Last updated on December 12, 2024
Note
This is archived documentation for Rublon Authentication Proxy version 2.5.1. This archived version is intended for users who have already deployed version 2.5.1 and cannot update or install the newest version.
We cannot guarantee the instructions in this archived version are up to date. For the most up-to-date instructions, please refer to the newest version.
Overview
Rublon Authentication Proxy is an on-premises RADIUS proxy server that allows you to enable Multi-Factor-Authentication (MFA/2FA) on any service that supports the RADIUS authentication protocol.
Supported systems:
- Linux (tested on CentOS, Ubuntu)
- Windows Server 2008 R2
- Windows Server 2012
- Windows Server 2016
- Windows Server 2019
- Windows Server 2022
Available authentication methods:
- Mobile Push
- Email Link
- Mobile Passcode (TOTP)
How does Rublon Authentication Proxy work?
After you deploy Rublon Authentication Proxy as an on-premises service and set it up as a RADIUS authentication source on one or more services (e.g. OpenVPN), Rublon Authentication Proxy starts listening for any incoming authentication requests.
When you initiate login to one of the integrated services, Rublon Authentication Proxy receives an Access-Request. Then, Rublon asks for your IdP credentials. If user credentials you provided are correct, Rublon initiates the second step of authentication.
Once you complete the second step of authentication, Rublon Authentication Proxy returns an Access-Accept response, which concludes 2FA. The following diagram shows a simplified, successful authentication process:
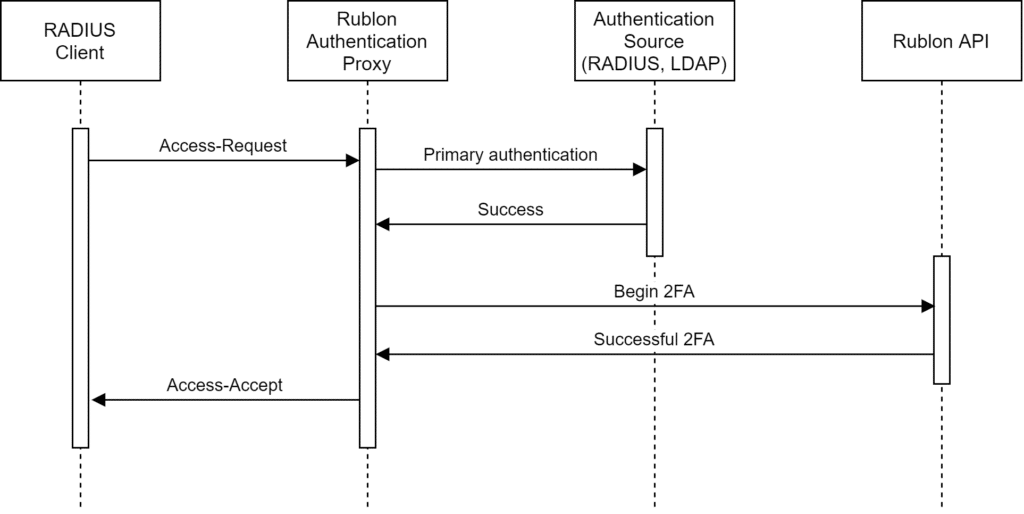
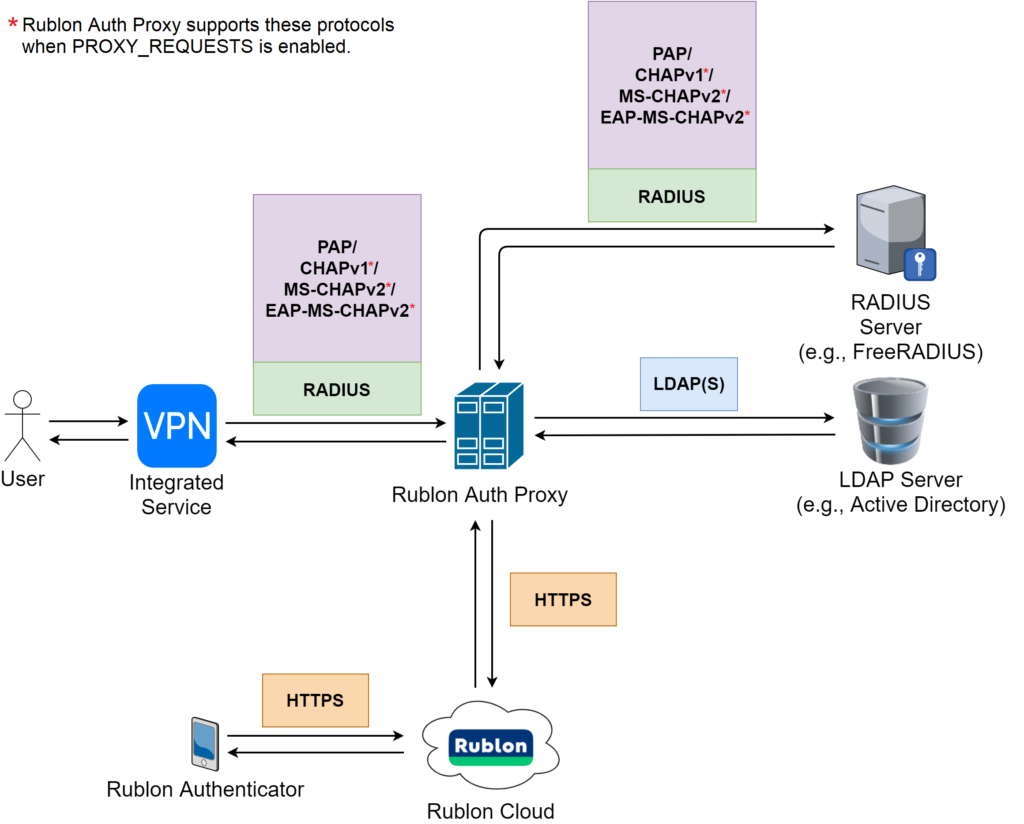
The following diagram portrays a Rublon Authentication Proxy login flow along with the names of protocols used in each part of the transaction.
Before you start
Rublon Authentication Proxy is not an Identity Provider (IdP). Rublon Authentication Proxy is a RADIUS proxy server that pulls users from an external IdP. As a result, you have to use (or set up) an external IdP that manages your user identities.
List of tested and verified IdPs:
- Active Directory
- OpenLDAP
- FreeIPA
- FreeRADIUS (standalone, full version)
- Cisco ACS
- Microsoft NPS (Network Policy Server)
