Last updated on July 8, 2025
Overview of Sophos XG Firewall VPN MFA
- MFA for Sophos SSL VPN
- MFA for Sophos IPsec VPN
- MFA for Sophos PPTP VPN
- MFA for Sophos Firewall User Portal
- MFA for Sophos Firewall web admin console
Supported Authentication Methods
Before You Start
Before configuring Rublon MFA for Sophos Firewall VPN:
- Ensure you have prepared all required components.
- Create an application in the Rublon Admin Console.
- Install the Rublon Authenticator mobile app.
Required Components
1. User Identity Provider (IdP) – You need an external Identity Provider, such as Microsoft Active Directory, OpenLDAP, or FreeRADIUS.
2. Rublon Authentication Proxy – Install the Rublon Authentication Proxy if you have not already.
3. Sophos Firewall – Ensure you have correctly configured your Sophos Firewall, especially that user logins work properly before deploying MFA for Sophos XG or Sophos XGS.
Create an Application in the Rublon Admin Console
1. Sign up for the Rublon Admin Console. Here’s how.
2. In the Rublon Admin Console, go to the Applications tab and click Add Application.
3. Enter a name for your application (e.g., Sophos XG Firewall VPN) and then set the type to Rublon Authentication Proxy.
4. Click Save to add the new application in the Rublon Admin Console.
5. Copy and save the values of the System Token and Secret Key. You are going to need these values later.
Install Rublon Authenticator
For increased security of Multi-Factor Authentication (MFA), end-users may install the Rublon Authenticator mobile app. So, as a person configuring MFA for Sophos Firewall, we highly recommend you install the Rublon Authenticator mobile app, too. Thanks to that, you will be able to test MFA for Sophos via Mobile Push.
Download the Rublon Authenticator for:
Configuring MFA for Sophos XG Firewall VPN
This section describes how to configure MFA for Sophos SSL VPN, Sophos PPTP VPN, Sophos IPsec VPN, Sophos Firewall User Portal, and Sophos Firewall web admin console on Sophos XG and Sophos XGS Firewall Appliances.
- Add Rublon Authentication Proxy as RADIUS server
- Use Rublon Authentication Proxy as authentication method in selected Sophos services
MFA for Sophos XG Firewall VPN Configuration Part 1: Adding Rublon Authentication Proxy as RADIUS server

2. Fill in the form. Refer to the following image and table.

| Server type | Select RADIUS server. |
| Server name | Enter a name for your server, e.g., Rublon Authentication Proxy. |
| Server IP | Enter the IP address of your Rublon Authentication Proxy. |
| Authentication Port | Enter the port number of your Rublon Authentication Proxy (1812 by default). |
| Time-out | Change to at least 60. |
| Enable accounting | Check. Rublon Authentication Proxy does not support accounting. However, Sophos Firewall requires this option to work correctly. |
| Accounting Port | Enter the RADIUS accounting port number (1813 by default). |
| Shared secret | Enter the RADIUS_SECRET you set in the Rublon Auth Proxy’s config file. |
| Domain Name | Enter your domain name (Optional). |
| Group name attribute | Enter the alias for the configured group name, which is displayed to the user, e.g., Rublon. |
3. Click Save to save the changes you made.
MFA for Sophos XG Firewall VPN Configuration Part 2: Using Rublon Authentication Proxy in selected Sophos services
Firewall authentication methods

Source of user authentication for logging into the firewall. We recommend you set it to a local user base only during the testing phase so that you have a fallback method of access to Sophos Firewall should Rublon login be impossible, e.g., due to a configuration mistake.
User portal authentication methods

Source of user authentication for users logging in to the User Portal. Users can log in to the User Portal to download the VPN client and a VPN profile configuration. We recommend you select Rublon Authentication Proxy so that users must complete MFA before accessing the portal.
VPN (IPsec/dial-in/L2TP/PPTP) authentication methods

Source of user authentication for most VPN types. Select Rublon Authentication Proxy so that users must complete MFA when connecting via IPsec, dial-in, L2TP, or PPTP VPN.
Administrator authentication methods

Source of user authentication for Sophos Firewall web admin console. This setting only applies to administrators. We recommend you select Local only for the testing phase unless you have access to the Super Administrator account.
SSL VPN authentication methods

