Last updated on December 16, 2025
Active Directory Federation Services (AD FS) Multi-Factor Authentication (MFA) is a security feature that requires users to provide two verification factors when logging in to a VPN, app, or service using Active Directory. The first factor is the user’s Active Directory username and password. The second factor is an additional verification method, such as a Mobile Push or FIDO. Only after completing both factors, the user can access the resource. MFA for AD FS enhances the security of Active Directory and prevents unauthorized access, even if the user’s login credentials are compromised.
Overview
Multi-Factor Authentication (MFA) for Active Directory Federation Services (AD FS) by Rublon is a security solution that protects your AD FS logins with an additional verification factor. You can enable MFA for AD FS by installing a dedicated connector on your AD FS server.
With Rublon MFA for AD Federation Services, users need to provide two verification factors to log in. The first factor is the Active Directory username and password. The second factor is an extra verification method, such as Mobile Push or Email Link. Rublon will block access if users fail to complete the second factor, preventing unauthorized access.
Rublon MFA for AD FS supports the following operating systems:
- Windows Server 2012 R2
- Windows Server 2016
- Windows Server 2019
- Windows Server 2022
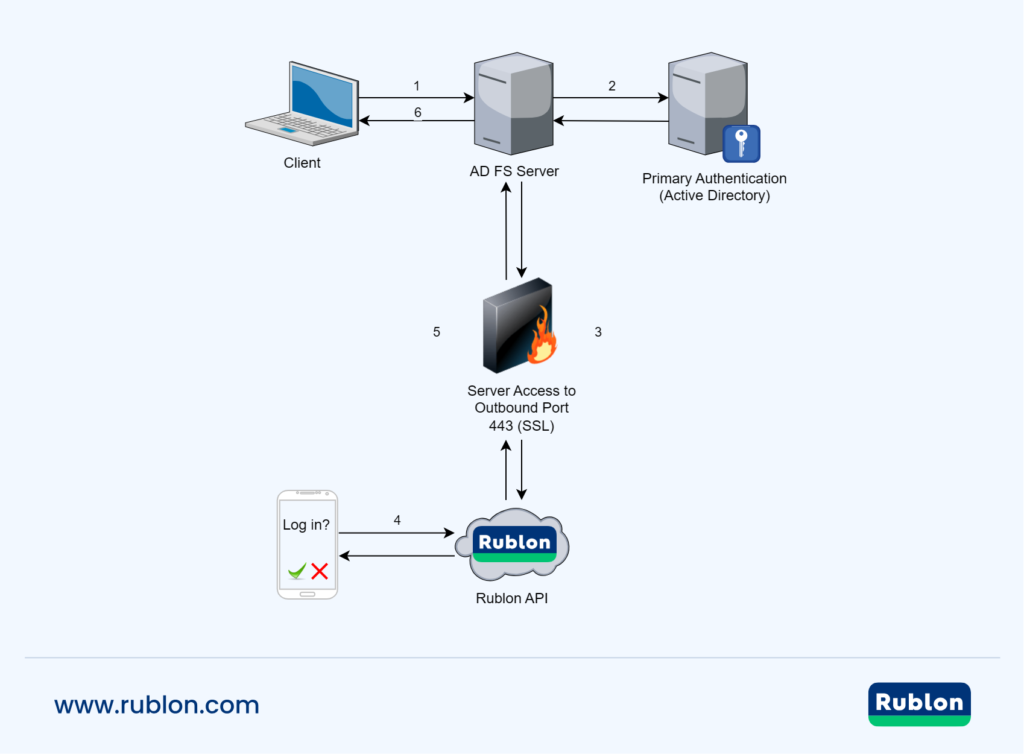
MFA for AD Federation Services – Network Diagram
- Enter your username and password.
- AD FS Server checks the user credentials against Active Directory.
- AD FS redirects to the Rublon API over TCP using SSL protocol.
- Rublon MFA challenges the user to complete secondary authentication.
- AD FS receives an authentication response of whether the user completed the second factor.
- You are successfully authenticated.
Supported Authentication Methods
| Authentication Method | Supported | Comments |
| Mobile Push | ✔ | N/A |
| FIDO | ✔ | N/A |
| Passcode | ✔ | N/A |
| SMS Passcode | ✔ | N/A |
| SMS Link | ✔ | N/A |
| Phone Call | ✔ | N/A |
| QR Code | ✔ | N/A |
| Email Link | ✔ | N/A |
| YubiKey OTP | ✔ | N/A |
| RFID | – | N/A |
Pre-Installation Steps
Before installing Rublon MFA for AD FS:
- Create an application in the Rublon Admin Console.
- Install the Rublon Authenticator mobile app.
Create an Application in the Rublon Admin Console
1. Sign up for the Rublon Admin Console. Here’s how.
2. In the Rublon Admin Console, go to the Applications tab and click Add Application.
3. Enter a name for your application and then set the type to Active Directory Federation Services (AD FS).
4. Click Save to add the new AD FS application in the Rublon Admin Console.
5. Copy and save the values of the System Token and Secret Key. You are going to need these values later.
Install Rublon Authenticator
For increased security of Multi-Factor Authentication (MFA), end-users should install the Rublon Authenticator mobile app.
Download the Rublon Authenticator for:
After installing the mobile app, users can authenticate using the following authentication methods:
Installing MFA for AD FS
Installing the Connector
1. Download Rublon MFA for AD FS by clicking the following link:
Download the Rublon MFA for AD FS installer
2. Run the Rublon MFA for AD FS installer.
3. On the first page of the installer, read about the product you are about to install.
- If this is the first time you are installing the connector, click Next.
- If this is not the first time you are installing the connector on this server, you will be able to either update the current installation or do a clean installation.
- Update current installation: If you choose to update the current installation, you will not be able to change any old options in the installer. However, if a new option has been introduced in this version of the installer, you will be able to change its value before the installation begins. The Update current installation option is recommended for those who want to update the connector to a newer version but want to keep all current settings.
- Clean installation: If you choose to do a clean installation, continue with the steps in this section.

4. Enter the API credentials (System Token and Secret Key) from your application of type Active Directory Federation Services (AD FS) from the Applications tab of the Rublon Admin Console (the values you copied before), and click Next.
