Last updated on January 7, 2026
Authentication is the process of verifying an individual’s identity and is an essential part of any secure digital environment. It ensures that only authorized individuals can access digital services, networks, and systems. Authentication is typically done through the use of passwords, biometrics, access control systems, or multi-factor authentication (MFA). This article will explore the different types of authentication and how to use them to secure digital systems and networks.
What Is Authentication?
Authentication is the process of verifying an individual’s identity. It ensures that only authorized individuals can access digital services, networks, and systems.
Authentication is an integral part of any secure digital environment. It helps protect organizations from cyber-attacks and unauthorized access. Organizations use authentication to keep unauthorized users out of their systems and networks by verifying the identity of users before granting them access.
Types of Authentication
Many different types of authentication can be used to secure digital systems and networks. Below are some of the most commonly used types of authentication.
- Password-Based Authentication
- Single-Factor Authentication (SFA)
- Multi-Factor Authentication (MFA)
- Two-Factor Authentication (2FA)
- Two-Step Authentication (2SA)
- Passwordless Authentication
- Passwordless MFA
- Adaptive Authentication (Adaptive MFA)
- Risk-Based Authentication (RBA)
- Biometric Authentication
- Certificate-Based Authentication
- Out-of-Band Authentication (OOBA)
- Token-Based Authentication
- Single Sign-On (SSO)
- Strong Authentication
- Challenge–Response Authentication
- Mutual Authentication
- Knowledge-Based Authentication (KBA)
- SMS Authentication
- LDAP Authentication
1. Password-Based Authentication
Password-based authentication is one of the most common types of authentication. It combines letters, numbers, and symbols to form a unique password. Users must then enter that password whenever they want access to the digital system or network.
Unfortunately, as simple as password-based authentication is, it has a few grave drawbacks.
The first drawback is that passwords can be easily guessed, broken, and stolen. Hacking passwords is easier than you may think. In 2023, breaking a 6-character password takes less than 30 seconds! Given that, it is crucial to choose a long and unique password. You can also use Multi-Factor Authentication (MFA) or Passwordless Authentication to make authentication more secure.

Another disadvantage of passwords that speaks in favor of a passwordless approach to cybersecurity is password fatigue. Password fatigue is a term used to describe the frustration and anxiety that comes from remembering and managing passwords. For many people, it can be difficult to remember multiple, complex passwords. The feeling of being overwhelmed and frustrated becomes a source of stress. While you can use a password manager to facilitate password management, in the past few years, more companies have started implementing a passwordless authentication approach, eliminating passwords.
Despite its many flaws, password-based authentication can still be successfully incorporated into other types of authentication, like MFA, to create a very secure form of authentication.
2. Single-Factor Authentication (SFA)
Single-Factor Authentication (SFA) is a type of authentication that requires only one form of identity proof. This type of authentication is typically used when the user needs to access a specific account or system that is not protected by Multi-Factor Authentication (MFA). The most common form of SFA is the username and password combination, which is the same as password-based authentication. However, using just your FIDO security key is also considered a form of Single-Factor Authentication.
In more technical terms, Single-Factor Authentication (SFA) uses only one of the three authentication factors.
SFA is one of the most basic types of authentication. In its basic password-based form, it does not provide much security, so companies should replace it with safer alternatives, such as MFA and Passwordless, whenever possible.
3. Multi-Factor Authentication (MFA)
Multi-Factor Authentication (MFA) is a type of authentication that requires more than one form of identity proof. This type of authentication requires the user to provide two or more pieces of information (or factors) to gain access to the account or system.

MFA is considered more secure than Single-Factor Authentication (SFA) as it requires multiple forms of authentication, making it harder for malicious users to gain access.
The downside of MFA is that it can be inconvenient for users. As users are required to provide more information during the authentication process, they experience more log-in friction, leading to user fatigue and frustration.
Despite its downsides, MFA is one of the most secure types of authentication.
4. Two-Factor Authentication (2FA)
Two-Factor Authentication (2FA) is a type of Multi-Factor Authentication (MFA) that requires exactly two authentication factors to access a system or account.
Typically, 2FA requires the user to provide two pieces of information to gain access: something they know (e.g., a password) and something they have (e.g., a phone, security key, or physical token) or something they are (e.g., fingerprint, face scan).

