Last updated on July 8, 2025
MFA for WatchGuard Firebox Mobile VPN is an extra layer of security that requires users to provide additional proof of identity to connect to a VPN. Next to the classic login/password primary authentication, WatchGuard Mobile VPN adds secondary authentication the user must complete. The secondary authentication requires the user to approve a Mobile Push authentication request sent to their mobile device. Only after completing both primary and secondary authentication does the user access their VPN. So, even if cybercriminals know your VPN password, MFA for WatchGuard Mobile stops them from connecting to the VPN.
Overview
Rublon Multi-Factor Authentication for WatchGuard Firebox Mobile VPN allows you to add an extra layer of security to your WatchGuard VPN logins. MFA for WatchGuard Mobile VPN is done using the Rublon Authentication Proxy.
Rublon MFA for WatchGuard Firebox Mobile VPN enables Multi-Factor Authentication (MFA) / Two-Factor Authentication (2FA) during WatchGuard connections via IPSec and SSL. If a user successfully enters the correct username and password, they will be required to complete an additional authentication method. If the user is unable to complete secondary authentication, Rublon will deny access, preventing a potential hacker from gaining entry.
Supported Authentication Methods
| Authentication Method | Supported | Comments |
| Mobile Push | ✔ | N/A |
| FIDO | – | N/A |
| Passcode | ✔ | N/A |
| SMS Passcode | – | N/A |
| SMS Link | ✔ | N/A |
| Phone Call | ✔ | N/A |
| QR Code | – | N/A |
| Email Link | ✔ | N/A |
| YubiKey OTP | ✔ | N/A |
| RFID | – | N/A |
Before You Start Configuring MFA for Watchguard Mobile VPN
Before configuring Rublon MFA for WatchGuard Mobile VPN:
- Ensure you have prepared all required components.
- Create an application in the Rublon Admin Console.
- Install the Rublon Authenticator mobile app.
Required Components
1. User Identity Provider (IdP) – You need an external Identity Provider, such as Microsoft Active Directory, OpenLDAP, or FreeRADIUS.
2. Rublon Authentication Proxy – Install the Rublon Authentication Proxy if you have not already.
3. WatchGuard Mobile VPN – Ensure you have correctly configured your WatchGuard Firebox Cloud (PAYG) with Mobile VPN, especially that user logins work properly before deploying MFA for WatchGuard.
Create an Application in the Rublon Admin Console
1. Sign up for the Rublon Admin Console. Here’s how.
2. In the Rublon Admin Console, go to the Applications tab and click Add Application.
3. Enter a name for your application (e.g., WatchGuard Mobile VPN) and then set the type to Rublon Authentication Proxy.
4. Click Save to add the new application in the Rublon Admin Console.
5. Copy and save the values of the System Token and Secret Key. You are going to need these values later.
Install Rublon Authenticator
All end-users must install the Rublon Authenticator mobile app. So, as a person configuring MFA for WatchGuard Mobile VPN, we highly recommend you install the Rublon Authenticator mobile app, too. Thanks to that, you will be able to test MFA for WatchGuard via Mobile Push.
Download the Rublon Authenticator for:
Configuring Multi-Factor Authentication (MFA) for WatchGuard Mobile VPN
Follow the following instructions to set up MFA for WatchGuard Mobile VPN.
