Last updated on December 8, 2025
Overview of MFA for OpenVPN Cloud
Multi-Factor Authentication (MFA) for OpenVPN Cloud is an additional security measure requiring users to provide two verification elements in order to access OpenVPN Cloud. The first element involves entering an Active Directory / RADIUS username and password. Once entering the correct credentials, the user must perform secondary authentication using one of the available authentication methods such as a Mobile Push or Email Link. After both steps have been completed, the user successfully gains access to the resource. Multi-Factor Authentication (MFA) for OpenVPN Cloud prevents malicious actors from compromising the VPN even when they know the user’s login credentials.
Supported Authentication Methods
| Authentication Method | Supported | Comments |
| Mobile Push | ✔ | N/A |
| FIDO | – | N/A |
| Passcode | ✔ | N/A |
| SMS Passcode | – | N/A |
| SMS Link | ✔ | N/A |
| Phone Call | ✔ | N/A |
| QR Code | – | N/A |
| Email Link | ✔ | N/A |
| YubiKey OTP | ✔ | N/A |
| RFID | – | N/A |
Before you start
You need to install and configure Rublon Access Gateway itself before configuring OpenVPN Cloud to work with it. Please read the Rublon Access Gateway documentation and follow the steps in the Installation and Configuration sections. Afterward, follow the Configuration section in this document.