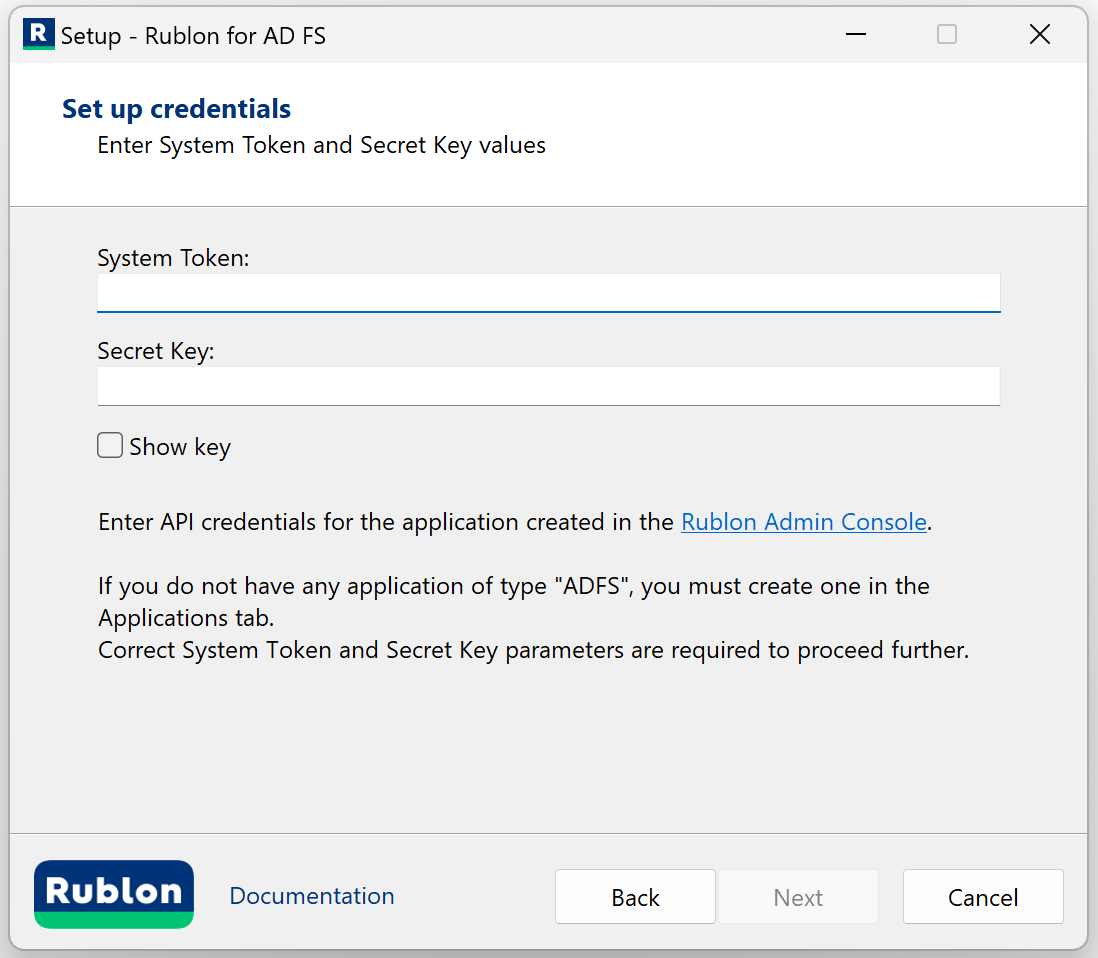
| Parameter | Description |
| System Token | System Token of your application in the Rublon Admin Console. Paste the value you noted down before. |
| Secret Key | Secret Key of your application in the Rublon Admin Console. Paste the value you noted down before. |
5. Check the configuration options you want and click Next. Refer to the following image and table.
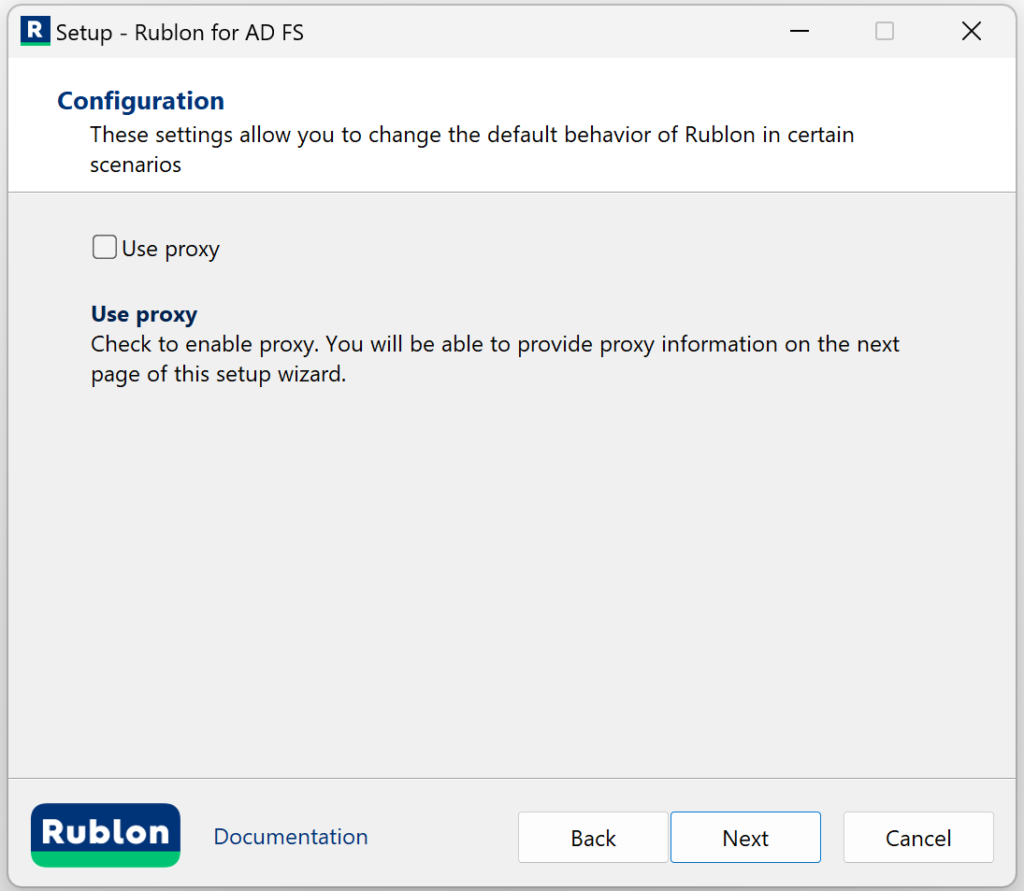
6. If you checked Use proxy on the previous page, you will see an additional page asking you to enter proxy details. After filling in the details, click Next. Refer to the following image and table.
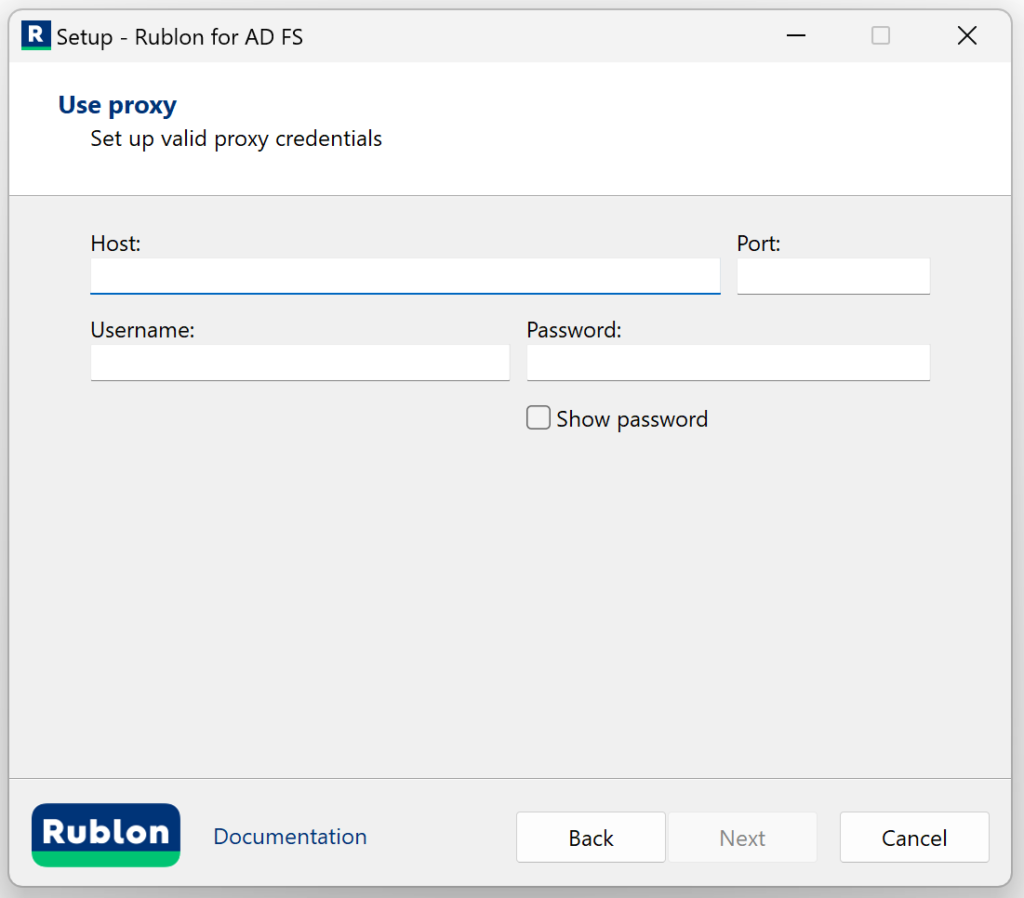
| Option | Description |
| Proxy Host | The address of the proxy server. |
| Proxy Port | The port on which the proxy server is operating. |
| Proxy Username | The username of the HTTP proxy server user. Optional. Fill in if verification by username is required. |
| Proxy Password | The password of the HTTP proxy server user. Optional. Fill in if required for verification. |
