A spoofed communication channel can be a powerful vector of attack. If a malicious actor manages to insert themselves in the middle of communication between a user and a system, then that malicious actor can pretend to be the system and consecutively intercept sensitive data sent by the unsuspecting user. If both authentication factors move data over the same channel, then with enough luck and skill, the malicious actor can break both of them. But there is a solution to this vulnerability.
What Is Out-of-Band Authentication (OOBA)?
Out-of-Band Authentication (OOBA) is a type of authentication that requires two different communication channels.
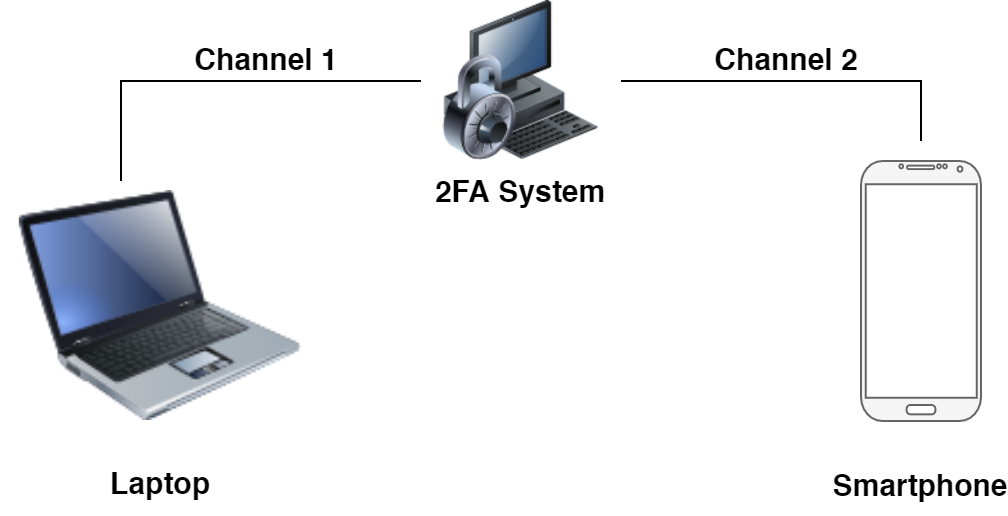
Consider the following example of Two-Factor Authentication (2FA):
- Bob logs in to an application on their laptop.
- Bob provides their login and password.
- The 2FA system confirms that the credentials provided by Bob are correct.
- The 2FA system sends a push notification (e.g., Rublon’s Mobile Push authentication request) to Bob’s mobile device.
- Bob receives a Mobile Push authentication request on their mobile device and approves the request.
- Bob is successfully logged in to the application.
Note the following:
- The communication between Bob’s laptop and the 2FA system (Steps 1-3) is the first channel.
- The communication between Bob’s mobile device and the 2FA system (Steps 4-5) is the second channel.
- The preceding authentication process is OOB Authentication because two different channels of communication were used during authentication. As a result, Bob logged in to their application (Step 6).
Even if a malicious actor manages to insert themselves into the first channel of communication and intercepts Bob’s password, the hacker is thwarted by the push notification sent over another channel.
What Is an Out-of-Band Device?
Out-of-Band Device is an authentication device that establishes an additional channel of communication with a 2FA system to receive an authentication request or another type of out-of-band secret.
The most popular type of out-of-band device is a mobile phone with an authenticator app (e.g, Rublon Authenticator). The authenticator app communicates with a 2FA system over a different channel than the computer the user uses to log in to an application.
Out of Band Authentication Thwarts Man-in-the-Middle Attacks
OOB Authentication is a critical component of a 2FA system that helps combat theft within financial institutions and retail organizations. In a MiTM attack, hackers take over the communication channel between the users’ main device (usually their computer) and the server. They can intercept and potentially read any information sent between the parties. A successful MiTM attack compromises a channel of communication and poses a great danger to the security of user accounts.
