Last updated on July 8, 2025
Overview of MFA for Parallels RAS
Rublon MFA for Parallels RAS enables Multi-Factor Authentication (MFA) / Two-Factor Authentication (2FA) during VPN connections. If a user enters the correct username and password, they proceed to the secondary authentication method. If the user is unable to complete the extra method, Rublon will deny their access, stopping any potential intruder from gaining access.
Supported Authentication Methods
Before You Start Configuring MFA for Parallels RAS
Before configuring Rublon MFA for Parallels RAS:
- Ensure you have prepared all required components.
- Create an application in the Rublon Admin Console.
- Install the Rublon Authenticator mobile app.
Required Components
1. User Identity Provider (IdP) – You need an external Identity Provider, such as Microsoft Active Directory, OpenLDAP, or FreeRADIUS.
2. Rublon Authentication Proxy – Install the Rublon Authentication Proxy if you have not already.
3. Parallels RAS Application Server – Ensure you have correctly configured Parallels RAS, especially that user logins work properly before deploying MFA for Parallels RAS.
Create an Application in the Rublon Admin Console
1. Sign up for the Rublon Admin Console. Here’s how.
2. In the Rublon Admin Console, go to the Applications tab and click Add Application.
3. Enter a name for your application (e.g., Parallels RAS) and then set the type to Rublon Authentication Proxy.
4. Click Save to add the new application in the Rublon Admin Console.
5. Copy and save the values of the System Token and Secret Key. You are going to need these values later.
Install Rublon Authenticator
Some end-users may install the Rublon Authenticator mobile app. So, as a person configuring MFA for Parallels RAS, we highly recommend you install the Rublon Authenticator mobile app, too. Thanks to that, you will be able to test MFA for Parallels RAS via Mobile Push.
Download the Rublon Authenticator for:
Configuring Multi-Factor Authentication (MFA) for Parallels RAS
Follow the following instructions to set up MFA for Parallels RAS.
Configuring Rublon Authentication Proxy as RADIUS Server
1. Log in to Parallels RAS Application Server Console.
2. Select Connection from the left pane and then select the Multi-Factor authentication tab.

3. Click the + (plus) icon in the upper-right corner and then select RADIUS → RADIUS….

4. In the new window, enter the following information:
- Name: Name for your RADIUS server (e.g., Rublon Authentication Proxy)
- Description: Optional description for your RADIUS server
- Themes: Check Default.

5. Click next and fill in the information about your RADIUS server. Refer to the following image and table.

| Display Name | Enter a name for the Rublon Authentication Proxy server that will be displayed for users during logins, e.g., Rublon. |
| Primary Server | Enter the IP or hostname of your Rublon Authentication Proxy server. |
| Secondary Server | If you have deployed a secondary Rublon Authentication Proxy server and would like to use it interchangeably with the primary server, you can optionally add a secondary server. Otherwise, leave it empty. |
| HA Mode | If you have added a secondary Rublon Authentication Proxy server, then here you can choose how to distribute packets between the two servers. Otherwise, leave it empty. |
| Port | Enter the port of your Rublon Authentication Proxy server. Default: 1812 |
| Timeout | 60 |
| Retries | 3 |
| Secret key | Enter the RADIUS_SECRET you set in the Rublon Authentication Proxy’s config file. |
| Password encoding | PAP |
6. All other options are optional. Click Finish to save your RADIUS MFA provider configuration.
Enabling Mobile Push and Email Link
Configuring MFA for Parallels RAS is unique in that the RADIUS MFA provider only supports the TOTP authentication method by default. To enable other methods (such as Rublon’s Mobile Push and Email Link), you have to add them manually as the so-called actions. Let’s do this!
1. On the Multi-Factor authentication tab, double-click the RADIUS server you have just created. In the newly-opened window, go to the Automations tab.
