Last updated on May 6, 2025
Overview of MFA for Amazon WorkSpaces
Multi-Factor Authentication (MFA) for Amazon WorkSpaces is an extra layer of security that requires users to complete two verification methods in order to access Amazon WorkSpaces. After entering their Active Directory/ RADIUS username and password, the user must complete an additional authentication step using one of the available methods such as a Mobile Push or Email Link. This additional step of MFA ensures that hackers are unable to gain access to Amazon WorkSpaces with just the user’s login credentials.
This document describes how to enable Rublon Multi-Factor Authentication (MFA) for users logging in to Amazon WorkSpaces. In order to achieve that, you have to use Rublon Authentication Proxy, an on-premise RADIUS proxy server, which allows you to integrate Rublon with Amazon WorkSpaces to add Multi-Factor Authentication to your logins.
Supported Authentication Methods
Required Components
- EC2 Instance – Windows Server 2012 R2 or Windows Server 2016 or Windows Server 2019 – to act as a Domain Controller
- EC2 Instance – Ubuntu 16.04/18.04/20.04 – to install Rublon Authentication Proxy
- Amazon WorkSpaces with AD Connector set as Directory Service
The Configuration section is going to walk you through setting up all three of those components.
Configuration of MFA for Amazon WorkSpaces
Follow these steps to enable Rublon 2FA for Amazon WorkSpaces.
