Last updated on December 8, 2025
Overview
Supported Authentication Methods
Before you start
Configuration
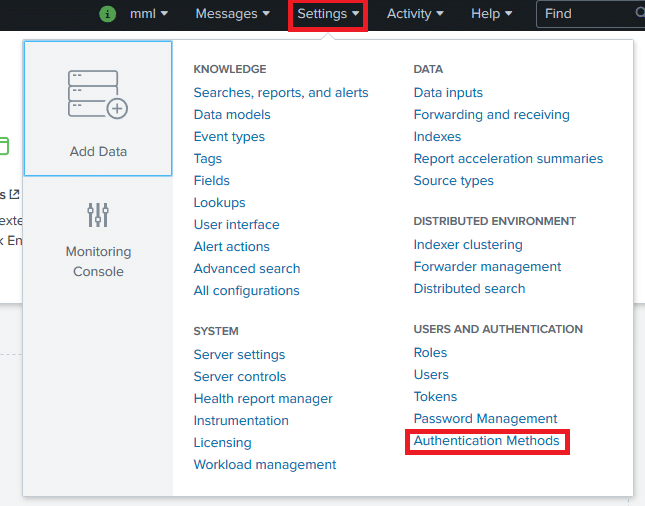
3. Select SAML as the External authentication source.
4. Click SAML Settings.
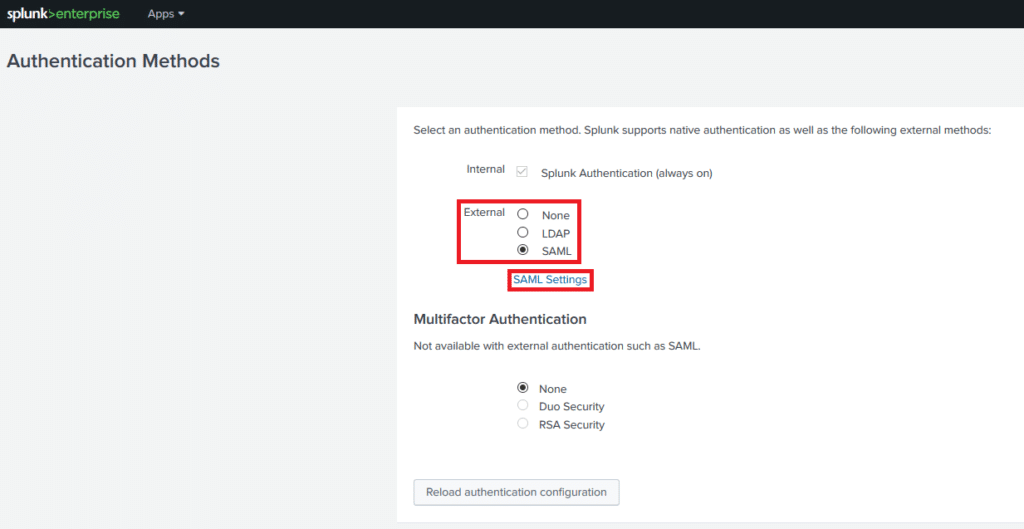
5. Click SAML Configuration in the top right corner.
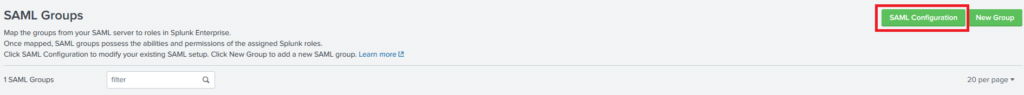
6. Download SP Metadata File. You are going to need it later.
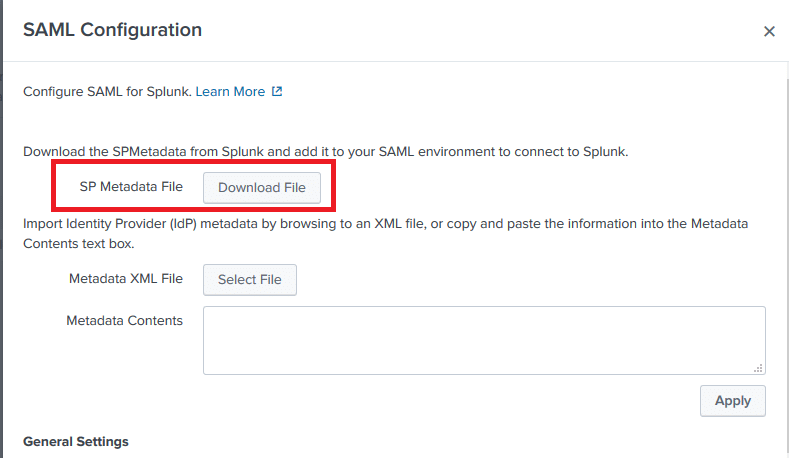
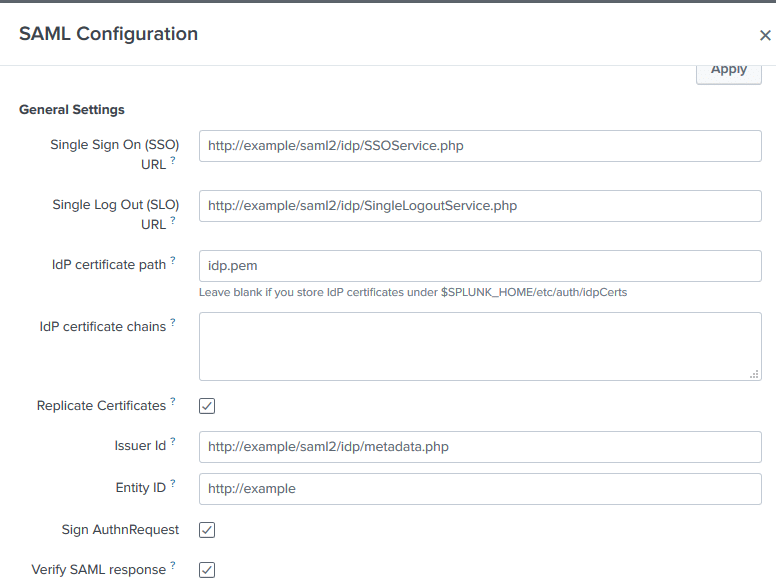
7. Fill in the General Settings section of the form. Do not close or save the form yet. Refer to the following image and table.
