Last updated on December 15, 2025
When administrators hold the proverbial keys to your MFA platform, every Admin Console sign-in should meet the highest assurance bar without slowing anyone down. Admin Sign-in Settings in the Rublon Admin Console gives administrators with the Owner role a single control pane to manage how admins authenticate to the Rublon Admin Console.
Admins vs. Users: Different Controls, One Platform
Organization’s administrators who authenticate to business apps, VPNs, RDP, or any other Rublon-protected resource are still treated as regular users by Rublon MFA. They appear in the Users tab of the Admin Console and remain subject to all existing Rublon Policies. Nothing has changed here.
Admin Sign-in Settings address a separate need: deciding which authentication methods Rublon administrators may use when they access the Rublon Admin Console—the centralized hub where MFA for applications, users, groups, and policies is managed. This keeps day-to-day user MFA policies unchanged while giving you fine-grained control over Admin Console access for admin accounts.
Why Centralized Admin Authentication Matters
| Challenge | Impact | How Admin Sign-in Settings Helps |
| Inconsistent authentication requirements across teams | Security gaps, audit findings | Define one universal admin setting |
| Reliance on vulnerable methods (e.g., SMS) | Higher susceptibility to hacking (e.g., phishing, SIM-swap attacks) | Disable weaker methods and enforce FIDO2-only logins with a few clicks |
| Session management | Forgotten logouts, lingering risk | Set a session lifetime that meets NIST AAL2/AAL3 guidelines |
| Disparate MFA settings for admins | Complex operations, higher misconfiguration risk | Consolidate all admin sign-in controls in one tab |
Free Trial of Phishing-Proof Rublon MFA Authentication →
Key Capabilities
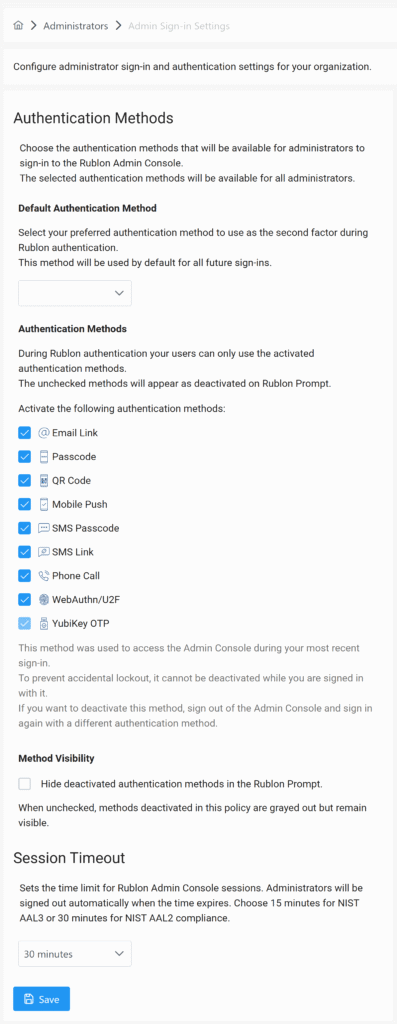
1. Method Allow-List
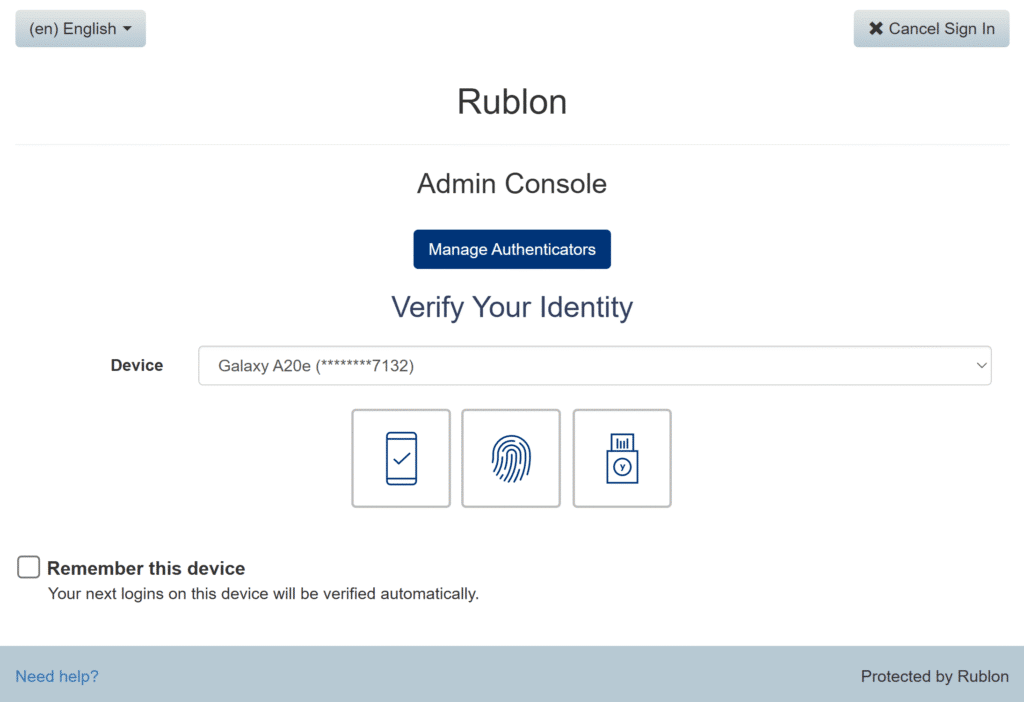
Select the authentication methods admins can use: FIDO, Mobile Push, Phone Call, or others. Depending on the settings, the Rublon Prompt either grays out or removes deactivated authentication methods, eliminating guesswork and confusion.
2. Session Lifetime Controls
