Last updated on March 5, 2026
Multi-Factor Authentication (MFA) is a secure sign-in process that requires at least two independent proofs of identity—for example, a password (something you know) plus a phone (something you have) or a fingerprint (something you are)—to reduce the risk of unauthorized access by hackers.
Multi-Factor Authentication (MFA) is no longer optional. In 2025, stolen credentials remain a leading path into organizations, and ransomware thrives on weak and reused passwords.
This Ultimate MFA Guide will explain everything you need to know about MFA: what it is, why it is essential, how it works, the various authentication methods (from OTP codes to FIDO2 passkeys), best practices for deployment, compliance requirements, and more. By the end, you will understand how MFA can dramatically improve your organization’s security and how to implement it effectively in 2025 and beyond.
Executive Summary: Multi-Factor Authentication (MFA) at a Glance
- What’s MFA: A sign-in that requires at least two independent authentication factors (knowledge, possession, inherence).
- Why It Matters: MFA blocks the most common breach paths (stolen/guessed credentials, ransomware vectors, bot attacks).
- Best Methods Today: Phishing-resistant FIDO2/passkeys for critical access; push with number-matching as a broad baseline; SMS only as a fallback.
- Quick Start: Enforce MFA on remote access, email, user identity providers, and admins. Roll out physical FIDO2 keys or passkeys to privileged accounts; provide backup codes and clear recovery; monitor and iterate.
- Compliance Fit: MFA aligns with GDPR, NIS2, PCI DSS, PSD2, HIPAA, FTC Safeguards, as well as cyber-insurance requirements.
- User Experience: Opt for low-friction methods (push notifications, passkeys), educate users, and maintain self-service options.
- Executive Summary: Multi-Factor Authentication (MFA) at a Glance
- Why Are Passwords Not Enough?
- What is Multi-Factor Authentication (MFA)?
- How Does MFA Work?
- Multi-Factor Authentication (MFA) Methods
- Attacks and Threats That MFA Helps Prevent
- Benefits of Multi-Factor Authentication
- Deploying MFA for Your Organization: Best Practices
- MFA Across Industries
- MFA and Regulatory Compliance
- Common MFA Use Cases
- Real-World Business MFA Deployment Examples
- Common Systems Protected by MFA
- MFA in the Broader Security Landscape
- Final Thoughts: MFA is an Essential Security Control
- Secure Your Infrastructure With MFA — Start Today!
- FAQ
Why Are Passwords Not Enough?
Cybercriminals have never had it so easy when all that protects an account is a single password.
Stolen and weak credentials remain one of the top causes of data breaches.
The Verizon Data Breach Investigations Report (DBIR) is one of the most comprehensive and widely cited cybersecurity studies globally, analyzing tens of thousands of real-world incidents and confirmed breaches each year. Its findings are based on data from law enforcement, public sector agencies, and private organizations, making it a trusted benchmark for understanding threat trends and attacker behavior.
Verizon’s 2025 Data Breach Investigations Report found that stolen credentials were used in 22% of all breaches, making it the most common initial access vector.
The same report pointed out that as many as 88% of basic web application attacks involved the use of stolen credentials.
Verizon’s 2025 Data Breach Investigations Report: 88% of Basic Web App Attack breaches involved the use of stolen credentials, 56% involved brute force (guessed credentials), 51% involved other varieties, while 42% involved backdoor or Command and Control (C2).
The takeaway is clear: relying on passwords alone is dangerously inadequate.
In response to growing threats, organizations are increasingly adopting multi-factor authentication (MFA) as a core component of their security strategy.
MFA adds additional verification steps to the login process so that a password by itself is not enough for access.
Microsoft observed that enabling MFA can block over 99.9% of account compromise attacks.
No surprise, then, that cyber insurers require MFA in order to offer coverage.
In practice, the importance of MFA increases as identity theft threats continue to rise, which is why many organizations explore why multi-factor authentication is important.
Yet despite its proven effectiveness, MFA is not ubiquitous. Many accounts and systems remain perilously unprotected.
But before exploring the barriers to adoption, let’s clarify what MFA is and how it works.
What is Multi-Factor Authentication (MFA)?
Multi-Factor Authentication (MFA) is a type of identity verification that asks a user for at least two distinct authentication factors to decide if a person is who they say they are.
The authentication factors are something you know (e.g., a password or PIN), something you have (e.g., a security key or smartphone), and something you are (e.g., a fingerprint or face).
The key strength of multi-factor authentication is that even if one factor is compromised (e.g., a stolen password), the remaining factor(s) still protect the account. Only when all required factors are verified will access be granted.
Watch: MFA Explained Like You’re 10 as Three Gates to Your Account
This 3-minute story shows MFA as three gates that must all open, so a leaked password alone cannot unlock your account.
Authentication Factors: Knowledge, Possession, Inherence
The three authentication factors refer to the types of evidence a user presents to prove who they are. The classic model includes three categories of authentication factors:
- Something You Know: A knowledge factor, such as a password, PIN, or answer to a security question. This is information that the user knows and can recall.
- Something You Have: A possession factor, meaning a physical device that you own. Possession factors include things like a smartphone with an authenticator app or a hardware security token (e.g., a FIDO2 security key or smart card).
- Something You Are: An inherence factor, which is a biometric characteristic inherent to the user. This could be a fingerprint, face scan, iris scan, or voiceprint.
These three categories are the foundation of MFA. Any authentication method you encounter will fall into one of these groups.

MFA vs. Single-Factor Authentication
In stark contrast to MFA, single-factor authentication (SFA) uses just one authentication factor (for example, a password alone). A familiar example of SFA is the common username + password login.
Single-factor authentication is inherently less secure because a single compromised factor can lead to account takeover.
One advantage multi-factor authentication has over single-factor authentication is that MFA mitigates account takeover attacks by requiring multiple credentials from different factor categories, vastly strengthening identity assurance.
MFA vs. Three- and Two-Factor Authentication
Clarifying the difference between two-factor authentication (2FA) versus multi-factor authentication (MFA) helps avoid confusion.
Essentially, 2FA is a subset of MFA. 2FA refers to the use of exactly two factors to authenticate (no more, no less). MFA is a broader term that means two or more factors. When somebody means exactly three factors, the most precise term would be Three-Factor Authentication (3FA).
Examples:
- Requiring a password and a one-time SMS code is a classic example of 2FA requiring two different factors (knowledge + possession).
- Requiring a smartcard, a PIN, and a fingerprint scan would be 3FA (possession + knowledge + inherence).
- Both of the preceding are also examples of MFA.
- The distinction is mostly in phrasing: if you add an additional factor on top of a password, you have moved beyond single-factor.
MFA vs. Two-Step Verification and Two-Step Authentication
Some providers use the terms “two-step verification (2SV)” and “two-step authentication (2SA)” as analogous to 2FA.
Nevertheless, these terms refer to two sequential steps that are not always two distinct factors.
So what is the difference between 2FA and 2SV?
