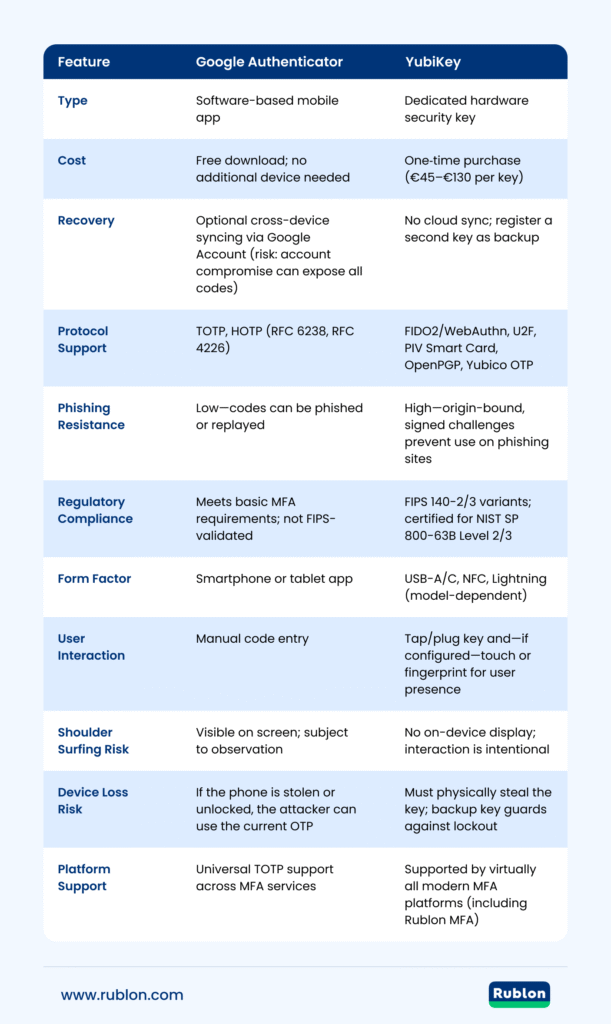
| Feature | Google Authenticator | YubiKey |
|---|---|---|
| Type | Software-based mobile app | Dedicated hardware security key |
| Cost | Free download; no additional device needed | One‐time purchase (€45–€130 per key) |
| Recovery | Optional cross-device syncing via Google Account (risk: account compromise can expose all codes) | No cloud sync; register a second key as backup |
| Protocol Support | TOTP, HOTP (RFC 6238, RFC 4226) | FIDO2/WebAuthn, U2F, PIV Smart Card, OpenPGP, Yubico OTP |
| Phishing Resistance | Low—codes can be phished or replayed | High—origin-bound, signed challenges prevent use on phishing sites |
| Regulatory Compliance | Meets basic MFA requirements; not FIPS-validated | FIPS 140-2/3 variants; certified for NIST SP 800-63B Level 2/3 |
| Form Factor | Smartphone or tablet app | USB-A/C, NFC, Lightning (model-dependent) |
| User Interaction | Manual code entry | Tap/plug key and—if configured—touch or fingerprint for user presence |
| Shoulder Surfing Risk | Visible on screen; subject to observation | No on-device display; interaction is intentional |
| Device Loss Risk | If the phone is stolen or unlocked, the attacker can use the current OTP | Must physically steal the key; backup key guards against lockout |
| Platform Support | Universal TOTP support across MFA services | Supported by virtually all modern MFA platforms (including Rublon MFA) |
Looking for a FIDO MFA Provider?
Protect Active Directory and Entra ID users from hackers with phishing-resistant FIDO security keys and passkeys.
Advantages of YubiKey Over Google Authenticator
- Stronger Physical Security: YubiKey is a tangible token. Attackers need physical possession to breach. This lowers the risk of threats, such as malware, and thwarts many types of attacks.
- Phishing Resistance: YubiKeys are phishing-resistant, allowing for extremely secure Phishing-Resistant MFA.
- Stronger Compliance With Stringent Regulations: YubiKey is considered the most secure type of authentication, thus ensuring stronger compliance with even the most stringent cybersecurity regulations like the Federal Zero Trust Strategy Memorandum and NIST SP 800-63B AAL3.
- Wider Set of Authentication Options: Newer YubiKey models support multiple authentication standards. These may include Yubico OTP, FIDO U2F, and FIDO2. This flexibility offers more options for enterprise deployments.
Advantages of Google Authenticator Over YubiKey
- No Hardware Costs: Google Authenticator is free and only requires a smartphone or tablet. This makes it cost-effective for smaller teams and budget-conscious home users.
- Wider Adoption: While the adoption of YubiKeys has been widening each year, Google Authenticator is still a more widely supported option.
- Immediate Availability: Users can download the app and start securing accounts right away, with no need to wait for shipping or physically manage keys.
Enterprise Considerations
Both Google Authenticator and YubiKey can secure business applications, but the choice often depends on budget, user training, and compliance requirements.
- MFA Integration: Pick an MFA provider that supports both options. For example, Rublon MFA allows companies to manage both Google Authenticator and YubiKey authentication methods under a single platform. Administrators gain centralized control over user onboarding, policy enforcement, and usage logs.
- Deployment Complexity: Software authentication may scale faster across a distributed workforce, as employees already own smartphones. Hardware keys like YubiKey are much more secure but require distribution to all users and thus demand extra logistics.
- Cost Over Time: Google Authenticator involves no direct costs beyond potential phone maintenance. However, its lower level of security can lead to a compromise that can prove costly to the organization, both money-wise and reputation-wise. In contrast, YubiKey requires an upfront investment but offers extra-strong phishing-resistant protection, dramatically decreasing the likelihood of a compromise.
Mitigate phishing. Sign up for a Free 30-Day Rublon Trial →
Which Should You Choose?
Selecting between Google Authenticator and YubiKey depends on several factors. While budget is important, security posture is key. Software-based solutions are easier and cheaper to deploy. However, YubiKey offers superior security. This makes YubiKey preferable for any organization that cares about security and compliance.
Enterprise solutions like Rublon MFA simplify using both methods side by side. This can be ideal for organizations seeking strong MFA protection for privileged accounts (via YubiKey) while still offering a user-friendly alternative (via Google Authenticator) for the rest of the workforce.
Looking for FIDO2 Security Keys? We Got Them!
Need reliable FIDO2 security keys for your staff or customers? We can help you choose the right models.
Start Free Rublon MFA Trial Today
Experience 30 days of Rublon MFA at no cost.
Strengthen your defenses with phishing-resistant logins, deploy FIDO2 security keys and use Google Authenticator (and other MFA mobile apps), and effortlessly elevate your organization’s security posture.
To begin your Free Trial, click the button below.