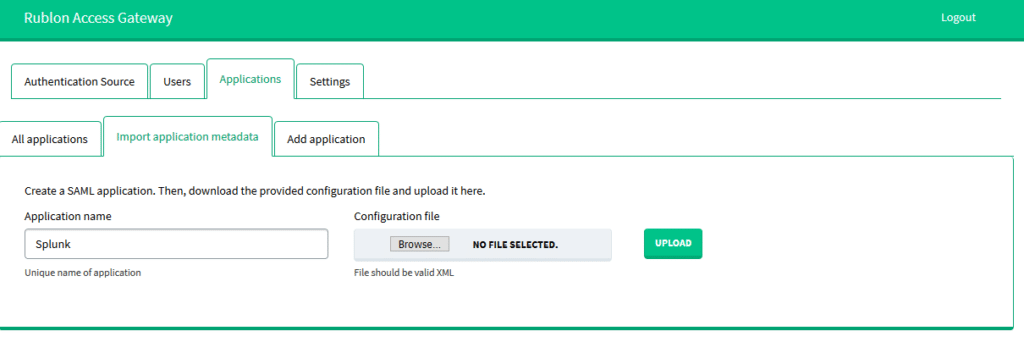
11. Go back to the Splunk SAML Configuration.
Note
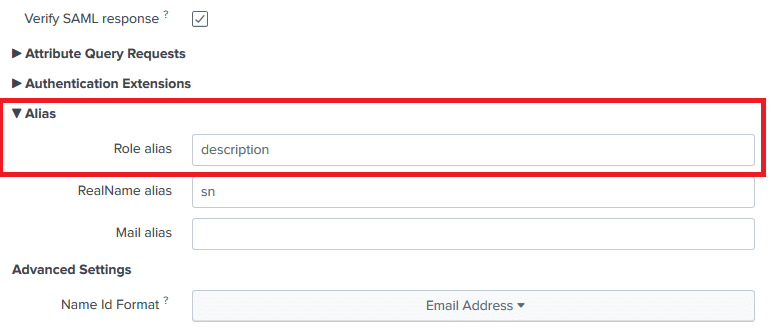
12. Expand the Alias section. Enter the Role alias according to your configuration. It’s description in our example.

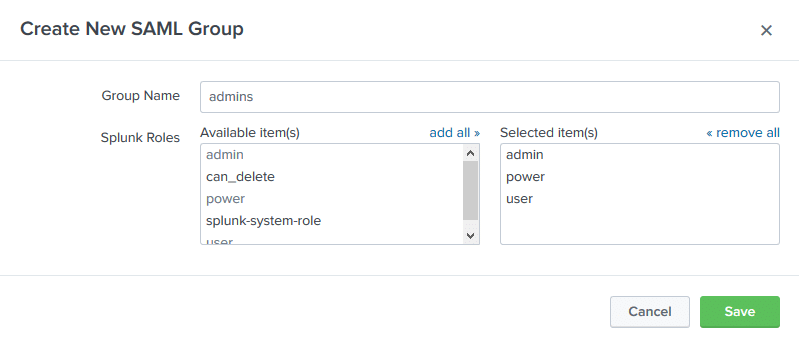
17. Your configuration is now complete. Your users can log in to Splunk with Rublon 2FA enabled.
Log in to Splunk with Rublon 2FA enabled
1. Open your browser and enter the address of your Splunk instance.
2. You should be redirected to the Rublon Access Gateway login page.
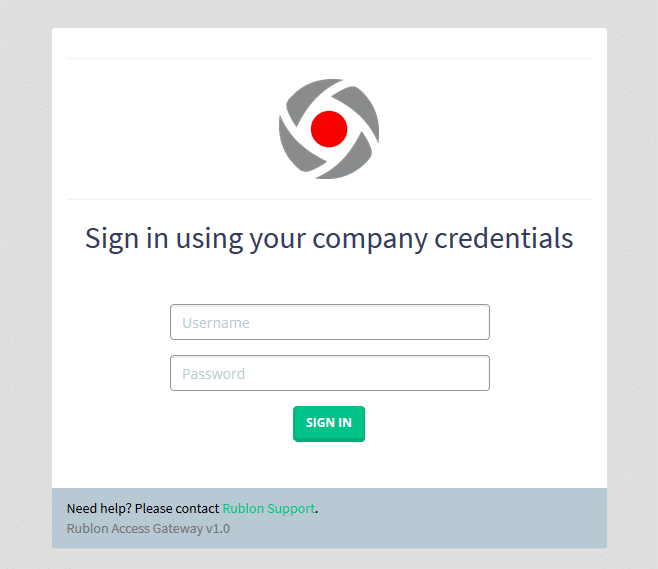
3. Provide your username and password. A window will appear with a selection of various 2FA methods from Rublon.