Let’s take a look at the following examples:
- Entering your password twice
- Using a password and a PIN
- Using a password and a security question
All of the preceding consist of two steps, but still only one factor.
Repeating the knowledge factor twice makes for two-step authentication, but not two-factor authentication. This is because the definition of MFA clearly states that the factors must be distinct, meaning they must come from different factor categories.
Using the same factor twice (like two passwords) does not count as 2FA. True multi-factor implies each step is drawing from a different factor category.
Other Names for MFA
Multi-factor authentication (MFA) is used under various names in literature and business practice. It’s important to understand that all of these terms refer to the same security mechanism: requiring more than one authentication factor during login. Some common synonyms and similar terms include:
- Multi-step verification – emphasizes the subsequent steps that the user must complete.
- Multi-layer verification – similar to multi-step verification, stressing the tiered approach.
- Multi-factor verification – used interchangeably with “multi-factor authentication” in the context of application security.
- Multi-factor login – a popular term among end users.
- Multi-step login – another popular term among end users.
- Multi-factor authorization – a misnomer that confuses authentication with authorization – these are two separate processes that should not be mixed.
All the preceding names refer to the same process of increasing login security by using at least two independent factors: knowledge (password, PIN), possession (phone, hardware key) or biometric feature (fingerprint, face).
How Does MFA Work?
In an MFA-protected system, authentication is no longer a single step of “enter password, gain access.” Instead, it involves multiple sequential steps, each verifying a different factor. The process can be summarized as follows:
MFA Example Flow
1. Initial login attempt: The user begins to log in by providing the first factor, usually a password.
2. Verification of first factor: The system checks the first credential (e.g., verifies the password against what’s on record).
- If this initial factor is incorrect, access is denied (just as it would be in a single-factor scenario).
- If it is correct, the process moves on to the next step.
3. Prompt for second factor: Since MFA is enabled, the user must now complete another form of verification. The system will prompt for a second factor, which is typically something the user has or is.
This could be done in various ways, depending on what methods are set up, e.g., sending a push notification to the user’s device or asking them to insert a FIDO2 security key.
4. Verification of second factor: The user performs the required action (taps “Approve” on a push notification opened in a phone app, types the 6-digit code from their token, etc.). The system verifies this second factor.
- If it checks out and no additional factors are required, the user is successfully authenticated and granted access.
- If the second factor fails (or is not provided), the login is denied even though the password was correct. This is the critical protection that stops attackers who have a stolen password but not the second factor.
5. Additional factors (if applicable): If the system requires three factors, steps 3–4 will repeat for that extra factor. For highly sensitive systems, you might see a third factor like a biometric scan. Each factor adds another independent verification layer.
To make this more concrete, let’s walk through a typical two-factor authentication (2FA) scenario and then a three-factor authentication (3FA) scenario.
Two-Factor Authentication (2FA) – Example Scenario
Imagine a user, Bob, who is signing in to his work application, which is protected by Two-Factor Authentication (2FA). The two factors Bob must use are (1) his password and (2) a mobile push notification confirmation (via an authenticator app on his phone):
1. Password (Knowledge Factor): Bob goes to sign in and enters his username and password (or PIN) as usual. This is the first factor (something he knows).
2. Password Verified: The system checks Bob’s password. It is correct, but now, instead of immediately logging him in, the system requires the second factor.
3. Second Factor Prompt: Bob is prompted to complete a second step. At this stage, the system can show available second-factor methods. If Bob has pre-enrolled his smartphone for push notifications, this method can be selected automatically as well.
4. Push Notification (Possession Factor): A login approval request (“Are you trying to sign in?”) is sent to Bob’s smartphone via the authenticator app. This is something Bob has – his physical phone serving as the possession factor.
5. User Approval: Bob sees the push notification on his phone and taps “Approve”.
6. Access Granted: The system confirms Bob’s identity and grants access to the application.
Result
Bob successfully logged in using two factors: knowledge (password) and possession (phone). An attacker who somehow obtained Bob’s password would still be thwarted at step 3. To impersonate Bob, the attacker would need not only Bob’s password but also access to Bob’s mobile device.
In this way, 2FA greatly improves security. Even if one factor is compromised, the chances of an attacker compromising a second, independent factor at the same time are extremely low.
For instance, stealing Bob’s password and also stealing/cloning/gaining remote access to his phone is far more difficult than just stealing the password. The factors come from different categories, so it is more difficult to get both factors using a single attack vector.
Three-Factor Authentication (3FA) – Example Scenario
Now let’s imagine a high-security scenario with three factors. For example, Alice is logging into a sensitive system that requires Three-Factor Authentication (3FA): a password, plus a hardware security key, plus a biometric. Here’s how it might play out:
1. Password (Knowledge): Alice enters her username and password. (First factor, something she knows.)
2. Password Verified: The password is correct. The system now asks for additional verification.
3. Security Key (Possession): Alice is prompted to use her physical FIDO2 security key (which in this case is a USB device with biometric capability, such as a YubiKey Bio). She inserts the security key into her computer’s USB port. The possession of this key serves as the second factor (something she has).
4. Biometric (Inherence): The security key requires Alice to provide a biometric proof. In this case, to scan her fingerprint on the security key’s built-in sensor. This is the third factor (something she is). Alice scans her fingerprint, which the key verifies against the enrolled biometric template.
5. Access Granted: Only after all three factors (password, security key, and fingerprint) have been provided and verified does Alice gain access to her account. If any factor had failed or been missing, she would be denied access.
Result
YubiKey Bio qualifies as 2FA under NIST SP 800-63B because it requires possession of the physical key and user verification (biometric or PIN) to unlock the private key stored on the device. NIST explicitly allows multi-factor authenticators that require two factors in a single authentication event (e.g., a cryptographic device with an integrated biometric sensor).
This 3FA example demonstrates the layered security of MFA. An attacker would need to defeat three independent checks: know Alice’s password, steal or duplicate her hardware key, and forge her fingerprint. Compromising one or even two of those factors is not sufficient without the third.
Multi-Factor Authentication (MFA) Methods
Each method offers unique strengths and trade-offs, as outlined in our article on MFA & 2FA authentication methods, their pros, cons, and ideal use cases.
