Last updated on July 8, 2025
Overview of MFA for ForestSafe Privileged Password Manager
Supported Authentication Methods
Before You Start Configuring MFA for EESM ForestSafe Privileged Password Manager
- Ensure you have prepared all required components.
- Create an application in the Rublon Admin Console.
- Install the Rublon Authenticator mobile app.
Required Components
Create an Application in the Rublon Admin Console
5. Copy and save the values of the System Token and Secret Key. You are going to need these values later.
Install Rublon Authenticator
Configuring Multi-Factor Authentication (MFA) for EESM ForestSafe Privileged Password Manager
Enabling Append Mode in Rublon Authentication Proxy
Configuring RADIUS in ForestSafe
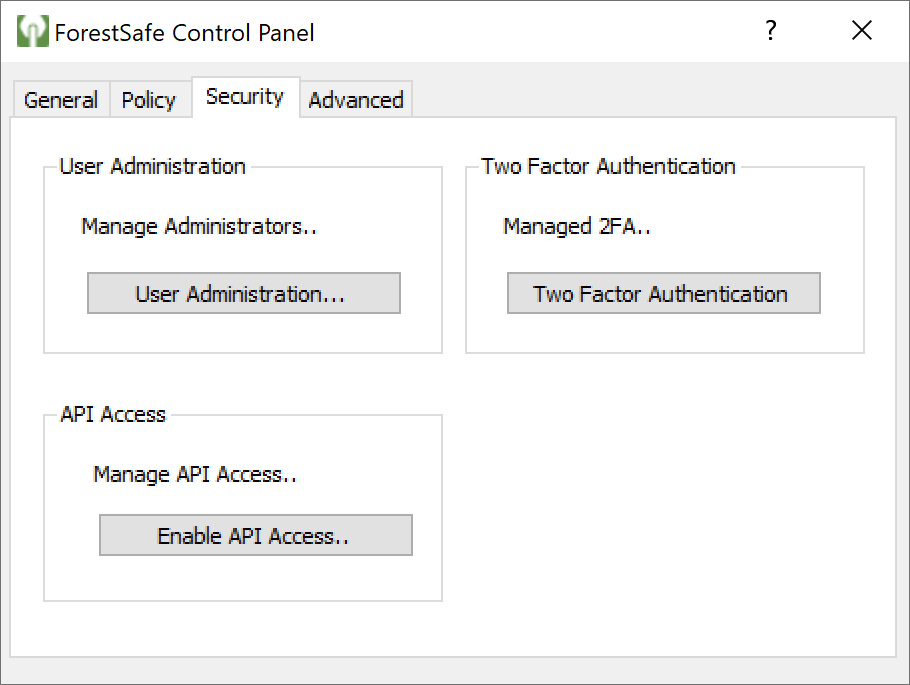
- RADIUS Server address and port SERVER:PORT – Enter the IP address and port of your Rublon Authentication Proxy server in the following form: IP:PORT, e.g., 10.0.9.18:1812.
- RADIUS Server Secret – Enter the RADIUS_SECRET you set in the Rublon Authentication Proxy’s config file.