Rublon requires a user’s email address to perform 2FA. Consequently, every user who wants to log in using Rublon Authentication Proxy must have their email address assigned in the Rublon Admin Console. If the user has an email address added to their IdP account, Rublon will automatically add this email address to the Rublon Admin Console during user enrollment. Otherwise, you must manually add the user’s email address in the Admin Console.
Rublon Authentication Proxy does not support RADIUS Accounting. As a result, Rublon Authentication Proxy does not listen on port 1813. Rublon may add support for RADIUS Accounting in the future. In the meantime, turn off RADIUS Accounting to avoid potential errors.
Install Rublon Authentication Proxy
You can install Rublon Authentication Proxy on Linux or Windows.
Linux
- If your Linux distribution uses glibc (GNU libc) version 2.29 or higher, download the rublonauthproxy package.
- If your Linux distribution uses glibc (GNU libc) version 2.28 or lower, download the rublonauthproxy_py36 package.
More info about glibc version
We strongly recommend you install Rublon Authentication Proxy on a Linux distribution that uses glibc (GNU libc) version 2.29 or higher. However, if your Linux distribution uses glibc version lower than 2.29, you can download this Rublon Authentication Proxy package.
You can check your Linux distribution’s glibc version using rpm or ldd. Some of the known Linux distributions with glibc lower than 2.29:
• RHEL 6
• RHEL 7
• CentOS 7
• Debian 9
- Deploy rublonauthproxy-latest in the desired location on the server and unpack it (make sure to change the file name when copy-pasting the command below).
tar -xzf rublonauthproxy-X.Y.Z.tgz - Go to the unpacked folder:
cd rublonauthproxy - Create a service file:
make service - Move the created service file to /lib/systemd/system:
mv rublon.service /lib/systemd/system - Reload daemon services:
systemctl daemon-reload - Create a rublonauthproxy/config/config.json file based on config.example.json (you can use our minimal config file templates).
Windows
- Download the Rublon Authentication Proxy installer.
- Launch the installer with administrator rights and follow the instructions to complete the installation.
- Modify the Rublon Auth Proxy\config\config.json file based on config.example.json.
