Last updated on July 8, 2025
Overview of MFA for Cisco RV Series
This document applies to the following Cisco RV Series router models:
- RV160, RV160W
- RV260, RV260P, RV260W
- RV320
- RV325
- RV340, RV340W
- RV345, RV345P
- Cisco RVL200 4-Port SSL/IPSec VPN Router (= Linksys 4-Port SSL/IPSec VPN Router)
Supported Authentication Methods
Before You Start Configuring MFA for Cisco RV Series VPN
Before configuring Rublon MFA for Cisco RV Series VPN:
- Ensure you have prepared all required components.
- Create an application in the Rublon Admin Console.
- Install the Rublon Authenticator mobile app.
Required Components
1. User Identity Provider (IdP) – You need an external Identity Provider, such as Microsoft Active Directory, OpenLDAP, or FreeRADIUS.
2. Rublon Authentication Proxy – Install the Rublon Authentication Proxy if you have not already.
3. Cisco RV Series Router – You need a Cisco RV Series router with firmware 1.0.03.21 or higher. This is because only version 1.0.03.21 and higher allows you to configure Timeout and No. of Retries parameters that are required for Rublon MFA to work correctly.
Create an Application in the Rublon Admin Console
1. Sign up for the Rublon Admin Console. Here’s how.
2. In the Rublon Admin Console, go to the Applications tab and click Add Application.
3. Enter a name for your application (e.g., Cisco RV Series VPN) and then set the type to Rublon Authentication Proxy.
4. Click Save to add the new application in the Rublon Admin Console.
5. Copy and save the values of the System Token and Secret Key. You are going to need these values later.
Install Rublon Authenticator
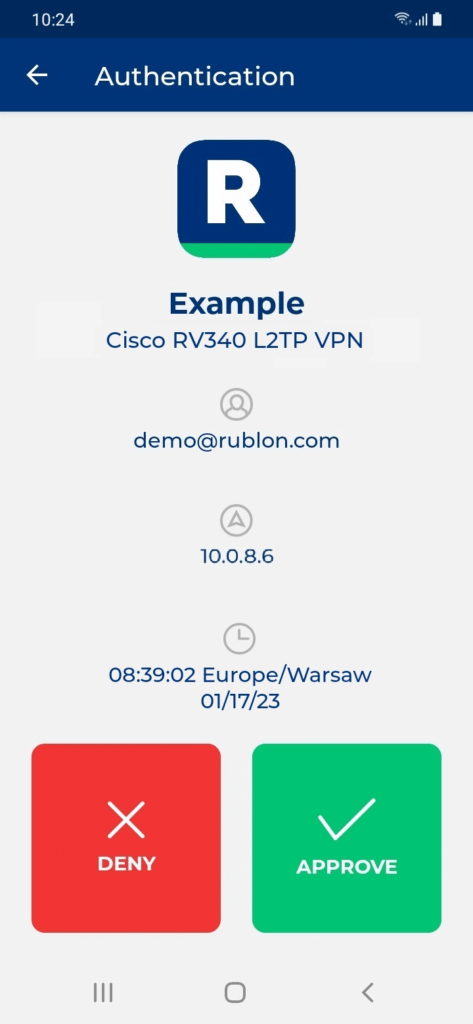
Some end-users will install the Rublon Authenticator mobile app. So, as a person configuring MFA for Cisco RV Series VPN, we highly recommend you install the Rublon Authenticator mobile app, too. Thanks to that, you will be able to test MFA for Cisco RV Series via Mobile Push.
Download the Rublon Authenticator for:
Configuring Multi-Factor Authentication (MFA) for Cisco RV Series VPN
Follow the following instructions to set up MFA for Cisco RV Series VPN.
Configuring Rublon Authentication Proxy as RADIUS Server
1. Log in to the Cisco RV Series admin panel.
2. Go to System Configuration → User Accounts.