4. In this example, let’s use the Email Link 2FA method (first icon on the left). Select it, and you should receive an email from Rublon. Confirm your login by clicking the link provided in the email.
5. One of the options in the Rublon 2FA window is to Remember this device. Check it, and you will not be required to go through Rublon Authentication during your next login to Dropbox.
6. After selecting the desired 2FA method, you will be presented with a window like the one below.
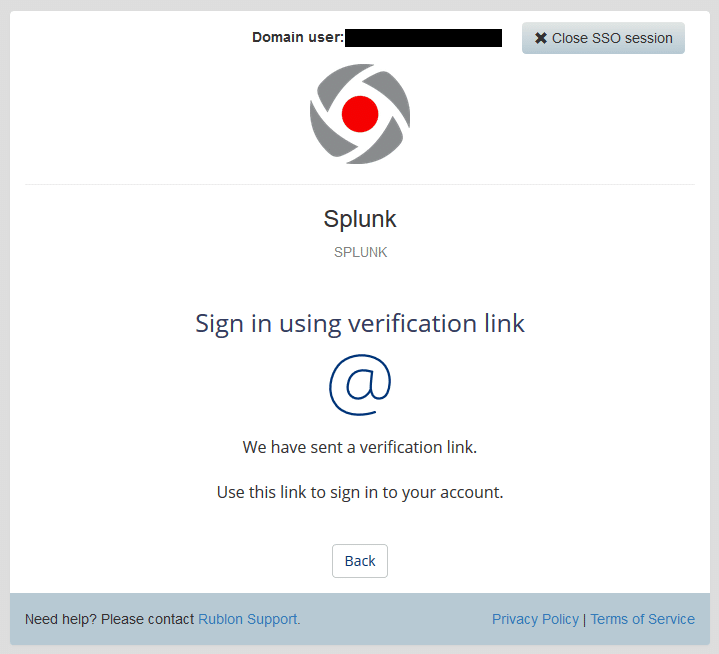
7. Once you have confirmed your login using the chosen 2FA method, you will be redirected to Splunk.
Troubleshooting
If you encounter any issues with your Rublon integration, please contact Rublon Support.