Configuration of OpenVPN Cloud
1. Sign in with Owner Account to your OpenVPN Cloud.
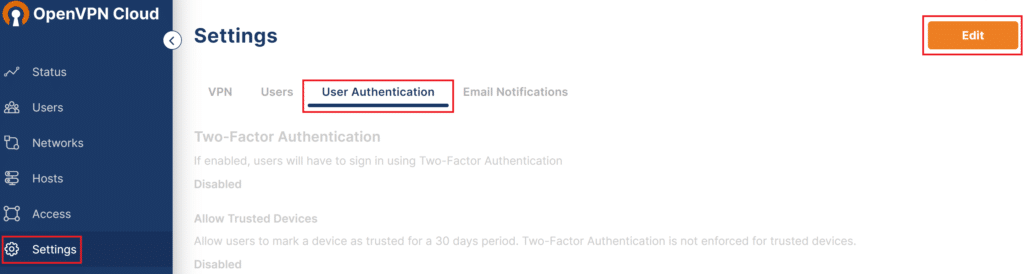
2. Go to Settings and select User Authentication.
3. Click Edit in the top right corner.
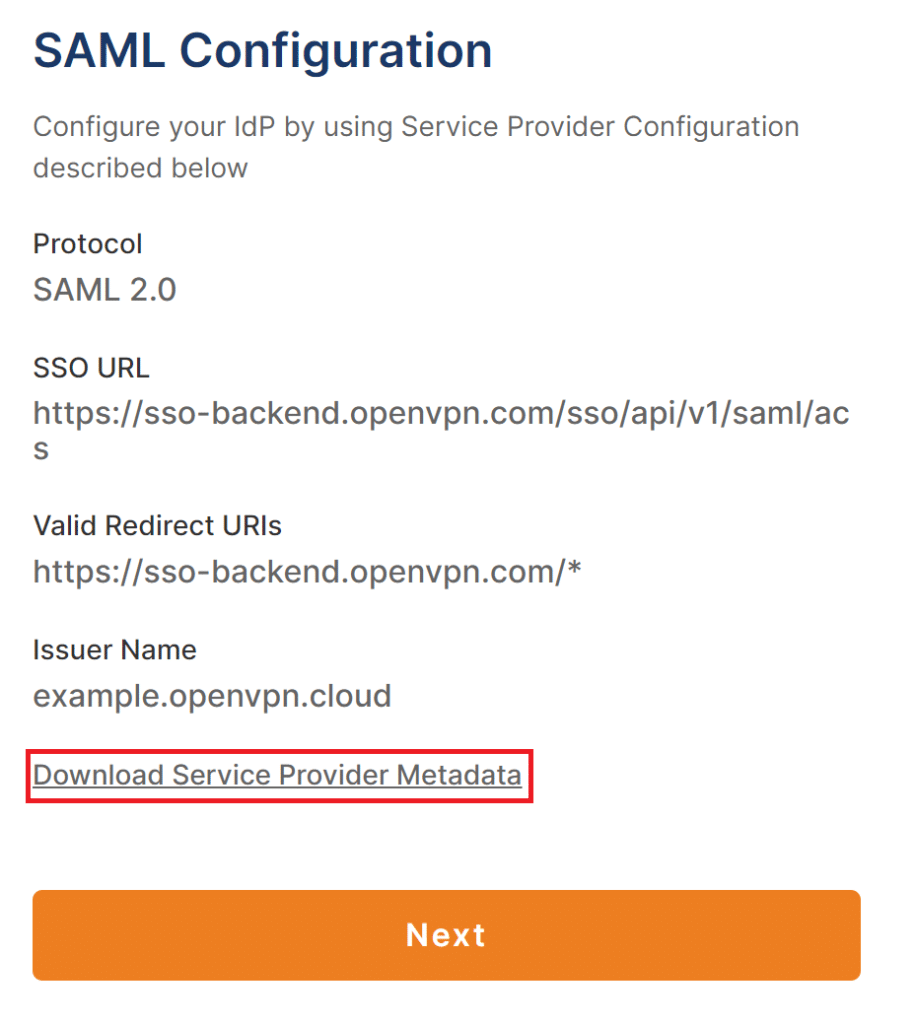
4. Select SAML in Authenticate Users Using and click View idP Configuration.
5. Set a name for your idP configuration, e.g. Rublon_Access_Gateway. This configuration will be used for SAML Authentication.
6. Click Download Service Provider Metadata to download the ServiceProviderMetadata.xml file. You are going to need this file later.
7. Do not close the OpenVPN Cloud admin panel. Log in to Rublon Access Gateway in a separate tab.
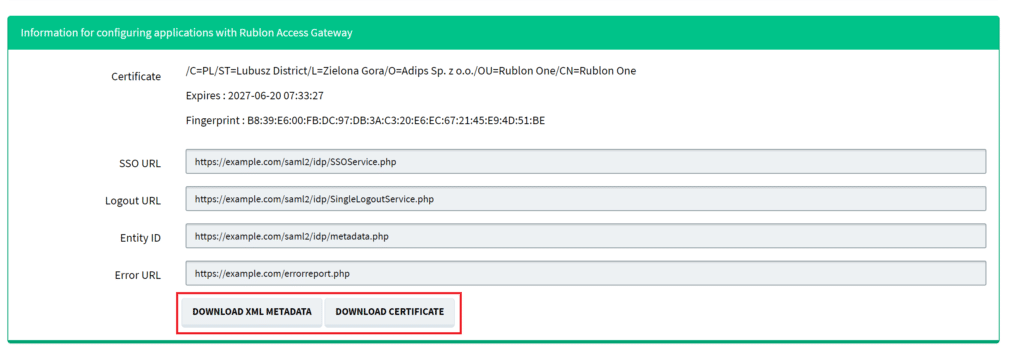
8. Click Applications and then click DOWNLOAD CERTIFICATE in the Information for configuring applications with Rublon Access Gateway section at the bottom. You are going to need this certificate later.
9. Click DOWNLOAD XML METADATA in the Information for configuring applications with Rublon Access Gateway section.
10. Get back to the OpenVPN admin panel. Open the XML metadata file you have downloaded and paste the contents of that metadata file in IdP Metadata XML.
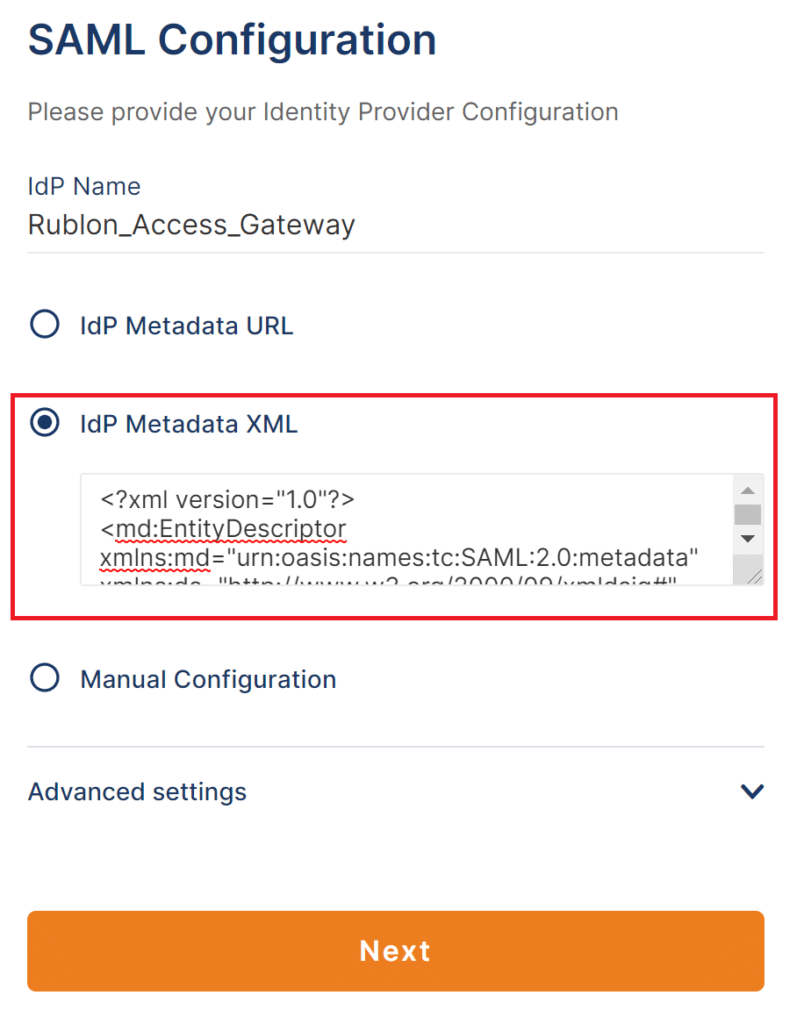
11. Click Next and then click Finish.
12 Get back to Rublon Access Gateway. Go to Applications → Add Application. Fill in the form. Refer to the following image and table.