Note
Some antivirus software, such as CrowdStrike and Kaspersky, may interfere with the installation or operation of the Rublon Authentication Proxy. To avoid this problem, please add Auth Proxy to the list of exceptions or trusted applications in your antivirus settings.
Configure Rublon Authentication Proxy
The config.json configuration file must be located inside the rublonauthproxy/config directory. Use a proper JSON convention. All property names must be uppercase.
Example configuration templates are the easiest way to start a configuration. Find them at the bottom of this document. Templates are also located inside the rublonauthproxy/config directory after you unpack Rublon Authentication Proxy.
If you would like to use RADIUS as an authentication source, you have to configure your RADIUS server first.
To obtain RUBLON_TOKEN and RUBLON_SECRET, sign in to the Rublon Admin Console and add a new application of type Rublon Authentication Proxy.
Note that after every change in the config.json file, you must restart the Rublon Authentication Proxy service for the changes to take effect.
Sections
PROXY
| RUBLON_API | Rublon API host (https://core.rublon.net) |
| RADIUS_SECRET | The RADIUS secret that services will use to communicate with Rublon Authentication Proxy. Note that even if you use LDAP as your authentication source, you still need to set the RADIUS_SECRET. You have to generate this value yourself. We recommend you use a password-generating tool to generate a strong and secure RADIUS secret. |
| CLIENT_IP_ATTR | RADIUS attribute that contains an IP address, which will be displayed during the user authentication process, e.g. “NAS-IP-Address”. If this attribute is not found within the request authentication packet, the IP address found in the UDP datagram will be used. It will usually be a local IP address. Case-sensitive. Default: “Calling-Station-Id” |
| DEBUG | Whether to log more verbose information to log files. Default: false |
| REMOVE_LOGS_OLDER_THAN | Logs are stored within a day range. This number indicates how many log files should be kept. If the number of log files reaches this value, the oldest log file is overridden by the newest. Default: 7 |
| USE_HOSTS_WHITELIST | Indicates whether to use the hosts IP whitelist. If set to true, Rublon Authentication Proxy will drop all the packets from hosts not listed inside the config/hosts.json file. Default: false |
| SERVERS | An array of JSON objects containing server configuration. See the server subsection below. You must provide at least one server configuration. |
| AUTH_TIMEOUT | Time limit (in seconds) for a user to finish 2FA. After that time the login request will be rejected and the user will have to re-authenticate. Default: 90 |
SERVERS
This subsection describes the possible options of a single element in the “SERVERS” array inside the “PROXY” section. See the configuration example for more details.
| IP | IP address the proxy will be listening on. If left empty, Rublon Authentication Proxy will be listening on 0.0.0.0. |
| PORT | The port the proxy will be listening on. If you configure more than one server, make sure to provide different ports for each server. Default: 1812 |
| MODE | “standard” – log in using a predefined 2FA auth method, or using Append Mode. “challenge” – use Radius Challenge. Rublon Authentication Proxy will respond with the AccessChallenge packet and wait for the Mobile Passcode provided in the next request “nocred” – specific system integration. Rublon Authentication Proxy will search for user email in AD, and then perform 2FA against Rublon. Default: “standard” To learn more about Auth Proxy Modes, refer to Rublon Authentication Proxy Modes Explained. |
| AUTH_SOURCE | Either “LDAP” or “RADIUS”. Indicates which authentication source should be used for primary authentication. If you have more than one authentication source (e.g. two LDAP servers), add these authentication sources to the configuration file with names in the following form: “LDAP_X” (e.g. “LDAP_1” and “LDAP_2”) and use these names in the “AUTH_SOURCE” property. You can specify backup authentication sources by separating them by a comma, e.g., “LDAP,LDAP_2”. See the configuration example for more details. |
| USE_APPEND_MODE | Available only in “standard” mode. Allows the user to choose the authentication method by appending it to the password. More details can be found here. Default: false |
| APPEND_MODE_SEPARATOR | If “USE_APPEND_MODE” is set to true, AppendMode will use this value to extract the appended auth method used by the user. Default: “,” (comma) |
| RUBLON_TOKEN | Token of an application with type Rublon Authentication Proxy added in the Applications tab of the Rublon Admin Console |
| RUBLON_SECRET | Secret of an application with type Rublon Authentication Proxy added in the Applications tab of the Rublon Admin Console |
| AUTH_METHOD | The authentication method used for 2FA. Valid options are “push” and “email”. You can provide an array of values here, e.g. “push,email”. In this case, if “push” fails, “email” will be used instead. Default: “email” |
| FAIL_MODE | Either “bypass” or “deny”. Indicates whether the user’s access should be bypassed or denied when connection issues with a Rublon server occur. Default: “bypass” |
| RADIUS_CLASS_ATTR | The RADIUS CLASS attribute which will be sent in the “Access-Accept” response by the proxy. |
| USE_USERNAME_AS_EMAIL | Allows using the username as an email address. If the username is not a valid email address, Rublon Authentication Proxy fetches the email address from the authentication source. Default: false |
LDAP
You can configure multiple LDAP authentication sources by adding more than one LDAP section suffixed with “_” (underscore), e.g. “LDAP_2”. See the configuration example to find out how to do it.