7. Check the bypass option if you want and click Next. Refer to the following image and table.
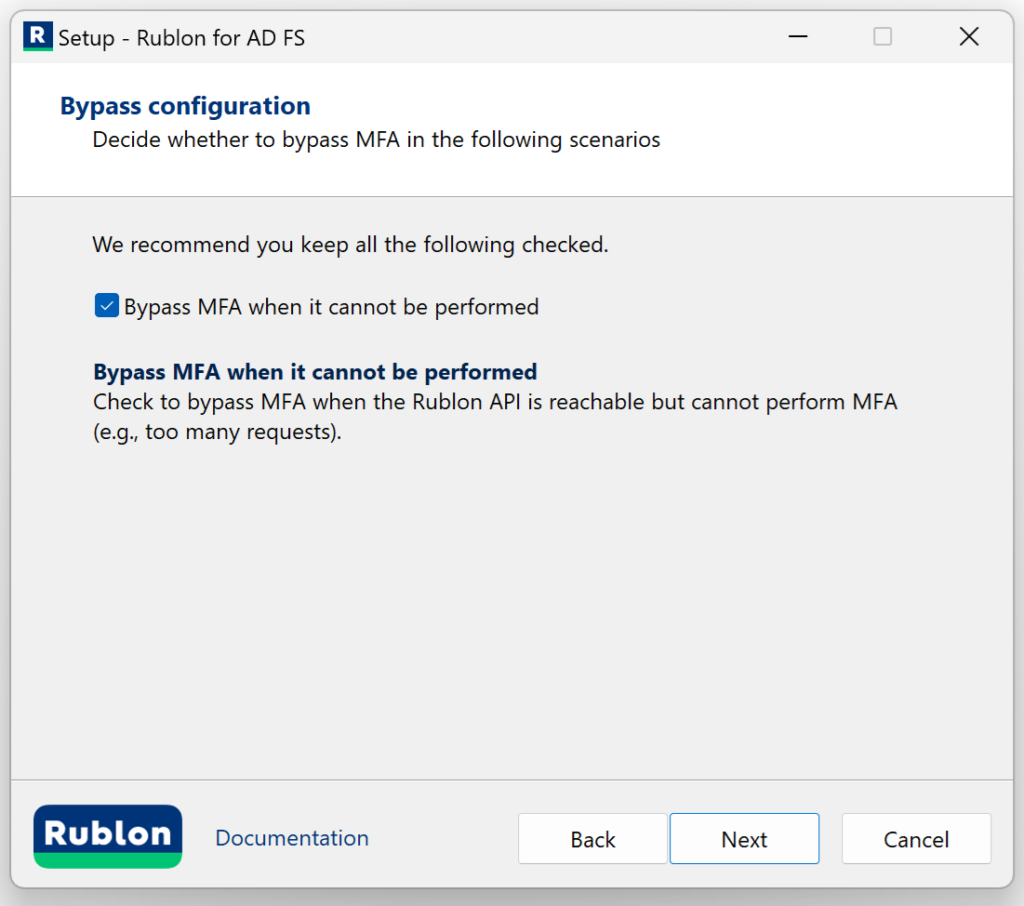
| Option | Description |
| Bypass MFA when it’s not feasible | Check to bypass MFA when the Rublon API is not reachable (no internet connection or API down) or when the Rublon API is reachable but cannot perform MFA (e.g., too many requests). |
8. Rublon MFA for AD FS is ready to install.
9. Click Install to install Rublon MFA for AD FS.
10. After a successful installation, the installer informs you that your installation is complete. Check View logs if you want and click Finish.
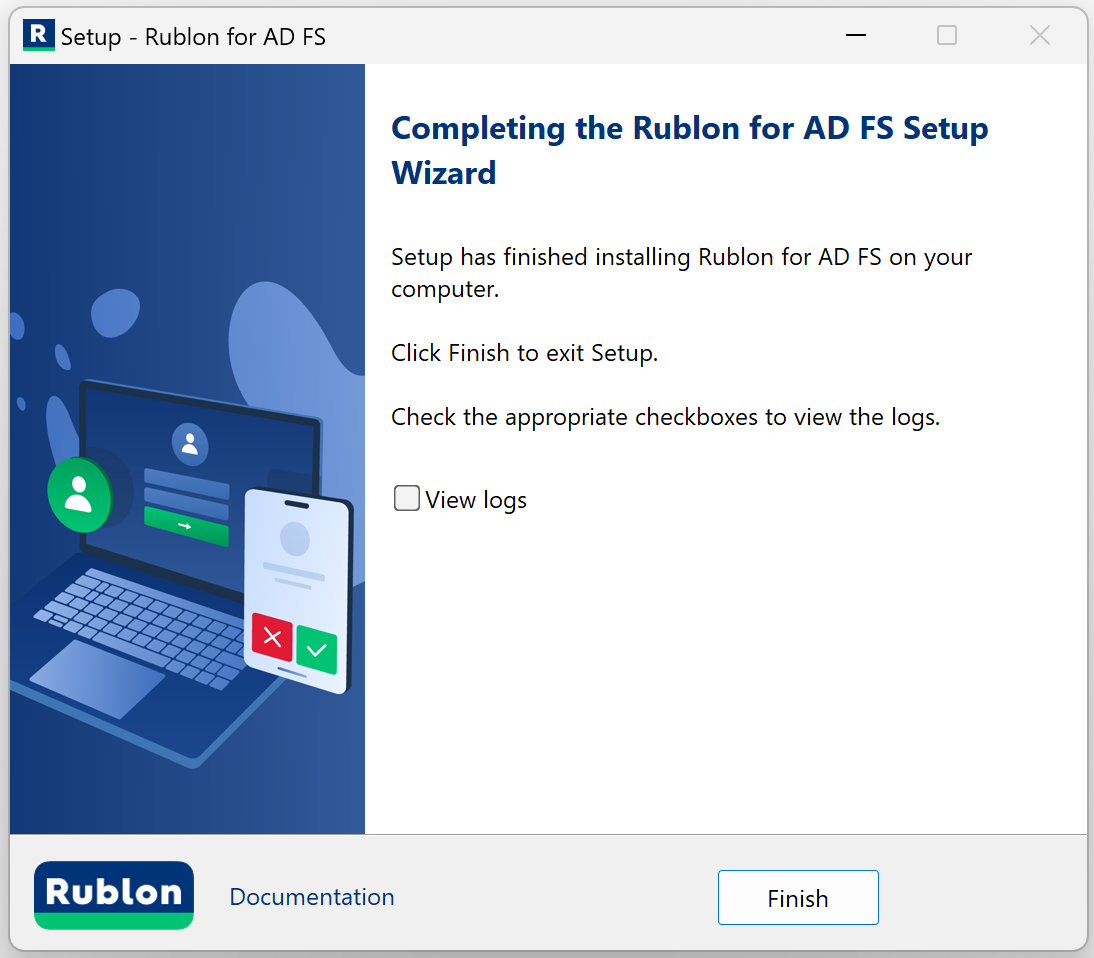
Configuring MFA in the AD FS Manager
The AD FS Manager configuration differs depending on the Windows Server version.
