Last updated on March 26, 2024
Authentication is the process of validating if a person is who they say they are.
In the authentication process, a person has to prove their identity to gain access to a resource. A security system seeks to answer the question: Is this person who they claim to be? Once the system ensures the person is who they say they are, the person is authenticated and gains access to a resource.
To prove your identity, you may use:
- Password – a series of characters you must provide to gain access.
- Authenticator App – an application you install on your smartphone and then use to identify yourself to a system or another application.
- Biometrics – a fingerprint or facial recognition to prove your identity.
Passwords can be:
- pre-defined (e.g., the PIN associated with your debit card)
- one-time (e.g., a one-time password sent via an SMS message)
How Does Authentication Work?
You are Mr. Smith, an agent of a secret organization. You want to enter a room that holds classified data. You walk to the door that secures the entrance to the room. Next to the door is an eye retinal pattern scanner. You bring your face close to the reader. A green ray enters your retina. The door unlocks. A robotic voice says “Welcome, Agent Smith”. You have just been authenticated.

While biometrics is used in IT, fingerprint scanners are much more widespread than retinal scanners, voice recognition, or other forms of biometric authentication. Modern smartphones and laptops often come with in-built fingerprint scanners that allow users to fingerprint lock their devices.
Even more ubiquitous are passwords. You do not have to be a secret agent to authenticate using your password. As a matter of fact, you probably do this every day while on the web!
When you log in to your bank account, you are asked to provide your username (or user identifier) and password. This is also an example of authentication.
Naturally, authentication may involve more than one step. When you log in to your bank account, you may also be asked to enter a passcode sent to your phone.
Authentication vs. Authorization: What’s the Difference?
Whereas Authentication is the process of verifying if a person is who they say they are, Authorization is the process of verifying what specific resources the person can access.
The terms authentication and authorization are often used interchangeably, which leads to many misconceptions about cybersecurity. Even though authentication and authorization are both parts of access control, authentication and authorization are entirely different things and should not be confused.

The difference is clear:
Authentication is verifying the identity of a user before allowing access to resources.
Authorization is verifying if a user has required permissions to perform an action.
In a properly designed cybersecurity system, authentication always comes before authorization. A system first checks your identity, and only then decides if you can perform the requested action.
Real-Life Example
You want to pay for your groceries with your debit card.
You must possess the card and also know the PIN. These are two proofs that you are you. Inserting the card into the terminal and entering your PIN is the authentication process.
After you inserted your debit card and provided the PIN, the system checks if you can complete the requested action. In this case, the system must check if you can deduct money from your bank account. This is the process of authorization.
In some circumstances, the security system may not allow you to pay with your debit card. For example, your account may not have enough money. Alternatively, you may be performing the operation in a different city.
Some security systems check your location, and if the location differs from your usual location, they may block you from performing the transaction. On the other hand, some security systems prompt the user for additional confirmation, instead of blocking them. For example, if you live in New York but the transaction occurs in Los Angeles, your bank’s mobile app may prompt you to confirm the transaction. This is an example of access control.