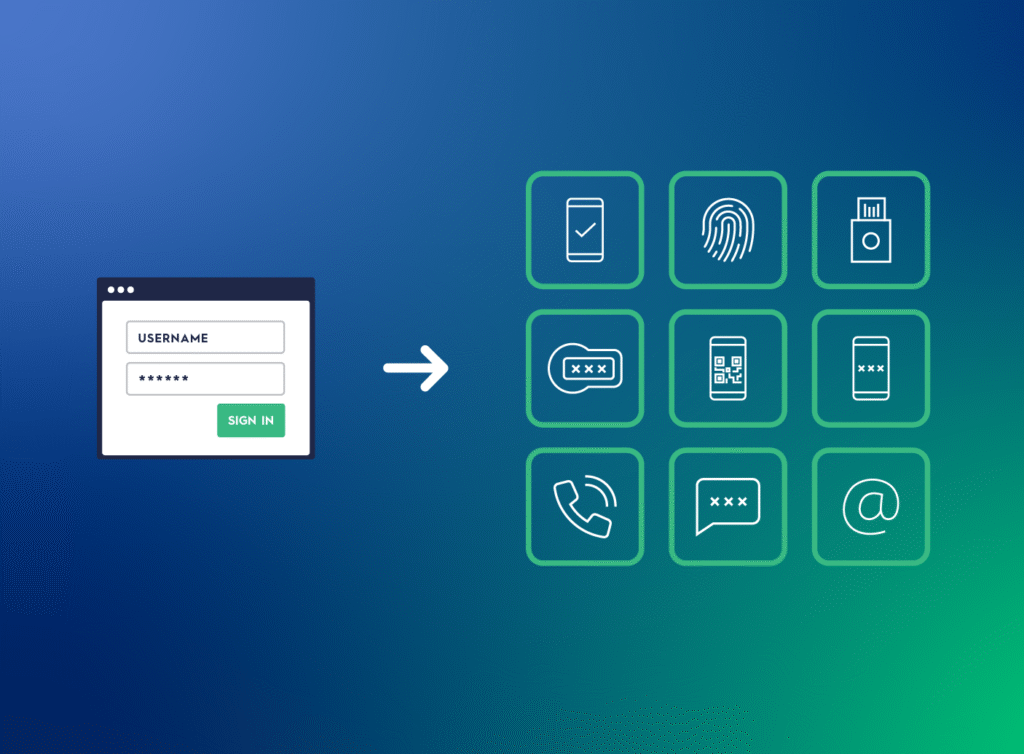
The following is a condensed summary of common MFA methods.
SMS One-Time Passcodes (OTP)
SMS One-Time Passcodes (OTP) are temporary numeric codes sent via SMS to the user’s mobile device and entered during login to confirm identity.
Authenticator App TOTP Codes
Authenticator App TOTP Codes are time-based one-time passcodes generated by mobile apps like Google Authenticator or Rublon Authenticator.
Hardware OTP Tokens
Hardware OTP Tokens are physical devices that display rotating one-time codes without needing an internet connection.
Magic Links via Email or SMS
Magic Links / Email or SMS Links are single-use authentication links sent via email or SMS that log the user in upon clicking.
Push Notifications
Push Notifications prompt users on their registered mobile devices to approve or deny a login attempt with a single tap.
Phone Call
Phone Call authentication delivers a one-time code through a voice call to the user’s phone number.
QR Code–Based Authentication
QR Code–Based Authentication requires the user to scan a QR code using an authorized mobile app to verify the login.
YubiKey OTP
YubiKey OTP generates one-time passcodes through a YubiKey hardware key.
FIDO U2F / FIDO2 Security Keys
FIDO U2F / FIDO2 Security Keys are physical authenticators that enable phishing-resistant authentication.
Passkeys (FIDO2 Passwordless)
Passkeys (FIDO2 Passwordless) are phishing-resistant credentials based on the FIDO2 standard that can be used in passwordless authentication or as a factor in multi-factor authentication.
Biometrics
Biometrics use a person’s unique physical traits (like a fingerprint or face) to verify their identity.
Smart Cards
Smart Cards are chip-enabled cards that provide certificate-based authentication in enterprise environments.
Backup Codes
Backup Codes are static, pre-generated recovery codes that users can use when other authentication methods are unavailable.
MFA Method Table
| Method | Typical Use Cases | Key Risks and Notes | Recommended Stance |
|---|---|---|---|
| SMS One-Time Passcodes (OTP) | Consumer sites; “last-resort” fallback | Interception/SIM-swap; weakest mainstream factor | Use only as backup; phase out where possible |
| Authenticator App TOTP Codes | Consumer & enterprise 2FA (VPNs, internal apps, gateways); offline auth | App install required; add app PIN/biometric where possible | Good baseline; upgrade critical apps to phishing-resistant methods where possible |
| Hardware OTP tokens | No-phone environments; regulated sites; legacy banking/enterprise; offline auth | Cost/logistics; replacement/expiry handling | Declining; consider mobile apps or FIDO2 keys; keep only where phones are prohibited |
| Magic links via Email or SMS | Legacy/fallback; recovery when user loses device | As strong as mailbox/SMS; delays; shares SMS risks; highly phishable | Better than nothing; treat as temporary/backup and protect email with MFA |
| Push notifications | Broad consumer/enterprise sign-ins | Can be abused via fatigue; use number matching and biometric unlock | Use anti-fatigue controls; prefer FIDO2 for high-risk apps |
| Phone Call | Offices with landlines | Prone to social engineering; share PSTN weaknesses | Backup only; not for sensitive workflows |
| QR code–based authentication | Web & app logins where scanning a QR code is convenient | Security depends on the channel and app used | Convenient but not phishing-resistant |
| YubiKey OTP | YubiKey deployments needing OTP compatibility | Shares OTP phishing risk; device logistics | Prefer FIDO2 on the same key; keep OTP for compatibility only |
| FIDO U2F / FIDO2 Security Keys | High-value accounts, admins, privileged accounts | Best phishing resistance | Primary for sensitive accounts; teach users key handling |
| Passkeys (FIDO2 passwordless) | Passwordless consumer & workforce login | Ecosystem & recovery considerations; educate users | Future-proof primary; allow multiple passkeys + cloud synchronization |
| Biometrics (as device unlock) | Local device unlock | Treat as local unlock, not a separate factor | Great user experience when paired with FIDO (e.g., Passwordless Windows Hello MFA) |
| Smart cards | Gov/finance; device login; signatures; offline auth | PKI complexity; card issuance logistics | Use in PKI-enabled environments |
| Backup codes | Emergency access if a device is lost | Must be stored securely; long-lived risk if exposed | Offer to all users; limit count & rotate; monitor use |
Attacks and Threats That MFA Helps Prevent
Multi-factor authentication (MFA) breaks the attack chain for many common intrusion techniques by requiring more than one factor.
With MFA enabled, malicious actors have to either target the MFA mechanism itself or find a completely different attack path (like exploiting software vulnerabilities or insider threats).
Even when attackers do attempt to bypass MFA (for instance, some have tried MFA fatigue attacks by sending repeated push requests, hoping a user will eventually accept out of annoyance), these are much more involved and noticeable than simply stealing a password.
It’s often easier for attackers to move on to a weaker target than to spend time and resources finding ways around MFA. This is why broad adoption of MFA is so critical to raising the security baseline of the whole organization.
Let’s take a look at the key categories of attacks that MFA helps defend against.
Password Phishing
Phishing is when an attacker tricks a user into revealing credentials (often by impersonating a legitimate login page or sending a fake email with a login link).
MFA is highly effective against password phishing because even if the user’s password is stolen, the attacker usually cannot get past the second factor.
For instance, if Bob fell for a phishing email and gave away his password, the attacker still could not log in to Bob’s account without Bob’s phone or security key.