Set how long an admin session remains valid before admins are automatically signed out of the Rublon Admin Console. Balance convenience with NIST AAL2 or NIST AAL3 compliance objectives.
3. Self-Lockout Guardrails
Built-in checks prevent an admin from disabling the authentication method they used to sign in, and alert any active admins if their current authentication method becomes deactivated mid-session. Result: zero accidental lockouts, even in distributed teams.
4. Audit-Ready Transparency
Every change in Admin Sign-in Settings is saved to the Audit Log, providing an immutable record for SOC 2, ISO 27001, and internal audits.
Practical Use Cases
FIDO2-Only Enforcement
Mandate phishing-resistant authentication for all admins. This is ideal for organizations adopting Zero Trust that aim to achieve phishing resistance to safeguard administrators’ access to the organization’s centralized MFA authentication management console.
Weak Method Restrictions
Disable phone number-based methods to abide by NIST guidelines. During a heightened threat window, you can also disable push-based methods and require hardware tokens until the incident is resolved.
Compliance-Driven Session Limits
Configure a 15-minute maximum console session to satisfy NIST AAL3 or extend slightly to 30 minutes while still meeting AAL2.
Subscribe Newsletter
Stay ahead with the latest in Rublon and top security practices. Subscribe to the Rublon Newsletter for monthly updates on product enhancements and valuable cybersecurity insights, delivered directly to your inbox.
Final Thoughts
Admin Sign-in Settings introduces a single, global setting for authentication methods that administrators can use when signing in to the Rublon Admin Console. Rublon MFA empowers you to protect administrator accounts without adding friction by enforcing specific authentication methods and aligning session lifetimes with NIST standards.
Ready to put your admin authentication on autopilot? Open the Admin Sign-in Settings tab in the Rublon Admin Console to tailor rules that fend off attackers while ensuring your admins remain productive.
Still haven’t tried Rublon MFA? Start a Free 30-Day Trial and see how to effortlessly protect your employees from cyber threats.