Last updated on January 7, 2026
Point-of-sale (POS) systems remain high-value targets because they sit on the payments path and connect to many back-office and edge components. This short guide groups recurring classes of weaknesses you should monitor in SAP POS environments and gives quick, low-effort mitigations, including where multi-factor authentication (MFA) helps.
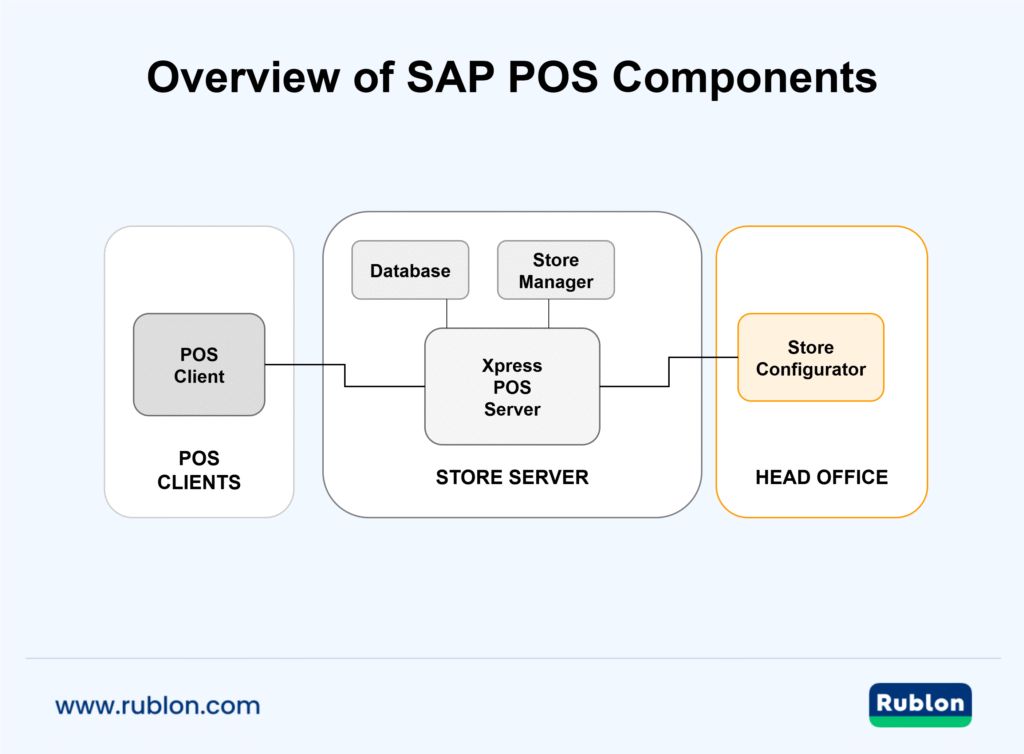
What is SAP POS?
SAP POS is part of the SAP for Retail portfolio: a client–server point-of-sale solution where thin POS clients (terminals) communicate with a store-level server (often called Xpress or POS Server) and with head-office management tools. The store server handles transaction processing, configuration, backups, and distribution of settings to terminals; the head office provides central management functions.
SAP POS Attack Scenario
1) Gain Network Foothold
An attacker obtains access to the store network (via an exposed management interface, a compromised IoT/edge device, a contractor laptop, or weak remote access). This is the usual first step in modern POS compromises.
2) Abuse Management Endpoints
From the store network, the attacker calls administrative/configuration endpoints (file uploads, config APIs, restart commands). If those endpoints lack strong authentication/authorization, the attacker can push malicious configurations or binaries.
3) Trigger and Persist Malicious Behavior
The store server applies the malicious config (or executes uploaded code), POS clients pick up the changes on restart, and the attacker achieves goals such as price manipulation, service disruption, or data exfiltration. The hacker frequently remains undetected if logging and monitoring are poor.
Mitigate POS hacking. Sign up for a Free 30-Day Rublon Trial →
Top 5 SAP POS Vulnerability Classes
1) Broken Authentication & Missing Authorization
Why: Admin/config endpoints that accept unauthenticated requests let an attacker perform privileged actions (change pricing, upload configuration).
What to check: Endpoints that accept file/config uploads, default/unused accounts, APIs trusting network location.
Examples: Older SAP POS Xpress issues demonstrated the impact of missing authentication. Recent 2025 upload/authorization CVEs in SAP show similar consequences if upload or admin paths are exposed.