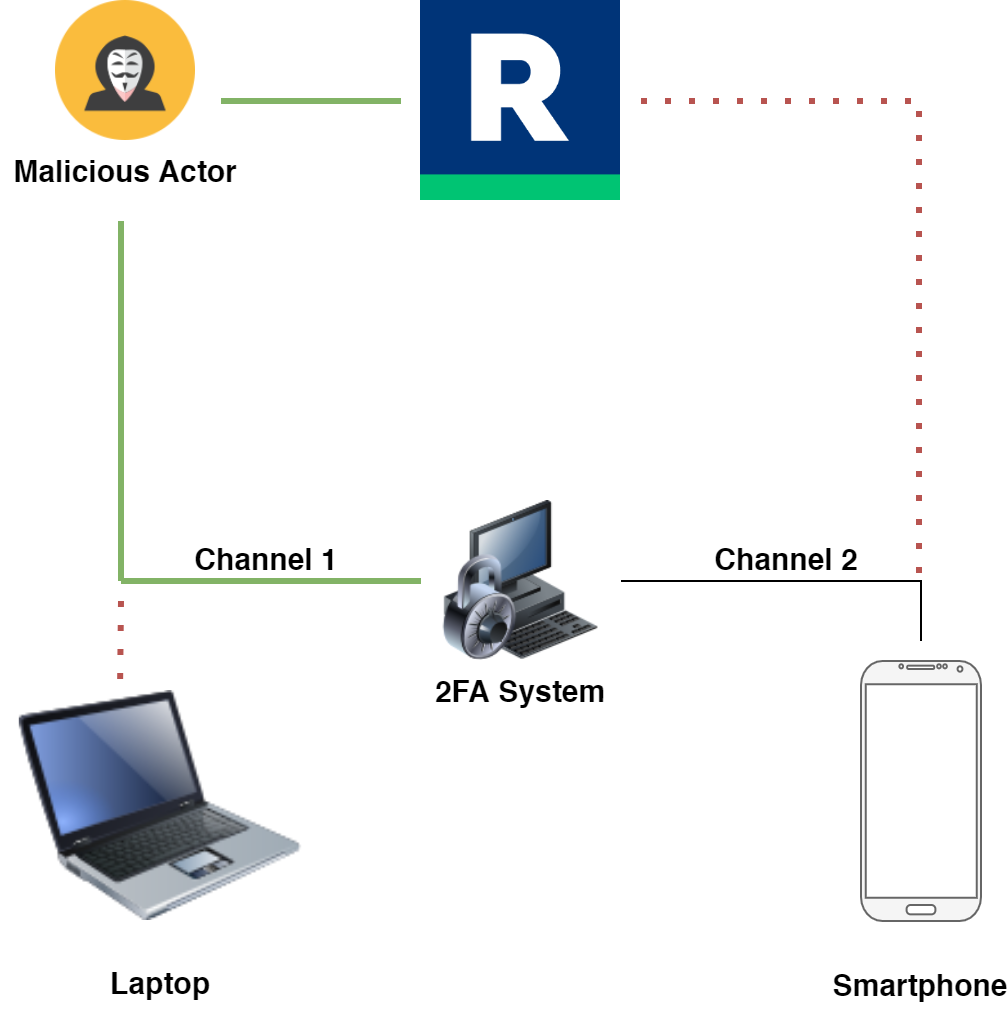
OOB Authentication can help prevent man-in-the-middle attacks by introducing an extra channel of communication between the user’s phone and the 2FA system. OOB makes attacks much harder for hackers because now they need access to both communication channels to successfully break the system.
Rublon Supports OOB Authentication
Rublon Authenticator is compliant with the definition of Out-of-Band Devices in section 5.1.3 of the NIST SP 800-63B Digital Identity Guidelines on Authentication and Lifecycle Management.
Rublon Authenticator allows for easy and secure two-factor authentication on Android and iOS phones. Thanks to the Mobile Push authentication method, users can log in to their VPNs, applications, and services with just one tap.
See for yourself and start a Free 30-Day Trial.