Source of user authentication for SSL VPN service. We recommend you select Rublon Authentication Proxy so that users must complete MFA when connecting via SSL VPN.
Testing MFA for Sophos Firewall
After configuring MFA for Sophos XG Firewall, test your setup by connecting to a selected VPN, User Portal, or web admin console. In all the following examples, Mobile Push has been set as the second factor in the Rublon Authentication Proxy configuration (AUTH_METHOD was set to push).
Testing MFA for Sophos User Portal
To test MFA for Sophos Firewall User Portal:
1. Open the Sophos User Portal by opening https://<Sophos Device IP Address> in your web browser.
2. Enter your Username and Password and enter the CAPTCHA code.

3. Rublon will send a Mobile Push authentication request to your phone. Tap APPROVE.

4. You will gain access to the User Portal.
Testing MFA for Sophos Firewall SSL VPN
To test MFA for Sophos Firewall SSL VPN, use the dedicated Sophos Connect client. You can download Sophos Connect from the Sophos User Portal (under the VPN tab).
1. To import the VPN profile into your Sophos Connect client, click Import connection, and select your .ovpn VPN profile file.
2. After importing your VPN profile, select it and click Connect.
3. Enter your username and password and click Sign in.

4. Rublon will send a Mobile Push authentication request to your phone. Tap APPROVE.

5. You will connect to the VPN.
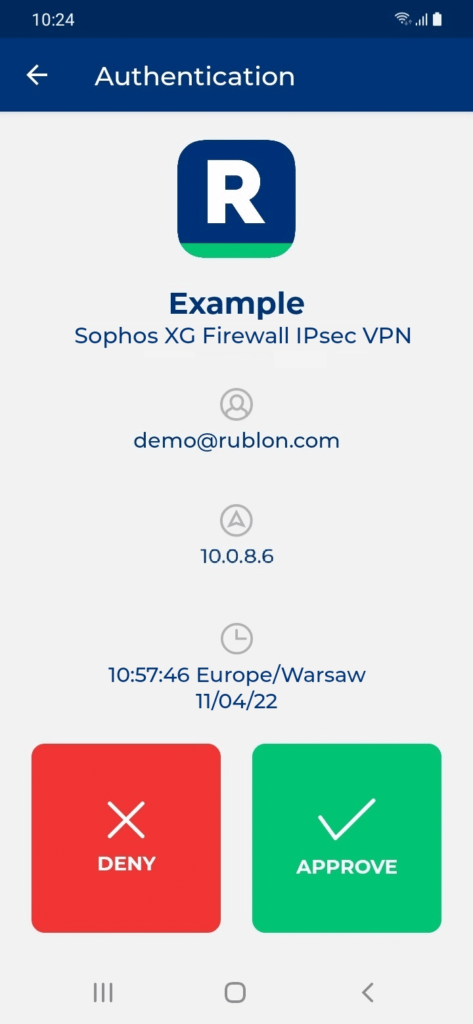
Testing MFA for Sophos Firewall IPsec VPN
To test MFA for Sophos Firewall IPsec VPN, use the dedicated Sophos Connect client. You can download Sophos Connect from the Sophos User Portal (under the VPN tab).
1. To import the VPN profile into your Sophos Connect client, click Import connection, and select your .scx VPN profile file.
2. After importing your VPN profile, select it and click Connect.
3. Enter your username and password and click Sign in.