In practice, MFA stops the vast majority of phishing-based account takeovers.
Nevertheless, attackers may also try to phish the second factor. For example, by prompting the user to enter their OTP code on a fake website.
This is where phishing-resistant multi-factor authentication methods like FIDO2 security keys come into play.
Multi-factor authentication is a great way to mitigate password phishing attacks, while phishing-resistant MFA helps thwart any credential phishing attacks.
Verizon’s 2025 Data Breach Investigations Report found that 22% of breaches had credential abuse as the initial access vector. 20% of breaches started from the exploitation of vulnerabilities, while 16% began with phishing.
Credential Stuffing & Password Reuse Attacks
Credential stuffing and password reuse are attacks where criminals take large lists of known breached username/password pairs and try them on other services, betting that people reuse passwords.
Without MFA, these attacks result in many accounts being compromised on various websites.
With MFA enabled, even if the password works, the attacker is halted because they do not have the second factor.
Stolen credentials from one site cannot be leveraged to breach another site if the second site has MFA on the account.
MFA significantly cuts off the value of big password breaches and protects users who (despite warnings) reuse the same passwords across multiple websites.
Brute Force and Guessing Attacks
Brute-force and dictionary attacks try to guess a password randomly or use common credential lists.
Multi-factor authentication (MFA) ensures that the password alone is not enough to gain access.
The attacker would also need to somehow guess or obtain the second factor in the moment, which is difficult and impractical for hackers.
Some attackers attempt password spraying (trying common passwords like “Winter2023!” across many accounts). Even if they hit the jackpot on the password, they are stopped short by MFA. Thus, MFA prevents these guessing attacks from leading to a breach.
Keylogging and Malware-Based Credential Theft
Suppose malware on a user’s PC records their keystrokes or otherwise harvests credentials (some malware even finds stored passwords).
Normally, that would give an attacker the keys to the kingdom. But with MFA, those stolen credentials alone are insufficient.
A keylogger might steal Alice’s VPN password, but when the attacker tries to use it, they will be prompted for the second factor, which they cannot provide.
MFA limits the damage malware can do. While MFA is not a full safeguard (malware can do other harm), it helps ensure that a malware infection on one device does not automatically lead to the attacker pivoting into the user’s accounts.
Man-in-the-Middle (MitM), Adversary-in-the-Middle, and Session Hijacking Attacks
In a classic Man-in-the-Middle (MitM) scenario, an attacker intercepts communication between a user and a service (often via phishing sites or compromised networks), potentially stealing credentials or session cookies.
Modern phishing-resistant MFA (like FIDO2/WebAuthn security keys) is specifically designed to detect the legitimate domain, so if a MitM tries to relay the authentication, the security key will refuse to work on the imposter site.
Phishing-resistant MFA can also thwart advanced phishing attacks like adversary-in-the-middle.
Ransomware Attacks
Breaches that lead to ransomware often start with attackers using stolen or weak credentials against exposed remote access points (RDP, VPN, remote admin tools).
Enforcing MFA on all remote access blocks this single-secret path and prevents many intrusions before encryption can begin.
As the U.S. government’s lead agency for cybersecurity and infrastructure protection, the Cybersecurity and Infrastructure Security Agency (CISA) provides authoritative guidance on defending against digital threats, including ransomware.
CISA’s #StopRansomware Guide tells defenders to apply multi-factor authentication (MFA) to RDP and to implement MFA on all VPN connections, while joint CISA–FBI ransomware advisories instruct organizations to require multi-factor authentication for remote access to OT and IT networks.
According to Verizon’s 2025 Data Breach Investigations Report, ransomware was present in 44% of all breaches. While large organizations saw ransomware in 39% of cases, small and medium-sized businesses (SMBs) were hit hardest, with ransomware involved in a staggering 88% of breaches, highlighting a growing disparity in cyber resilience across organization sizes.
Remote Access Exploits
A lot of breaches start with attackers exploiting remote access points like RDP (Remote Desktop Protocol) or VPNs using stolen credentials.
By enforcing MFA on all remote access, organizations can prevent attackers from leveraging stolen passwords to get into the network.
Even if an attacker finds a valid username/password for an RDP server, they cannot get past the MFA prompt on login, effectively stopping many intrusions cold.
Business Email Compromise
Attackers frequently hijack mailboxes to launch invoice fraud, payroll redirection, or internal spear-phishing. This is called Business Email Compromise (BEC).
Enforcing MFA on email and SSO portals cuts off the single-password path, preventing many mailbox takeovers that drive BEC.
Benefits of Multi-Factor Authentication
Deploying multi-factor authentication yields significant security and business benefits. The primary benefit is the enhanced security against account compromise. But there are several other compelling advantages to MFA.
Here are some of the key benefits organizations and users gain by using multi-factor authentication.
1. Greatly Reduced Account Compromise Risk
MFA drastically lowers the probability of unauthorized access. By requiring multiple proofs of identity, MFA addresses the root cause of so many breaches (stolen or weak credentials). Even if one factor (like a password) is guessed or stolen, an attacker is unlikely to have the second factor.
Google found that even a relatively weak form of multi-factor authentication—an SMS code sent to a phone—was remarkably effective, blocking 100% of automated bots, 96% of bulk phishing attacks, and 76% of targeted attacks. A more secure alternative, on-device prompts (Google’s push notifications), performed even better, stopping 100% of automated bots, 99% of bulk phishing, and 90% of targeted attacks. Security keys stood out as the most robust defense, offering near-100% protection across all attack types, including automated bots, bulk phishing, and sophisticated targeted attacks.
In essence, MFA turns what would have been a simple account takeover with a leaked password into a failed hacking attempt, where the attacker is stopped short. This mitigates a huge range of threats (phishing, credential stuffing, keylogging, etc.) that would otherwise easily succeed against password-only accounts. With more factors, the security increases further: two factors are good, three are even better (though two factors are usually sufficient for most cases).
The effectiveness of second-factor authentication varies. This study by Google, UCSD, and NYU (2019) highlights how phishing-resistant methods—especially security keys—offer near-total protection against account hijacking, outperforming SMS codes and push notifications.
2. Improved Overall Authentication Security
MFA adds critical depth to your defenses, making your authentication process resilient to a broad spectrum of attack techniques.
Requiring MFA inherently forces the use of at least one stronger authentication factor beyond just knowledge. Possession factors and inherence factors are harder to compromise at scale.
For example, a hardware key cannot be remotely hacked in the same way a password can, and a fingerprint required to unlock the key cannot be phished via email. MFA introduces stronger factors and thus elevates the security posture of your authentication system. It aligns with modern approaches like Zero Trust, where trust is continuously verified. Even if attackers breach one layer, the additional layers of MFA harden the system. This layered approach is far more robust than single-factor authentication.
3. Protection Against Fraud and Data Breaches
Using MFA to secure accounts helps organizations actively prevent data breaches and financial fraud.
Many high-profile data breaches and business email compromise incidents could have been prevented (or contained) if MFA had been in place for the targeted accounts.