Quick mitigations: Enforce strong multi-factor authentication and RBAC on all management endpoints; remove/rotate defaults; protect management interfaces with network ACLs and MFA where possible.
2) Unrestricted File Upload & Insecure Deserialization
Why: Unsafe uploads or deserialization can let attackers deploy backdoors or execute code on the store server.
What to check: Any uploader or metadata endpoint; server-side deserialization of untrusted data.
Examples: 2025 NetWeaver/Visual Composer upload/deserialization advisories show file upload/deserialization remains an active vector.
Quick mitigations: Isolate upload endpoints, require authentication + allowlist file types, sandbox deserialization, monitor file system for unexpected binaries.
3) Weak Network Segmentation & Exposed Management Interfaces
Why: Lateral movement from a compromised IoT device or non-segmented VLAN frequently precedes POS compromise.
What to check: Can POS servers be reached from general corporate networks or the internet? Are management ports accessible?
Examples: Major breaches often begin with a foothold in peripheral systems and escalate when network segmentation is weak, a pattern visible in several large incidents (for example, the SolarWinds supply-chain compromise showed how a single vector can lead to widespread, high-impact access when segmentation and least-privilege controls are insufficient). In POS networks, similarly, exposed IoT devices and weak segmentation in retail and banking environments enable attackers to move laterally into critical payment and supply systems.
Quick mitigations: Segment POS networks (deny east-west by default), block management interfaces from general access, require a hardened jump host and MFA for remote admin access.
4) Supply-Chain & Third-Party Integrations (Middleware, Edge Gateways, Plugins)
Why: Third-party modules, payment middleware, and edge devices are common entry points and often poorly maintained.
What to check: Inventory of plugins, firmware versions, signed code, and update policies.
Examples: Recent OAuth token abuse cases, such as the 2025 Salesloft/Drift incidents, highlight how a single compromised third-party integration can cascade into widespread exposure across customer environments — a risk mirrored in POS systems that rely on external orchestration layers. Similarly, supply-chain attacks like the 3CX Supply Chain Attack show how trusted vendor software can deliver malicious code at scale, often reaching retail POS endpoints through infected middleware, management tools, or firmware updates.
Quick mitigations: Inventory & prioritize vendor updates; minimize plugin privileges; require code signing where supported.
5) Poor Logging, Monitoring, and Recovery Practices
Why: Attacks often succeed because manipulations go undetected and backups are vulnerable.
What to check: Are POS logs centralized and monitored? Are backups offline/immutable and tested?
Examples: Insufficient logging and monitoring, as noted by OWASP, allow attackers to persist undetected and exfiltrate data, especially in POS environments where subtle manipulations often evade alerts. Additionally, weak or untested backup and recovery processes in retail systems frequently lead to prolonged outages and costly recovery after ransomware or supply-chain compromises.
Quick mitigations: Centralize logs to SIEM/EDR, add alerts for config changes, keep offline/immutable backups, and practice restores.
Where MFA Helps
- Admin interfaces / head-office access: Enforce MFA for any human access to store-level management consoles or configurators (reduces risk from credential theft).
- Remote admin / jump hosts: Require MFA + conditional access for remote connections into POS management networks.
- POS terminals (where feasible): For cashier/admin logins, consider MFA options supported by your POS platform (TOTP, hardware tokens, or secure smartcard logins) to reduce the damage from shared credentials; some retail POS suites now support MFA flows for sensitive operations.
Looking for a FIDO MFA Provider?
Protect Active Directory and Entra ID users from hackers with phishing-resistant FIDO security keys and passkeys.
Quick Checklist — Do It This Week
- Confirm all management/upload endpoints require authentication and RBAC; enable MFA for human admin accounts.
- Ensure POS management ports are not publicly reachable; block them at the perimeter and require a hardened jump host for remote admin access.
- Apply any critical SAP Security Notes / out-of-band patches (review Patch Days and immediate advisories such as recent 2025 upload/deserialization fixes).
- Inventory third-party plugins and edge firmware; schedule critical updates.
- Centralize POS logs into your SIEM; alert on unexpected config file changes; ensure backups are offline/immutable and test restores.
Conclusion
Treat the 2017 Xpress-style scenario as a historical lesson. The pattern (network access → management endpoint → config push → terminal behavior) remains valid. In 2025 and 2026, the immediate threats may come from modern upload/deserialization flaws and chained exploitation across edge/middleware, but the defenses are simple and low-effort: patch critical SAP Security Notes, segment networks, enforce MFA for admin access, and monitor for config changes.