Last updated on December 8, 2025
Overview
Supported Authentication Methods
Before you start
You need to install and configure Rublon Access Gateway itself before configuring SonicWall SMA 8200v to work with it. Please read the Rublon Access Gateway documentation and follow the steps in Installation and Configuration sections. Afterwards, follow the Configuration section in this document.
Configuration
Follow these steps to enable Rublon 2FA for SonicWall SMA.
Rublon Access Gateway
1. Log in to Rublon Access Gateway.
2. Go to Applications → Add Application.
3. Fill in the form. Refer to the following image and table.
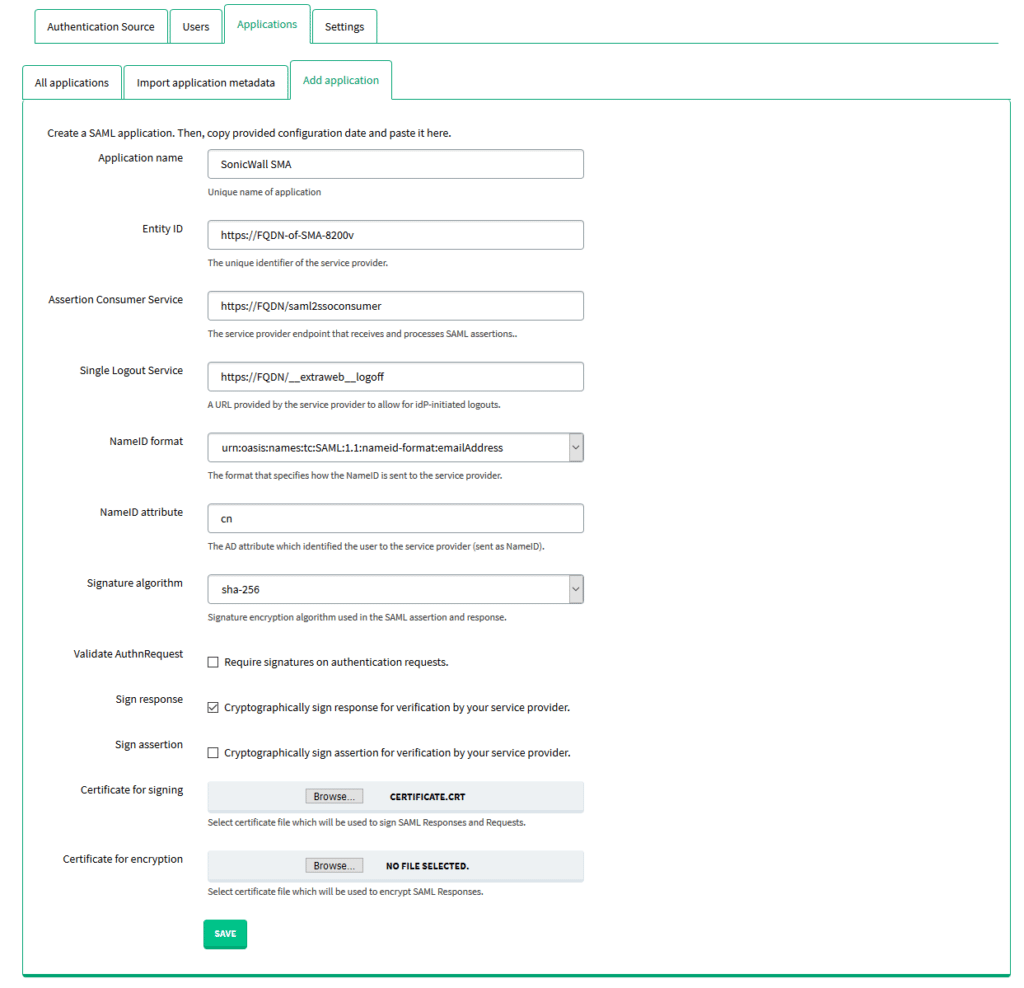
| Application name | SonicWall SMA |
| Entity ID | https://FQDN-of-SMA-8200v |
| Assertion Consumer Service | https://FQDN/saml2ssoconsumer |
| Single Logout Service | https://FQDN/__extraweb__logoff |
| NameID attribute | cn |
| Validate AuthnRequest | Uncheck |
| Sign response | Check |