For businesses, MFA means lower risk of financial losses, legal liabilities, and reputational damage from an incident.
According to the FBI’s Internet Crime Complaint Center (IC3), reported losses from internet crime in the U.S. surged from $12.5 billion in 2023 to $16.6 billion in 2024, a staggering 33% increase. The rise was fueled by investment scams, business email compromise, and tech support fraud, underscoring the growing financial impact of cyber threats on individuals and organizations.
Deploying MFA also benefits users. Even if they slip up and fall for a phishing email, that mistake alone will not immediately result in their data or money being stolen, thanks to the safety net of MFA.
In sectors like banking, MFA has already proven effective: consider that ATM withdrawals have long required two factors (the card + PIN), dramatically reducing ATM fraud compared to if only one factor were required. Applying the same principle to IT systems helps prevent unauthorized fund transfers and protects sensitive data from compromise, making MFA a cornerstone of modern digital security.

4. Increased User Trust and Confidence
Implementing MFA sends a strong signal to users, customers, and partners that you take security seriously. Savvy users are aware of the importance of MFA, and many will not trust a service that does not offer it.
Deploying multi-factor authentication reflects a proactive approach to account security, fostering greater user confidence. End-users feel safer knowing there’s an extra safeguard on their login.
MFA can become a selling point and a competitive advantage. Conversely, a company that does not use MFA may be seen as negligent and outdated.
In some industries, not using MFA could even damage your reputation. For instance, a fintech or healthcare provider that does not use multi-step logins might be viewed as not following security best practices.
5. Stronger Identity Assurance and Regulatory Compliance
MFA enhances identity assurance by requiring multiple authentication factors, helping confirm that the user is genuinely who they claim to be. This is crucial for protecting sensitive systems and data since you do not want an attacker masquerading as an authorized user.
Strengthening identity verification helps companies enforce policies that only legitimate, verified users access resources. This benefit ties closely into compliance: many regulations and industry standards now either recommend or mandate MFA.
Over the past few years, MFA has moved from a nice-to-have to a must-have in regulatory frameworks. For example, the new EU NIS2 Directive explicitly requires organizations to use MFA (while ENISA’s NIS2 implementation guidance talks about phishing-resistant MFA).
Even cyber insurance providers now demand MFA usage as a condition of coverage.
Implementing multi-factor authentication (MFA) strengthens an organization’s security posture and helps ensure compliance with regulatory standards, minimizing the risk of fines or legal consequences. It also takes the guesswork out of meeting authentication control mandates.
A good MFA solution will help check the boxes for multiple standards at once. As regulations continue to evolve, MFA is consistently highlighted as a key control for protecting accounts.
Jen Easterly
Director of CISA6. Flexibility: Integration with Modern Security Strategies
Modern MFA solutions are not one-trick ponies. They often come as part of a broader identity and access management (IAM) framework. This means they can integrate with single sign-on (SSO) systems, support adaptive authentication, and provide centralized MFA management for diverse applications.
A well-implemented MFA system provides an organization with flexibility in securing access. For instance, you might enforce MFA at every login for highly sensitive apps, but only once a day for less sensitive ones. You can also configure MFA to challenge users only for unusual logins, e.g., from a new device, location, or at unusual times. Many providers offer access policies to customize these rules.
Good MFA solutions can integrate with directory services (like Active Directory, Entra ID), network VPNs, cloud services, and other systems via standards (RADIUS, LDAP, SAML, etc.). This integration capability means you can extend strong authentication across your entire IT ecosystem, from VPN logins to on-premises server logons to SaaS applications, all under one unified MFA program.
The flexibility and breadth of coverage that a good MFA solution provides ultimately make your security more consistent and easier to manage.
Deploying MFA for Your Organization: Best Practices
Understanding MFA conceptually is one thing. Implementing it across an organization is another challenge.
How to deploy multi-factor authentication (MFA) effectively, with minimal user friction and maximum security gains?
Whether you are a security leader, IT admin, or compliance officer, these best practices will help ensure your MFA rollout is successful.

Patryk Suchorowski
Head of IT Operations at Rublon1. Plan a Phased Rollout – Start with High-Impact Systems
You do not have to turn on MFA everywhere for everyone all at once.
Begin by identifying the most critical systems and accounts that should be protected ASAP.
MFA for privileged access accounts and administrative accounts, remote access entry points (VPN, remote desktop gateways), and key business systems containing sensitive data should be a top priority.
You should enable MFA for your IT administrators and any remote access users first. These accounts are both high-risk and high-value targets.
After that, you can expand MFA to broader employee accounts and additional applications in phases. Starting with critical systems ensures you cover your biggest exposure early, and it also allows you to iron out any kinks on a smaller scale before wider deployment.
Simultaneously, identify any compliance-driven requirements. For example, if a regulation or cyber insurance policy mandates MFA for certain access (such as accessing customer data or finance systems), include those in the initial phase as non-negotiables.
2. Catalog Inventory Applications and Integration Methods
Make a list of all the systems, applications, and services where you plan to enforce MFA. For each, determine the integration method needed.
Some apps might support modern protocols like SAML or OAuth. Others might rely on RADIUS or LDAP. Some might require installing an agent (e.g., for Windows Logon). Cloud services might have their own MFA options or API integration.
Cataloging integration methods will make it clear what technical approaches to use for each system and how the chosen MFA solution supports them.
It’s okay if not every single legacy system can support MFA initially. Note those edge cases and have a plan to address them, e.g., maybe upgrading the system or using a workaround like a jump host with MFA.
Keep the inventory updated as you deploy; it will serve as your checklist and can be expanded as new apps come online.
3. Choose the Right MFA Solution
Selecting the right MFA solution depends on your requirements, most important of which are:
- Coverage (does it support all the apps and protocols you need?)
- Available authentication methods (does it support the authentication methods you want, like push, FIDO2?)
- Ease of use (does it have a convenient user interface and self-service for users?)
- Administration and reporting features (can it give you logs and integrate with SIEM?)
- Cost (is it affordable and cost-efficient, any hidden costs?)
Some organizations leverage the MFA that comes with their primary cloud IdP (like Entra ID’s MFA for Office 365), but many find they need a more unified MFA platform to cover the entire infrastructure of the organization, including on-prem systems, VPNs, etc.
Ensure the solution you pick can integrate with your existing directories (Active Directory, OpenLDAP), and consider if a cloud-based identity solution fits your strategy.
Also, verify the solution meets any compliance criteria you have (for instance, FIPS 140-2 validation if required, or specific data residency needs).
4. Provide a Variety of Secure Authentication Methods
When rolling out MFA to a diverse user base, one size may not fit all for the second factor.
Aim to enable multiple MFA methods to accommodate users, but while doing so, enforce that only secure methods are used for high-risk areas.
For example, you might allow users to choose between push notifications and FIDO2 hardware keys as their second factor. However, you might decide to disable less secure methods like SMS codes for certain user groups (like admins) or altogether if possible.