Configuring Rublon Authentication Proxy as RADIUS Server
1. Log in to the WatchGuard Firebox Admin Panel (Fireware Web UI).
2. In the left pane, click Authentication and then select Servers.
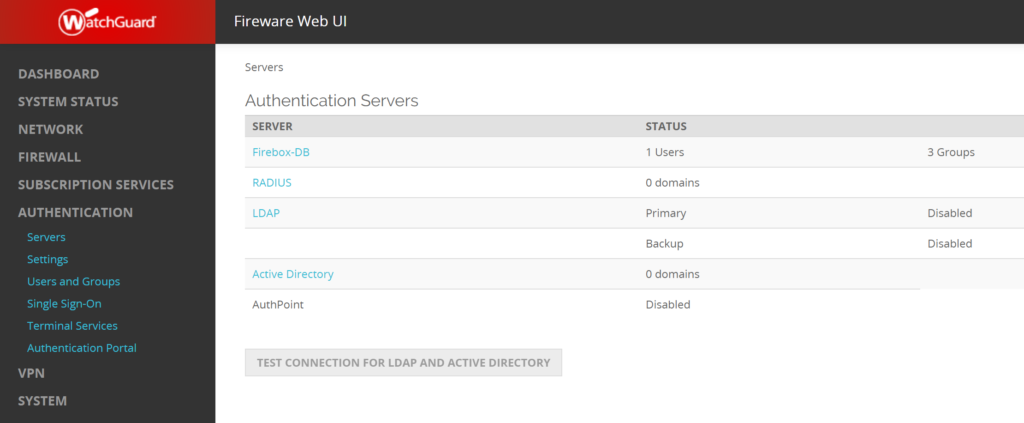
3. Click RADIUS.
4. Click the lock to make changes and then click ADD.
5. Fill in the form. Refer to the following image and table.
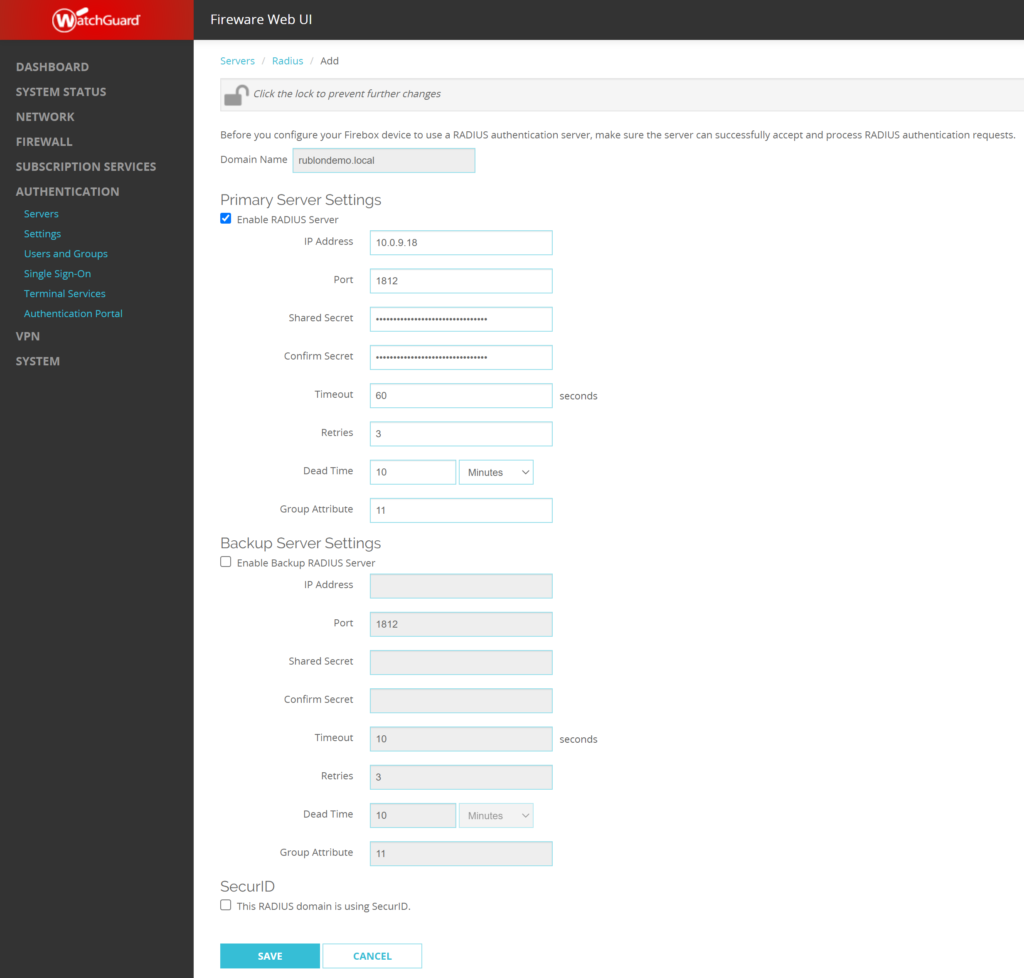
| Domain Name | Enter the name of your RADIUS domain. |
| Enable RADIUS Server | Check. |
| IP Address | Enter the IP of your Rublon Authentication Proxy server. |
| Port | Enter the port of your Rublon Authentication Proxy server. Default: 1812 |
| Shared Secret | Enter the RADIUS_SECRET you set in the Rublon Authentication Proxy’s config file. |