Windows Server 2016 or newer
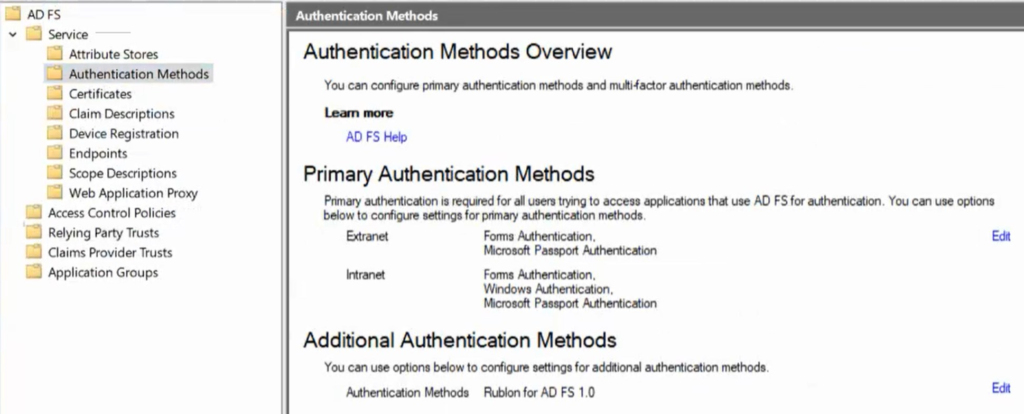
1. Open the AD FS Management, go to AD FS → Service → Authentication Methods, and click Edit in the Additional Authentication Methods section (depending on your settings, this section may also be called Multi-factor Authentication Methods).
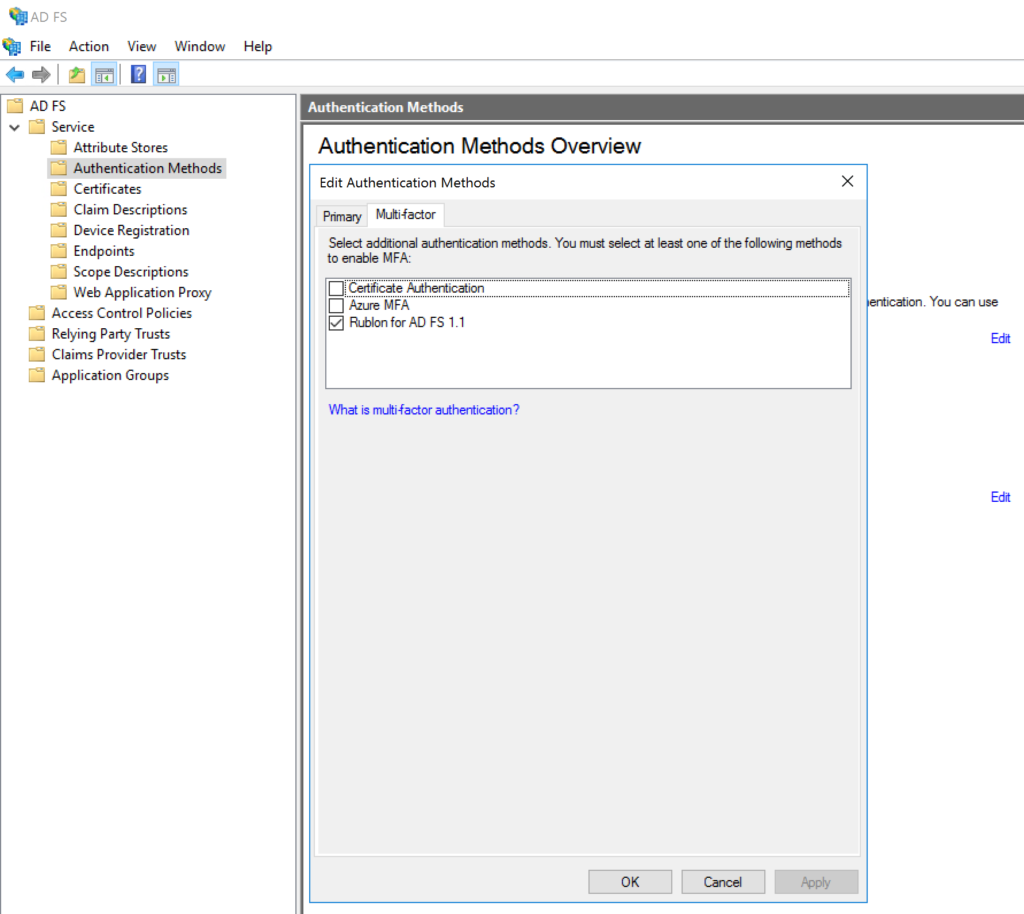
2. Ensure Rublon for AD FS is selected in additional authentication methods of the Multi-factor tab.
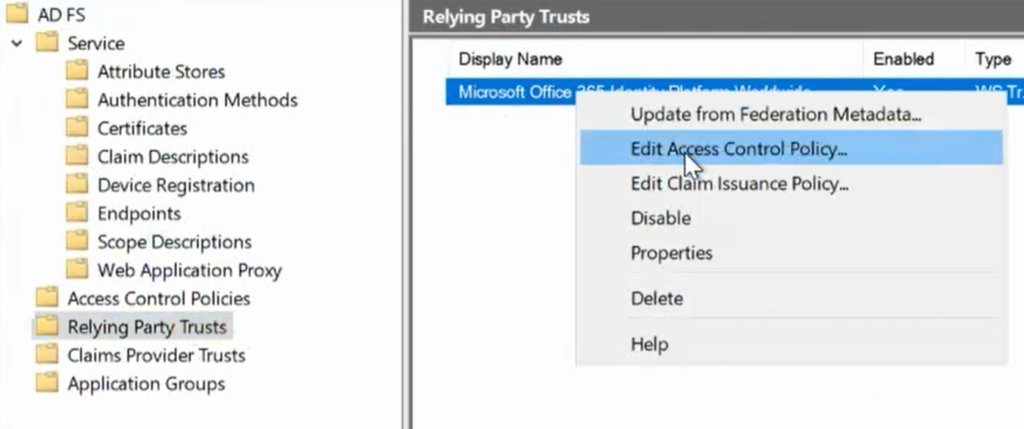
3. In the AD FS Management, go to AD FS → Relying Party Trusts, right-click your Relying Party, and select Edit Access Control Policy….
Then, click Use access control policy.
