Last updated on March 19, 2025
Overview of MFA for SonicWall WAN GroupVPN
Supported Authentication Methods
Demo Video of MFA for SonicWall WAN GroupVPN
Before you start
Configuration of MFA for SonicWall WAN GroupVPN
5. Click the Advanced tab, and check the group selected in the User group for XAUTH users dropdown. You have to use this group in your RADIUS configuration.
6. Make sure Require authentication of VPN clients by XAUTH is checked.
7. Click OK to save the changes you made. Clicking OK closes the VPN Policy window.
8. Navigate to the menu on the left. Expand Users and select Settings.
9. Select Authentication from the menu at the top.
10. Set User Authentication Method to RADIUS.
11. Click CONFIGURE RADIUS on the right. Clicking the button opens the RADIUS Configuration window.
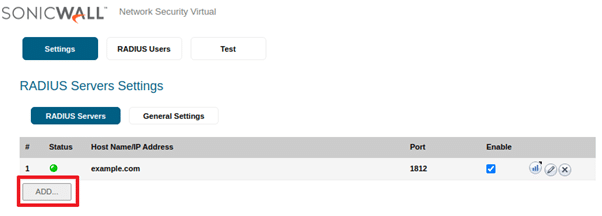
12. Click ADD… to add a new server. This opens the Add server window.
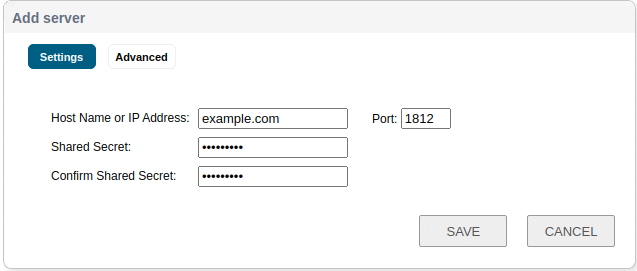
13. Enter the FQDN or IP address of the RADIUS server used for primary authentication.
14. Enter the RADIUS Secret set in Rublon Authentication Proxy as the Shared Secret in this window.
15. Click SAVE to add the new server.
16. While still in RADIUS Servers Settings, switch to General Settings.
17. Set RADIUS Server Timeout to 60 seconds.
18. Set Retries to 2.
19. Click APPLY to save these changes.
20. Select the RADIUS Users tab.
21. Set Default user group to which all RADIUS users belong. It has to be the same group as in the VPN server configuration (step 5).
22. Click OK to save this change. Clicking OK closes the RADIUS Configuration window.
23. Navigate to the left menu. Extend SSL VPN and select Server Settings.
24. Make sure Use RADIUS in is unchecked in the RADIUS User Settings section. In case it’s checked, uncheck it, and click the ACCEPT button at the bottom of the site.
Testing MFA for SonicWall WAN GroupVPN
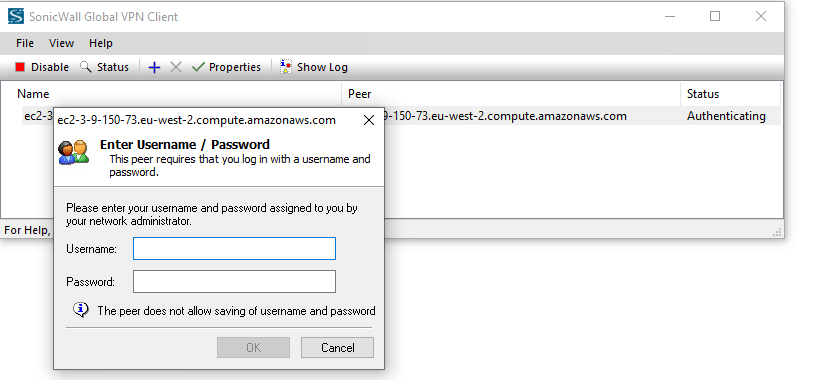
3. Check your mailbox for an email from Rublon. Open the email, and click Sign In.