Strike a balance: offering many authentication options can improve adoption (someone without a smartphone could use a YubiKey, for instance), but too many options could complicate support.
At a minimum, consider having at least one backup method available, e.g., if the primary is push but the user’s phone is offline, they could use a code from the app.
Make sure whatever methods you allow are manageable and that users can easily enroll them. Importantly, for extremely sensitive systems and privileged accounts, consider mandating the most secure methods (such as only allowing FIDO2 security keys or hardware tokens for domain admins, etc.).
The ability to configure policies per application and group is very useful (many MFA solutions let you do this).
5. Pick a User Enrollment Strategy
The success of an MFA deployment hinges on user adoption. So, you have to plan out how users will be enrolled in MFA. Will you have a self-enrollment period where users are prompted to set up their second factor at their next login? Or will administrators pre-enroll user devices?
Provide clear, step-by-step instructions for enrollment. It is a good idea to start with a pilot group (perhaps the IT department or a tech-savvy set of users) to quickly work out any issues, then phase in other groups.
Provide support during this deployment phase. The help desk should be ready to assist users who have trouble enrolling or who do not have a compatible phone. The initial rollout might even be opt-in for some period (for example, make MFA optional but recommended, then later switch to mandatory once most have enrolled).
Also consider enrollment for new hires. Build user-side MFA setup into onboarding so every new user enrolls from day one.
6. Communicate and Educate End Users
One of the biggest blockers to MFA adoption is user resistance and confusion.
It’s crucial to communicate clearly to users why MFA is being deployed, how it protects them and the organization, and what they need to do. Emphasize that this is a positive security measure that will help prevent breaches and that it’s becoming a standard practice everywhere.
Provide training materials or brief demos on how to use the new MFA system. Address common misconceptions upfront. Reassure users that modern MFA is easy (no, they don’t all need physical tokens – a smartphone will do for most, and no, it won’t constantly spam them with notifications).
If possible, share statistics or anecdotes: e.g., “80% of breaches are due to stolen passwords. MFA prevents this, keeping our company and your personal data safer.”
Also, instruct users on what to do if they get unexpected MFA prompts, since that could indicate an attempted attack (e.g., “if you receive an MFA request you didn’t initiate, deny it and report to IT.”).
User education will not only smooth the rollout but also increase cybersecurity awareness in general. Make sure to communicate how users can get support for MFA (like if they get a new phone, how to re-enroll, etc.).

7. Prepare IT Support and Fallback Options
Set up a process for handling cases where a user cannot use their MFA method.
Examples:
- a user loses their phone
- their hardware token is damaged
- they are in a location with no mobile signal to receive codes
Typical fallback options include:
- providing backup codes (like bypass codes users can use if needed)
- allowing a backup method like a Phone Call
- having help desk verify identity and issue a temporary MFA bypass
You should decide what is appropriate for your environment. Backup codes are a good practice (users can be given a set of one-time codes to keep in a safe place). Administrators should be able to reset MFA for a user or mark an account as temporarily exempt in emergencies, with proper verification. All such actions should be logged for security auditing.
Train your help desk staff about the MFA system so they can assist users who call in confused or locked out. Ideally, the support staff should have a clear runbook: how to verify a user’s identity over the phone if they are locked out, how to issue a temporary pass, and how to reset their MFA settings, etc.
Ensuring support readiness will reduce frustration and help ensure users do not seek workarounds or shortcuts that weaken MFA’s effectiveness.
8. Leverage Access Policies
Most MFA systems allow for policies to reduce user friction without sacrificing security. For example, you can enable “remember this device” for a set number of days so a user logging in from their regular work laptop does not get prompted for MFA every single time.
Enabling a remembered devices policy can significantly enhance the user experience. However, it’s important to strike the right balance. For critical systems, it may be best to disable this feature entirely. But for everyday applications, allowing a device to be remembered for, say, 48 hours can offer convenience without compromising security.
9. Extend MFA Everywhere Feasible (Close the Gaps)
Over time, aim to cover as many access points as possible with MFA.
This includes VPNs, cloud apps, on-premise apps, and legacy systems (which might need an intermediary like an authentication proxy or Windows bridge).
Attackers will look for one VPN account or one legacy app without MFA as their way in. Try to eliminate those gaps.
For systems that truly do not support MFA, consider network-level controls (only allow them to be accessed from certain machines or via jump hosts that are MFA-protected). Document these exceptions and revisit them periodically to see if they can be closed (for example, maybe the vendor will add LDAP support in a future version, etc.).
If your organization uses single sign-on (SSO), integrate multi-factor authentication (MFA) directly into the SSO process. This ensures that all applications federated through SSO inherit MFA protection automatically. As an added benefit, users experience fewer login prompts overall, which reduces friction while still maintaining strong security through MFA at the initial authentication point.
10. Monitor and Refine
Once MFA is rolled out, continue to monitor usage and effectiveness.
Most MFA solutions provide logs and dashboards of authentication attempts. Review these for any unusual patterns. For example, lots of denied MFA prompts could indicate someone’s password is compromised and they are being blocked by MFA. This needs investigation.
Monitoring can also show if users are struggling. For example, multiple failed 2FA attempts may mean that they need training or have a bad device.
Refine your security policies over time. Tighten requirements (e.g., move from allowing SMS to requiring an authenticator app as users get more comfortable) and adjust remember-device durations based on feedback.
Gather input from users and stakeholders after initial deployment. If certain departments have unique needs, address them with policy tweaks.
Keep an eye on evolving threats as well. For example, if “MFA bombing” (attackers spamming push notifications) is observed, you might enable features like number matching in push (where the user has to enter a number displayed on the login screen into their app) or switch some users to more phishing-resistant methods.
Stay updated on your MFA vendor’s new features. They often add enhancements like phishing-resistant modes or easier integrations that you can benefit from.
And of course, continue to promote a culture of security: remind users periodically not to approve unexpected prompts and to keep their authentication devices secure.
MFA Across Industries
Multi-factor authentication is now a security staple in virtually every sector. Different industries face unique threats and compliance pressures, but all benefit from MFA’s added layer of protection.
The most common industries that use multi-factor authentication (MFA) include:
- Financial Services: Banks and investment firms use MFA to secure online banking, trading platforms, and internal systems. The financial sector is a high-profile target for cybercrime, and MFA helps meet strict regulations like PCI DSS, PSD2, and NYDFS cybersecurity rules.
- Healthcare: Hospitals and clinics implement MFA to protect electronic health records (EHR) and patient portals. Given that healthcare organizations store massive amounts of sensitive data, strong authentication is vital to comply with laws like HIPAA that require safeguards against unauthorized access.
- Education: Universities and schools use MFA to secure student information systems, research data, and faculty accounts. Educational institutions increasingly face breaches, so MFA is deployed to defend against unauthorized access to sensitive student and research data.
- Government: Government agencies and contractors adopt MFA to protect confidential citizen data and classified information. Many governments mandate MFA for access to critical systems. The EU’s NIS2 directive encourages strong authentication measures, including MFA, especially for “essential entities” such as public administration bodies.