Configure Windows Server and Active Directory
1. Launch a new instance from the EC2 Instances console.
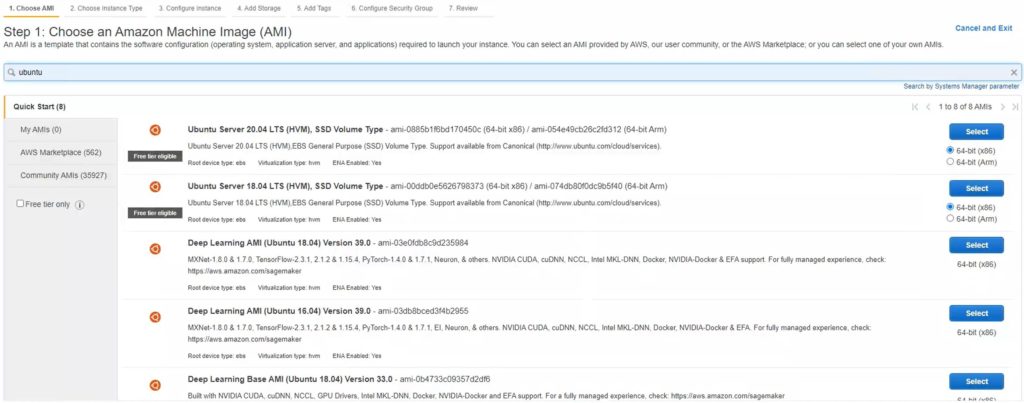
2. Click Choose AMI and select your desired Windows version.
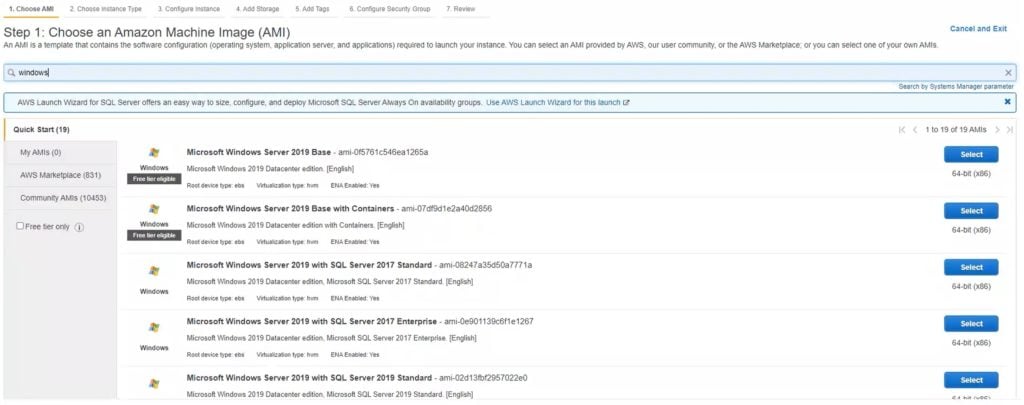
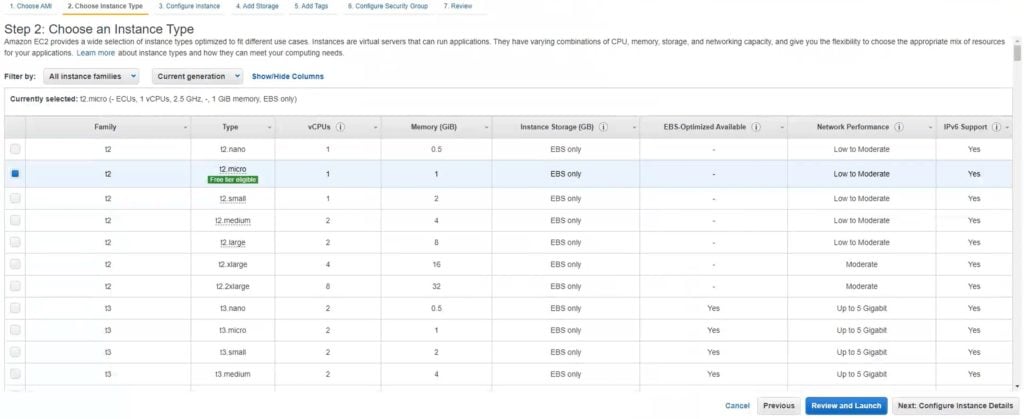
4. Click Next: Configure Instance Details.