The advantage of 2FA is that it provides an extra layer of security, making it more difficult for malicious users to gain access. The downside of 2FA is that it can be inconvenient for users, as they must provide multiple pieces of information during the authentication process.
MFA and 2FA are often used interchangeably but are not always the same. There are some differences between MFA vs. 2FA.
Two-Factor Authentication is one of the most popular types of authentication. Three-Factor Authentication (3FA) is generally more secure than 2FA, though.
5. Two-Step Authentication (2SA)
Two-Step Authentication (2SA) is a type of authentication that requires the user to provide two pieces of information to gain access.
However, any two authentication factors suffice to call an authentication process Two-Step Authentication. This includes using the same authentication factor twice. For that reason, 2SA is considered more secure than Single-Factor Authentication (SFA) but not as secure as Two-Factor Authentication (2FA) or Multi-Factor Authentication (MFA). This is because MFA and 2FA are authentication types that do not allow using the same authentication factor twice.
6. Passwordless Authentication
Passwordless authentication is a type of authentication that does not require the user to enter a static password. Instead, it identifies the user using other means, such as biometrics, hardware tokens, or time-based one-time passwords (TOTP).


Passwordless authentication can provide a more secure authentication experience because it does not rely on easily hackable passwords. While passwords can be easily compromised during a data breach, other types of authentication, such as biometrics and hardware tokens, are much more secure.
7. Passwordless MFA
Passwordless MFA is a type of Multi-Factor Authentication (MFA) that does not require users to enter a static password to gain access to an account or service. Instead, users are authenticated using biometrics (e.g., facial or fingerprint recognition) or other methods, such as FIDO security keys or push notifications. Passwordless MFA helps to increase user convenience while ensuring that the user accessing the account or service is the legitimate account owner.

Passwordless MFA is one of the most secure types of authentication because it eliminates the weakest link in MFA: the Knowledge Factor.
8. Adaptive Authentication (Adaptive MFA)
Adaptive Authentication is a type of Multi-Factor Authentication (MFA) that uses a range of technologies (e.g., biometrics, location tracking, device recognition, behavioral analysis, and more) to verify user identities and detect suspicious activity.
By monitoring user activity and dynamically adjusting authentication requirements based on the risk associated with the user’s current activity, Adaptive Authentication offers an additional layer of security for user logins. For example, a user logging in from a new device or location may be required to complete additional authentication steps to prove their identity.
Adaptive Authentication is a great way to add extra security to your system without being too intrusive for the user.
9. Risked-Based Authentication (RBA)
Risk-Based Authentication (RBA) is an authentication process that dynamically changes and evaluates the level of verification based on the risk associated with a user session or transaction. It uses real-time analytics and risk-scoring algorithms to determine the risk associated with a user’s activity. It then dynamically adjusts the authentication requirements to match the level of risk.
For example, a user logging in from a new device or location may be required to complete additional authentication steps to prove their identity.

