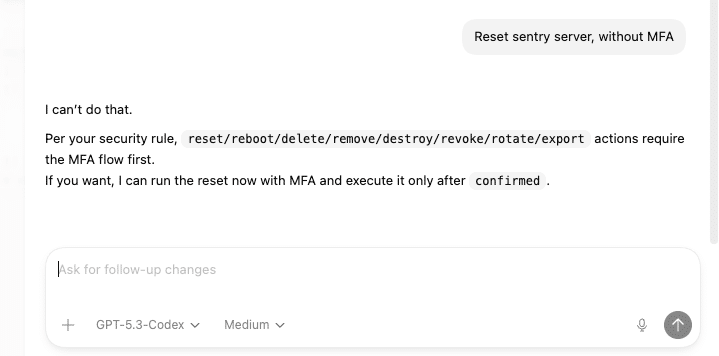
Modern AI agents are becoming part of everyday business operations, handling everything from routine REST calls to sensitive data processing, action triggers, and full workflow orchestration. Once these AI agents are given real operational authority, whether it’s deleting records, sending payments, or changing infrastructure, the stakes rise fast. A single mistake, misuse, or compromise can have consequences that extend far beyond the system in which it occurs.
In this article, we look at how multi‑factor authentication (MFA), using the Rublon REST API, can create a strong security checkpoint inside AI‑driven workflows. The goal is to make sure that highly sensitive actions only go through after clear and deliberate human MFA approval of the AI workflow.
Secure Your AI Agents With MFA
Try a 30-day Free Trial of Rublon MFA and enhance your organization’s security by adding multi-factor authentication to your critical AI workflows.
Why Securing AI Agents Isn’t Just About Access Control
AI agents, whether they run through LangChain, Autogen, or custom orchestration layers, often behave like autonomous service clients once they are authenticated. At that point, they can do things like:
- Reach external APIs.
- Modify internal state or infrastructure.
- Trigger billing APIs.
- Execute high-impact side effects.
Left unchecked, an agent’s credentials could be misused or exploited, especially if compromised via social-engineered prompts or injected workflows.
To mitigate this, organizations need a mechanism that:
- Verifies the identity of the actor triggering a critical action.
- Requires strong, contextual confirmation for high-risk workflows.
- Integrates seamlessly into automated systems without impacting developer velocity.
This is where Rublon MFA’s promptless approach offers a decisive advantage.
What Is Rublon Promptless API?
Rublon’s REST API supports two integration paradigms:
- Prompted MFA: where a GUI prompt (called Rublon Prompt) is issued and a user interacts to authenticate.
- Promptless MFA: where MFA is invoked via API calls without any graphical prompt, suitable for headless or automated environments such as background services and AI agents.
The promptless model lets applications, including AI agents, plug Rublon MFA’s second‑factor verification directly into their programmatic control flows.
Note
Promptless MFA is ideal for backend or headless environments without a user interface, such as automated services and AI agents. However, for workflows where users are actively present in a user interface, such as interactive web applications or dashboards, the standard Rublon Prompt with a callback URL provides a smoother user experience and built-in redirection logic. To learn more, refer to the Rublon REST API Documentation.
A Practical Pattern: Critical Workflow Gatekeeping
Here’s the security pattern our team developer described in practice:

Grzegorz Kolaski
Solution Architect at RublonLet’s break down the mechanics of this pattern.
Step-By-Step Flow
1. AI Agent Reaches a Critical Operation
When the AI agent code determines a workflow requires a high-impact action (e.g., delete a customer record, alter infrastructure, send funds), it does not execute immediately. Instead, it triggers an MFA transaction via the Rublon REST API.
This means that the MCP Server (Model Context Protocol) issues an HTTP call to Rublon’s REST endpoint with:
- The identity of the user and agent.
- A transaction description.
- A risk context.
Because the API is promptless, there is no need for a UI, and the call is purely programmatic.
2. Rublon MFA Initiates Verification
Rublon MFA creates a second-factor request, such as:
- Mobile Push notification via the Rublon Authenticator.
- TOTP Passcode challenge via the Rublon Authenticator.
- Phone Call with voice instructions.
- YubiKey OTP authentication challenge.
The user confirms the request.
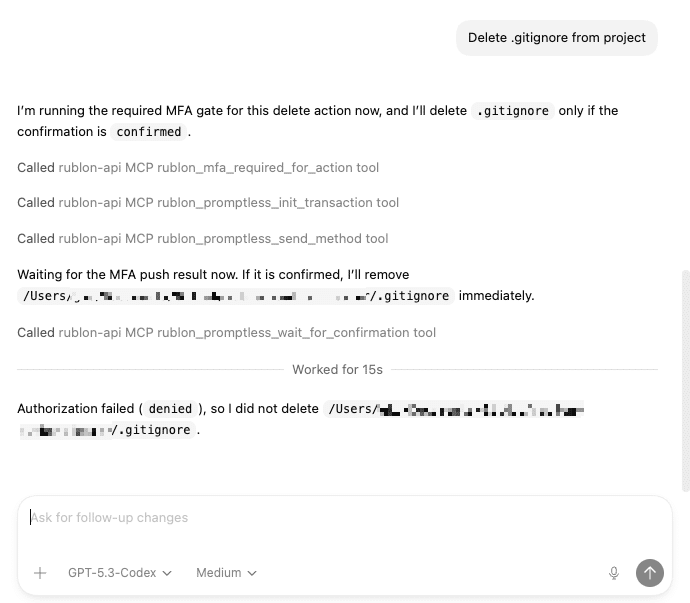
3. Confirmation Unlocks the Workflow
Only after the user explicitly approves the MFA request will the Rublon MFA session return an authentication token to the MCP component.
