Last updated on February 18, 2025
RDP and Azure AD are not compatible out of the box. Say you create a VM in Azure and Azure AD-join it so that you can log in via RDP with an Azure AD account. Well, the sad news is that you will receive a ”The user name or password is incorrect. Try again” error. (Or simply see “The logon attempt failed” message on the login box.) This guide has all the instructions you need to fix this error and enable RDP into VM using Azure AD credentials.
Secure Your RDP Connections Against Hackers
Fortify your remote desktop access with powerful multi-factor authentication. Ensure secure Remote Desktop connections every time you log in.
Why Can’t I RDP Into Azure AD VM?
You need to turn off Network Level Authentication (NLA).
RDP works in such a way that when you enter a login and password in the RDP client, they are immediately checked and if they are correct, the user is immediately allowed into the system.
But when your machine is joined to Azure AD, the RDP client does not know how to serialize credentials correctly, so it always shows that the data entered is incorrect.
So, to use Azure AD with RDP, you have to disable the authentication function in the client. After you do that, the client will immediately start showing you the Windows login screen where you can enter the login and password.
How to Connect to Remote Azure Active Directory Joined Device?
1. Log in to your VM in Azure.
We have a Windows 11 VM but the instructions are the same for other versions of the Windows operating systems.
2. Open the Control Panel and click System and Security.
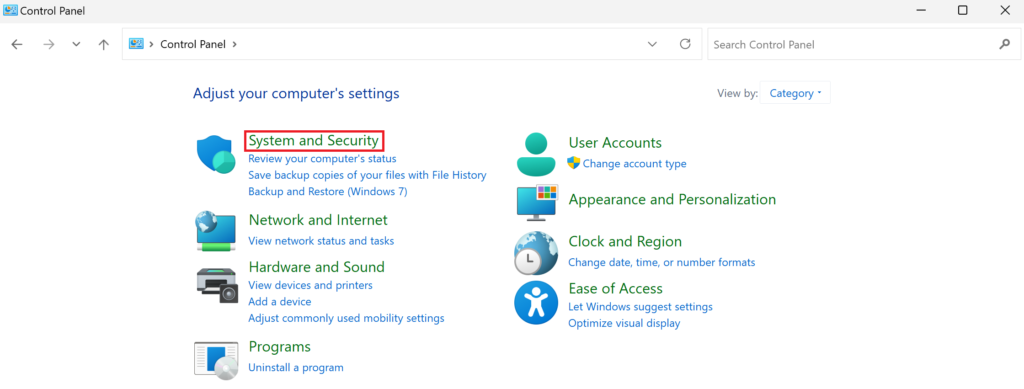
2. Click Allow remote access.
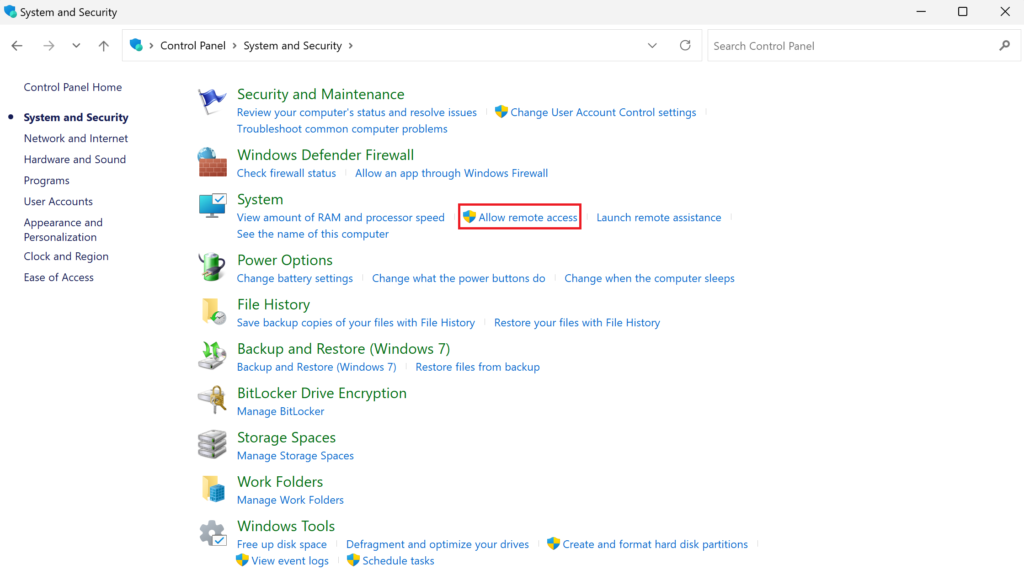
3. Uncheck Allow connections only from computers running Remote Desktop with Network Level Authentication and click OK to save the change.

4. Create an RDP file that you will use to connect to your Azure AD-joined VM. Of course, you can edit your existing RDP file instead of creating a new one.
The contents of the file should be as follows:
full address:s:IPADDRESS:3389
prompt for credentials:i:0
authentication level:i:2
enablecredsspsupport:i:0
username:s:USERNAME@DOMAIN.onmicrosoft.com
domain:s:AzureAD
Here’s what each line means:
- Full Address: The IP address of your Azure VM. The 3389 is the Remote Desktop Protocol port.
- Prompt for credentials: This decides if you need to enter your credentials before starting your session. Use 1 to ask for credentials and 0 to skip this step.
- Authentication level: This sets the server authentication level. Use 2 to show a warning and let you connect or disconnect if the server authentication fails.
- Enablecredsspsupport: This chooses whether RDP will use Credential Security Support Provider (CredSSP) for authentication if possible. Use 0 to disable CredSSP, even if the system supports it.
- Username: This is your Azure AD user account name
- Domain: This is your Azure AD domain name
5. Use the RDP file you just modified to connect to the VM.
6. The user name field should have the domain prefix appended before the username. Some users reported that this does not work for them and they have to enter their domain name manually. Either way, your username field should look like this:
AzureAD\USERNAME@DOMAIN.onmicrosoft.com
7. After entering the user name, enter your password and log in to your Azure AD-joined VM.
8. Congratulations! You just logged in with your ADD credentials to your VM created in Azure.
Enable MFA for your Azure AD VM Logins
Your Azure AD machine needs more security. Enable sophisticated Multi-Factor Authentication (MFA) today and enjoy world-class protection for your Azure AD account. Rublon MFA uses the most secure authentication methods like Mobile Push and YubiKey OTP to bolster your cyber defenses. Even if hackers know your Azure AD credentials, Rublon MFA thwarts them from RDPing into the Azure AD-joined VM.
How does Rublon MFA do that? It’s simpler than you think. Take a look at Enable MFA for Azure AD logins to Windows Logon and RDP.
Try Powerful Rublon MFA for Free
Try Rublon MFA for free and enjoy the top security of logins via RDP, VPN, cloud app, and more.
Conclusion
RDPing into an Azure AD-joined VM using Azure Active Directory credentials does not work out of the box. But a simple fix described in this guide allows you to connect to remote Azure AD devices via RDP. Remember that RDP is a common attack vector that hackers can use to access your remote machine. For that reason, we strongly recommend you enable Multi-Factor Authentication (MFA) on all your VMs. Rublon MFA is a robust solution that adds an extra layer of security to your local Windows logons, RDP connections, cloud app logins, VPN connections, and more.