Last updated on January 7, 2026
MFA for Azure AD is a security feature that requires users to provide two or more forms of verification before they can access their accounts or resources. Azure AD MFA helps protect your organization from identity attacks, such as phishing, password spraying, and credential theft.
In this article, you will learn how to enable and use MFA for Azure AD in different ways, depending on your role and scenario. You will also learn how to choose from different MFA methods and factors based on your preferences, needs, and availability. Finally, we will give you some best practices and tips to get the most out of MFA for Azure AD.
Why MFA Is Important For Azure AD
Multi-Factor Authentication (MFA) is a process that requires users to provide two or more forms of verification before they can access their accounts or resources. The verification forms are based on something you know (such as a password), something you have (such as a phone or a hardware key), or something you are (such as a fingerprint or a face scan). By requiring multiple forms of verification, MFA makes it harder for attackers to compromise your credentials or impersonate your identity.
MFA is important for Azure AD because it helps protect your organization from common identity attacks, such as:
- Phishing. A fraudulent attempt to obtain your credentials or personal information by sending you an email or a message that looks like it comes from a legitimate source, such as your bank, your employer, or a trusted website.
- Password spraying. A brute-force attack that tries to guess your password by using common or weak passwords across multiple accounts or services.
- Credential theft. A malicious act of stealing your credentials by using malware, keyloggers, or other techniques.
By using MFA for Azure AD, you can reduce the risk of these attacks and enhance the security of your accounts and resources. According to Microsoft, users who enable MFA for their accounts are 99.9% less likely to be compromised than those who only rely on passwords.
How Does Azure Active Directory MFA Work?
Azure Active Directory (Azure AD) Multi-Factor Authentication (MFA) is a feature that provides an additional layer of security for your Azure AD identities. It requires users to verify their identity using a second factor, such as a text message, or mobile app notification, after entering their username and password. This way, even if someone knows your password, they won’t be able to access your account without the second factor.
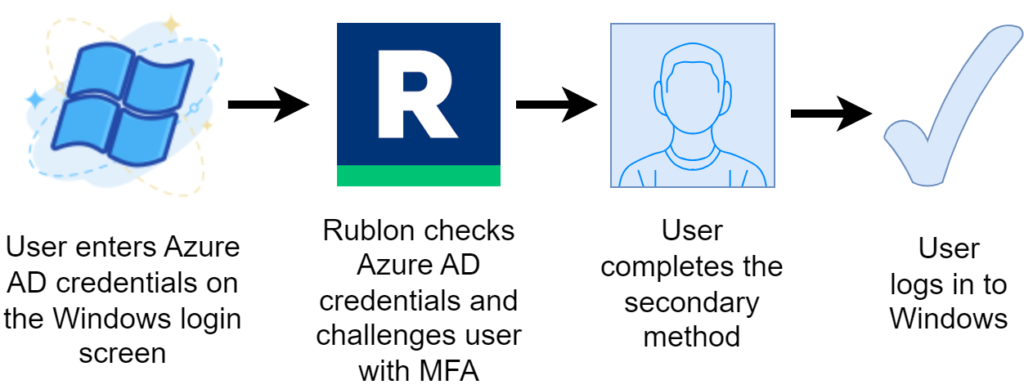
The login flow for Azure AD MFA depends on how you enable and configure it for your users and applications. The following steps describe the login flow for Windows login using Rublon’s Azure AD Multi-Factor Authentication:
- The user types in their Azure AD username and password on the Windows login screen.
- Rublon checks the user’s username and password and sees if they need to do something else to prove their identity. This is called MFA or Multi-Factor Authentication.
- If the user needs to do MFA, Rublon asks them to pick a way to verify themselves. They can use an app on their phone, a text message, or any other of the available methods.
- The user picks a verification method and does what it tells them to do. For example, they might get a notification on their phone and tap on it, or they might get a code in a text message and type it in.
- Rublon makes sure the user did the verification correctly and logs the user in Windows.
The following image illustrates this interaction:
What Are the Different MFA Methods Available for Azure AD
Protect your Azure AD logins with various MFA methods to verify your identity:
- Microsoft Authenticator: A mobile app that allows you to approve sign-ins from your phone using push notifications, biometrics, or one-time passcodes. You can also use the app to generate codes for other services that support authenticator apps.
- Rublon Authenticator: A mobile app that lets you confirm your identity on your phone using a Mobile Push, Mobile Passcode (TOTP), and QR Code with a Fingerprint / Face ID biometric lock.
- FIDO security key: A physical device that you can plug into your computer or tap on your phone to sign in without a password. You can also use it as a backup method in case you lose your phone or access to the app.
- SMS: A method that sends you a text message with a one-time passcode that you can enter to sign in. You can use it as a backup method in case you don’t have access to other methods.
- Email Link: A magik link you receive to your email address. Click a link in the email message to sign in to your account.
You can choose from these methods based on your preferences, needs, and availability. You can also use multiple methods for your account and switch between them as needed.
How to Enable and Use MFA for Azure AD
Rublon is a service that provides MFA for various applications and platforms, including Windows Logon and RDP. Rublon MFA for Windows Logon and RDP adds a second layer of security to your Remote Desktop and local logons by requiring you to approve or deny each login attempt from your phone or another device. Here’s good news. Rublon MFA for Windows Logon and RDP works with Azure AD credentials, so you can use the same username and password that you use for other Azure AD services.
To enable and use MFA for Azure AD credential logins to Windows Logon and RDP, you need to do the following steps:
- Sign up for Rublon Admin Console and create an application for Windows Logon and RDP.
- Download and install Rublon for Windows Logon.
- Run the installer and follow the prompts.
- When you log in to your Windows client or server using Azure AD credentials, you will see a Rublon Prompt after entering your username and password. You will need to provide an additional form of verification to complete the login.
What Are the Best Practices and Tips for MFA for Azure AD
To get the most out of MFA for Azure AD, you should follow some best practices and tips, such as:
- Activate multiple methods. Registering multiple methods and factors for your account gives you more options and flexibility when you need to verify your identity. It also helps you avoid being locked out of your account if you lose access to one of your methods or factors.
- Keep your methods updated. Keeping your methods updated ensures that you can always receive verification prompts and codes when you need them. You should update your phone number, email address, device name, or other information whenever they change. You should also replace or remove any methods or factors that you no longer use or trust.
- Report any suspicious activity. Reporting any suspicious activity helps protect your account and organization from potential threats. You should report any verification prompts or codes that you did not request or expect, any sign-in attempts that you did not initiate or authorize, and any other unusual behavior on your account or device.
- Educate and train your users on how to use MFA. You should provide clear and consistent guidance to your users on how to register, use, and troubleshoot MFA. You should also explain the benefits and importance of MFA for protecting their accounts and data.
Conclusion
MFA for Azure AD is a security feature that helps protect your organization from identity attacks by requiring users to provide two or more forms of verification before they can access their accounts or resources. MFA for Azure AD offers various methods and factors that you can use to verify your identity, such as Microsoft Authenticator, FIDO security keys, and more. Follow the best practices and tips to get the most out of MFA for Azure AD.