| Certificate for signing | Import a certificate for the domain on which the Sonicwall SMA 8200v External Interface runs. |
4. Click the SAVE button to add this new application to Rublon Access Gateway.
5. Click DOWNLOAD CERTIFICATE in the Information for configuring applications with Rublon Access Gateway section of the Applications → All applications tab. You are going to need this certificate later.
SonicWall SMA 8200v
1. Log in to the SMA 8200v interface.
2. Go to System Configuration → SSL Settings.
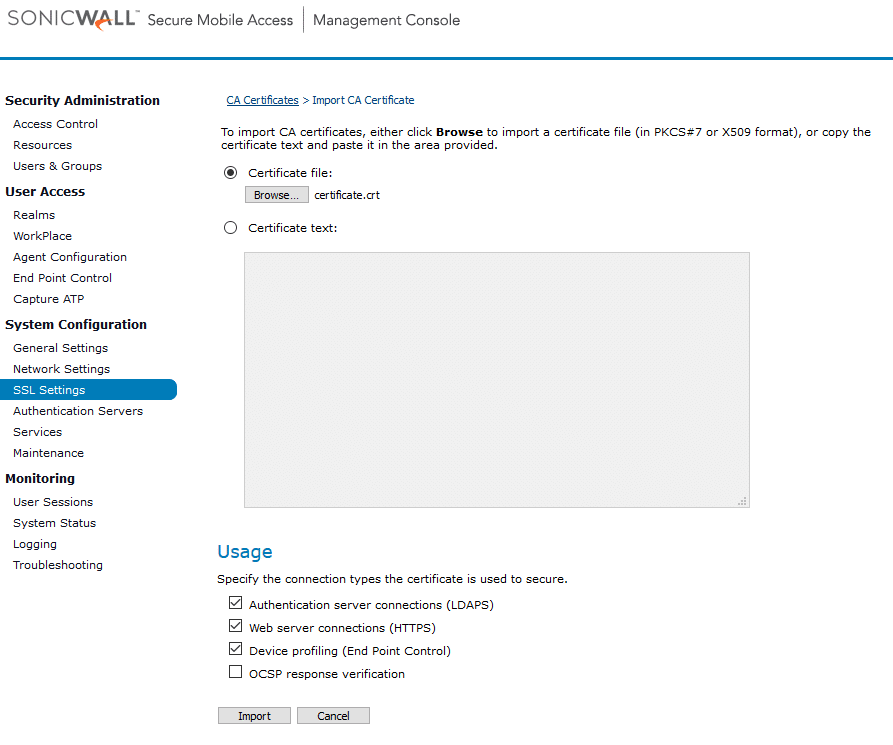
3. Click Edit under the CA certificates section.
4. Click New.
5. Check Certificate file. Select the certificate you have downloaded from Rublon Access Gateway. Click Import.
6. Go to System Configuration → Authentication Servers.
7. Click New… in the top right-hand corner.
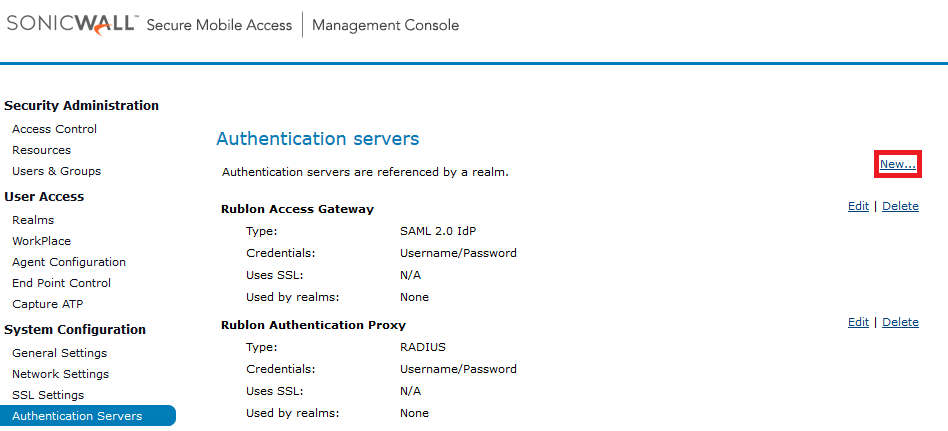
8. Select SAML 2.0 Identity Provider in Authentication directory.
9. Select Username/Password in Credential Type.
10. Click Continue….