Risk-Based Authentication is a great way to provide extra security to your system while still providing a great user experience. It can help protect your system from malicious users and protect your sensitive data from unauthorized access. This makes Risk-Based Authentication one of the most reliable types of authentication.
10. Biometric Authentication
Biometric Authentication is a type of authentication that uses physical characteristics to verify an individual’s identity. It is based on the idea that each person’s fingerprints, retina, or other physical features are unique and can be used to identify them.
Biometric authentication is typically more secure than password-based authentication because it is much harder to hack or guess. However, biometric authentication can be expensive and only suitable for some applications.
Thankfully, modern devices often come with in-built biometric sensors. For example, most modern smartphones have fingerprint readers and allow facial recognition using the front camera.
Examples of biometric authentication include but are not limited to fingerprint scanning, iris scanning, retina scanning, facial recognition, and voice recognition. It is important to note that other types of biometric authentication, such as gait recognition have also been tested as an authentication type.
11. Certificate-Based Authentication
Certificate-Based Authentication (CBA) is an authentication type that uses digital certificates to verify a user’s identity and to grant access to a computer system. CBA requires users to present a valid digital certificate from a trusted authority to access the system.
The digital certificate contains a unique code used to verify the user’s identity. It is issued by a certificate authority and includes information on the user as well as cryptographic keys that are used to establish a secure connection.
Certificate-Based Authentication is a great way to ensure high-level security while still providing a good user experience. It is often used in highly-sensitive systems where the highest level of protection is needed. CBA is one of the most secure types of authentication.
12. Out-of-Band Authentication (OOBA)
Out-of-Band Authentication is a type of Two-Factor Authentication (2FA) that uses two communication channels to verify a user’s identity. This type of authentication is typically used to secure online accounts.
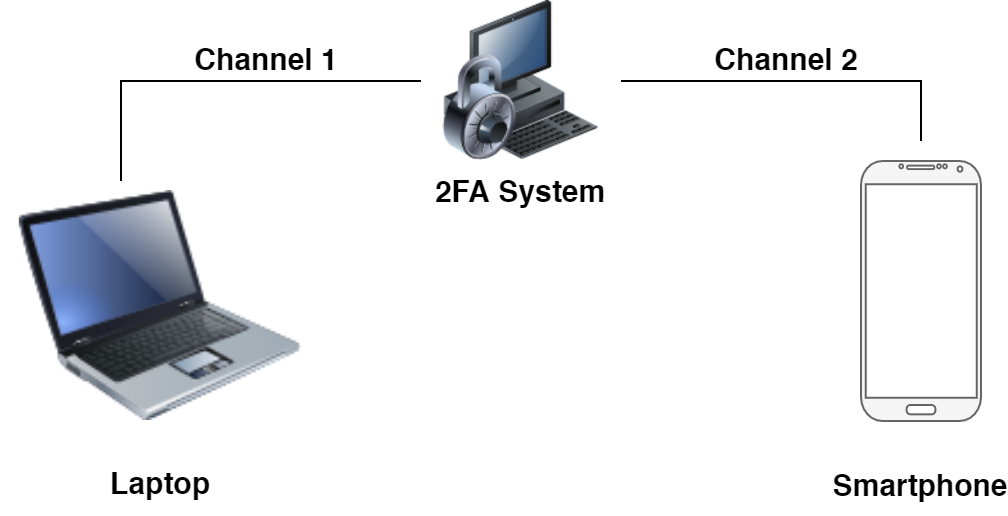
In out-of-band authentication, a user is usually prompted to enter their password on their computer. Then, they are asked to enter a code sent to a secondary device, such as a mobile phone. The user’s identity is therefore verified by two different communication channels.
13. Token-Based Authentication
Token-based authentication is an authentication scheme that uses tokens generated by the server to authenticate a user. It requires the user to provide a valid token to access a system.
After the server generates an access token, the user can use it to access an app or website without having to re-enter credentials. The token is valid until it expires or is revoked.
Token-based authentication is considered more secure than other types of authentication, such as username and password because the token is generated by the server and is not guessable. Furthermore, tokens can be set to expire after a certain amount of time, which provides an additional layer of security.
14. Single Sign-On (SSO)
Single Sign-On (SSO) is a form of identity and access management (IAM) that allows users to authenticate once and access multiple applications and services with a single identity. This eliminates the need to remember multiple sets of login information. The user only needs to remember a single set of credentials, such as a username and password, to access all of their accounts. This makes SSO one of the most user-friendly types of authentication.
Organizations often use this type of authentication to simplify the process of logging into their systems and applications and provide an extra layer of security. It also helps reduce the risk of unauthorized access, as users must authenticate themselves before accessing any of the protected systems.
On the downside, single sign-on can create a single point of failure. If the single user’s credentials are compromised, all systems and applications accessed using those credentials become vulnerable to attack.
To fix this downside, SSO is sometimes used in tandem with Multi-Factor Authentication, but SSO and MFA are not the same thing.
15. Strong Authentication
Strong authentication is a type of authentication that uses multiple factors and components to secure an account or system. This method is considered one of the most robust authentication methods, as it requires multiple credentials and components for users to gain access.
The components that are used in strong authentication include passwords, biometric data, physical tokens, and other authentication factors. Using multiple authentication factors makes it much harder for malicious users to gain access to an account or system.
Strong authentication can be an effective way to protect sensitive information and accounts from unauthorized access. However, it can be inconvenient for users, as it requires them to provide multiple pieces of information or credentials in order to gain access, resulting in a longer log-in process.
16. Challenge–Response Authentication
Challenge-response authentication is a type of authentication that requires the user to respond to a challenge to gain access to an account or system.
This type of authentication is more secure than single-factor authentication, as the challenge requires more than one piece of information. For example, the challenge might require the user to answer a question, enter a code sent to their mobile device, or enter a password.
Examples:
One of the most popular types of challenge-response authentication is CAPTCHA.
RADIUS challenge-response authentication is also a type of challenge-response authentication.
17. Mutual Authentication
Mutual authentication is a type of authentication in which both parties involved in a communication verify each other’s identity. For example, when you log in to a system, the system asks you who you are, and you ask the system who it is. This way, you both know you are talking to the right person or system. This is also called two-way authentication.
Mutual authentication can help protect against man-in-the-middle (MITM) attacks by verifying that the user and the system are who they claim to be.
18. Knowledge-Based Authentication (KBA)
Knowledge-Based Authentication (KBA) is an authentication process that verifies a person’s identity by asking them one or more questions based on information that only they would know. This information can range from a password to personal details like their mother’s maiden name to security questions based on specific account information. Knowledge-Based Authentication is popular as an additional layer of security for account registration and verification processes.
Nevertheless, it is important to note that Knowledge-Based Authentication is not one of the most secure types of authentication. This is because it uses information that somebody knows, and such information can be easily disclosed. Hackers often scan a person’s social media looking for answers to security questions. And people often disclose more information than they should on their social media accounts.
19. SMS Authentication
SMS authentication (also known as SMS 2FA and text message authentication) is an increasingly popular type of two-factor authentication (2FA) that sends a text message containing a unique one-time code to a user’s registered mobile phone number. When the user receives the code, they must enter it into the requested field before they are granted access.