| Confirm Secret | Reenter the RADIUS_SECRET. |
| Timeout | 60 If experiencing issues, increase to 90. |
| Retries | 3 |
| Dead Time | 10 (Minutes) |
| Group Attribute | 11 |
6. If you have a second backup Rublon Authentication Proxy server, you can add it under Backup Server Settings.
7. Click SAVE to save your changes.
8. The RADIUS server you added should now be visible in the list of servers.
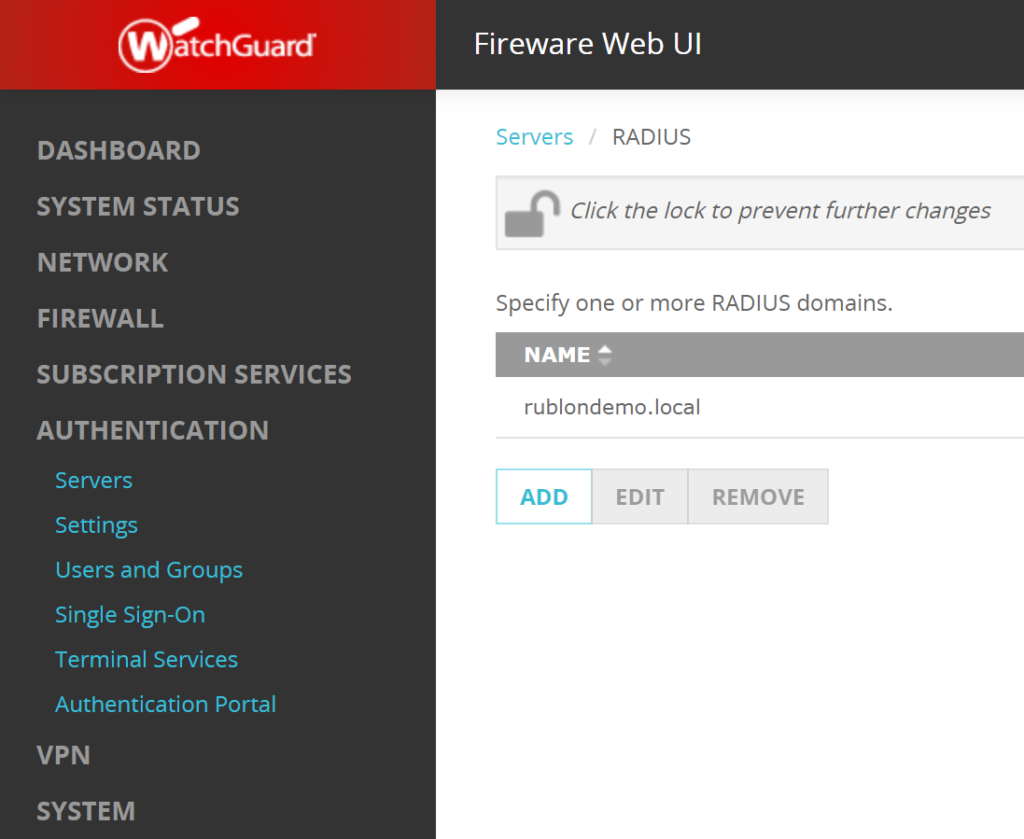
Configuring Mobile VPN
1. In the WatchGuard Firebox Admin Panel, click VPN and then select Mobile VPN.
2. Make sure the padlock is open. If it is closed, click it to open it. Otherwise, you will not be able to make any changes.