2. Click the + (plus) icon in the upper-right corner and fill in the form. Refer to the following image and table.
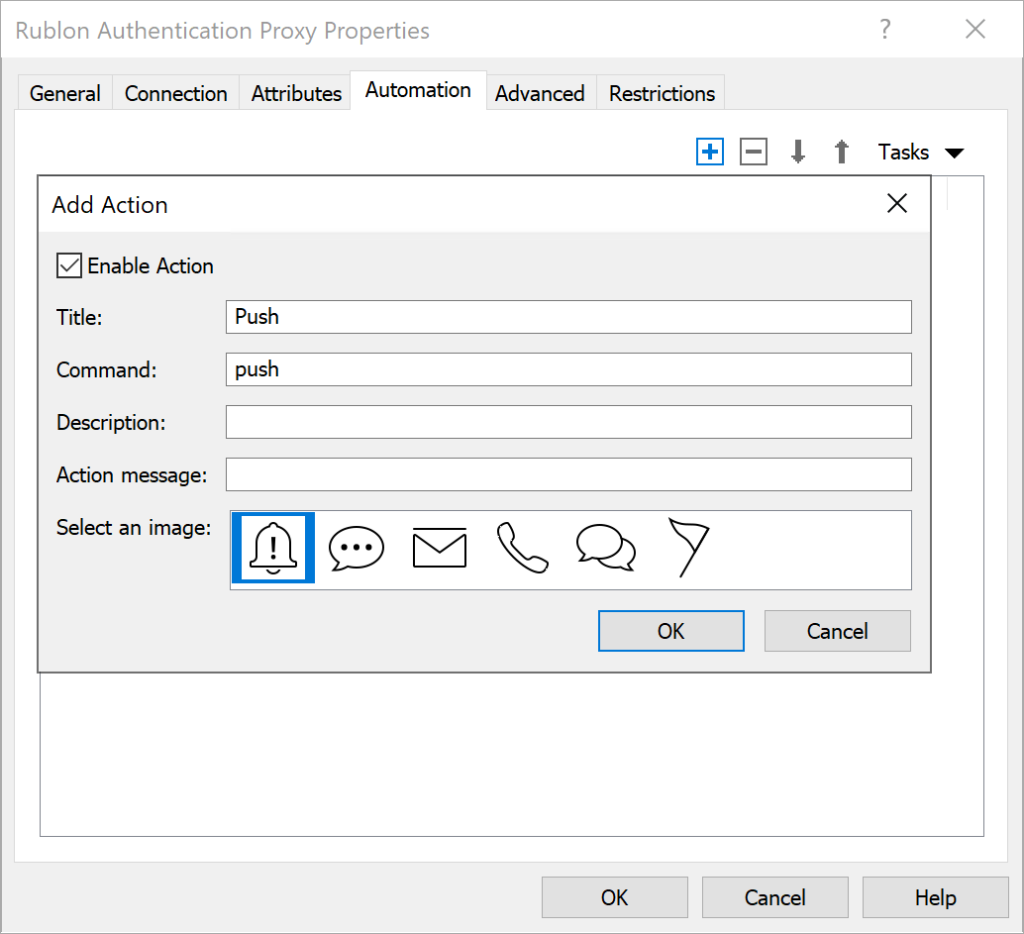
| Enable Action | Check. |
| Title | Push |
| Command | push |
| Description | Enter an optional description. |
| Action message | Enter an optional message displayed when this action is performed. |
| Select an image | Select the icon displayed next to the action in the login panel of the Parallels RAS portal. We recommend you choose the bell icon for Mobile Push. |
3. Click OK to save the changes, and click the + (plus) icon in the upper-right corner again. Fill in the form. Refer to the following image and table.
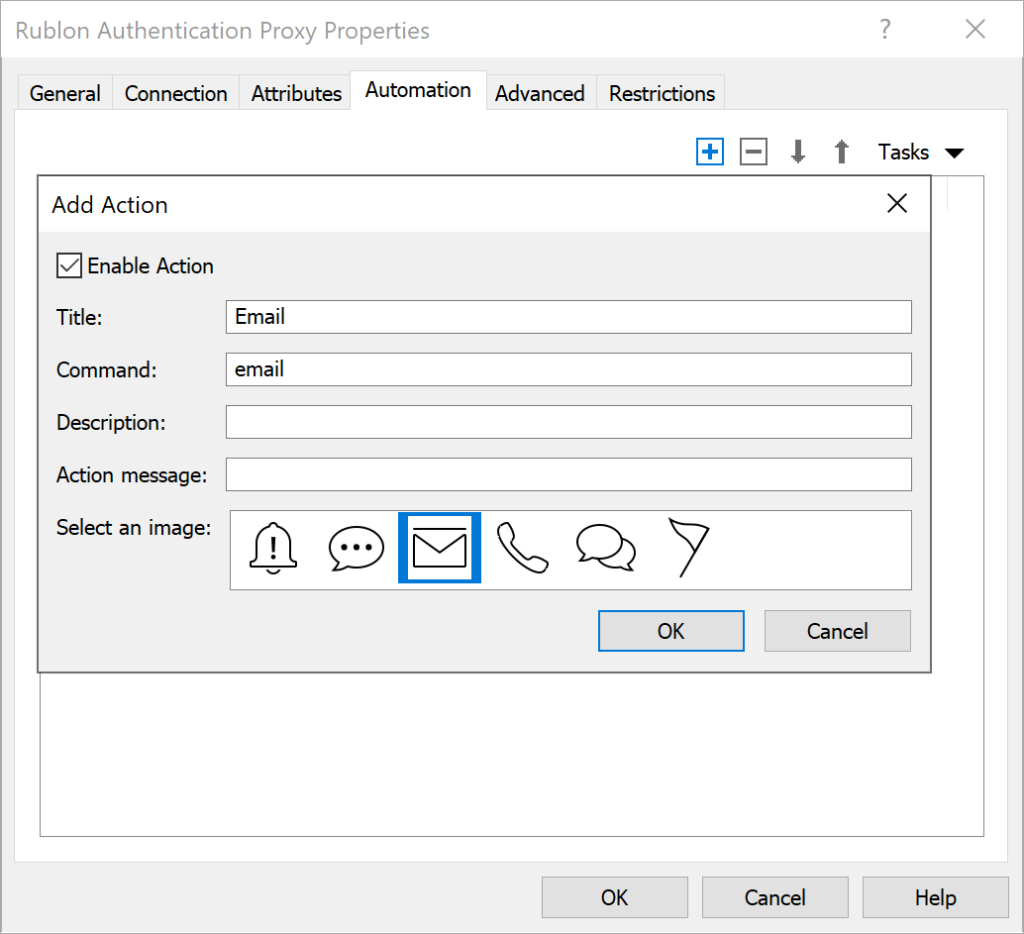
| Enable Action | Check. |
| Title | |
| Command | |
| Description | Enter an optional description. |
| Action message | Enter an optional message displayed when this action is performed. |
| Select an image | Select the icon displayed next to the action in the login panel of the Parallels RAS portal. We recommend you choose the envelope icon for the Email Link method. |
4. Click OK to save the changes. Ensure there are two actions in the Automation tab and click OK to close the properties window.