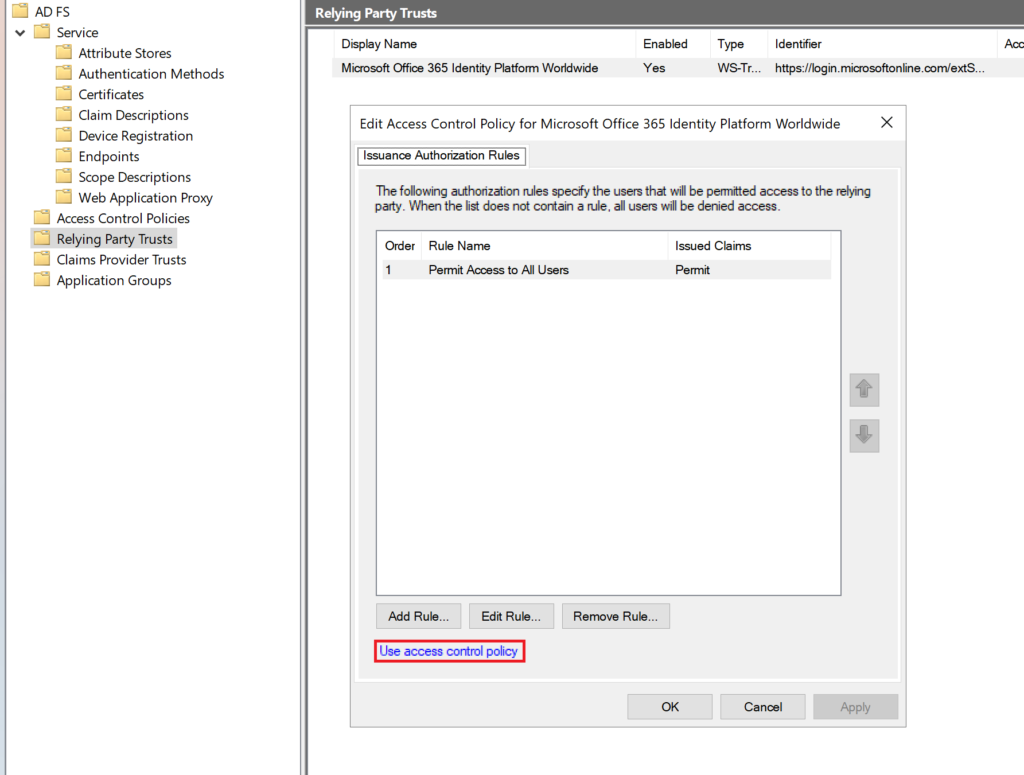
And ensure one of the following access control policies is selected (You must select one of these for Rublon MFA to work!):
- Permit everyone and require MFA
- Permit everyone and require MFA for specific group
- Permit everyone and require MFA from extranet access
- Permit everyone and require MFA from unauthenticated devices
- Permit everyone and require MFA, allow automatic device registration
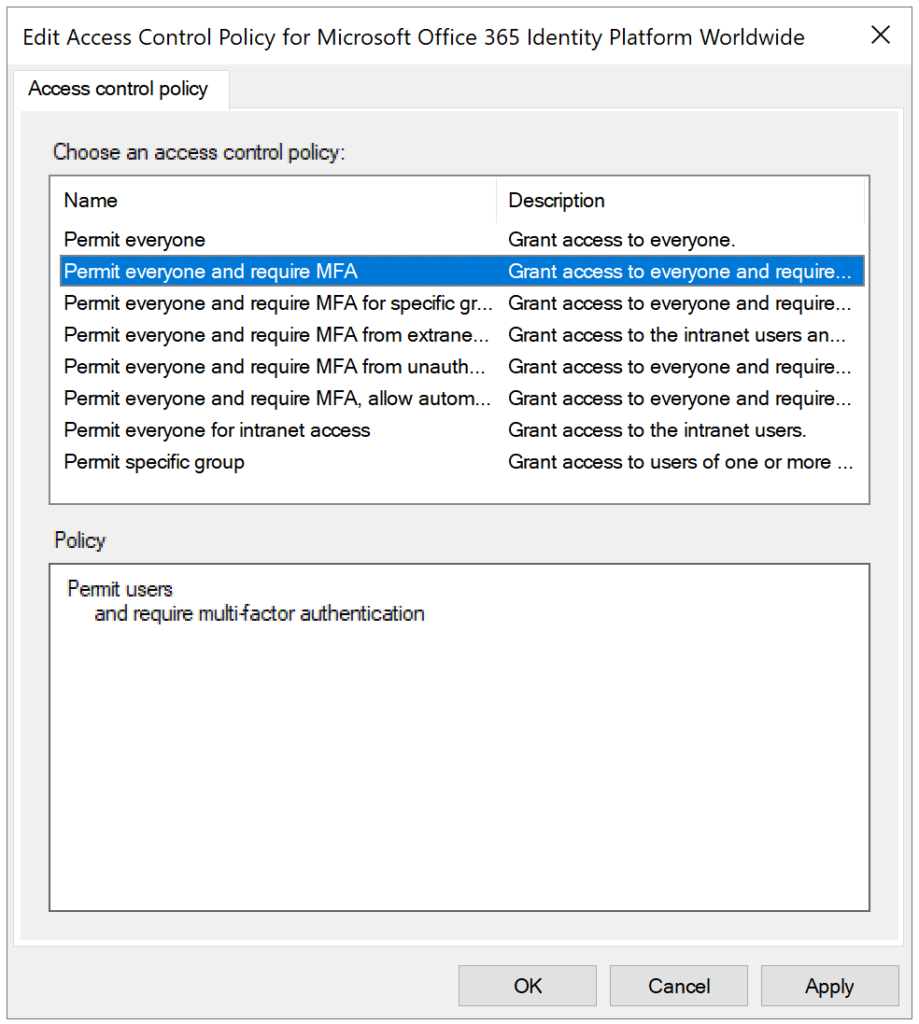
6. After selecting one of the policies, click OK to save your changes.
7. You have to perform steps 3-6 for every trust you want to enable MFA for.
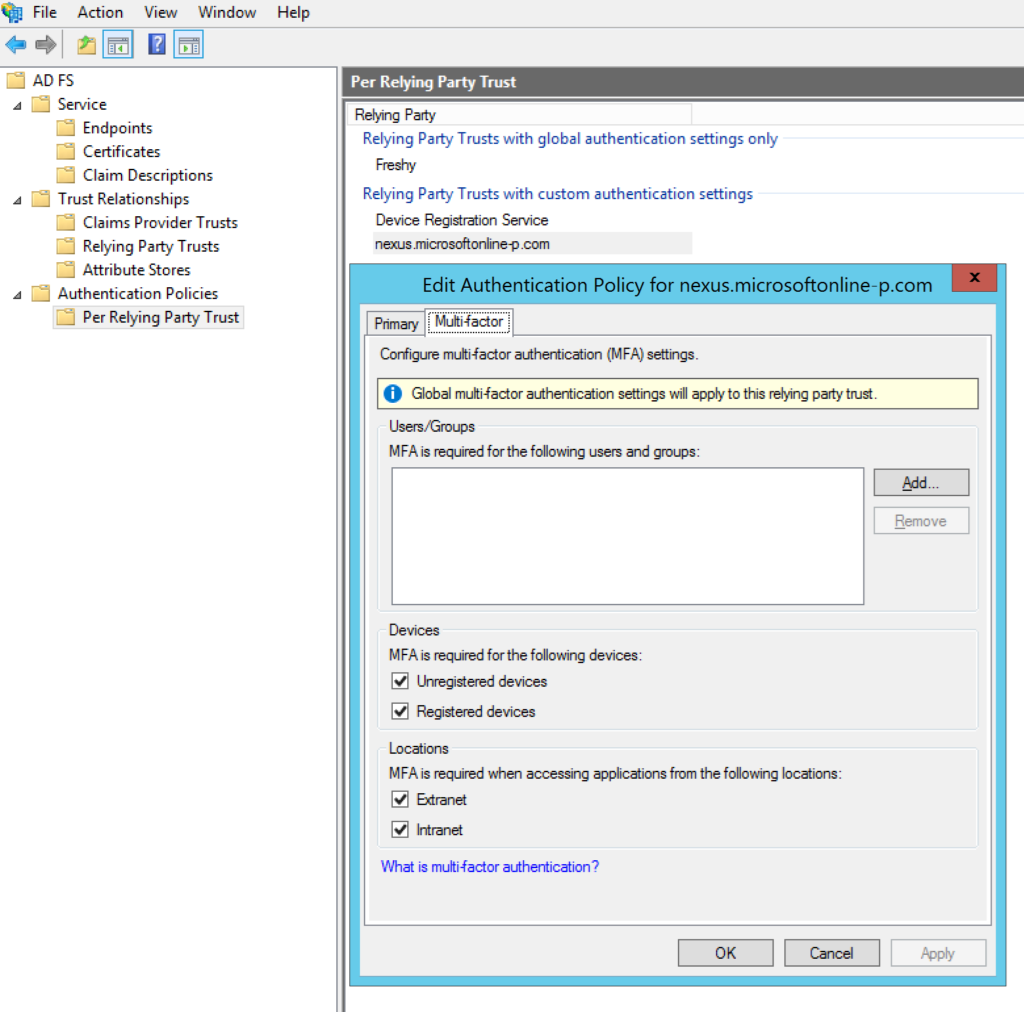
Windows Server 2012 R2
1. Open the AD FS Management, go to Authentication Policies, and select Edit next to Global Settings in the Multi-factor Authentication section.