3. Scroll down to the Remote Authentication Service section, check RADIUS and click the edit icon.

4. Fill in the form. Refer to the following image and table.
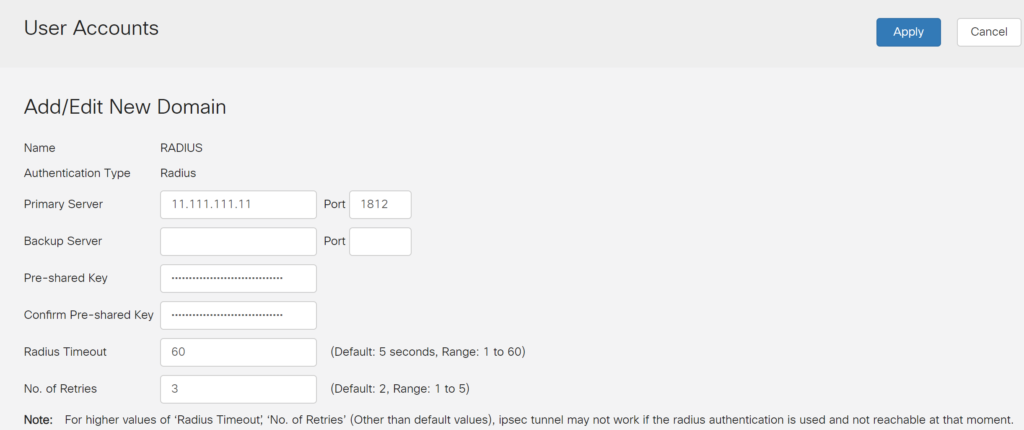
| Primary Server | Enter the IP of your Rublon Authentication Proxy server. |
| Port | Enter the port of your Rublon Authentication Proxy server. Default: 1812 |
| Pre-shared Key | Enter the RADIUS_SECRET you set in the Rublon Authentication Proxy’s config file. |
| Confirm Pre-Shared Key | Reenter the RADIUS_SECRET. |
| Radius Timeout | 60 If experiencing issues, increase to 90. |
| No. Of Retries | 3 |
5. Click Apply to save the changes. After adding a new RADIUS server, you will be redirected to the User Accounts tab. Stay on this page.
Configuring RADIUS as the Main Authentication Source for VPN Modules
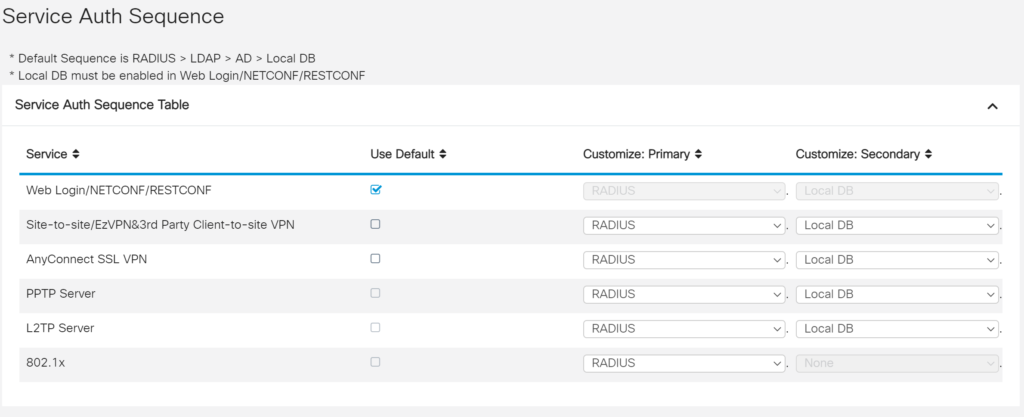
1. On the User Accounts tab, scroll all the way down to the Service Auth Sequence section and uncheck Use Default next to each desired service in the list.
Note
Configuring a group for RADIUS_CLASS_ATTR

