Last updated on March 26, 2024
You can now enable MFA for Cisco Meraki Client VPN. Rublon Multi-Factor Authentication (MFA) for Cisco Meraki Client VPN logins allows users to securely access Cisco Meraki Client VPN using Mobile Push, Mobile Passcode (TOTP), and Email Link authentication methods.
How to Enable Multi-Factor Authentication for Cisco Meraki Client VPN?
Check the following step-by-step guide on how to enable Multi-Factor Authentication (MFA) for Cisco Meraki Client VPN:
MFA for Cisco Meraki Client VPN
How Does the Rublon MFA for Cisco Meraki Client VPN Work?
With Rublon MFA for Cisco Meraki Client VPN, you can add an extra security layer to your Cisco Meraki logins.
After setting up the Rublon Authentication Proxy and connecting it to your Cisco Meraki Dashboard, Rublon will require users to complete a second authentication method besides their password. This method can be Email Link, Mobile Passcode (TOTP), or Mobile Push.
This way, hackers cannot access your applications, virtual desktops, and data via Cisco Meraki with just a password. Rublon will block their access if they fail the second authentication step. Users will only be able to access Parallels RAS after passing both authentication steps.
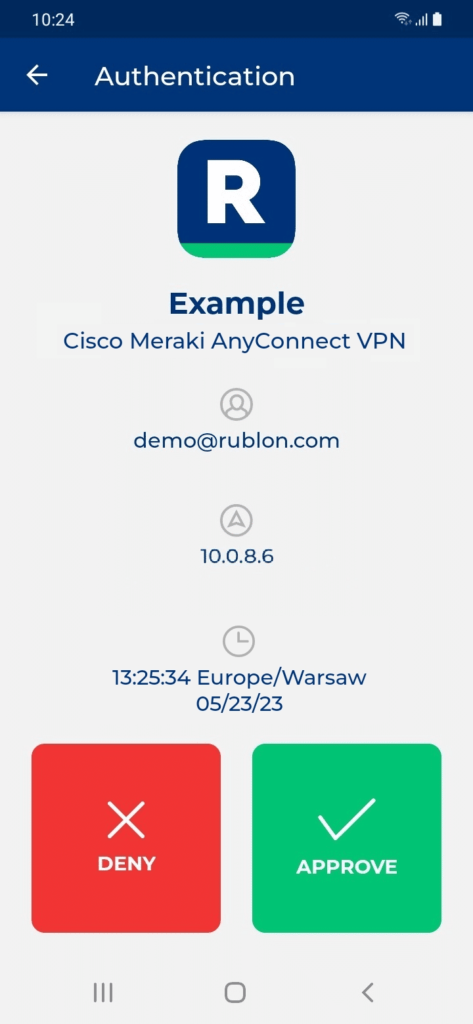
To secure your Cisco Meraki Client VPN users with Rublon MFA, follow these integration instructions: MFA for Cisco Meraki Client VPN.
We Value Your Feedback
At Rublon, we always welcome your suggestions and ideas on how to improve our MFA solution. If you have any feature requests or feedback on the Rublon Admin Console, Rublon Authentication Proxy, or any of our connectors, please contact Rublon Support and share your thoughts.
Try MFA for Free for 30 Days
Protect your Virtual Private Networks (VPNs), cloud applications, and Remote Desktop Services (RDS) with Rublon’s free Multi-Factor Authentication (MFA) using Mobile Push, WebAuthn/U2F Security Key, and more. Start your Free 30-Day Rublon Trial today: