Last updated on April 23, 2024
When you start a Remote Desktop connection, the Remote Desktop client on your computer starts listening to the connection on a defined listening port. The default port for RDP is 3389. This article describes how to change the RDP listening port.
How to change the RDP port in Windows?
1. Before you make any changes, choose a new port number.
Pick a port within the 1024-49151 range.
Using well-known ports (1-1023) or dynamic, private, or ephemeral ports (49152-65535) is not recommended.
We picked port 33900 for this tutorial.
2. If you use a firewall, open the port you want to use for RDP.
3. Connect to your remote computer (Windows Client or Server) via RDP.

4. Start the registry editor (press WIN+R, type regedit, and press Enter).

5. Navigate to the following Remote Desktop Registry:
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp
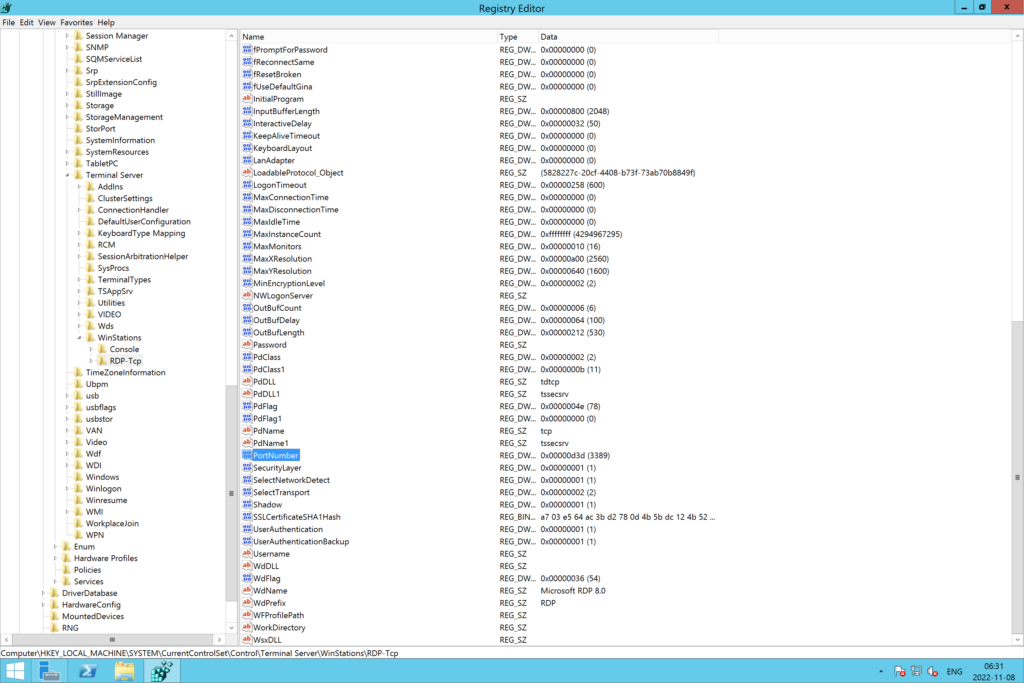
6. Find the PortNumber value, double-click it, and change the port number (Base Decimal).
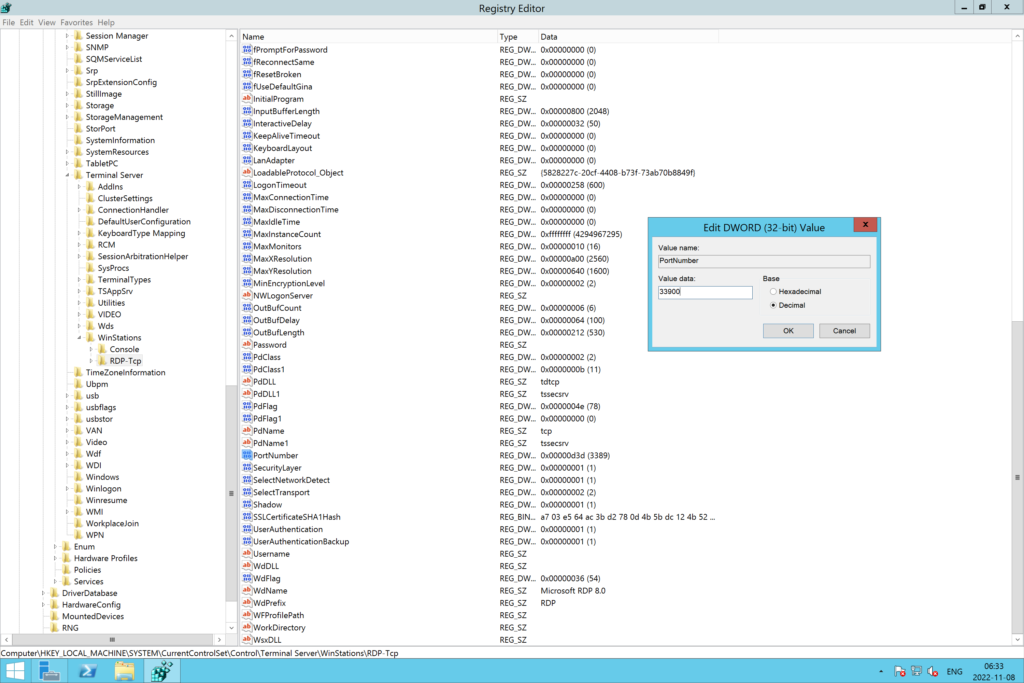
7. Click OK to save the changes and restart your computer for the changes to take effect.
How to validate the RDP port change in Windows?
1. After changing the RDP port in Windows and restarting your computer, connect to your Windows Server or Client via RDP.
2. Open Powershell (press WIN+R, type powershell, and press Enter).