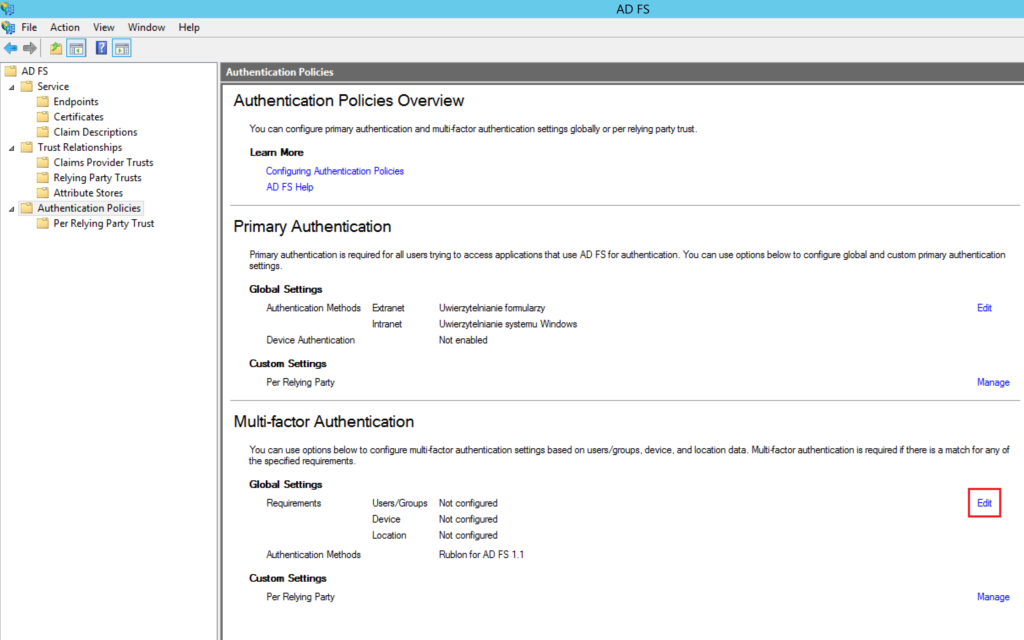
2. In the Multi-factor tab:
- Ensure at least one item (Unregistered devices, Registered devices) is selected in the Devices section
- Ensure at least one item (Extranet, Intranet) is selected in the Locations section
- Ensure Rublon for AD FS is selected in Select additional authentication methods.
3. Click Apply and then OK to save your changes.
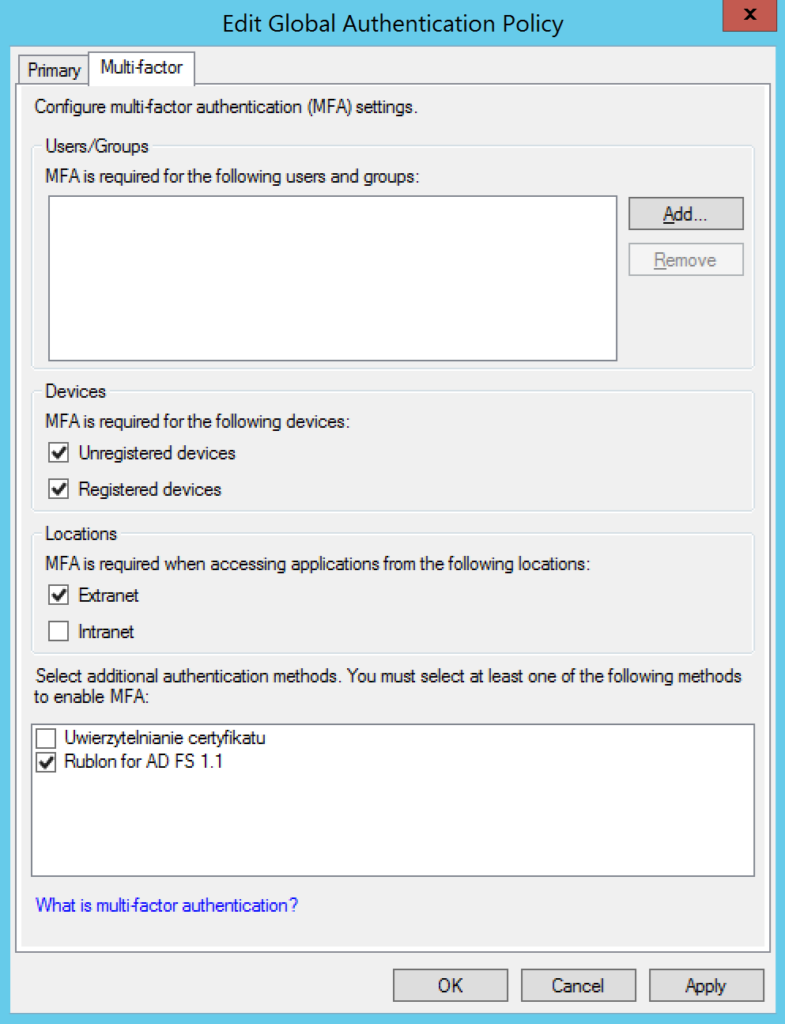
4. In the AD FS Management, go to AD FS → Authentication Policies → Per Relying Party Trust.
5. Select a party trust, right-click it, and select Properties.
6. In the Multi-factor tab:
- Ensure that at least one item (Unregistered devices, Registered devices) is selected in the Devices section
- Ensure that at least one item (Extranet, Intranet) is selected in the Locations section
- Click Apply and then OK to save your changes.
You have to perform steps 4-6 for every trust you want to enable MFA for.
Finishing up
Congratulations! Your installation is complete.
There are some things you may want to do before continuing:
Note
Ensure that the firewall on the server on which you have installed Rublon Multi-Factor Authentication (MFA) for Active Directory Federation Services (AD FS) does not restrict Rublon communication on TCP port 443.
- Refer to the Configuring MFA for AD FS section in this documentation to learn how to change the settings set during installation.
- Refer to Testing MFA for AD FS to learn how to test your AD FS MFA.
Configuring MFA for AD FS
All default values of settings depend on your choices during installation.
To change the settings of Rublon MFA for Windows, go to Windows Registry: HKEY_LOCAL_MACHINE\SOFTWARE\RUBLON\ADFS
With binary values, 1 stands for Yes, and 0 for No.