Testing Multi-Factor Authentication (MFA) for EESM ForestSafe Privileged Password Manager
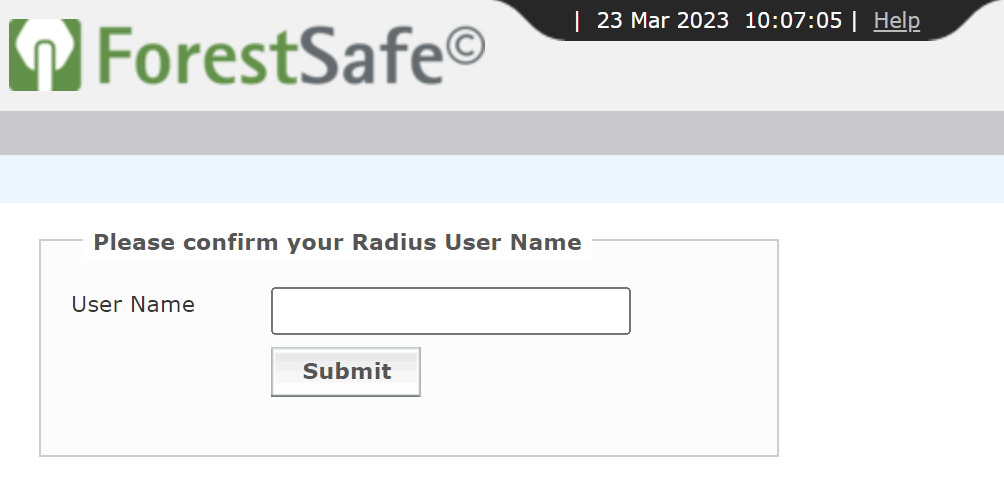
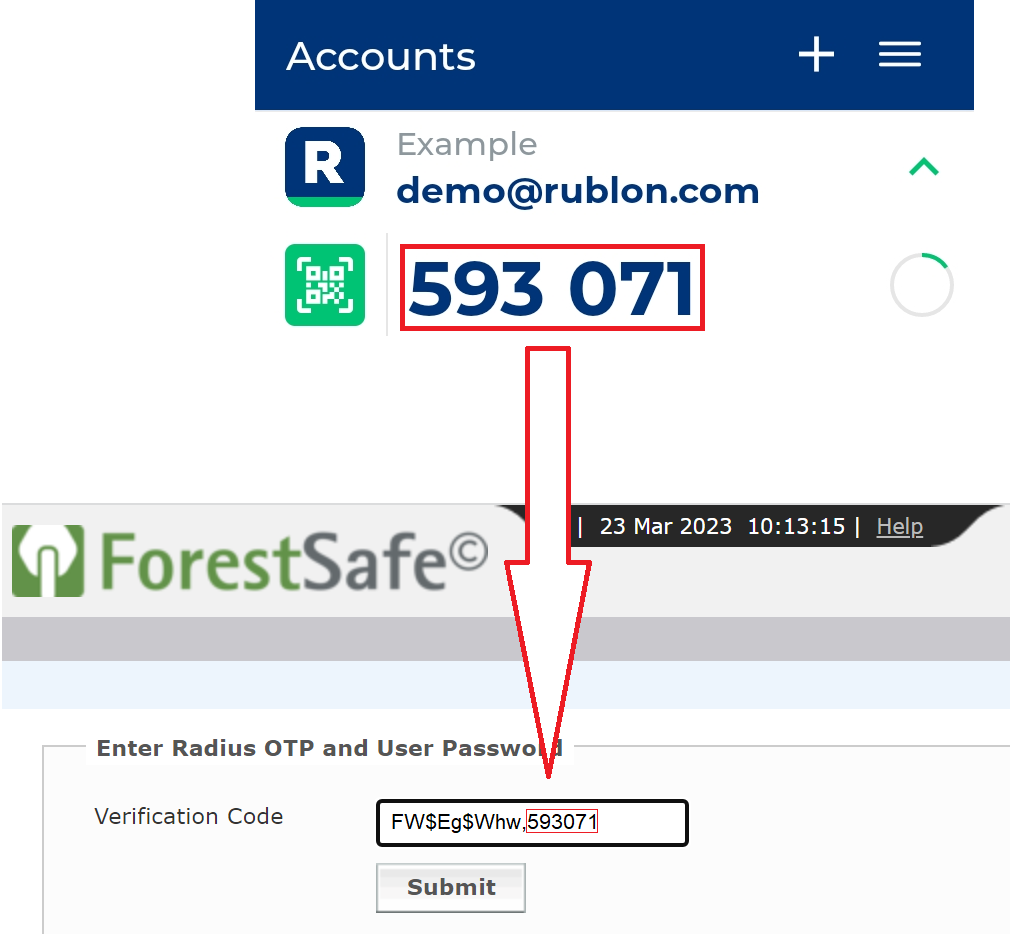
- 123456 – a Passcode (6-digit TOTP code generated by Rublon Authenticator or a third-party app like Google Authenticator or Microsoft Authenticator)
- 123456789 – a Bypass Code (9-digit code received from the administrator)
- push – a Mobile Push is sent to their phone; requires Rublon Authenticator
- email – an email message containing an Email Link is sent to their email address
- smsLink – a text message containing an SMS Link
- phoneCall – a Phone Call from Rublon
- <YubiKey OTP code> – insert the YubiKey and press the button on the key; the OTP will be typed automatically and then Enter will be pressed
Note
Note