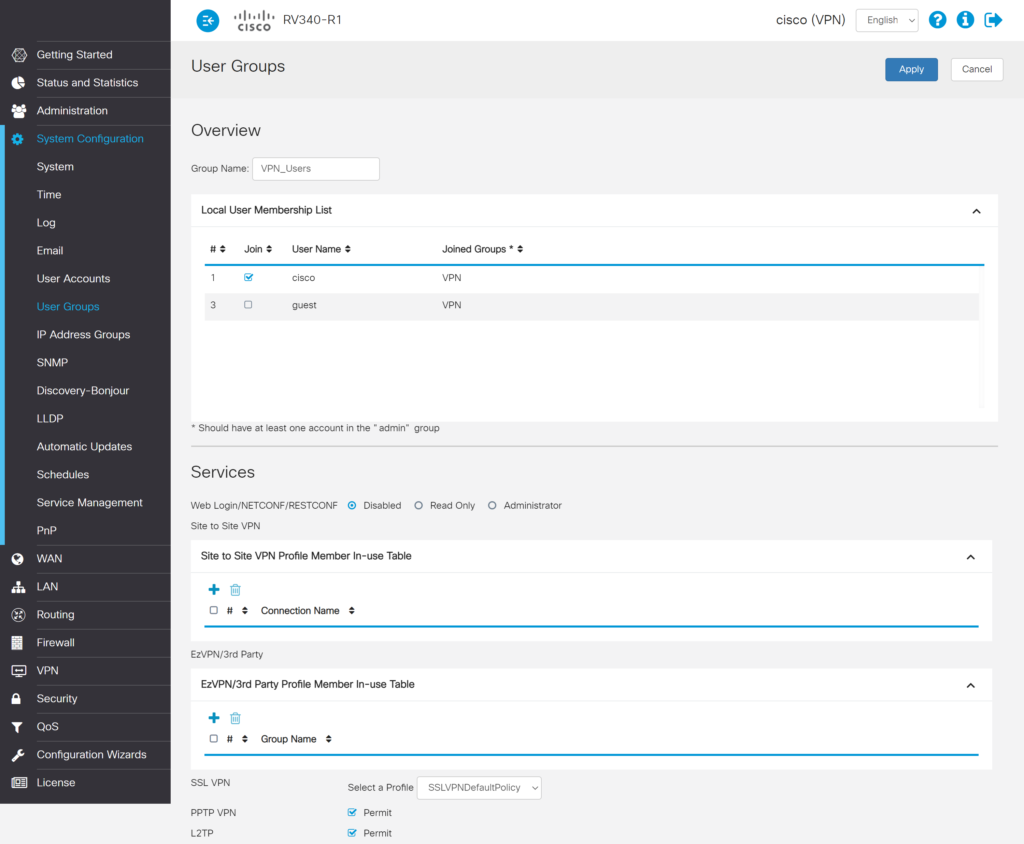
|
|
|
| Group Name | Enter a name for your group, e.g., VPN_Users. |
| Local User Membership List | If you want one or more local accounts to be members of this group, you can select them here. |
|
|
|
| Web Login/NETCONF/RESTCONF | Choose whether the members of the group you are creating should be able to log in to the Cisco RV Series Admin Panel and in what role. Select Disabled if you do not want to enable Rublon MFA for Admin Panel logins. Select Read Only to allow logging into the Cisco RV Series Admin Panel but not allow making configuration changes. Select Administrator to allow logging into the Cisco RV Series Admin Panel and making configuration changes. We recommend you disable MFA for Admin Panel logins. |
| Site to Site VPN | Do not change anything. |
| EzVPN/3rd Party | Do not change anything. |
| SSL VPN | Select the appropriate SSL VPN profile from the Select a Profile list. |
| PPTP VPN | Permit. |
| L2TP | Permit. |
| 802.1x | Optional. You can leave it unchecked. |
3. Click Apply to save the changes.
"RADIUS_CLASS_ATTR": "VPN_Users",Changing settings for L2TP VPN

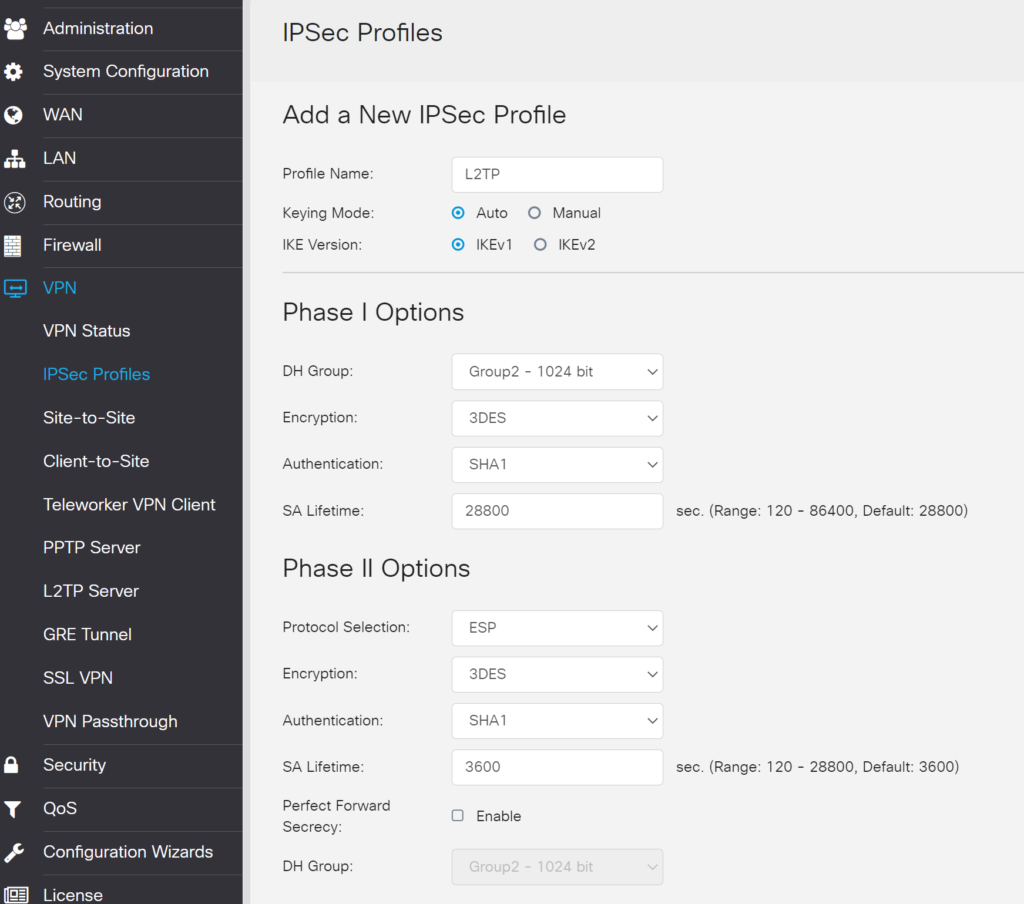
|
|
|
| Profile Name | Enter a name for your profile, e.g., L2TP. |
| Keying Mode | Auto |
| IKE Version | IKEv1 |
|
|
|
| DH Group | Group 2 – 1024 bit |
| Encryption | 3DES |
| Authentication | SHA1 |
| SA Lifetime | 28800 |
|
|
|
| Protocol Selection | ESP |
| Encryption | 3DES |
| Authentication | SHA1 |
| SA Lifetime | 3600 |
| Perfect Forward Secrecy | Uncheck. |
3. Click Apply to save the new profile.