5. Select the Authentication tab and set the options as seen in the image and table.
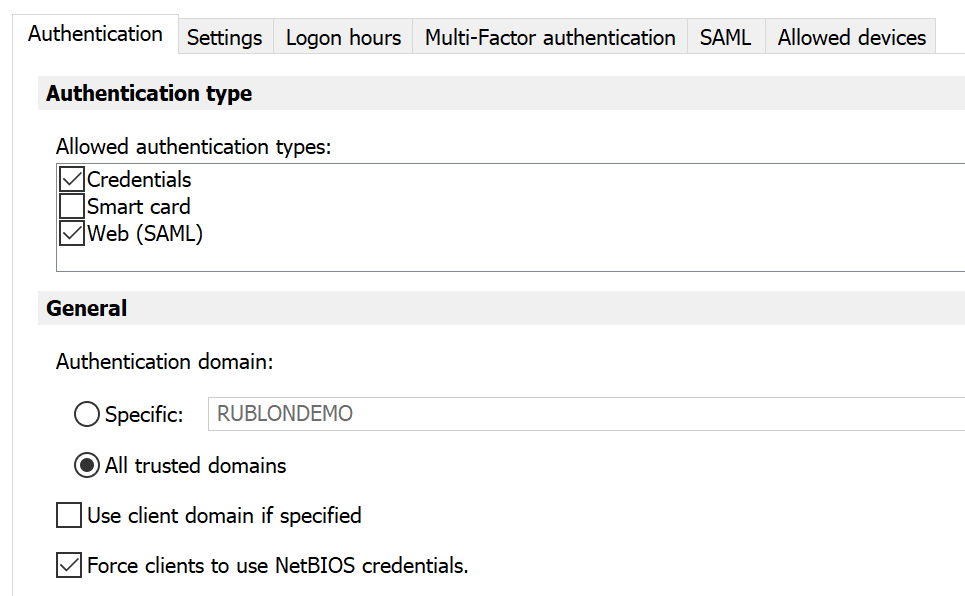
| Allowed authentication types | Check Credentials and Web (SAML). |
| Authentication domain | Select All trusted domains. |
| Use client domain if specified | Uncheck. |
| Force clients to use NetBIOS credentials | Check. |
6. Click the Apply button in the left-bottom corner to confirm all your changes.
Modifying the Rublon Authentication Proxy Config File
Note
Testing Multi-Factor Authentication (MFA) for Parallels RAS (Browser)