- Retail: Retailers rely on MFA to secure point-of-sale systems, e-commerce platforms, and customer payment data. With threats like fraud and database breaches, MFA helps prevent account takeover and protects consumers’ personal and financial information.
- Legal & Law Firms: Law firms and legal departments use MFA to guard confidential client files and case management systems. By enforcing MFA on remote access and document portals, the legal industry mitigates the risk of data leaks and demonstrates diligence in protecting client confidentiality.
- Technology Companies: Tech firms and software providers use MFA to secure development environments, developer code repositories, cloud consoles, and admin accounts. Protecting intellectual property and customer data is paramount, so companies in the tech sector embrace MFA alongside other advanced security measures.
Each of these sectors recognizes that a single compromised password can have devastating consequences. By implementing MFA, organizations across industries add a critical security layer to defend their most valuable data and services.

MFA and Regulatory Compliance
MFA has become not just a best practice, but a requirement under many cybersecurity regulations. Around the world, laws and standards increasingly mandate MFA or strongly recommend it as part of access controls. Adopting MFA helps organizations demonstrate compliance and avoid costly penalties. A few prominent examples include:
- Payment Card Industry Data Security Standard (PCI DSS): In the finance and retail sectors, PCI DSS explicitly requires MFA for remote access to cardholder data environments and administrative accounts. Enforcing MFA is essential to prevent breaches of credit card information.
- Health Insurance Portability and Accountability Act (HIPAA): In healthcare, HIPAA compels providers to implement authentication safeguards to protect electronic patient health information. Using MFA is a concrete way to meet this requirement and keep medical data confidential.
- NIS2 Directive: Article 21 of the NIS2 Directive obliges essential and important entities to implement appropriate technical and organizational measures to manage cybersecurity risks. This includes securing supply chain access, internal communication systems, and managing temporary access. Multi-Factor Authentication (MFA) is a foundational technology for fulfilling these requirements by ensuring that only authorized users can access critical systems, strengthening the overall security posture mandated by the directive.
- Digital Operational Resilience Act (DORA): Article 9 of the DORA Regulation mandates that financial entities implement ICT access control policies based on principles like least privilege and need-to-know. To comply, organizations must use “strong authentication mechanisms” to verify user identities, especially for privileged access. Multi-factor authentication (MFA) is the industry standard for strong authentication, providing a critical layer of security to prevent unauthorized access to sensitive financial data and systems, thereby ensuring the operational resilience required by DORA.
- CJIS Security Policy: The FBI’s CJIS Security Policy mandates that U.S. law enforcement and criminal justice agencies implement advanced authentication for all access to Criminal Justice Information (CJI). This includes remote and physical access to systems handling sensitive data. Multi-factor authentication (MFA) is a core requirement under this policy to ensure that only authorized personnel can access these critical systems, protecting data integrity and public safety.
- FTC Safeguards Rule: The FTC Safeguards Rule requires US financial institutions, including non-banking entities like mortgage brokers and payday lenders, to implement robust security programs to protect customer information. A key provision of the rule is the mandatory implementation of Multi-Factor Authentication (MFA) for any individual accessing customer data. This measure is designed to prevent unauthorized access and mitigate the risk of data breaches in the financial sector.
In addition, many cybersecurity insurance providers now require companies to have MFA for remote network access and privileged accounts before granting coverage. Regulatory compliance is a major driver for MFA adoption. But beyond satisfying auditors, the result is stronger security for the organization. Implementing MFA allows businesses to create audit trails and tangible proof that they are taking due care to secure logins, which can significantly simplify compliance reporting and reduce liability in the event of a breach.
Common MFA Use Cases
Organizations deploy MFA across a wide range of scenarios to build a robust security posture. Key use cases include:
- Securing the Remote Workforce: MFA is a cornerstone for enabling a secure remote workforce. It protects critical entry points such as VPN connections, VDI infrastructure, and remote desktop applications. Implementing strong authentication for all remote employee access is not only a best practice but often a prerequisite to satisfy cyber insurance requirements and a vital defense to stop ransomware attacks.
- Strengthening Application and System Security: Organizations deploy MFA to significantly improve application security across their entire portfolio. This includes modern cloud services as well as legacy applications and even custom software built in-house. By securing critical systems like email and integrating security into the Software Development Life Cycle (SDLC), MFA helps prevent account takeover (ATO) and measurably reduces the overall attack surface.
- Securing the Microsoft & Windows Ecosystem: MFA is crucial for protecting the Microsoft environment. This involves deploying passwordless MFA for Windows logins and RDP to protect endpoints. It also extends to identity federation, enabling secure Windows logins for users with Microsoft accounts or even Google Workspace identities. A primary use case is to secure access to Microsoft 365, protecting email, files, and collaboration tools.
- Protecting Data and the Supply Chain: At its core, MFA is about data protection. It is a fundamental control to secure sensitive business data from unauthorized access. This is especially critical when dealing with external parties, where MFA can secure third-party and supplier access. By implementing phishing-resistant MFA for the supply chain, organizations can mitigate one of the most significant modern breach vectors.
- Centralizing Security Management and Visibility: Beyond user-facing security, modern MFA solutions provide significant administrative benefits. A key use case is to centralize MFA management across all integrated applications from a single console. This consolidation provides security teams with much-needed visibility into application access, allowing them to monitor authentications, enforce policies, and respond to threats more effectively.
The scenarios listed above are just a few examples that highlight MFA’s versatility. Essentially, any security-critical login or transaction can and should be reinforced with multi-factor authentication. When MFA is aligned with specific workflows, organizations gain stronger protection against both external and internal threats. Explore more real-world MFA use cases to see how strong authentication can protect every part of your IT infrastructure.
Real-World Business MFA Deployment Examples
The following real-life deployment examples illustrate how MFA makes a difference in practice. Below are a few case studies of MFA deployments, showing the motivation and outcomes:
- Karczew Cooperative Bank: This local bank in Poland rapidly rolled out Rublon MFA for all employees to secure VPN access and integrate with Active Directory. By using push-based three-factor authentication (3FA) for remote logins, the bank gained full compliance with new financial regulations (DORA, NIS2, GDPR) while protecting customer data against phishing and fraud attempts.
- U.S. Department of Agriculture (USDA): Faced with users who couldn’t use the government’s standard smart ID cards, USDA turned to FIDO2 security keys as a phishing-resistant MFA solution. Approximately 40,000 USDA employees now authenticate with FIDO-based MFA, allowing secure access to systems without relying on passwords. Deploying FIDO-based MFA eliminated the risks of credential phishing for those users and met the Federal Zero Trust mandate for strong authentication.
- Google: The tech giant famously required 85,000+ of its employees to use MFA based on physical security keys for internal logins. Not a single successful phishing attack has been reported against Google’s staff since adopting hardware MFA. This case demonstrates the effectiveness of phishing-resistant MFA in a large enterprise.