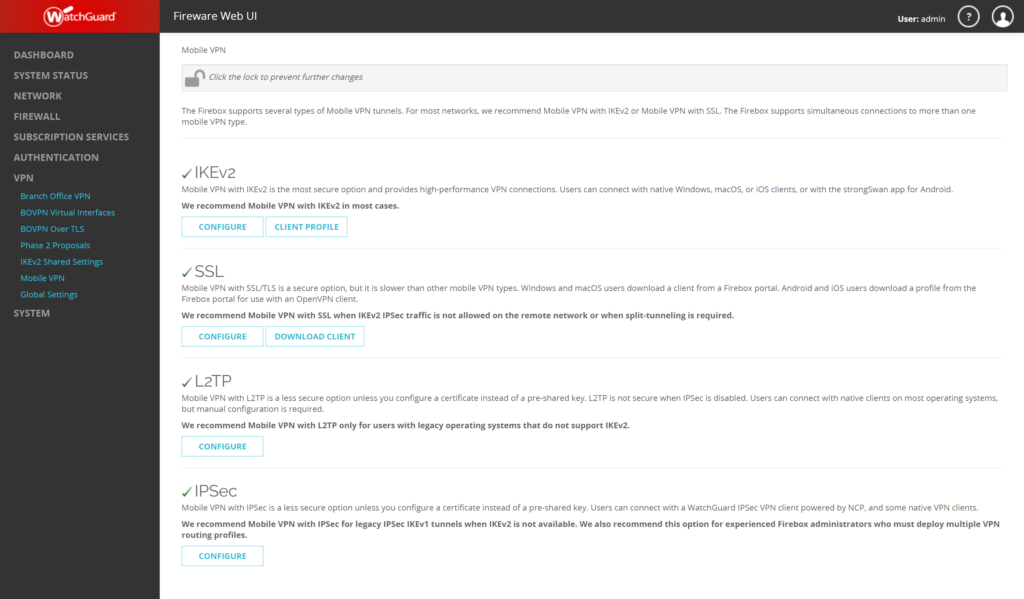
Mobile VPN Configuration with IPSec
1. In Mobile VPN, navigate to the IPSec section and click CONFIGURE.
2. In the Groups section, select your profile and click EDIT.
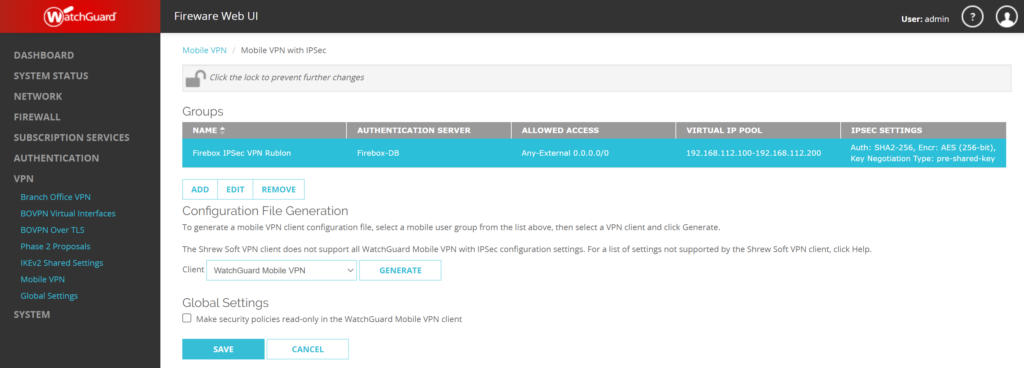
3. Select the General tab.
4. In the Authentication Server dropdown, select your Rublon Authentication Proxy server. It has the Domain Name you set when configuring Rublon Authentication Proxy as RADIUS Server.