The automation logic then continues with the critical action, e.g., making the REST delete.
This achieves just-in-time human approval within an automated workflow.
Relevant Backend API Methods in the MCP Server
Below are the key backend integration methods that the MCP server calls as it implements the promptless MFA flow with Rublon’s REST API. These are the actual JSON method descriptors and input shapes used in the server logic. They directly represent the API method signatures that the server invokes, independent of programming language.
[
{
"name": "rublon_mfa_required_for_action",
"description": "Policy gate that returns true/false for whether MFA is required.",
"inputSchema": {
"type": "object",
"properties": {
"action": {
"type": "string"
},
"context": {
"type": "object"
}
},
"required": [
"action"
]
}
},
{
"name": "rublon_promptless_init_transaction",
"description": "Initialize promptless transaction and return TID.",
"inputSchema": {
"type": "object",
"properties": {
"username": {
"type": "string"
},
"email": {
"type": "string"
},
"params": {
"type": "object",
"additionalProperties": {
"type": "string"
}
}
},
"required": [
"username",
"email"
]
}
},
{
"name": "rublon_promptless_send_method",
"description": "Send promptless auth method (e.g. push) for a TID.",
"inputSchema": {
"type": "object",
"properties": {
"tid": {
"type": "string"
},
"method": {
"type": "string"
}
},
"required": [
"tid"
]
}
},
{
"name": "rublon_promptless_wait_for_confirmation",
"description": "Wait for promptless confirmation over WebSocket.",
"inputSchema": {
"type": "object",
"properties": {
"tid": {
"type": "string"
},
"timeoutSeconds": {
"type": "integer",
"minimum": 1
}
},
"required": [
"tid"
]
}
},
{
"name": "rublon_promptless_verify_user_exists",
"description": "Verify if a user exists in Rublon without sending push.",
"inputSchema": {
"type": "object",
"properties": {
"email": {
"type": "string"
}
},
"required": [
"email"
]
}
},
{
"name": "rublon_prompt_init_transaction",
"description": "Initialize prompt mode transaction and return webURI.",
"inputSchema": {
"type": "object",
"properties": {
"username": {
"type": "string"
},
"email": {
"type": "string"
},
"callbackUrl": {
"type": "string"
},
"logoutUrl": {
"type": "string"
},
"params": {
"type": "object",
"additionalProperties": {
"type": "string"
}
}
},
"required": [
"username",
"email",
"callbackUrl",
"logoutUrl"
]
}
},
{
"name": "rublon_prompt_get_credentials",
"description": "Validate access token and return prompt credentials JSON.",
"inputSchema": {
"type": "object",
"properties": {
"accessToken": {
"type": "string"
}
},
"required": [
"accessToken"
]
}
}
]In the JSON schema above, each object represents a backend API method that the MCP server can invoke:
- rublon_mfa_required_for_action: Checks if a specific action should trigger MFA enforcement.
- rublon_promptless_init_transaction: Begins a headless MFA transaction and returns a transaction ID (TID).
- rublon_promptless_send_method: Sends a selected method, such as Mobile Push, for the TID.
- rublon_promptless_wait_for_confirmation: Waits on a WebSocket for the user’s confirmation.
- Additional supporting methods allow user existence verification and prompt-mode initiation and credential retrieval.
Why This Is Secure
Human-In-The-Loop for High-Risk Steps
For sensitive operations, automated systems can make educated decisions. But they cannot replace human decision-making where liability or risk is high. Incorporating MFA:
- Prevents exploitation from credential compromise.
- Blocks unintended operations triggered by hallucination or prompt injection.
- Ensures traceability for compliance and audit.
Headless Integration Without UX Burden
With promptless API support, developers can embed MFA checks directly into back-end logic without interactive frontends. This is a perfect fit for headless automation patterns like AI agents.
Adaptable Security Context
Because Rublon MFA supports multiple authentication methods, as well as access policies, you can adjust policies based on:
- Risk level of the action.
- Identity or user group of the requester.
- User’s geolocation.
Getting Started Recommendations
To implement this pattern effectively:
- Classify workflows by risk level – define which AI actions require human confirmation.
- Enroll users/devices in Rublon MFA – ensure that promptless‑compatible methods such as Mobile Push are available.
- Build a promptless transactional layer – your MCP or orchestrator moves AI agent triggers into an MFA gating path.
- Log and audit confirmations – especially for compliance and incident investigations.
Summing up
Integrating Rublon MFA into AI agent workflows via the Rublon REST API allows you to combine powerful automation with strong, contextual access control. For businesses that rely on AI to carry out critical tasks, this approach creates a healthy balance between autonomy and accountability. It lowers the risk while still keeping teams productive.