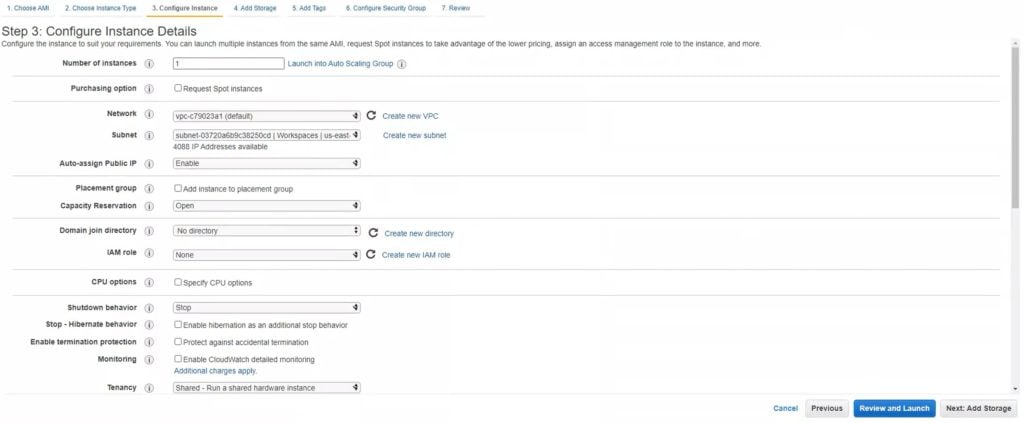
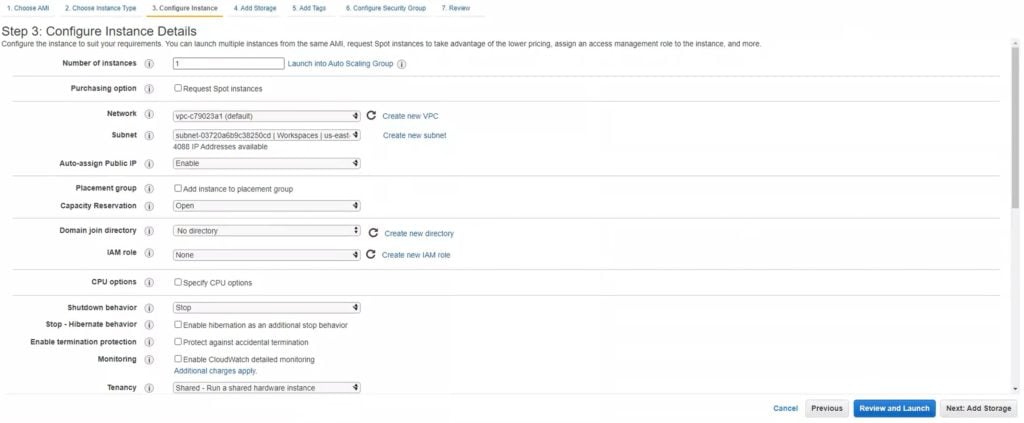
5. Fill in the form. Some of the options relate to the network side. Make sure that both of your instances reside in the same VPC and Subnet. If you wish, you can create a new VPC and Subnet. Alternatively, select the default options.