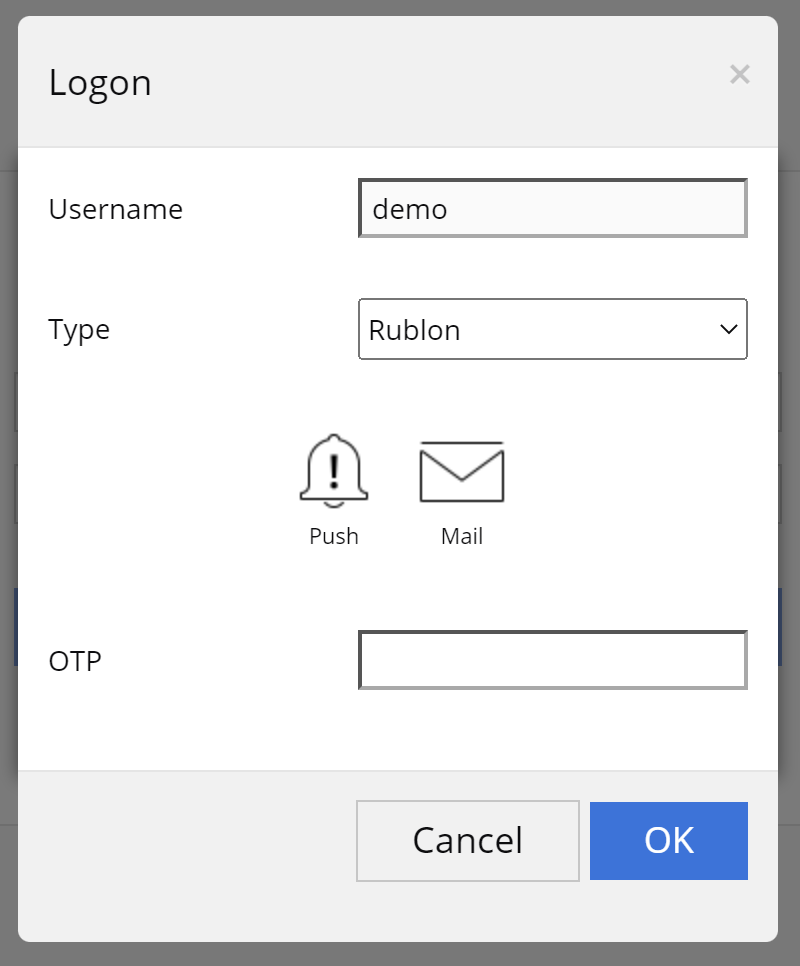
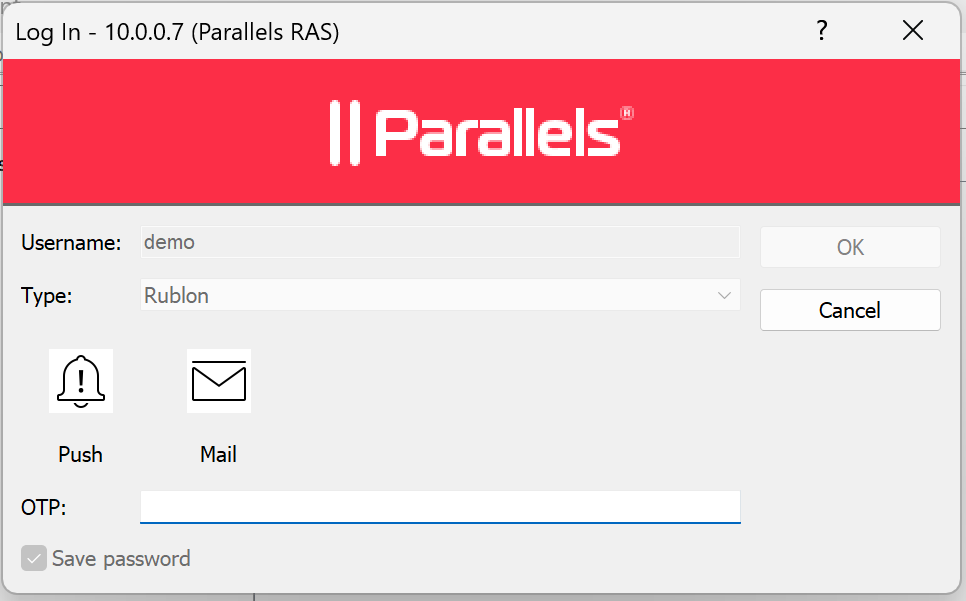
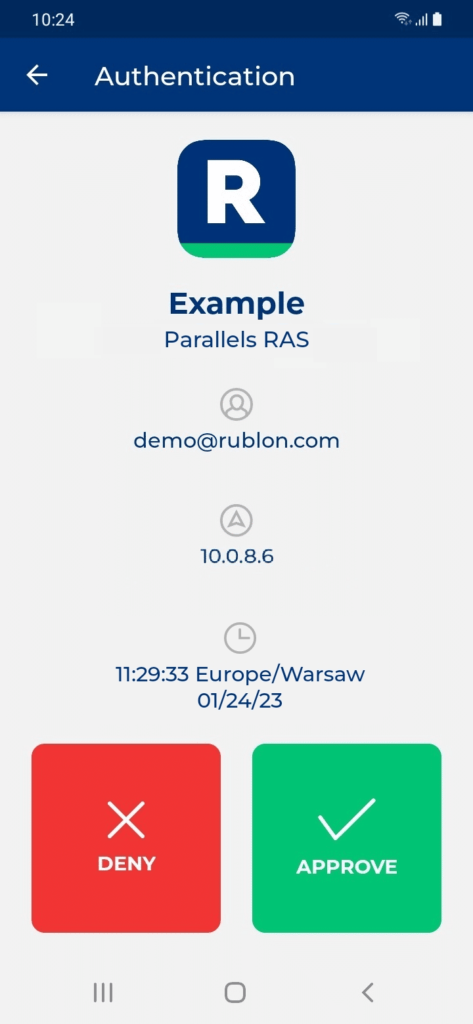
3. Rublon will send a Mobile Push authentication request to your phone. Tap APPROVE.