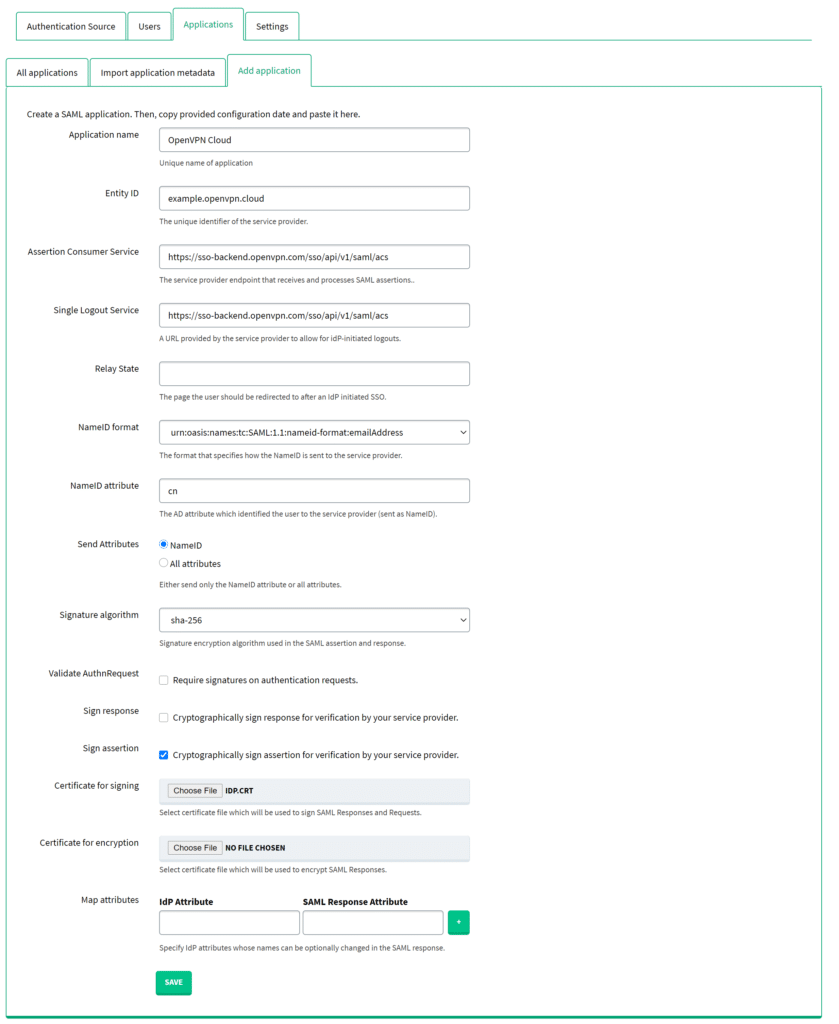
| Application name | Set a name for your application, e.g. OpenVPN Cloud. |
| Entity ID | Enter the value that comes after entityID=(without quotation marks) in the ServiceProviderMetadata.xml file you have downloaded before. |
| Assertion Consumer Service | Enter the value that comes after Location=(without quotation marks) in the ServiceProviderMetadata.xml file you have downloaded before. |
| Single Logout Service | Enter the value that comes after Location=(without quotation marks) in the ServiceProviderMetadata.xml file you have downloaded before. |
| NameID attribute | Enter cn. |
| Validate AuthnRequest | Uncheck. |
| Sign assertion | Check. |
| Certificate for signing | Upload the certificate you have downloaded in Step 8. |
13. Your configuration is now complete. You can log in to OpenVPN with Rublon 2FA.
Log in to OpenVPN Cloud using MFA for OpenVPN Cloud
1. Click Sign In to initiate Rublon 2FA.

2. You will be redirected to the Rublon Access Gateway login page.
3. Provide your username and password. Click SIGN IN. Rublon Prompt will appear with a selection of various authentication methods from Rublon. Let’s choose Mobile Push.

4. You will be sent a push notification. Tap APPROVE.

5. You will be successfully logged in to OpenVPN Cloud.
Troubleshooting
If you encounter any issues with your Rublon integration, please contact Rublon Support.