Write down the values of VPC and Subnet. You are going to need these later when setting up the Ubuntu instance.
Make sure to set Auto-assign Public IP to Enable. Later on, you will have to connect to both instances and it might be more convenient to use the standard RDP and SSH connection instead of the AWS Console.
Keep the rest of the settings as they are or change them according to your needs.
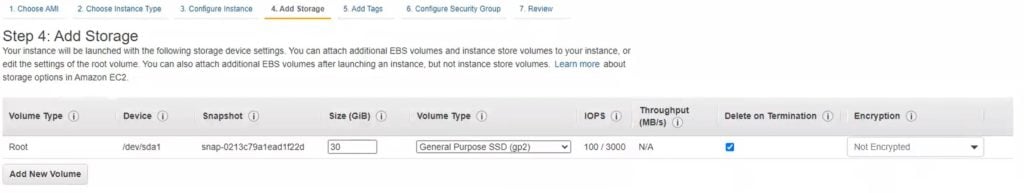
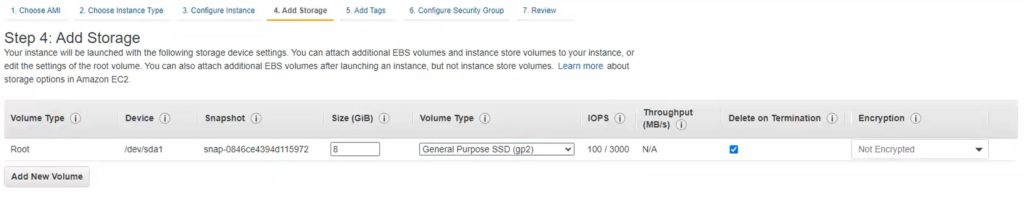
6. Click Next: Add storage. Specify the size of the volume for your instance. Set the size according to your needs or keep the default value of 30GB.
7. Click Next: Add tags. You do not have to specify any tags for this configuration to work. Add tags if you need tags for some other reason.
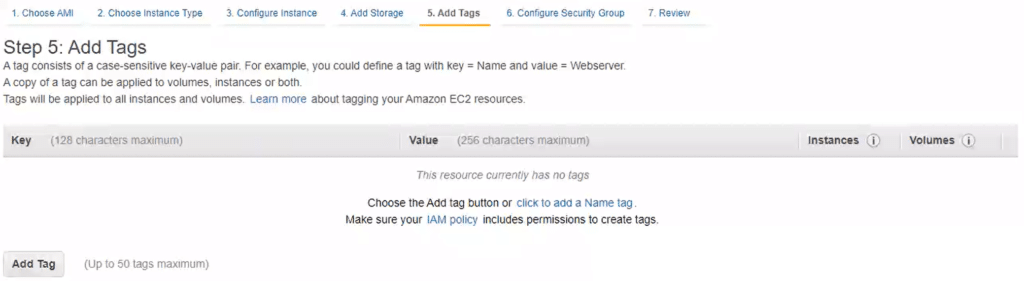
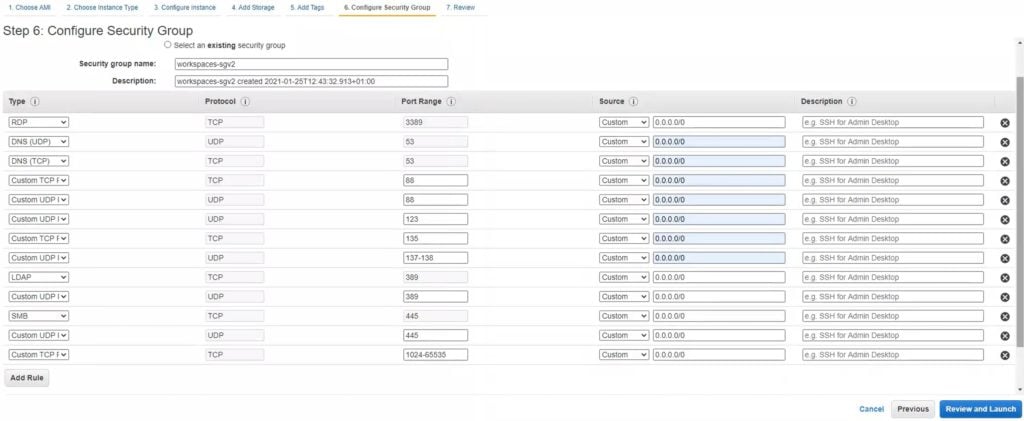
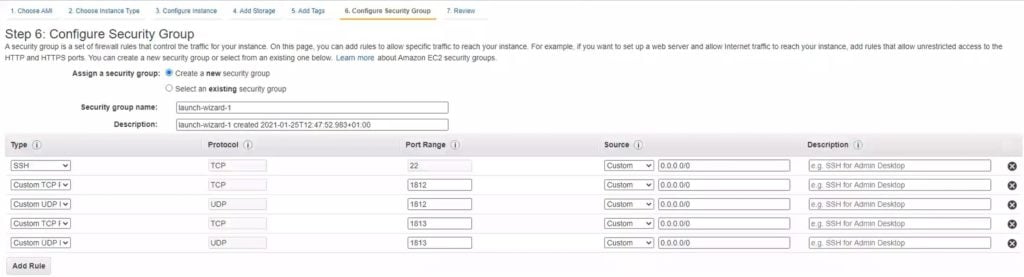
8. Click Next: Configure Security Group. If you already have an existing Security Group for your VPC, edit the existing group. Otherwise, create a new Security Group.
Verify that the following ports are open on your directory controllers for the Amazon WorkSpaces VPC CIDR:
- TCP/UDP 53: DNS
- TCP/UDP 88: Kerberos authentication
- UDP 123: NTP
- TCP 135: RPC
- UDP 137-138: Netlogon
- TCP 139: Netlogon
- TCP/UDP 389: LDAP
- TCP/UDP 445: SMB
- TCP 1024-65535: Dynamic ports for RPC
Add TCP port 3389 and open this port to your public IP address if you wish to connect to this instance using RDP.
Note
Configure Ubuntu and Rublon Authentication Proxy
5. Click Next: Add storage. Specify the size of the volume for your instance. Set the size according to your needs or keep the default value of 8GB.