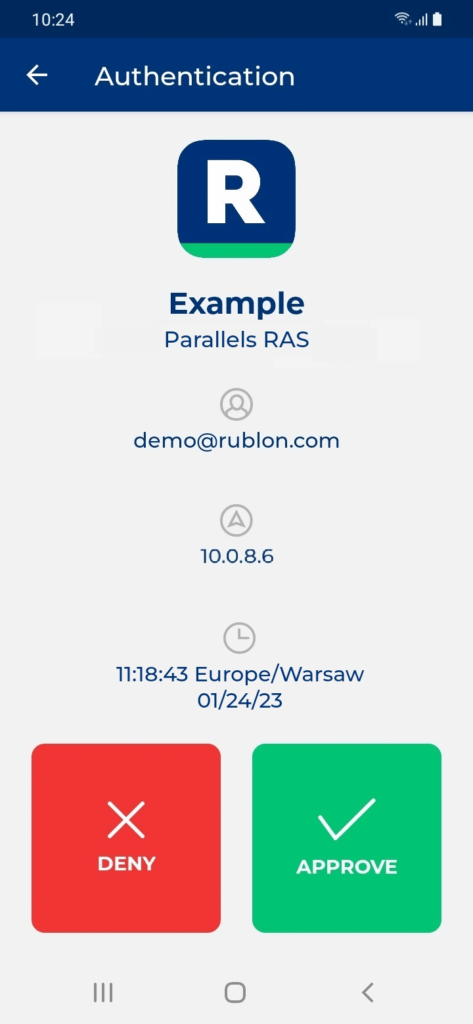
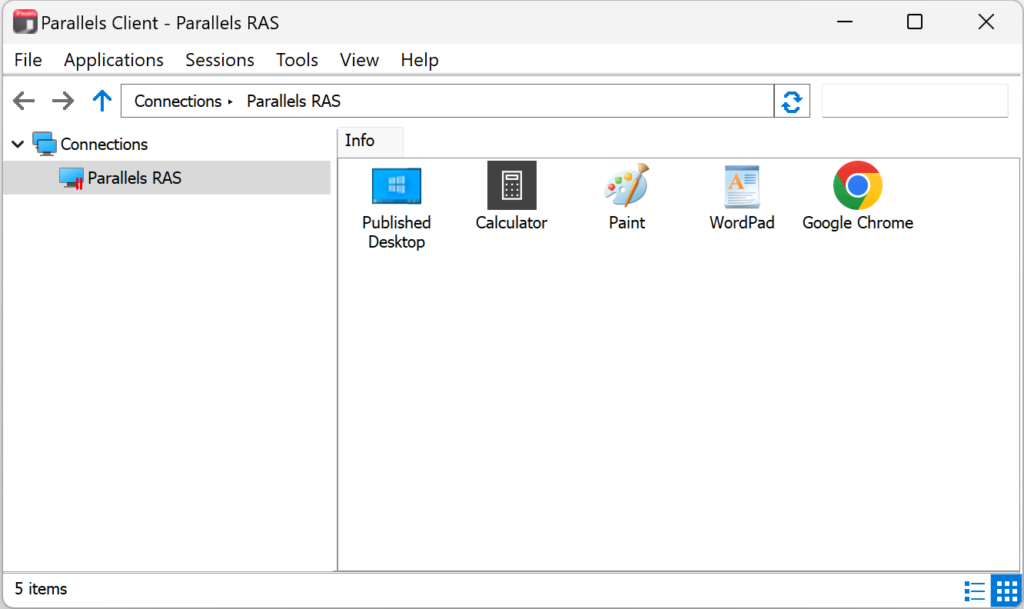
4. You will be logged in.
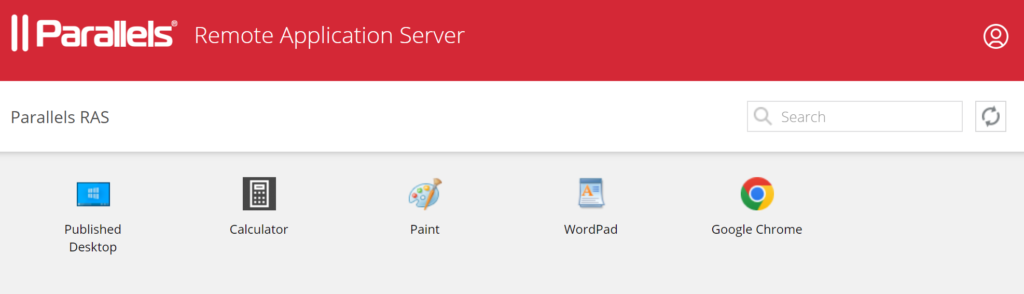
Testing Multi-Factor Authentication (MFA) for Parallels RAS (Parallels Client)
