Last updated on May 6, 2025
Overview of MFA for Awingu
Note
Supported Authentication Methods
Demo Video of MFA for Awingu
Before your start
Configuration of MFA for Awingu
Rublon Authentication Proxy
log:
debug: false
rublon:
api_server: https://core.rublon.net
system_token: system_token_obtained_from_rublon_admin_console
secret_key: secret_key_obtained_from_rublon_admin_console
proxy_servers:
- name: RADIUS-Proxy
type: RADIUS
ip: 172.16.1.100
port: 1812
radius_secret: secret_to_communicate_with_the_proxy
mode: nocred
auth_method: email
Awingu
2. Fill in the Multi-factor Authentication section. Refer to the following image and table to learn how to fill in the form.
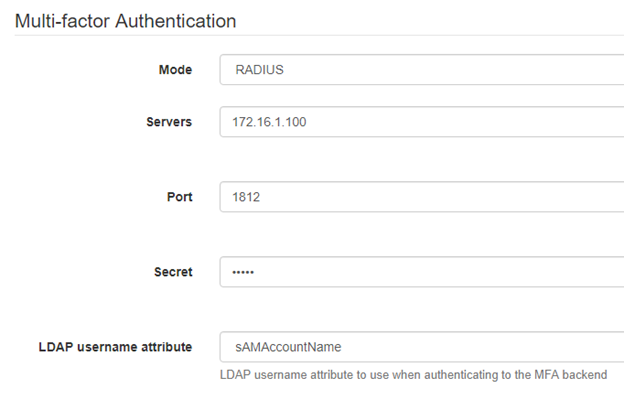
| Mode | Set to RADIUS |
| Servers | The IP address of your Rublon Authentication Proxy server |
| Port | The port of your Rublon Authentication Proxy server |
| Secret | The RADIUS SECRET you set in Rublon Authentication Proxy |
| LDAP username attribute | Use the same USERNAME_ATTRIBUTE you set in Rublon Authentication Proxy. By default, it is set to “sAMAccountName” |
3. Click the Apply button to save the changes.
4. Your configuration is now complete. You can use Rublon 2FA when logging in to Awingu.
Example of using Rublon MFA for Awingu
The example below shows how Rublon authenticates a particular user when they try to log in to Awingu.
1. First, they are asked to provide their username and password.
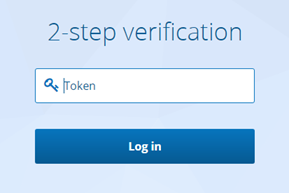
- 123456 – a Passcode (6-digit TOTP code generated by Rublon Authenticator or another third-party authentication app like Google Authenticator or Microsoft Authenticator)
- 123456789 – a Bypass Code (9-digit code received from the administrator)
- push – a Mobile Push is sent to their phone; requires Rublon Authenticator
- email – an email message containing an Email Link is sent to their email address
- smsLink – a text message containing an SMS Link
- phoneCall – a Phone Call from Rublon
- <YubiKey OTP code> – insert the YubiKey and press the button on the key; the OTP will be typed automatically and then Enter will be pressed

Note