The following table describes all values:
| Value | Description |
| SecretKey | Secret Key of your Rublon MFA for Windows application in the Rublon Admin Console. |
| SystemToken | System Token of your Rublon MFA for Windows application in the Rublon Admin Console. |
| ProxyHost | The address of the proxy server. Optional. |
| ProxyMode | Default: 0 You need to set at least two parameters for the proxy to work: ProxyHost and ProxyPort. If you add both of these parameters, then the proxy will be automatically activated (and ProxyMode will be set to 1). If you only specify ProxyHost or only specify ProxyPort, registry changes will be made, but ProxyMode will be set to 0, meaning the proxy will not be active. Set ProxyMode to 0 to disable the proxy. The password of the HTTP proxy server user. Optional. |
| ProxyPassword | The password of the HTTP proxy server user. Optional. |
| ProxyPort | The port on which the proxy server is operating. Optional. |
| ProxyUsername | The username of the HTTP proxy server user. Optional. |
| RublonApiServer | Default: https://core.rublon.net The server of the Rublon API. |
| FailMode | Defines whether the user is to be logged in or denied when Rublon servers are reachable but MFA authentication cannot be performed. One reason why MFA authentication cannot be performed is when an authentication request to the Rublon API reaches its destination but fails. Possible values: bypass – If the authentication request to the Rublon API fails, the user is bypassed. deny – If the authentication request to the Rublon API fails, the user is denied. |
SendUPN |
Default: 0 If set to 1, Rublon looks up the Universal Principal Name (UPN) in Active Directory and sends the UPN to the Rublon API as Rublon username (e.g., user@domain.com). Suppose you set SendUPN to 1, but Rublon cannot find the User Principal Name (UPN) for a given user in Active Directory. In that case, Rublon either bypasses or denies the user based on the value of FailMode. If FailMode is set to bypass, Rublon bypasses the user. Otherwise, Rublon denies access to the user and adds appropriate information to the logs. Note: If user1 has assigned user2@rublon.com UPN, they will get user2’s MFA methods. Be careful using such a configuration. |
| DebugRublonRequests | Default: 0 Set to 1 to enable a debug window (developer tools) next to the Rublon Prompt during each login. |
Testing MFA for AD FS
This example portrays testing Multi-Factor Authentication for Active Directory Federation Services by logging in to the Microsoft 365 Portal and choosing the Mobile Push authentication method.
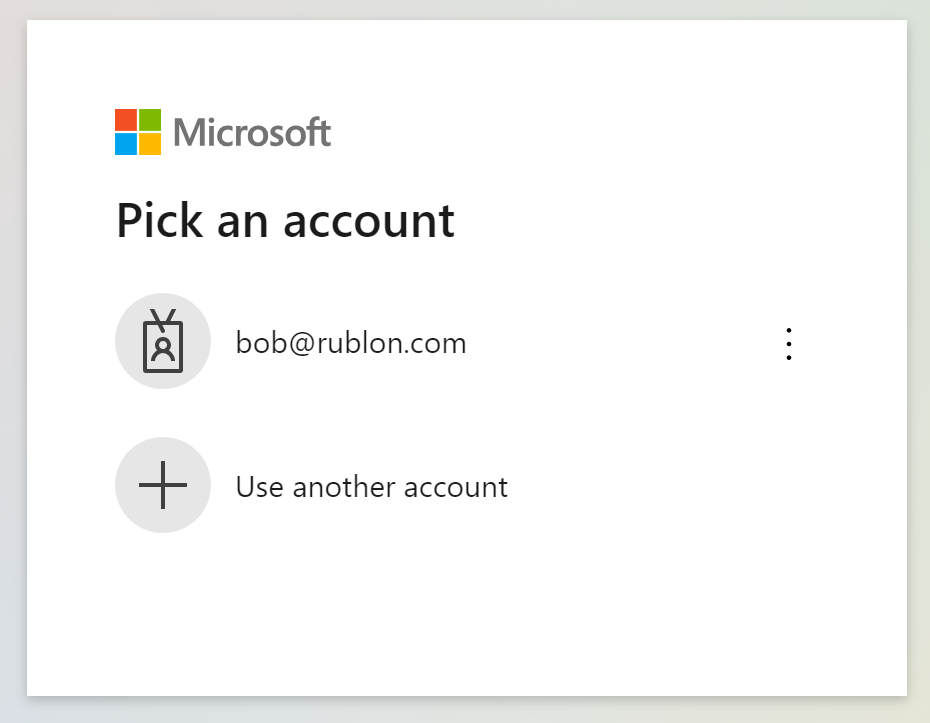
1. Go to portal.office.com and enter your email or select your account from the list if you have already logged in before.