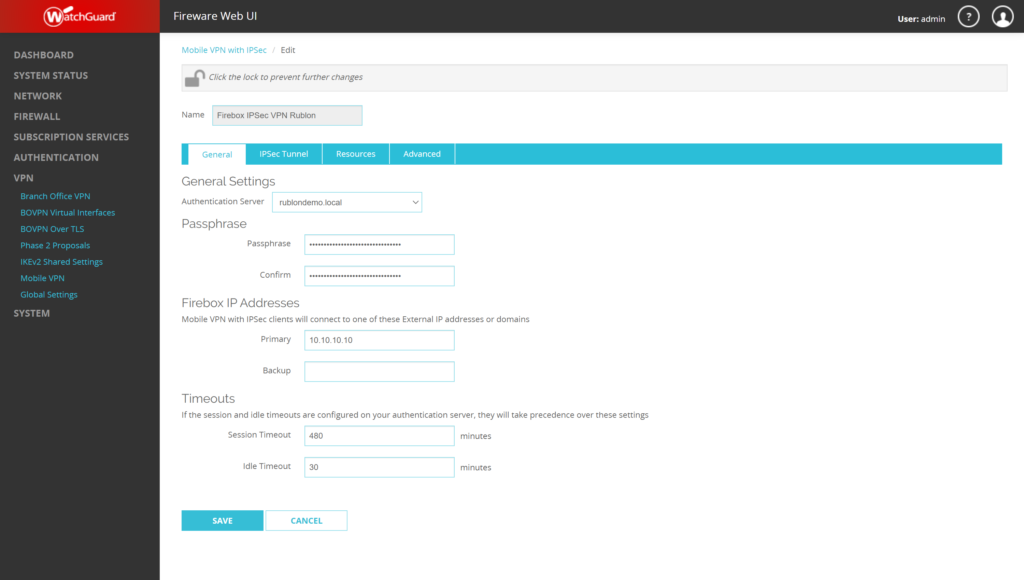
5. Click SAVE to save your changes.
Mobile VPN Configuration with SSL
To make MFA for SSL Mobile VPN work, you have to manually add all your users to WatchGuard VPN and then allow them to use SSL VPN. Let’s do it:
1. In the left pane, expand Authentication and select Users and Groups. Then, click ADD to add a new user.
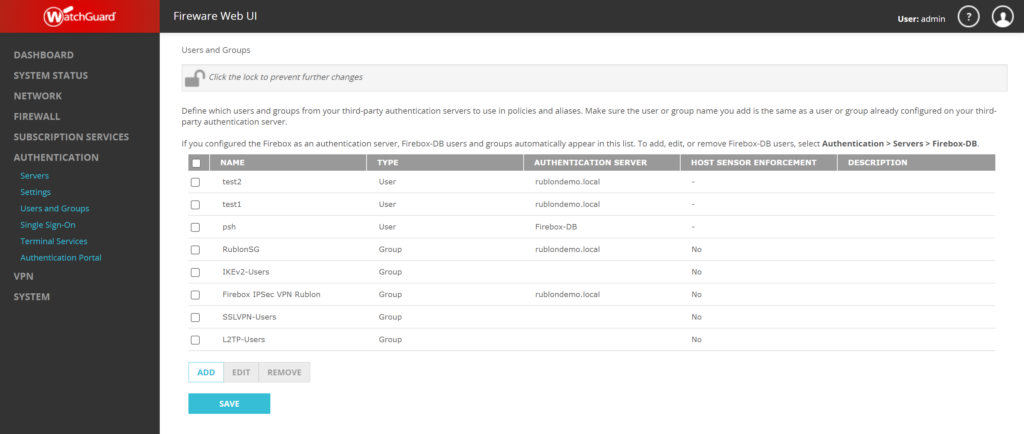
2. In Add User or Group, enter the name of the user and select the authentication source.

| Type | User |
| Name | Enter the username. |
| Description | This is optional, but you can enter a description of the user if you want. |
| Authentication Server | Select the Rublon Authentication Proxy server you have created before. |
3. Other options are optional. Click OK and then click Save in the main list of all groups and users to confirm the new user.
You need to do the above three steps for all users you want to allow to use Mobile VPN with SSL.
4. After you added all your users, you can configure SSL VPN. In the left pane, click VPN and select Mobile VPN. Then, navigate to the SSL section and click CONFIGURE.