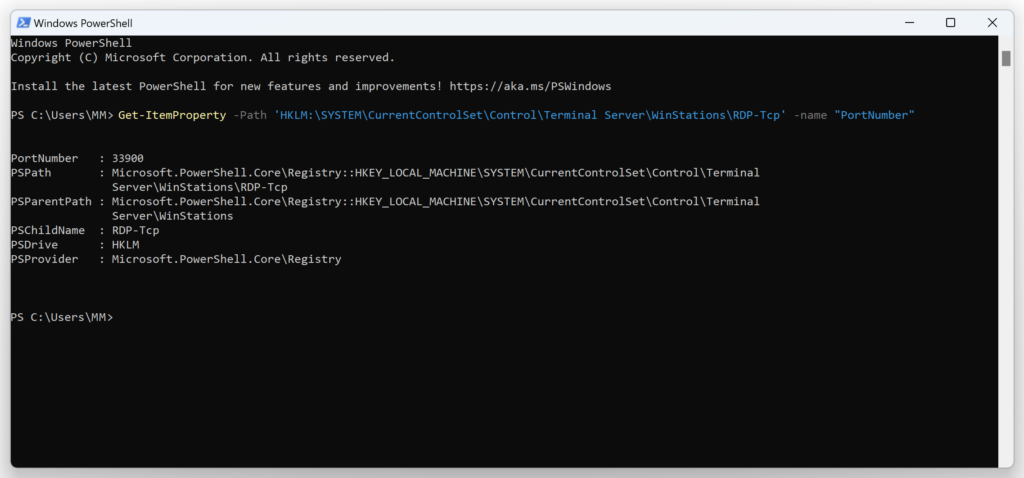
3. Run the following PowerShell command to confirm Remote Desktop Service is listening on the new port:
Get-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp' -name "PortNumber"
Note
You can also verify the port change by running the command netstat -an in the Command Prompt and looking for your new port number in the list of addresses.
Why should I change the RDP port in Windows?
Remote Desktop Connection (RDP) is one of the most common cyberattack vectors. Changing the RDP port can help you defend against port scanning and hackers using brute force attacks to enter your remote computers to steal data.
How can I further improve my RDP security?
You can use Multi-Factor Authentication (MFA) to secure your Remote Desktop connections with an extra layer of protection. MFA adds a secure second factor that prevents 99.9 percent of attacks on your accounts.
Enabling company-wide Multi-Factor Authentication (MFA) may seem a daunting task. But it really isn’t. Mercifully, there are MFA security providers that can help you deploy MFA on all your endpoints, achieve regulatory compliance, and introduce strong security controls for your workforce.
How Rublon MFA can help
Rublon MFA is a sophisticated Multi-Factor Authentication (MFA) security provider that enables organizations with MFA for RDP, MFA for RD Gateway, MFA for RD Web Access, MFA for RD Web Client, and more.
To enable MFA for Remote Desktop Services, start a Free 30-Day Rublon Trial.