- TCP/UDP 1812
- TCP/UDP 1813
log:
debug: false
rublon:
api_server: https://core.rublon.net
system_token: system_token_obtained_from_rublon_admin_console
secret_key: secret_key_obtained_from_rublon_admin_console
proxy_servers:
- name: RADIUS-Proxy
type: RADIUS
ip: private_ip_of_the_ubuntu_instance
port: 1812
radius_secret: secret_to_communicate_with_the_proxy
mode: nocred
auth_method: email
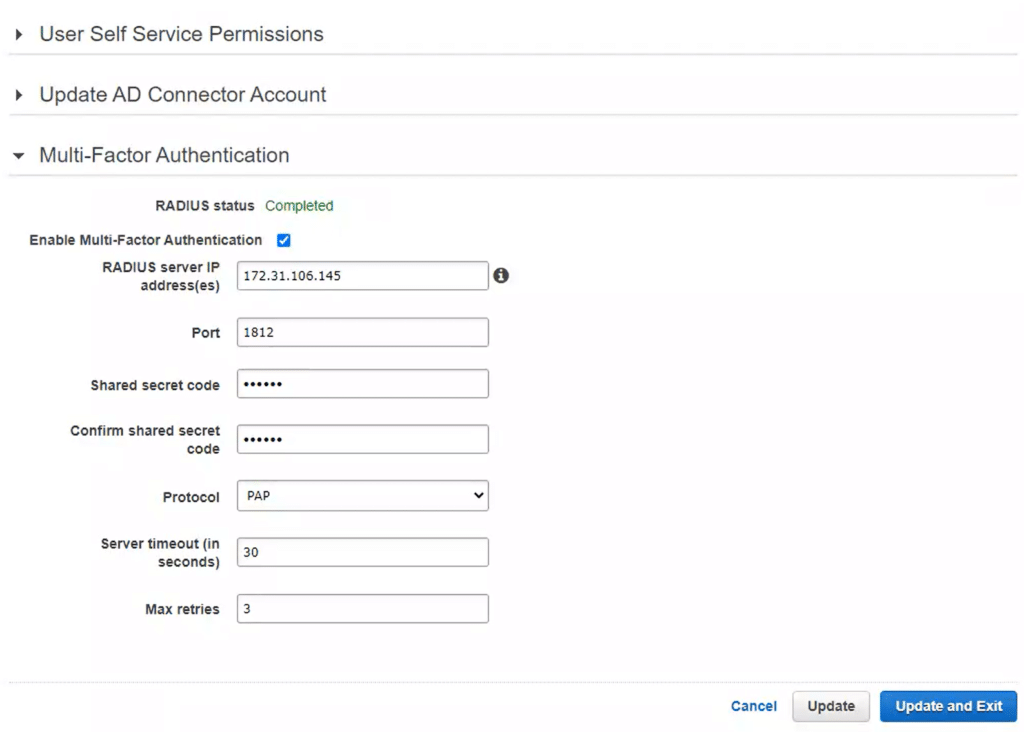
Set up Amazon WorkSpaces with AD Connector
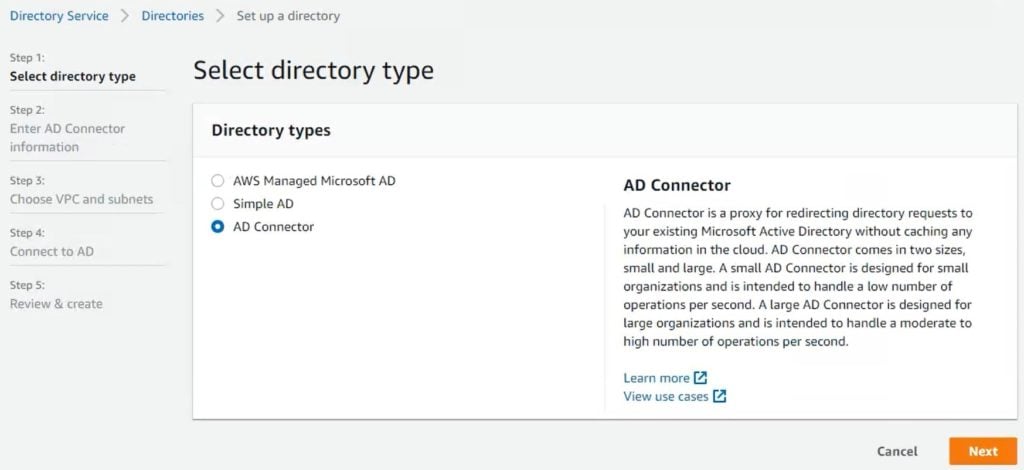
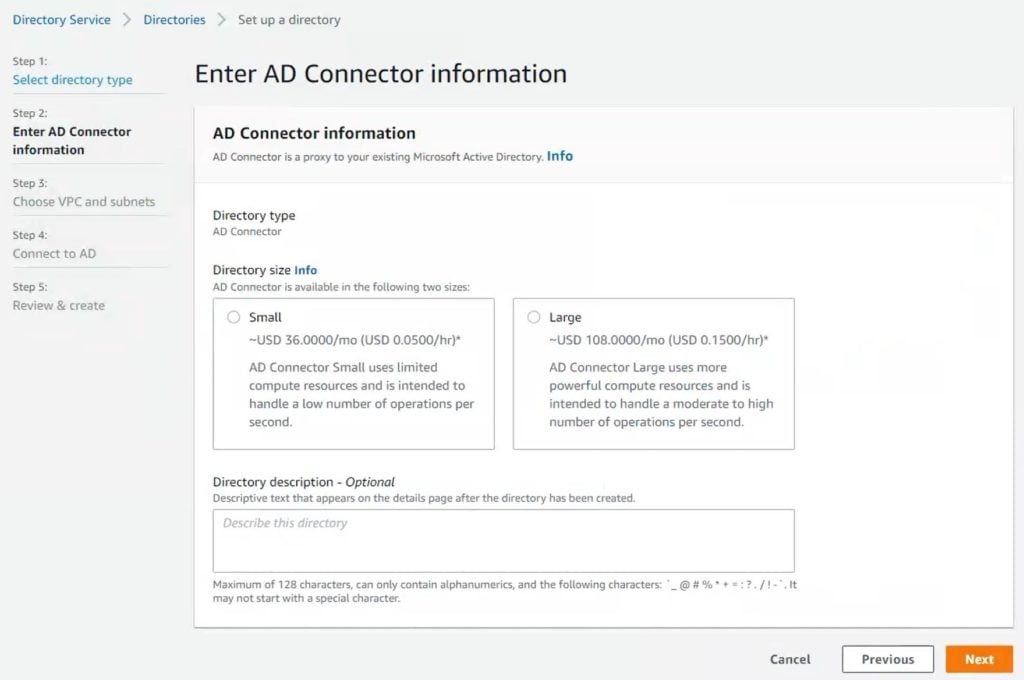
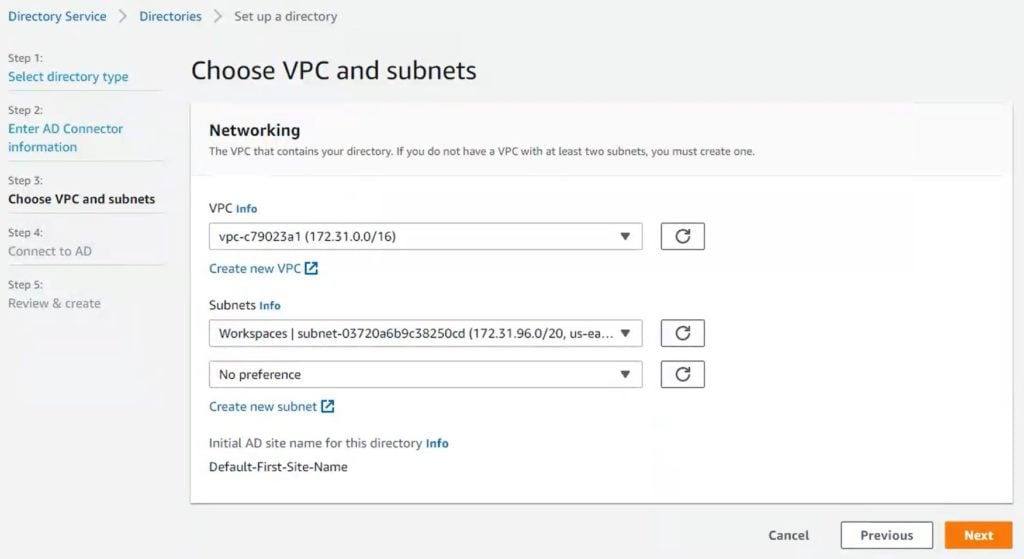
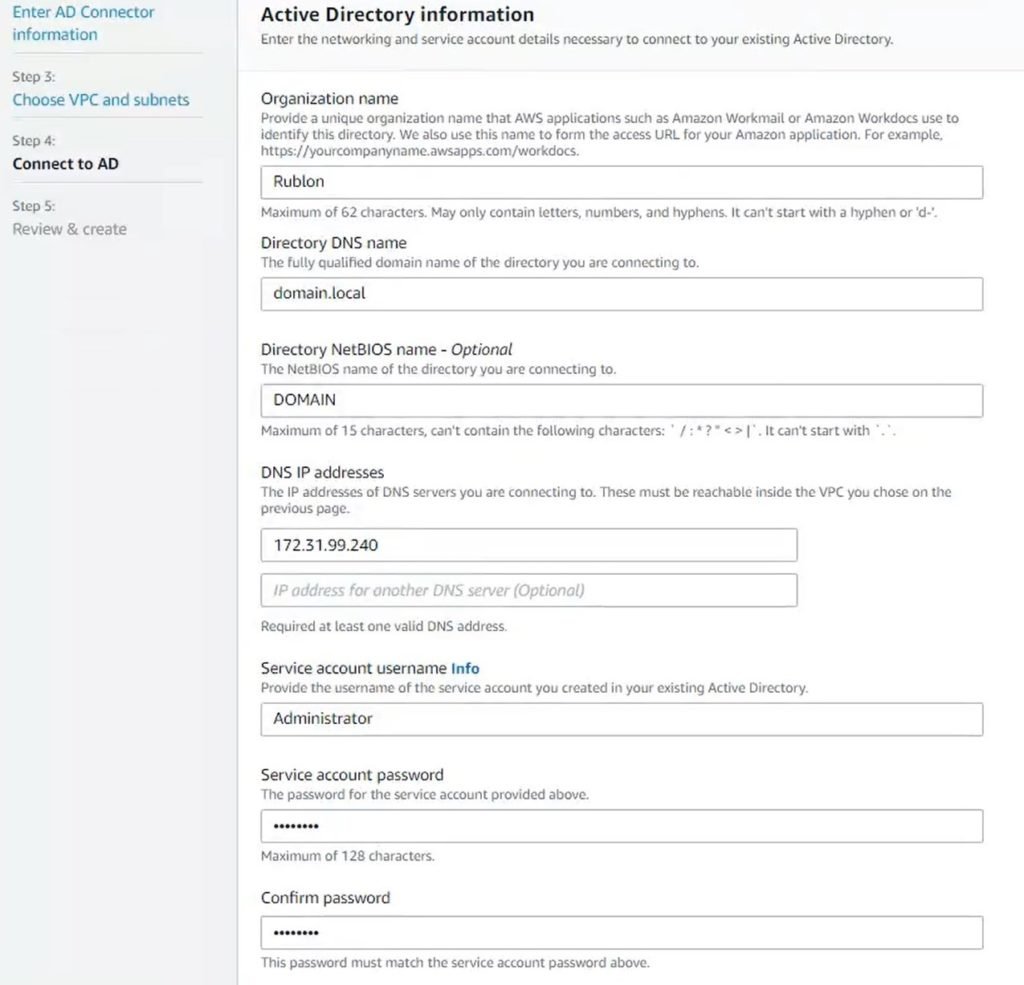
6. Click Next and provide your Active Directory information. Refer to the following image and table.
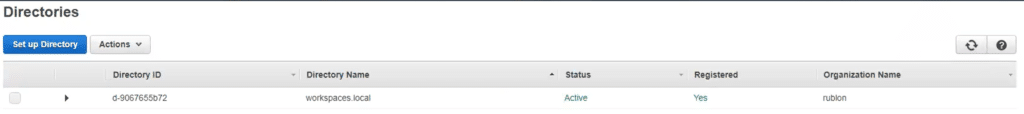
Testing MFA for Amazon WorkSpaces

- push – sends a Mobile Push notification to your phone
- mail – sends an Email Link to your email
- 123456 – verifies the Passcode generated by Rublon Authenticator or a third-party app like Google Authenticator or Microsoft Authenticator; must be exactly 6 characters long with no spaces in between
- 123456789 – verifies the Bypass Code; must be exactly 9 characters long with no spaces in between