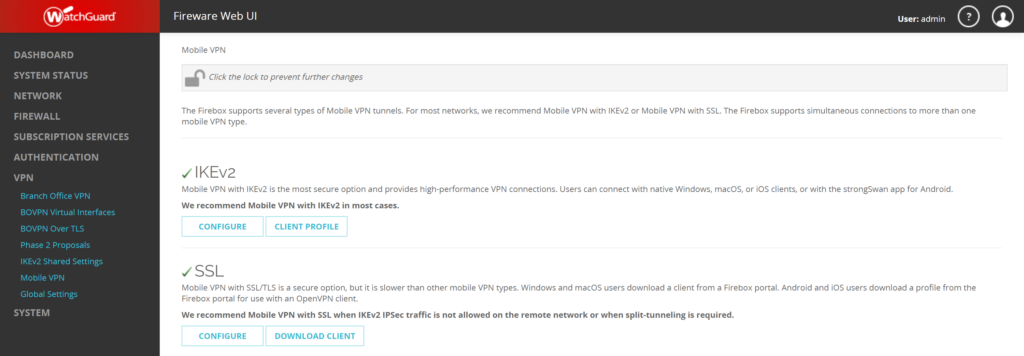
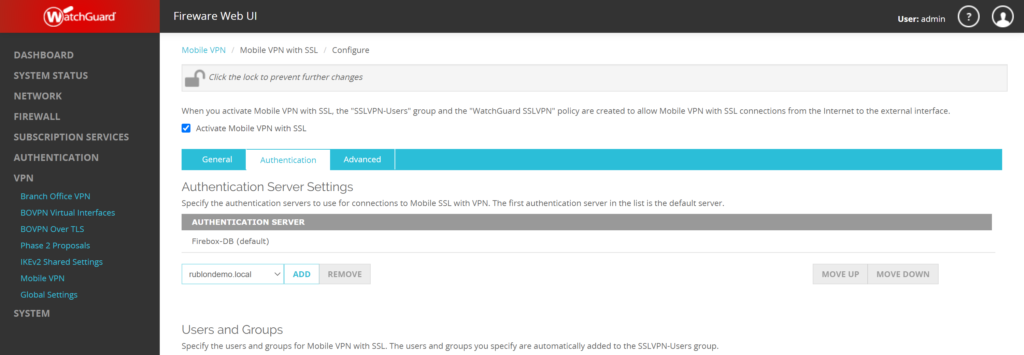
5. Select the Authentication tab.
6. In AUTHENTICATION SERVERS, select your Rublon Authentication Proxy server and click ADD. Then, select it on the list of authentication servers and click MOVE UP to make it default.
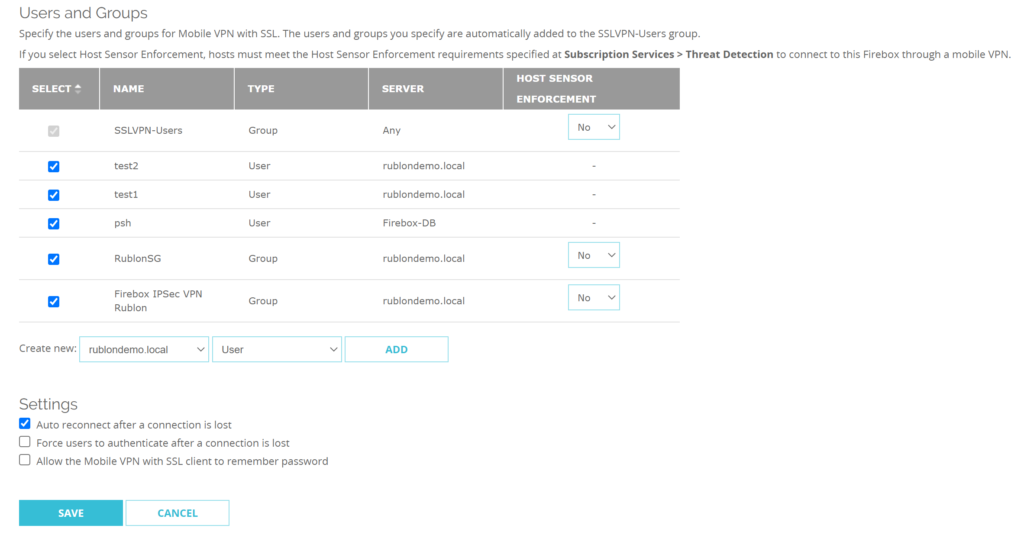
7. In Users and Groups, select the groups and users you want to allow to use SSL VPN.
8. Click SAVE to confirm and save the changes you made.
Testing Multi-Factor Authentication (MFA) for WatchGuard Mobile VPN (IPSec)
In this WatchGuard Mobile IPSec VPN testing example, we used the WatchGuard Mobile VPN application (Mobile VPN Monitor). The first time you run WatchGuard Mobile VPN, you have the opportunity to create a VPN profile. When creating the VPN profile, you can import the configuration file generated in Mobile VPN.