| HOST | Hostname or IP address of Active Directory used for primary authentication. |
| PORT | LDAP port used for primary authentication. By default 389 is used for “plain” connection (LDAP) and 636 for “ssl” (LDAPS). |
| SEARCH_DN | Rublon uses the Distinguished Name to search for groups of users that will authenticate with the Rublon Authentication Proxy. This is usually your company’s AD FQDN. Example: dc=example,dc=com Here’s how to find FQDN. |
| TIMEOUT | Time (in seconds) after which LDAP connection attempt will be aborted and access rejected. Default: 10 |
| USERNAME_ATTRIBUTE | Username attribute used to log in. Default: sAMAccountName |
| ACCESS_USER_DN | The full Bind DN of a user that has Read rights in Active Directory. This account will be used for user searches. We suggest creating an additional user with Read-only rights. Here’s how to find Bind DN. |
| ACCESS_USER_PASSWORD | Password of the user in ACCESS_USER_DN. |
| SECURITY_GROUP_DN | Distinguished name of a group whose users will be authenticated against. If not set, all users found by using SEARCH_DN will be able to log in. |
| CUSTOM_FILTER | Rublon Authentication Proxy will grant access only to the users matching this LDAP filter. Use standard LDAP filter syntax. |
| TRANSPORT TYPE | “plain” – do not use encryption when connecting via LDAP, not recommended. “ssl” – use SSL encryption, trust certificates located inside the certs directory if present. “starttls” – start with a normal connection and then immediately switch to an encrypted one. Default option is: “plain” |
| CERT_DIR_PATH | Path to the directory containing certificates for the SSL connection. Certs should be in .pem format. One cert per file. By default, Rublon Authentication Proxy will search inside the config/certs directory. |
| EMAIL_ATTRIBUTE | Rublon needs a user’s email address to link the user to their Rublon account. EMAIL_ATTRIBUTE allows you to choose which Active Directory attribute to use as an email attribute. If you have a custom AD attribute that stores email addresses, then provide the name of this AD attribute here. Default: “mail” |
RADIUS
You can configure multiple RADIUS authentication sources by adding more than one RADIUS section suffixed with “_” (underscore), e.g. “RADIUS_2”. See the configuration example to find out how to do it.
| IP | The IP address of the RADIUS server used for primary authentication. |
| PORT | The port of the RADIUS server for Access-Request. Usually, this port is 1812. |
| SECRET | RADIUS secret used in Rublon Authentication Proxy – RADIUS server communication. If left empty, the proxy’s RADIUS_SECRET is used. |
| TIMEOUT | Time (in seconds) after which a single connection attempt with the RADIUS server will be aborted. Note that you have to multiply this value by the retries count to get the actual time, after which Rublon will abort trying to connect to the RADIUS server. Default: 5 |
| RETRIES | The number of reconnection attempts when a response is not received. Default: 3 |
| PROXY_REQUESTS | Whether to proxy requests to the RADIUS server. Rublon 2FA will be performed after successful authentication. Works only in “standard” proxy mode and for “AUTH_SOURCE” set to “radius”. Append Mode does not work when proxying requests. Note that you will have to set the proxy’s RADIUS secret to the same value as the RADIUS server secret. See Non-PAP protocol for RADIUS communication communication for more information. Default: false |
| NAS_IP_ADDRESS | The IP address that will be sent in the “NAS-IP-Address” attribute to the RADIUS server. If left empty, no “NAS-IP-Address” is sent. However, proxied requests will copy “NAS-IP-Attribute” from origin requests. |
| EMAIL_ATTR_NAME | Attribute that should be received from RADIUS within the AccessAccept packet containing the user’s email. Modify only if, for some reason, you have changed the suggested RADIUS server configuration. Default: “Rublon-Email” |
Append Mode
Append Mode is a feature available in Rublon Authentication Proxy when the “standard” mode is set in the configuration file. Append Mode allows you to choose your authentication method by appending specific values to your password when logging in to an integrated service. The specific value is preceded by the append mode separator.