Each of these examples underscores how MFA can be rolled out in different contexts, from small businesses to global enterprises, and from off-the-shelf solutions like mobile apps to cutting-edge methods like FIDO2 keys. The outcomes are consistently positive: better security, improved compliance, and peace of mind that a stolen password alone will not compromise the organization.
Common Systems Protected by MFA
What do businesses protect with MFA most often?
Businesses most often use MFA to shield the critical points where a breach would be most damaging. These include remote access portals, employee laptops/servers, identity systems, and cloud services.
Deploying multi-factor authentication on these common targets helps organizations drastically reduce their attack surface. MFA solutions like Rublon MFA for Windows Logon and RDP make it straightforward to implement this protection without disrupting users. The result is a far stronger defense-in-depth: even if one layer (the password) fails, the attacker still cannot get in without a second factor that they do not possess.
In practice, organizations apply multi-factor authentication to a wide array of systems and entry points. MFA solutions today can cover virtually every access point in an IT environment. Some of the key systems and resources commonly protected by multi-factor login include:
- Remote access gateways: VPN connections and remote desktop sessions (e.g., Microsoft Remote Desktop and RemoteApp) are secured with MFA to stop unauthorized network entry. Even if an attacker steals a VPN password, they’ll be unable to pass the additional verification step.
- User workstations and servers: MFA is added to operating system logins on both Windows and Linux servers. This means users must approve a second factor when signing into their computers, which greatly reduces the risk from lost or stolen credentials. (Even standalone Windows machines in workgroup mode can be protected with MFA via lightweight connectors.)
- Directory and authentication systems: Organizations integrate MFA with their identity infrastructure. For example, they add MFA on top of Microsoft Active Directory domain logins, LDAP-based systems, or RADIUS authentication flows. By plugging MFA into these core authentication services, businesses enforce strong security across all applications that rely on them. Similarly, SAML single sign-on providers can have MFA layered on, ensuring federated logins are verified with a second factor.
- Cloud platforms and email services: Many companies protect their cloud accounts and SaaS applications using MFA. A common step is enabling MFA for Microsoft 365 and Azure AD (now known as Entra ID) to secure email, OneDrive, and other Office 365 apps. Likewise, administrators enable MFA for Amazon WorkSpaces, AWS consoles, and other cloud platforms. Enabling MFA on cloud identity accounts ensures that even if a user’s password is phished, attackers cannot access cloud resources without a second factor like a trusted device or biometric.
MFA in the Broader Security Landscape
Multi-factor authentication is a cornerstone of modern cybersecurity, but it does not operate in a vacuum. It works best as part of a layered, comprehensive security strategy.
A Pillar of Zero Trust and Layered Defense
MFA complements strong password management and is a critical component of Identity and Access Management (IAM). It is a key pillar of the Zero Trust security model, where trust is never assumed and verification is always required. To be most effective, MFA should also be paired with robust monitoring. Analyzing failed authentication attempts can help detect targeted attacks and other security issues, turning your MFA system into a valuable source of threat intelligence.
The Future of Authentication
Looking ahead, the trend is toward making MFA even more secure and user-friendly.
Phishing-resistant MFA using FIDO2 security keys and passkeys is gaining widespread adoption. Its goal is to eventually reduce our dependence on passwords. In the future, continuous and behavior-based authentication may augment traditional MFA, offering an extra layer of verification.
User Impact and Adoption
While adding MFA does introduce an extra login step, most users find it reasonable given the security benefits. The minor inconvenience is insignificant compared to the potential fallout of a breach. With a thoughtful deployment using features like remembered devices and SSO integration, the process can be made nearly seamless for users. A positive side effect is that employees often adopt 2FA in their personal lives, improving their overall cyber hygiene.
Final Thoughts: MFA is an Essential Security Control
Any organization not using MFA for its critical accounts is taking a significant and unnecessary risk.
Implementing MFA is proven to drastically improve security outcomes, making breaches far less likely and less severe.
For example, Microsoft has stated that MFA can block over 99.9% of account compromise attacks. Similarly, a joint study by Google, UCSD, and NYU found that even basic SMS-based MFA blocked 96% of bulk phishing attacks, while stronger on-device prompts and security keys blocked 99%.
This data confirms that MFA makes breaches far less likely and severe by adding a critical layer of defense that stolen credentials alone cannot bypass.
Secure Your Infrastructure With MFA — Start Today!
The best time to start is now. Don’t wait for an incident to force your hand. Enable MFA proactively and stay one step ahead of threat actors.
SECURE YOUR ACCESS: It’s never too late to bolster your defenses. Whether through a built-in solution or a third-party service like Rublon MFA, take the step to enable multi-factor authentication on all critical accounts.
FAQ
What is multi‑factor authentication?
It’s a security method that requires at least two independent identity proofs (factors)—such as a password, app-generated code, or biometric scan—which significantly enhances account and data protection.
How do I enable multi‑factor authentication?
In most services, go to your account’s security settings and activate MFA by selecting a method like TOTP app, hardware key, or push notifications. In enterprise environments, centralized systems like Rublon MFA are recommended.
What is multi‑step authentication?
It’s a process where authentication occurs in sequential steps (e.g., entering a password first, then a verification code), but not necessarily using different factors. It’s often used interchangeably with MFA, though they differ technically.
What is a multi‑factor authentication system?
It’s an authentication mechanism that uses multiple components (e.g., password, token, biometric) in a single login process, commonly implemented in both online services and enterprise systems.
Is SMS-based MFA secure?
SMS adds a second authentication step, but it’s vulnerable to SIM-swap and phishing. For critical access, use phishing-resistant FIDO2 security keys & passkeys or push with number matching.
What’s the difference between 2FA and MFA?
2FA uses exactly two authentication factors. MFA is any sign-in with two or more factors (2FA is a subset of MFA).
Are passkeys and FIDO2 the same thing?
FIDO2 is a modern, phishing-resistant authentication standard. Passkeys are a user-friendly form of FIDO2 credentials. In contrast, hardware security keys are devices capable of storing FIDO2 credentials. There are other ways of storing FIDO2 credentials. For example, passkeys can be stored locally on a user’s device, such as a smartphone or laptop, or even synchronized securely across platforms using cloud services like Apple iCloud Keychain or Google Password Manager. This allows users to authenticate seamlessly across multiple devices without relying on external hardware.
Do I still need passwords if I deploy passkeys?
You can go passwordless for apps that support it, but keep break-glass methods and admin procedures. Phase passwords out gradually where supported.
Where should I enable MFA first?
Start with remote access (VPN, RDP), local login to endpoints such as workstations and laptops, email, IdP/SSO, admin accounts, and any system containing regulated or sensitive data.
Will MFA hurt usability?
Modern options (push, passkeys) are fast, and most users adapt quickly. Pair rollout with training and self-service for users to make MFA’s impact on usability negligible.
What about offline or no-phone users?
Issue hardware FIDO security keys or OTP tokens. Generate offline codes for emergencies.