In this example, we assume you have already downloaded the Parallels client and added a connection in your Parallels Client.
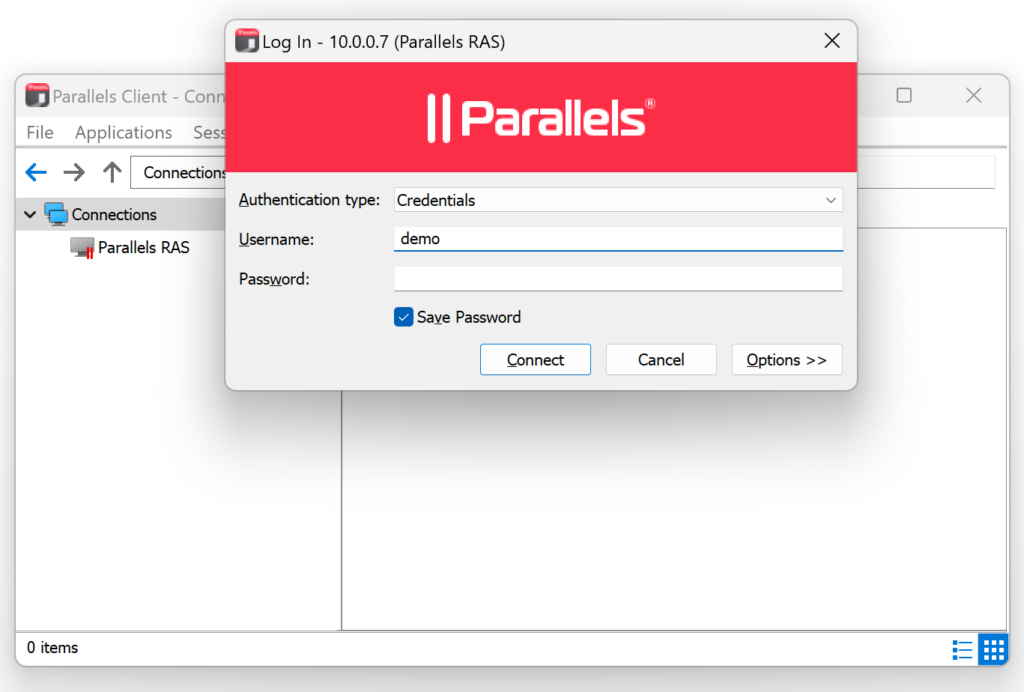
1. On the login form, enter your login credentials and click Connect.