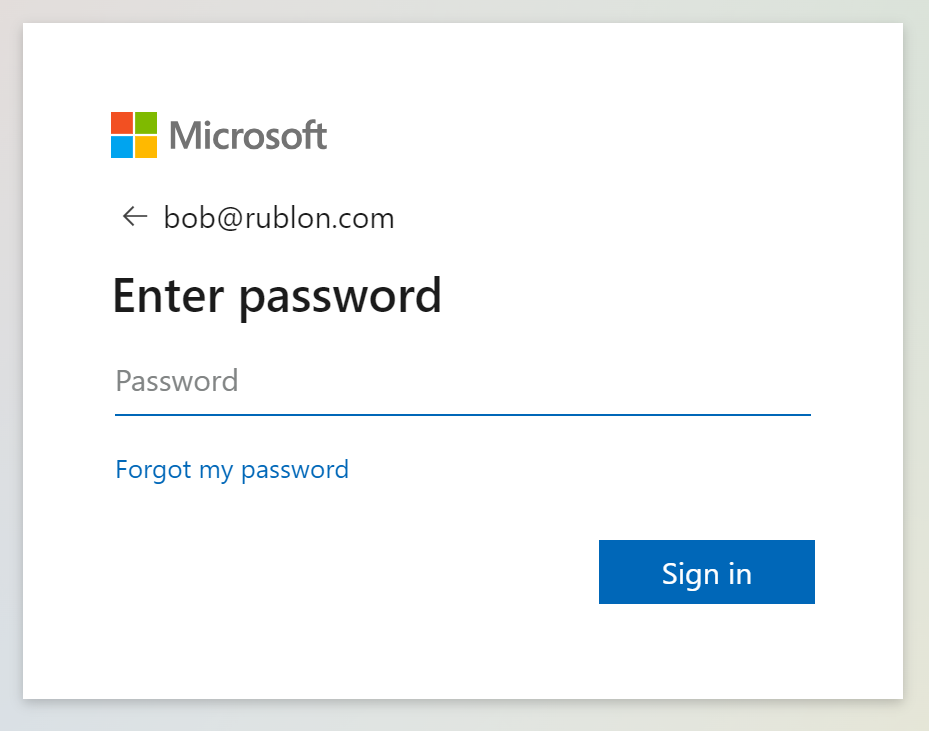
2. Enter the password for your account.
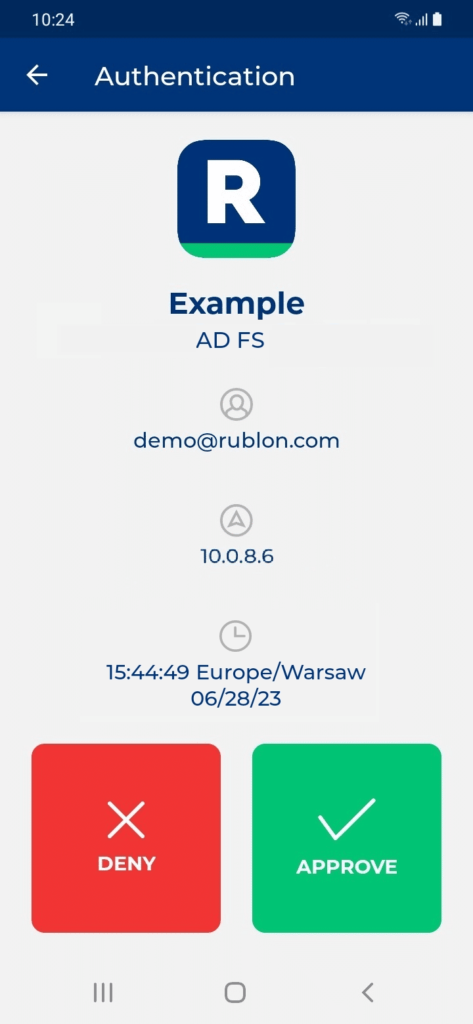
3. A window will appear with various MFA options from Rublon. Let’s choose Mobile Push.

4. Rublon will send a Mobile Push authentication request to your phone. Tap APPROVE.
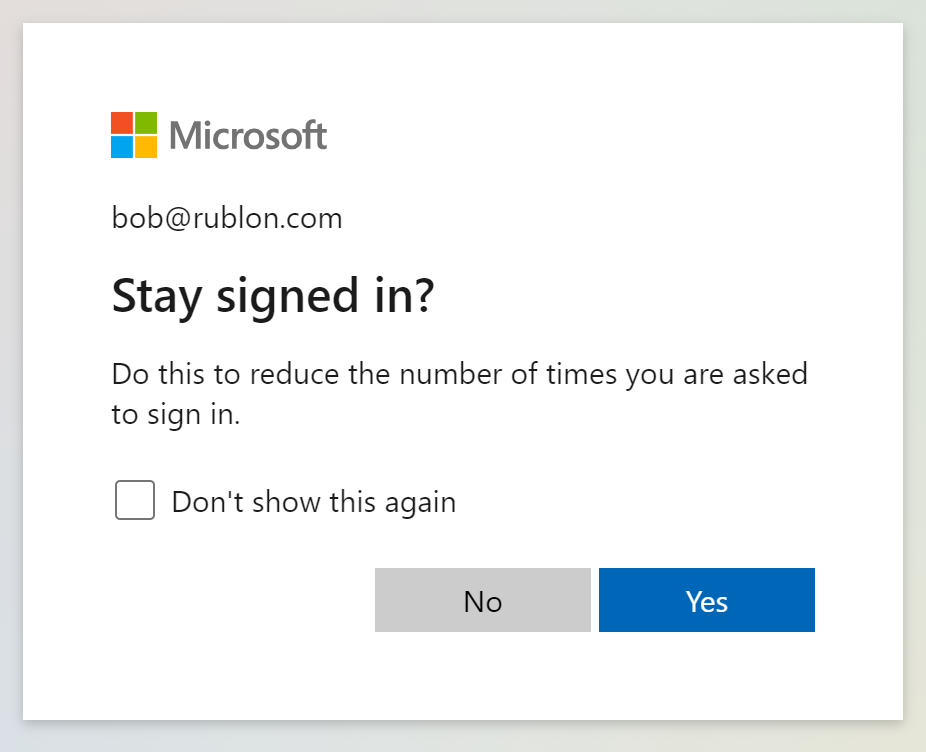
5. You may be asked whether you want to stay signed in. Select whatever fits your personal or organizational needs.
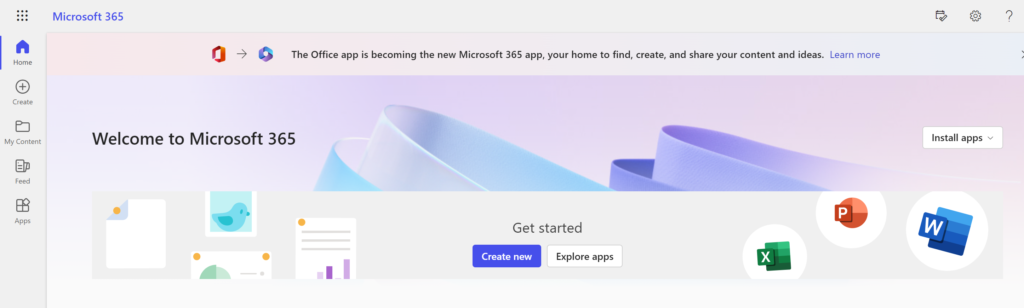
6. You will be successfully logged in to the Microsoft 365 Portal.
Updating MFA for AD FS
To update your Rublon MFA for AD FS connector, download and install the new version on the ADFS server where you have installed the old version before.
You can simply run the installer and select Update current installation.

If the new installer introduces a new option that was not available in previous versions of the connector, you will be able to change that option after clicking Next. Otherwise, your update will start right away.
Uninstalling MFA for AD FS
To uninstall Rublon MFA for AD FS:
- Run C:\Program Files\Rublon\ADFS\unins000.exe as administrator.
- Alternatively, open Apps & features (or Add and remove programs on some Windows versions), select Rublon for AD FS, and click Uninstall.
Troubleshooting
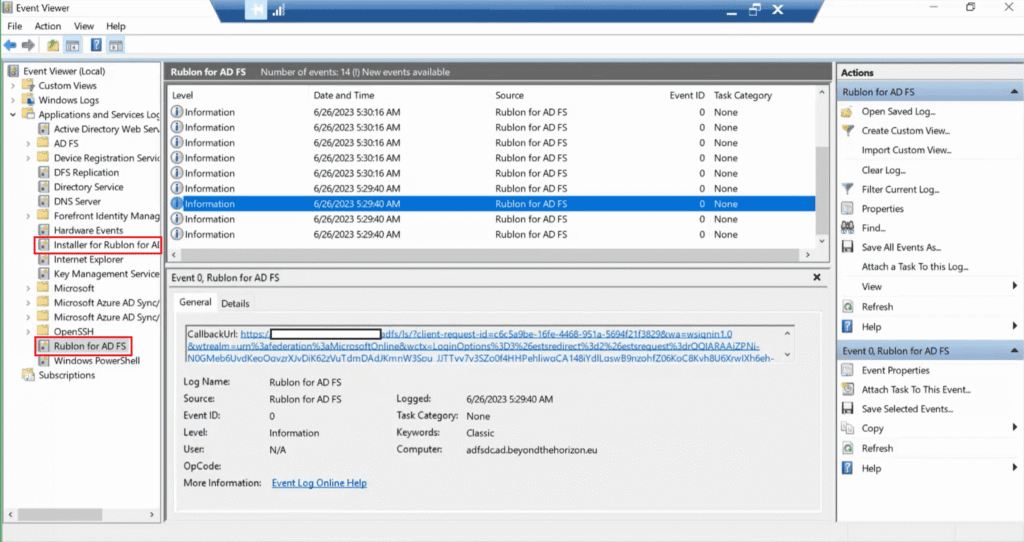
- To troubleshoot your installation:
- Open the Event Viewer and go to Applications and Services Logs → Installer for Rublon for AD FS
- To troubleshoot your Rublon MFA for AD FS connector after it’s been installed:
- Open AD FS Management and ensure the proper access policy is assigned for your Relying Party Trust (Recheck every step in Configuring MFA in the AD FS Manager).
- Open the Event Viewer and go to Applications and Services Logs → Rublon for AD FS
- Send the file to Rublon Support along with a description of your issue:
- In the Event Viewer, select logs that you want to export, right-click them and select Save All Events As
- Enter the name for your file and save it as a TXT file
- Send us the file
If you encounter any issues with your Rublon integration, please contact Rublon Support.