Last updated on December 8, 2025
Overview
Before You Start
- Check the list of described Rublon Access Gateway integrations. Chances are, your application is already there. In that case, follow the instructions for that particular integration instead of this generic documentation for more detailed steps and screenshots.
- Install and configure the Rublon Access Gateway.
- Install and configure the Rublon SSO Portal. This step is optional but highly recommended because the Rublon SSO Portal is required for Single Sign-On (SSO) user logins.
Configuration
SAML Service Provider
NOTE
- SSO URL – often called Single Sign-On URL or Single Sign-On endpoint on the service provider side
- Logout URL – note that some service providers do not support Single Log-Out (SLO). If this is the case with your service provider, you will not need the Logout URL value.
- Entity ID – sometimes called IdP Issuer
- Certificate – click the DOWNLOAD CERTIFICATE button to download the certificate to your computer and then upload the certificate to the service provider or copy the entire contents of the certificate and paste it into a text field on the service provider side
- Certificate Fingerprint – some service providers only require a certificate fingerprint
- Metadata File – some service providers require a metadata file; click the DOWNLOAD XML METADATA button and then upload the metadata file on the service provider side
- Assertion Consumer Service (ACS) URL
- Service Provider (SP) Entity ID
- Single Logout Service – note that some service providers do not support Single Log-Out (SLO). If this is the case with your service provider, you will not find this value
Rublon Access Gateway
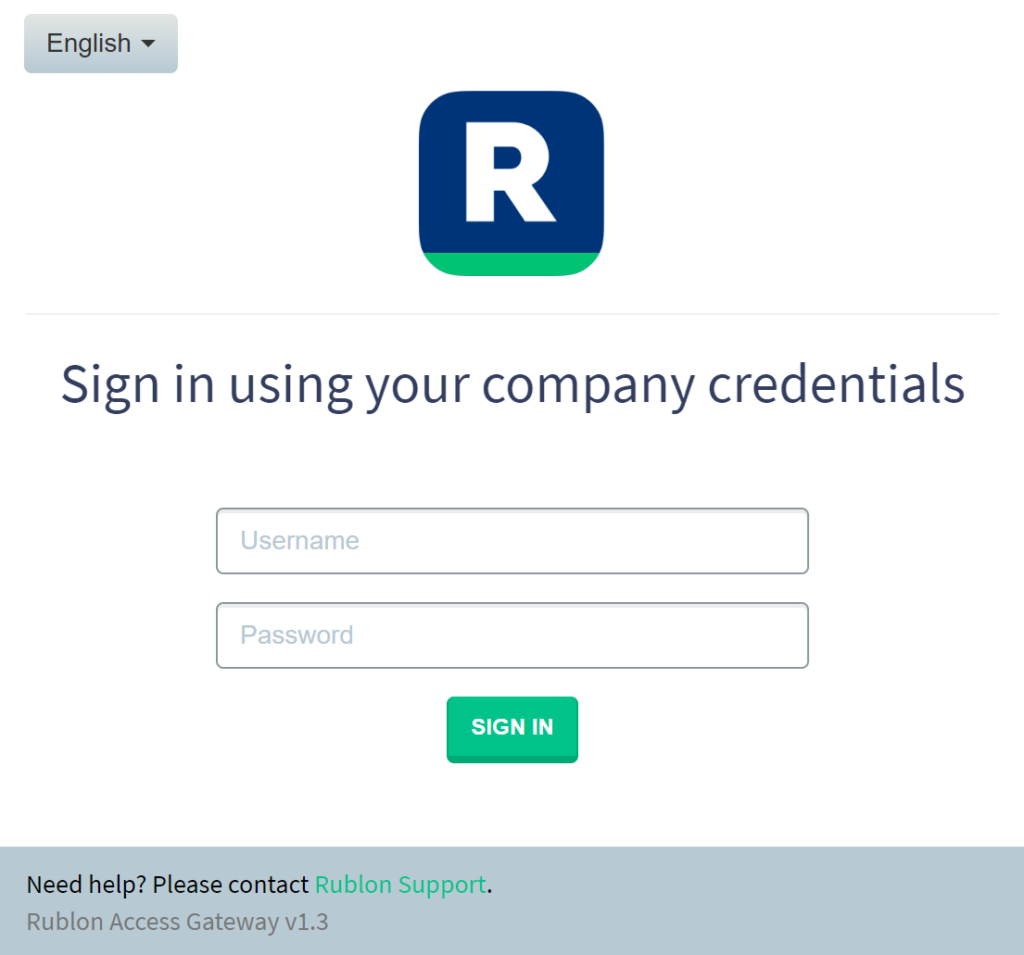
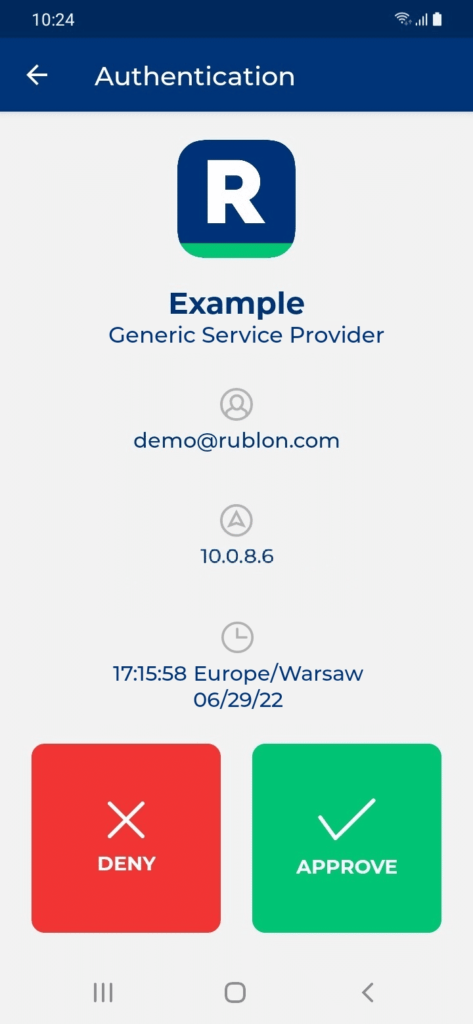
Log in to your Generic SAML Service Provider with Rublon 2FA
If you have configured the Rublon SSO Portal, access your application via the Portal. If not, initiate the sign-in process like you always did before enabling Rublon. The example below portrays logging into a generic SAML Service Provider outside the SSO Portal.
1. Initiate login to your application.
2. You will be redirected to the Rublon Access Gateway login page.