Append Mode works only in “standard” mode. Enable Append Mode by adding the following options to one of your server’s configurations under the “SERVERS” section:
"USE_APPEND_MODE": true
"APPEND_MODE_SEPARATOR": ","By default, the separator is set to “,” (comma).
How does it work?
After you enable Append Mode, when logging in to an integrated service, type in your password. Then, append the APPEND_MODE_SEPARATOR. Then, you can append one of the following values:
- “push”
- “email”
- “123456” – the TOTP code; must be exactly 6 characters long with no spaces in-between
If Append Mode is enabled but the user only provides their password without appending anything, the authentication method set in AUTH_METHOD is used.
Similarly, if the appended value is not recognized, the entire provided string is treated as a password and the authentication method set in AUTH_METHOD is used.
Note that AppendMode is case-sensitive. Values like “Push”, “EMAIL”, “pUsH” do not work.
Examples
Let’s assume that your password is: “pancakes123”, and the separator is not set in the configuration file, so its value is the default “,” (comma).
If you would like to choose push as the authentication method, type:
pancakes123,pushIf you would like to choose email as the authentication method, type:
pancakes123,emailIf you would like to choose totp as the authentication method, type:
pancakes123,123456Where 123456 is the TOTP code generated by Rublon Authenticator.
Non-PAP protocol for RADIUS communication
By default, Rublon Authentication Proxy uses only the PAP protocol to authenticate users. This means that all systems that try to use other protocols (like CHAPv1, EAP-MS-CHAPv2) to communicate with Rublon Authentication Proxy will not work. However, it is possible to configure Rublon Authentication Proxy to proxy all non-PAP requests to the RADIUS server.
To do so, add:
"PROXY_REQUESTS": true
To your configuration file, under the “RADIUS” section. Rublon 2FA will be performed upon receiving the Access-Accept response packet from the RADIUS server.
If the RADIUS server was configured to accept these protocols, protocols such as CHAPv1 or MS-CHAPv2 (even EAP-MS-CHAPv2) should work from now on.
Refer to the following flowchart, which portrays how proxying works.

Configuration example
{
"PROXY": {
"RADIUS_SECRET": "secret_to_communicate_with_the_proxy",
"RUBLON_API": "https://core.rublon.net",
"SERVERS": [
{
"IP": "172.16.1.100",
"PORT": 1812,
"MODE": "standard",
"AUTH_SOURCE": "LDAP,LDAP_2",
"RUBLON_TOKEN": "SYSTEM_TOKEN",
"RUBLON_SECRET": "SECRET_KEY",
"AUTH_METHOD": "email",
"USE_APPEND_MODE": true,
"APPEND_MODE_SEPARATOR": ","
},
{
"IP": "172.16.1.100",
"PORT": 18120,
"MODE": "standard",
"AUTH_SOURCE": "RADIUS_2",
"RUBLON_TOKEN": "SYSTEM_TOKEN_2",
"RUBLON_SECRET": "SECRET_KEY_2",
"AUTH_METHOD": "push,email"
}
]
},
"LDAP": {
"HOST": "172.16.3.100",
"SEARCH_DN": "dc=test,dc=local",
"ACCESS_USER_DN": "cn=Administrator,cn=Users,dc=test,dc=local",
"ACCESS_USER_PASSWORD": "v3ryH@rdpa$$w0rd"
},
"LDAP_2": {
"HOST": "172.16.3.101",
"SEARCH_DN": "dc=test2,dc=local",
"ACCESS_USER_DN": "cn=Administrator,cn=Users,dc=test2,dc=local",
"ACCESS_USER_PASSWORD": "v3ryH@rdpa$$w0rd"
},
"RADIUS": {
"SERVER_IP": "172.16.2.100",
"PORT": 1812,
"SECRET": "secret_to_communicate_with_radius_server"
},
"RADIUS_2": {
"SERVER_IP": "172.16.2.101",
"PORT": 1812,
"SECRET": "secret_to_communicate_with_radius_server_2"
}
}
Start Rublon Authentication Proxy
Linux
To run Rublon Authentication Proxy, start the service using one of the following commands:
systemctl start rublon.service
or
service rublon start
Windows
Run Rublon Authentication Proxy as a console application to ensure everything is set up properly:
- Open cmd as administrator and go to the proxy’s installation directory:
cd C:\Program Files\Rublon Auth Proxy
- Run the proxy:
.\bin\rublonauthproxy.exe
If Rublon Authentication Proxy is configured properly, the console displays the Started listening log. At this point, you can test user authentication. To test user authentication, use NTRadPing or start configuring Rublon with one of the services that support the Rublon Authentication Proxy.