Unfortunately, SMS authentication has its drawbacks. For one, if the user’s device is stolen or lost, they may be unable to access their accounts or services until they get a new device. Furthermore, hackers can use many types of SMS attacks to compromise this authentication method. Despite these drawbacks, SMS authentication is a common and easy way to ensure that users are who they say they are.
20. LDAP Authentication
Lightweight Directory Access Protocol (LDAP) authentication uses an LDAP server to verify the credentials of users who log in to a system. LDAP authentication is one of the most common types of authentication. As such, LDAP authentication is often used in corporate environments where a centralized authentication system is needed.
The process of LDAP authentication begins with a user entering their username and password. The system will then connect to the LDAP server and authenticate the credentials against the directory. The user is authenticated and can access the system if the credentials are valid. LDAP servers are usually configured to require strong passwords, so any weak or easily guessed credentials will be rejected.
Confused With All the Types? This MFA Solution is All You Need!
Rublon MFA is an affordable and reliable Adaptive Multi-Factor Authentication solution that lets you access cloud apps, VPNs, and Remote Desktop Services (RDS) easily with authentication methods, such as Mobile Push and FIDO.
Summing Up Types of Authentication
Authentication is an essential part of any secure digital environment. It is used to verify an individual’s identity and ensure that only authorized individuals can access digital services, networks, and systems. Many different types of authentication can be used to secure digital systems and networks, including password-based authentication, biometric authentication, multi-factor authentication (MFA), and passwordless. Each authentication type has its advantages and disadvantages, so choosing the right one for your organization is essential.