| Name | Specify the name, for example Rublon Access Gateway. |
| Appliance ID | Enter the IP or FQDN of the external interface in the following format: PROTOCOL://FQDN/IP For example:https://rag.example.com |
| Server ID | Enter the value from Entity ID from Rublon Access Gateway (Applications → Information for configuring applications with Rublon Access Gateway). |
| Authentication service URL | Enter the value from SSO URL from Rublon Access Gateway (Applications → Information for configuring applications with Rublon Access Gateway). |
| Logout service URL | Enter the value from Logout URL from Rublon Access Gateway (Applications → Information for configuring applications with Rublon Access Gateway). |
| Trust the following certificate | Select the certificate you have downloaded from Rublon Access Gateway. This has to be the same certificate you have imported in System Configuration → SSL Settings. |
| Sign AuthnRequest message using this certificate | Check. Select the certificate used for External interface. |
13. Click Save to add your new Authentication Server.
14. Go to User Access → Realms.
15. Click +New realm in the upper right corner.

16. Set a name for your realm, for example Rublon_Access_Gateway_Realm.
17. Set Status to Enabled.
18. Choose the Rublon Access Gateway authentication server you have created before.
19. Click Finish to create a new realm.

20. Go to Security Administration → Users & Groups.
21. Select the Mapped Accounts tab.
22. Click New and create a new account whose name corresponds to the cn of a user in the authentication source set in Rublon Access Gateway (in the case of Active Directory).
23. Clicking Pending changes in the top right corner, and then click Apply Changes.

24. Your configuration is now finished. Users have Rublon 2FA enabled when logging in to your VPN.
Log in to SonicWall SMA with Rublon 2FA
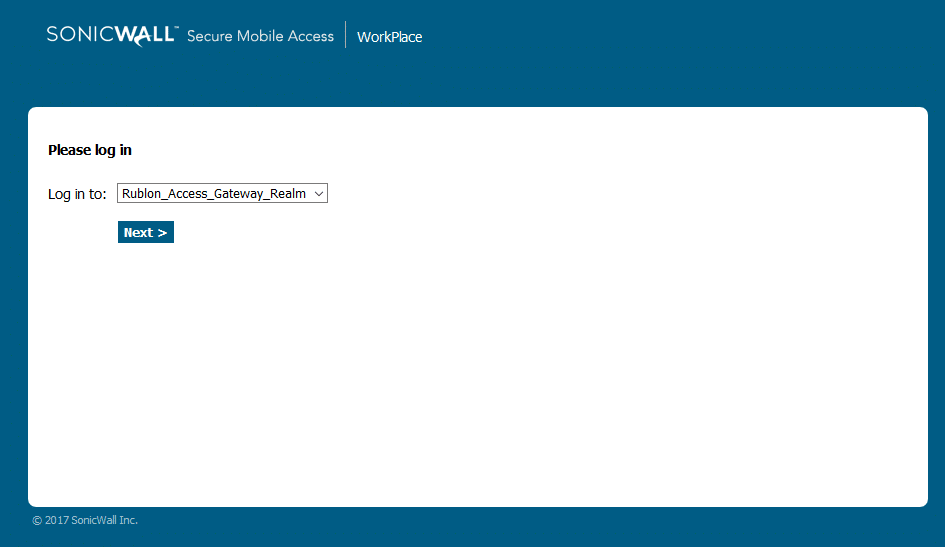
1. Open SonicWall SMA.
2. Select the realm to log in to. Click Next.



6. You will be successfully logged in to your VPN.
Troubleshooting
If you encounter any issues with your Rublon integration, please contact Rublon Support.