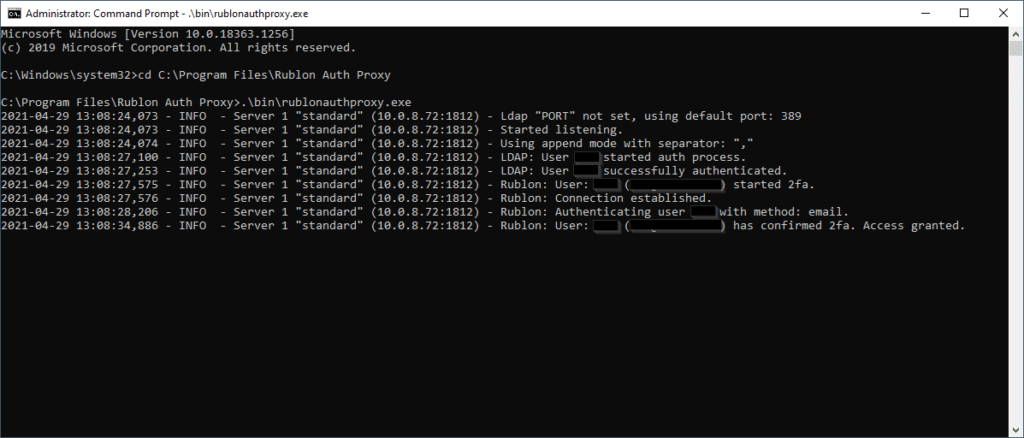
If everything works, start the proxy as a service:
net start RublonAuthProxy
Alternatively, you can start the proxy as a service in the following way:
- Find Rublon Authentication Proxy Service on the Windows services list (services.msc).
- Right-click Rublon Authentication Proxy Service and select Start.
Update Rublon Authentication Proxy
Linux
- Stop Rublon service:
systemctl stop rublon.service
or
service rublon stop - Download the latest rublonauthproxy package and unpack it.
- Replace the lib directory inside the previously deployed rublonauthproxy folder.
- Make sure the rublonauthproxy/lib/rublonauthproxy file has proper permissions:
chmod 775 rublonauthproxy/lib/rublonauthproxy - Run the service:
systemctl start rublon.service
or
service rublon start
Windows
Run the installer over your current installation to update Rublon Authentication Proxy. Config and log files will be preserved.
Uninstall Rublon Authentication Proxy
Linux
- Stop Rublon service:
systemctl stop rublon.service
or
service rublon stop - Remove rublon.service:
rm -f /lib/systemd/system/rublon.service - Remove the rublonauthproxy directory:
rm -rf rublonauthproxy
Windows
Run the unins000.exe file located in the installation directory. Note that configuration and log files will be preserved.
Troubleshooting
If you are facing an issue with the Rublon Authentication Proxy, try restarting the Rublon Authentication Proxy.
If restarting the Rublon Authentication Proxy didn’t fix your issue, go to your configuration file and set the DEBUG option to true. Then, check the contents of your rublonauthproxy.log file. Information contained in this file should in most cases be enough to troubleshoot issues related to Rublon Authentication Proxy.
If you installed the Rublon Authentication Proxy on Windows, then rublonauthproxy.log is located in the following location:
C:\Program Files\Rublon Auth Proxy\logs\rublonauthproxy.log
If you installed the Rublon Authentication Proxy on Linux, then rublonauthproxy.log is located in the following location:
rublonauthproxy/logs/rublonauthproxy.log
Note that most issues occur due to incorrect configuration.
If you encounter any issues with your Rublon integration, please contact Rublon Support.
Related Posts
Rublon Authentication Proxy – Release Notes
Rublon Authentication Proxy – Integrations
Rublon Authentication Proxy – Download
Rublon Authentication Proxy – Archive (Older Versions)