After importing a connection profile, test the connection:
1. Open the WatchGuard Mobile VPN client and click the red Connection button.

2. Enter your User ID and password and click OK.

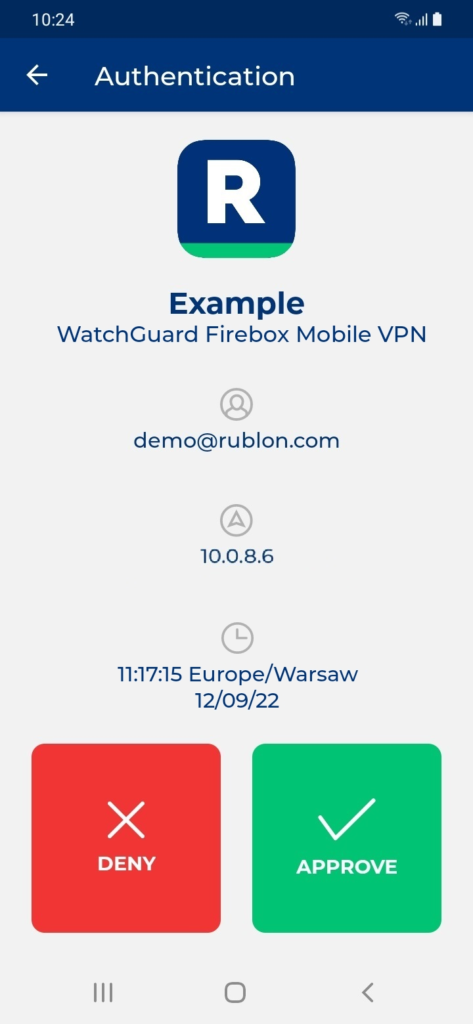
3. Rublon will send a Mobile Push authentication request to your phone. Tap APPROVE.
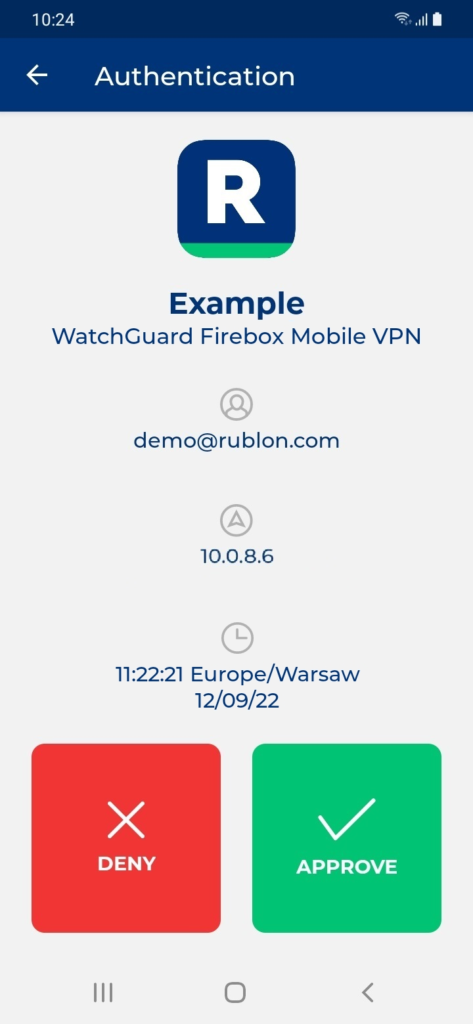
4. You will connect to the VPN.

Testing Multi-Factor Authentication (MFA) for WatchGuard Mobile VPN (SSL)
In this WatchGuard Mobile SSL VPN testing example, we used the WatchGuard Mobile VPN with SSL client.
1. Provide the IP of your server, the user name and password, and click Connect.

2. Rublon will send a Mobile Push authentication request to your phone. Tap APPROVE.
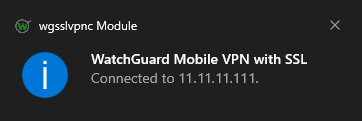
3. After approving the push, the window will minimize, and you will see a notification informing you that a connection was made.
Troubleshooting
Blast-RADIUS Vulnerability Protection
RADIUS integrations may enforce the validation of the Message-Authenticator RADIUS attribute as part of their mitigations for the Blast-RADIUS vulnerability.
The Rublon Authentication Proxy supports the Message-Authenticator attribute starting from version 3.5.3. The Rublon Auth Proxy uses the force_message_authenticator option in the configuration file (set to true by default) to safeguard against Blast-RADIUS attacks.
If you are experiencing issues with your RADIUS integration, ensure that the force_message_authenticator is set to true.
If you are using Rublon Authentication Proxy 3.5.2 or older, update to the newest available version.
If you encounter any issues with your Rublon integration, please contact Rublon Support.