Last updated on March 26, 2024
Two-Step Authentication is an easy concept you can use to make logins to your account more secure. Two-Step Authentication is closely related to Two-Factor Authentication (but it’s not always the same) and requires two sets of credentials instead of just one. Once 2SA is in place, you first type in your password. Then, you provide an authentication code, accept a notification on your phone, plug in a security key, or scan a QR code. With 2SA, both sets of credentials are required to gain access to your account. But why do you need 2SA?
The Old Way: Login and Password
Many people only use one layer of login protection – their password. Protecting your account only with a password raises a serious issue: A hacker only needs to crack the password to gain access to your account.
Passwords are very easy to crack or even guess. What’s more, a hacker does not even have to crack your password. A malicious actor can use one of the millions of passwords that have already been leaked during one of the big data leaks that happen now and then.
Beyond Password
Passwords are not enough to protect your business.
If you do not want to be at the mercy of something as insecure as a password, add another authentication method to your authentication process. You need something that will be more secure than your password and will protect you against most threats associated with passwords.
In a word, you need another login step. You need Two-Step Authentication (2SA).
What Is 2SA (Two-Step Authentication)?
Two-Step Authentication (2SA) is a type of authentication that uses any two authentication factors to decide if a person is who they say they are.
For example, a login process during which the user is asked to provide two passwords is 2-Step Authentication. While using two passwords is only a tad bit more secure than using one password, it already is Two-Step Authentication because you went through two steps when authenticating. You used the Knowledge Factor twice.
Any two authentication factors suffice, including doubles. Imagine that you have a bag full of authentication factors and your friend asks you to pick any two factors. Whatever factors you pick, if you use them during authentication, that’s 2SA.
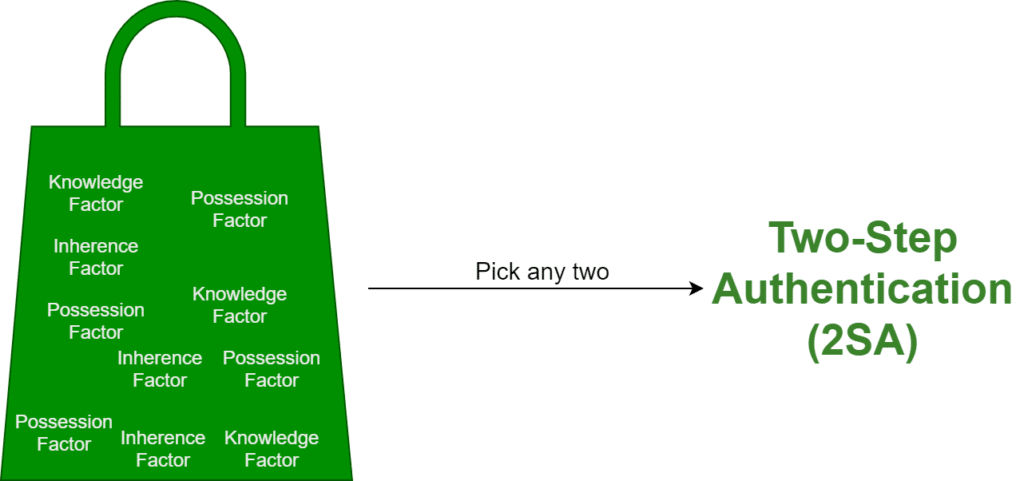
Authentication factors are a theoretical concept. It is much easier to think of 2SA in terms of authentication methods. Authentication methods are real-life implementations of the three authentication factors. For example, a password is an implementation of the Knowledge Factor while the Mobile Push authentication request is an implementation of the Possession Factor. Let us make the preceding image more practical and replace factors with specific authentication methods.

What is Two-Step Verification?
Two-Step Verification (2SV) is a name used interchangeably with Two-Step Authentication (2SA).
Sometimes the number ‘2’ is used instead of the word ‘two’.
All of the following names and abbreviations are acceptable and you can use them to talk about 2SA:
- Two-Step Authentication
- 2-Step Authentication
- 2SA
- Two-Step Verification
- 2SV
Verify It’s You With a Second Step
The second layer of security is crucial for protecting your identity on the web. You can set up 2SA in one of many ways. The additional layer of security may involve:
- Providing an authentication code generated by an authenticator app (e.g., Google Authenticator, Rublon Authenticator)
- Providing an authentication code sent to your phone via SMS
- Plugging in a WebAuthn/U2F Security Key
- Using any other method available on your authenticator app (while Google Authenticator only allows you to use a TOTP authentication code, Rublon Authenticator also offers authentication methods such as Mobile Push and QR Code)
What Happens When You Turn On 2-Step Authentication (2SA)?