4. Rublon will send a Mobile Push authentication request to your phone. Tap APPROVE.
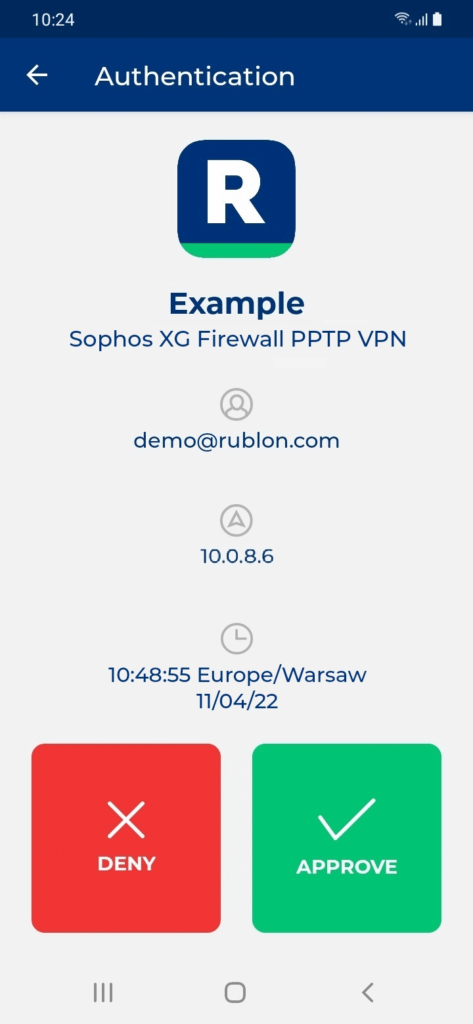
Testing MFA for Sophos Firewall PPTP VPN
How to Add and Configure a Sophos Firewall PPTP VPN connection in Windows VPN

2. Click Save to save your new VPN connection profile.
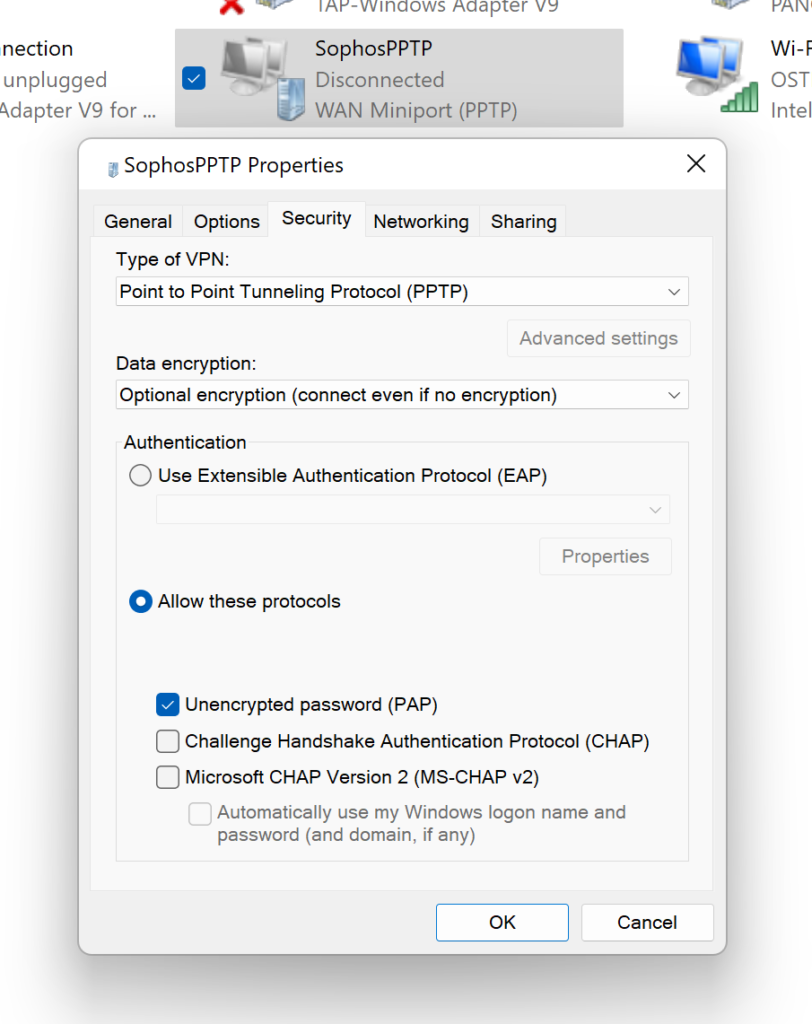
3. Edit the VPN connection and specify the authentication protocol.
Go to Control Panel → Network and Sharing Center and select Change adapter settings from the menu on the left.
4. Right-click the newly created VPN profile and select Properties.
5. A new window with properties for this connection will open.
6. Go to the Security tab and change Authentication to Allow these protocols. Then, check Unencrypted password (PAP).
Connecting to Sophos Firewall PPTP VPN


Testing MFA for Sophos web admin console

