Microsoft is slowly rolling out Windows 11. Some Windows 10 devices have already started prompting their users with information about a possible free
Rublon Adds MFA to Your VMware Horizon View (VDI) Logins
Nowadays, Virtual Desktop Infrastructure (VDI) has become the new standard across industries around the world. The benefits of VDI include simpler
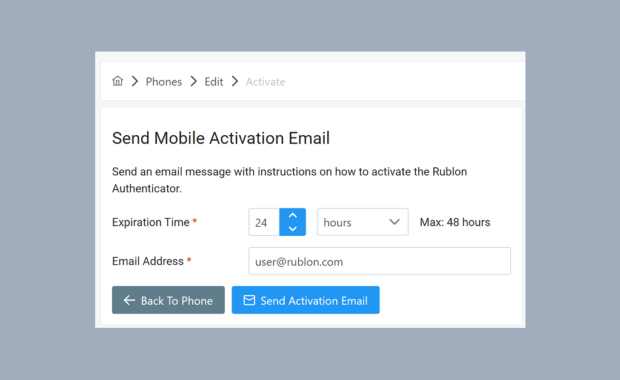
Administrators Can Now Send Mobile Activation Emails To Users
We have just added a new helpful feature to the Rublon Admin Console. This new feature makes the activation of mobile devices much easier for users by
Google To Enforce 2FA on 150m Users
Google plans to auto-enroll 150 million users in 2-Step Verification (2SV) by late 2021. In addition to that, 2 million YouTube creators will have to
Take Your MFA to the Next Level With YubiKey Bio
Yubico’s first biometric authentication security key YubiKey Bio Series is now available for purchase. YubiKey Bio reinforces the YubiKey design
What Is Authentication?
Authentication is the process of validating if a person is who they say they are. In the authentication process, a person has to prove their
13 Best Remote Work Security Practices
The outbreak of COVID-19 is forcing us to rethink how we work. With the influx of remote employees, the cybersecurity sector has been busier than
Remembered Devices Now Available for Windows Logon
Not only does our big September update introduce new features, but it also unlocks possibilities that have not been available before. One of these
Big Update Coming Next Week
A big Rublon platform update will be released on Wednesday, September 22, 2021. The process will start at 2:00 am Eastern Time (New York) and will