Testing Multi-Factor Authentication (MFA) for Cisco RV Series VPN
Testing MFA for Cisco RV Series SSL VPN – AnyConnect VPN Client


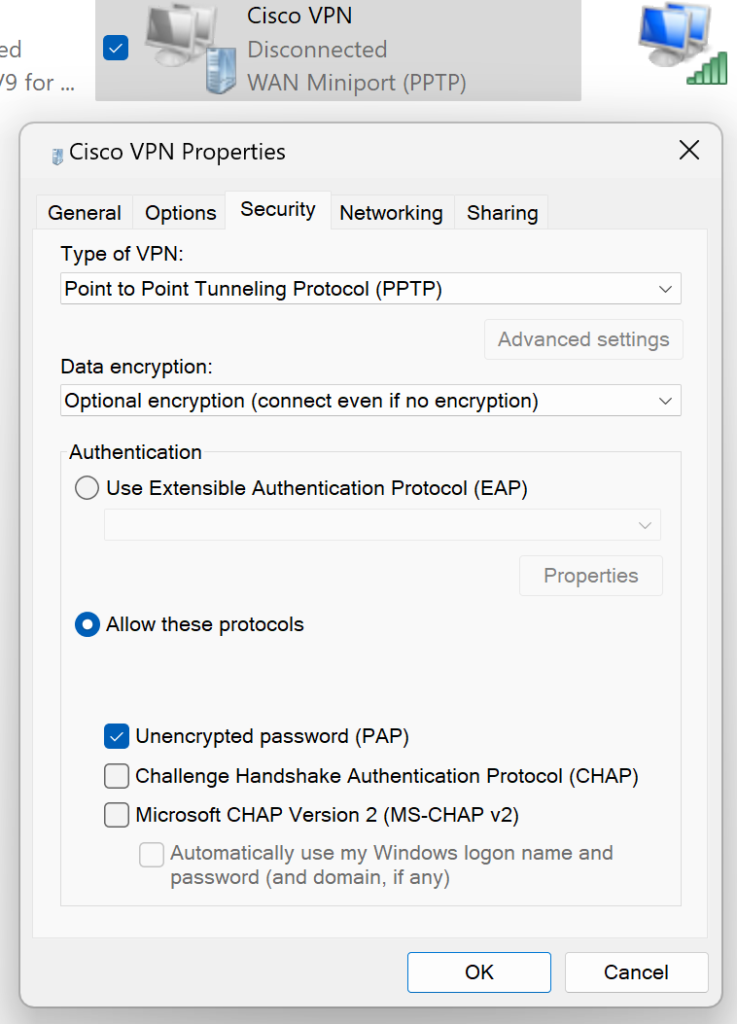
Testing MFA for PPTP VPN and L2TP VPN

2. Click Save to save your new VPN connection profile.