IT Example
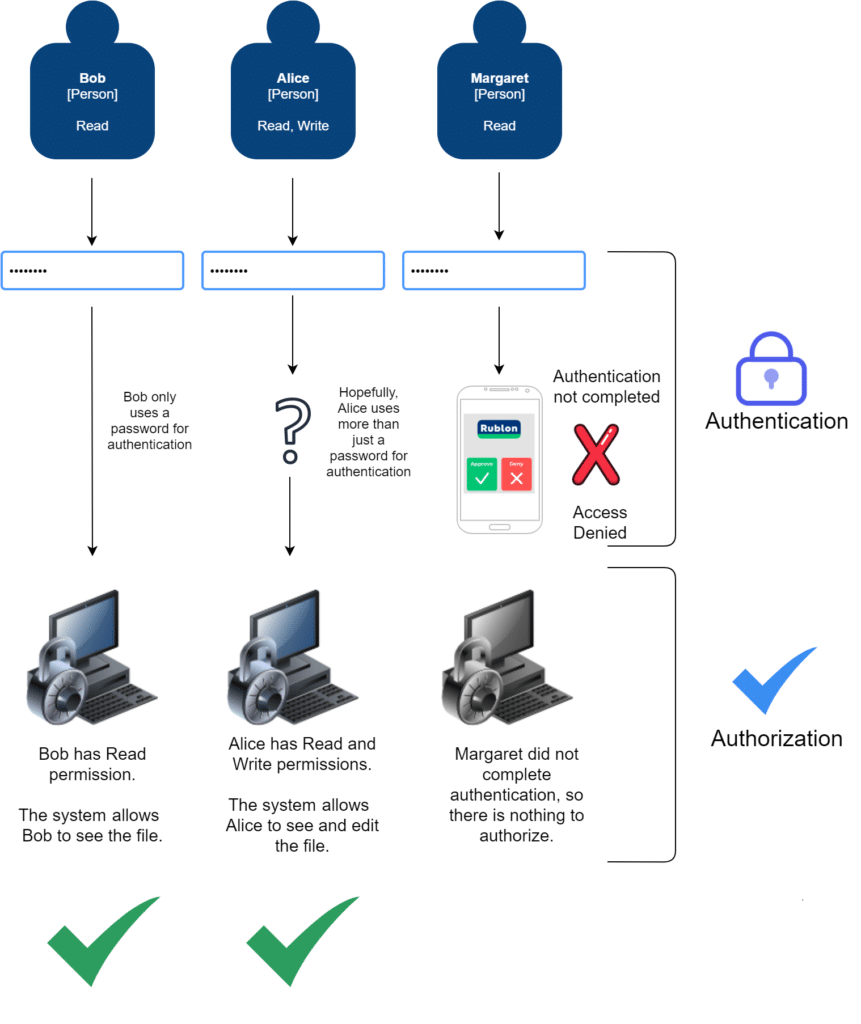
A classified text file is available online. To access the file, you have to log in. Three people have access to the file:
- Bob – user with Read permission
- Margaret – user with Read permission
- Alice – admin with Read and Write permissions
Bob and Margaret are users who can only read the file. Alice is an administrator who can also change the file, e.g., add another paragraph or permanently delete the file.
Let us see what happens when Bob wants to read the file.
- Bob wants to access the classified file
- Bob provides their password
- The security system checks Bob’s password and asserts the password is correct – Authentication
- The security system checks Bob’s permissions. Bob can only read the file, so the system removes Edit and Delete actions from Bob’s user interface – Authorization
- Bob can read the file.
Let us see what happens when Margaret wants to read the file.
- Margaret wants to access the classified file
- Margaret provides their password
- The security system confirms the password is correct – Authentication
- Margaret has another form of authentication enabled on their account. The security system sends a Mobile Push notification to Margaret’s phone. Margaret has to confirm the authentication request to gain access to their account – Authentication
- Margaret does not confirm the authentication request, so the security system denies Margaret’s access – Authentication
The party that tried to log in as Margaret was not Margaret. It was a malicious actor who guessed Margaret’s password. Had Margaret’s account not been protected with another authentication method, the malicious actor would have gained access to Margaret’s account.
IT Example: Ideas to Consider
Although the preceding scenario is just an example, here are some ideas to consider:
- Thanks to two distinct ways of protection, Margaret’s account has not been compromised. The malicious actor had Margaret’s password but did not have Margaret’s smartphone to confirm the authentication request.
- Bob was lucky. Bob protects their account with only a password. If the malicious actor tried to break into Bob’s account and got to know Bob’s password, the malicious actor would have succeeded in gaining access to the classified file.
- We hope that Alice protects their account with with more than just a password. If the malicious actor accessed Alice’s account, they could, for example, permanently delete the file.
- If the file is classified, then it is probably not a good idea to store it online.
Why You Need Authentication
Authentication validates your identity and protects your accounts against unauthorized access, making it the cornerstone of all security systems. The IT example shows that an authentication process that uses something more than just a password can save your account from getting compromised. Always use more than just one factor.
Get Multi-Factor Authentication (MFA)
If username and password are the only way of verifying user identities in your workforce, get Rublon Multi-Factor Authentication (MFA) to safeguard your business.
Multi-Factor Authentication (MFA) ensures the security of your network, users, applications, VPNs, and other technologies. Rublon supports many types of authentication, including biometric authentication (WebAuthn/U2F Security Key) and very secure Mobile Push authentication requests. Rublon integrates with all your services to enable robust authentication and secure you from threats.
Try Rublon for free by starting the 30-Day Trial.