To strengthen your protection against threats and mitigate security risks, set up 2-Step Authentication.
But what happens when you set up 2SA? It depends on the additional layer of security you chose during login.
A simplified 2SA process looks as follows:
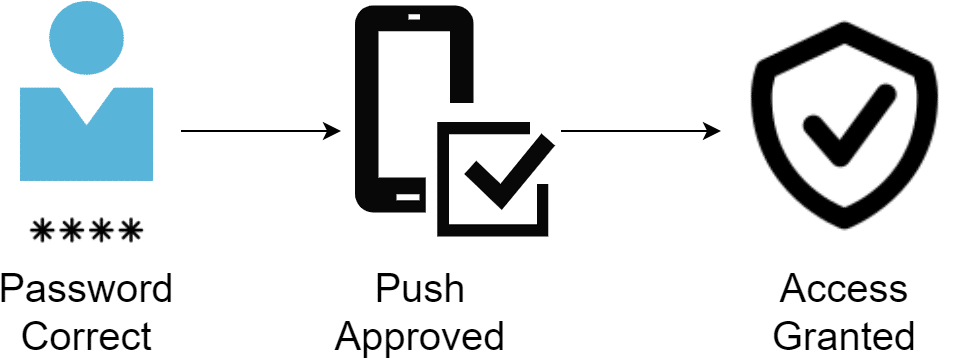
- User provides the password.
- User approves the second authentication step.
- User gains access to the application.
Most 2SA providers allow you to choose which authentication method you want to use. Rublon displays the Rublon Prompt on which you can choose one of the available authentication methods (e.g., Mobile Push). Administrators can decide which methods will be available for users and deactivate methods they see unfit for their organization. Administrators can also apply different authentication methods to different applications to gain better authentication flexibility and security control in their company. Lastly, administrators can also make users automatically receive a Mobile Push authentication request on their phones (Auto Push). While this takes away the choice of the authentication method from the user, it can come in handy with applications that do not have a Graphical User Interface (GUI). Administrators can pick any authentication method as default, not just Mobile Push, although picking Mobile Push is the most common.
But above all, when you turn on 2-Step Authentication, you increase the security of your account and data. 2SA helps you keep the bad guys away.
How Does 2-Step Authentication Work?
The following is a more detailed diagram of Two-Step Authentication using the Mobile Push authentication method:

- Initiate login to your account
- Use your credentials (username and password) – this is the first step
- Choose the authentication method you want to use, e.g., Mobile Push
- Receive a push notification on your mobile device
- Approve or deny the push notification – this is the second step
- Gain access to your account or get denied
The Power of Authenticator App
In the last couple of years, using an authenticator app has become an unwritten standard for authentication.
An authenticator app is a mobile app you install on your mobile device to use during authentication.
In short, mobile applications such as Rublon Authenticator act as Possession Factor and support Out-of-Band Authentication (OOBA).
Users install such apps on their out-of-band devices (phones), which increases security in two ways:
- A device with an installed authenticator app becomes the Possession Factor.
- If we assume the authentication process has been started on a computer, the device with an installed authenticator app uses a separate channel of authentication, which is one of the requirements of Out-of-Band Authentication.
Is 2FA the Same as 2-Step Authentication (2SA)?
Not every 2-Step Authentication (2SA) is Two-Factor Authentication (2FA). When planning a security solution for your workforce, make sure the product of your choice offers Two-Factor Authentication and/or Multi-Factor Authentication.
Two-Factor Authentication is widely considered more secure than Two-Step Authentication and therefore provides better login security for your workforce. Yes, 2SA can be as secure as 2FA, but not always.
Two-Step / Two-Factor Authentication With Rublon
Introduce a security-first approach to your company and put user account security at the top of your risk assessment strategy.
Rublon improves your company’s security posture and gives you peace of mind by introducing robust Multi-Factor Authentication (MFA) enhanced with Access Policies and Single Sing-On.
Try Rublon for free by starting the 30-Day Trial.