Last updated on December 8, 2025
Overview
Supported Authentication Methods
Before you start
Configuration
1. Log in to Pulse admin panel.
2. Go to Authentication → Auth. Servers.

3. Select SAML Server in the New dropdown, and click New Server….

4. Fill in the fields in the Settings tab. Refer to the following image and table.

5. Click Save Changes.
6. Scroll down to the bottom of the page and click Download Metadata. You are going to need that XML file later.

7. Do not close Pulse admin panel. Log in to Rublon Access Gateway in another tab.
8. Go to Applications → Import application metadata.
9. Enter a name for your application, e.g. Pulse. Select the XML file you have downloaded before, and click UPLOAD.
10. Your application will appear on the applications list in the All applications subtab.

11. Get back to Pulse admin panel. Go to Users → User Realms → New User Realm….

12. Set a Name for your new realm, e.g. Rublon Access Gateway.
13. Select the previously created Rublon Access Gateway authentication server in the Authentication dropdown.
14. Click Save Changes.

15. Select the Role Mapping tab and click New Rule….
16. Set a name of your choice for your new rule.
17. Set Rule:If username… to is *.
18. Assign a Users role. Select Users on the Available Roles list and click Add ->.
19. Click Save Changes.
20. Go to Authentication → Signing In → Sign-in Policies.
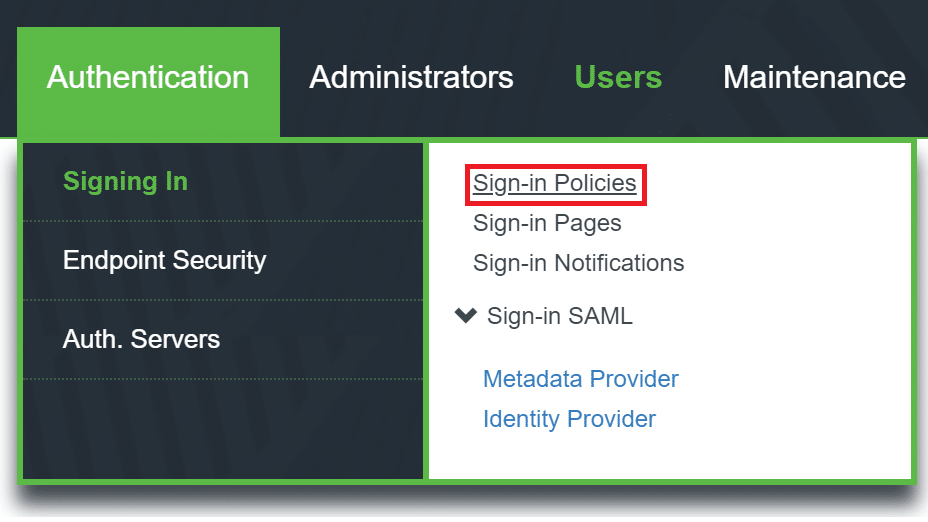
21. Click New URL… to create a new URL.
22. Set Sign-in URL to */saml/.
23. Set Sign-in page to Default Sign-in page.
24. Select User picks from a list of authentication realms and select the Rublon Access Gateway realm you have created before. To do this, just select Rublon Access Gateway on the Available realms list and click Add ->.

25. Click Save Changes.
26. Your configuration is now complete. Your users can now log in to Pulse Connect Secure SSL VPN with Rublon 2FA enabled.
Log in to Pulse Connect Secure with Rublon 2FA
This example portrays logging in to Pulse Connect Secure SSL VPN via a web browser.



5. You will be successfully logged in to Pulse SSL VPN.

Troubleshooting
If you encounter any issues with your Rublon integration, please contact Rublon Support.