Last updated on January 7, 2026
Business-critical SAP components can be used as a vector to deliver ransomware by abusing client-side vulnerabilities, exposed services, or poor segmentation. The specific mechanics vary, but the defensive priorities are constant: patching, segmentation, strong authentication, monitoring, and isolated backups.
The Threats of Ransomware
Ransomware remains one of the highest-impact threats to enterprises. While many high-profile incidents have targeted internet-exposed databases and file shares, attackers can also leverage ERP infrastructure, including SAP servers and SAP GUI clients, to deploy ransomware at scale inside corporate networks. Recent industry reporting shows a marked rise in ransomware activity targeting SAP and other business-critical applications.
Can SAP Be Affected by Ransomware?
Yes. SAP ecosystems can be affected by ransomware if attackers can reach and abuse components that touch user endpoints or critical data flows. Historically, this has included client-side vulnerabilities (e.g., CVE-2017-6950, a remote-code execution issue in SAP GUI) and misconfigured or exposed services that allow code or configuration pushes to many workstations.
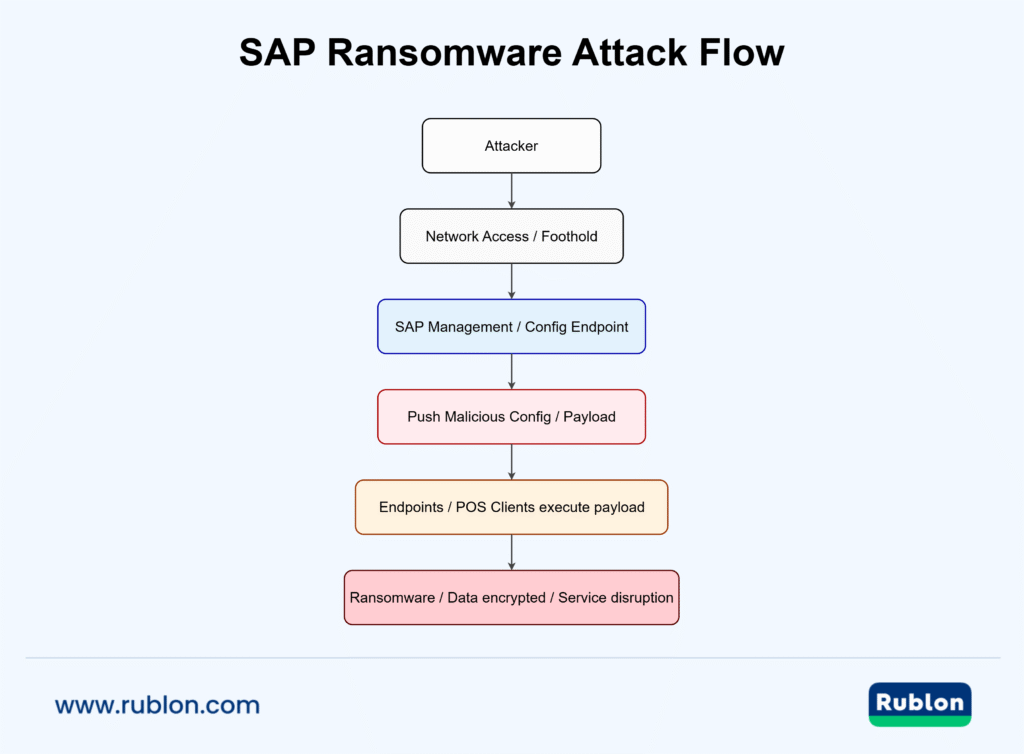
Ransomware Attack on SAP at a Glance
- Gain a foothold: Attacker compromises a server, contractor laptop, or an edge/IoT device inside the store/corporate network (or finds an exposed service).
- Abuse SAP infrastructure: Attacker uses admin/configuration interfaces, custom transactions, or client vulnerabilities to push code/configuration to many SAP GUI clients or backend hosts.
- Deploy ransomware: Infected endpoints download and run ransomware (or attackers encrypt SAP data), causing service disruption and demanding payment.
Why This Matters Now
- High impact: SAP often stores and orchestrates business-critical processes, so a successful disruptive attack can shut down finance, supply chain, and retail operations.
- Increased targeting: Recent analysis from Onapsis reports a multi-hundred-percent surge in SAP-related exploit activity and ransomware mentions since 2021, including a 400% rise in ransomware incidents and a 490% increase in online discussions of SAP vulnerabilities. These trends reflect growing threat actor interest in SAP-specific cloud services, with forum activity up 220% from 2021 to 2023.
- Low-effort vectors still exist: Internet-exposed management interfaces, misconfigured services, or unpatched clients continue to be exploited in supply-side and opportunistic ransom campaigns. For example, mass compromises of unsecured MongoDB servers and misconfigured Elasticsearch instances have been repeatedly abused in opportunistic ransom campaigns; these incidents show how simple misconfiguration can enable large-scale impact.
How an Attacker Could (Realistically) Weaponize SAP Infrastructure
- Compromise a server or management account (phishing, vulnerable service, weak credentials).
- Use admin/custom transactions or a vulnerable client to push a config or script that instructs clients to download and run a payload.
- Trigger a restart or a scheduled task so clients execute the payload and become encrypted/locked.
- This approach mirrors real-world chains used in other enterprise ransomware campaigns where a single privileged foothold enables broad distribution.
Protecting SAP (Practical What-to-Do Controls)
- Patch & harden: apply SAP Security Notes promptly for both server components and client tools (SAP GUI). Track vendor advisories and prioritize critical fixes.
- Segment & isolate: isolate SAP systems and user workstations in VLANs/subnets; deny lateral movement and block management interfaces from general networks.
- Strong auth & access controls: enforce multi-factor authentication (MFA) for admin users, remove/rotate default accounts, and apply least privilege on service accounts.
- Monitoring & detection: centralize logs to SIEM/EDR, add integrity monitoring for configuration files, and automated alerts for sudden configuration pushes or unexpected file drops. Onapsis and other SAP-focused vendors recommend application-layer monitoring tailored to SAP traffic.
- Backups & recovery: ensure offline or immutable backups, test restore procedures, and protect backup credentials and media from the main network. Cloud and SAP vendor guidance emphasizes secure recovery mechanisms for SAP deployments.
Looking for a SAP MFA Provider?
If you need MFA for SAP admin accounts, try a 30-day evaluation:
Immediate 3-Step Actions
- Patch and harden critical SAP components (servers and clients).
- Segment SAP networks and enforce phishing-resistant MFA for privileged access.
- Centralize logs/EDR, alert on config pushes, and ensure offline/immutable backups that are regularly tested.
FAQ
Is there a “standard” ransom for SAP incidents?
No. Ransoms vary widely and depend on the victim’s size and impact. Large enterprise incidents can involve 5–7 figure demands, but ransom amounts are only one measure of cost (downtime and recovery are often far more expensive).
Does patching fix everything?
Patching fixes known CVEs but does not replace layered defenses. Attackers exploit misconfiguration, exposed services, weak auth, and human factors, as well as unpatched bugs. Combine patching with segmentation, MFA, monitoring, and recovery planning.
Are SAP systems more attractive to attackers than other services?
They are attractive because of their high business impact. Compromising SAP can halt core operations, which increases the incentive for extortion. That said, attackers also target easier low-hanging fruit when available (exposed DBs, unpatched web apps).