Last updated on December 8, 2025
Overview
Supported Authentication Methods
Before you start
Configuration
Aha!
1. Log in to Aha!.
2. Go to Settings → Account.
3. Click Security and single sign-on in the Set Security settings section.
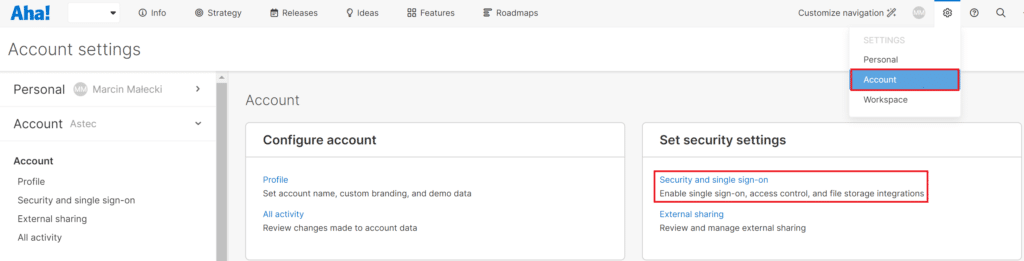
4. Select SAML 2.0 in the Identity provider dropdown. A form will appear.
5. Enter a name for your Identity Provider, e.g. Rublon Access Gateway.
6. Select Metadata URL in Configure using.
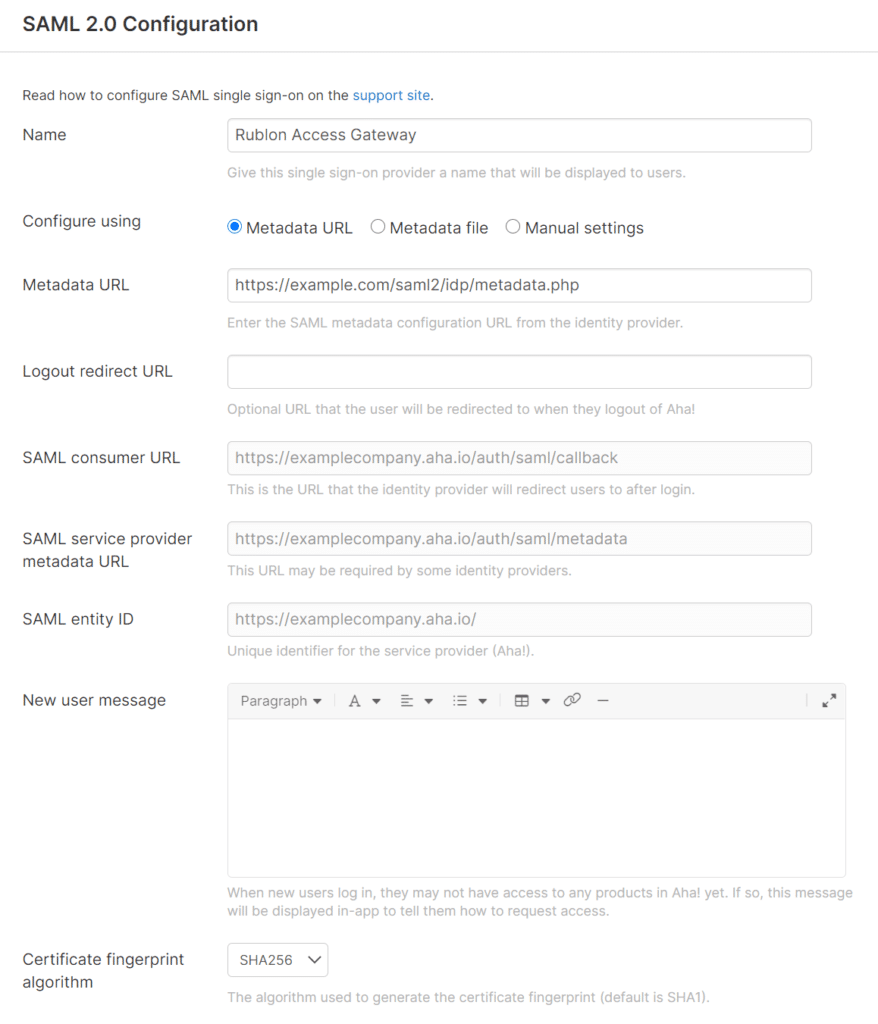
Two other Configure using options exist. You can select the following options instead of Metadata URL:
Metadata file:
- Download the metadata file from Applications → Information for configuring applications with Rublon Access Gateway → DOWNLOAD METADATA.
- Upload this metadata file in the Metadata file field in the SAML 2.0 Configuration form in Aha!.
- Ensure that Certificate fingerprint algorithm is set to SHA256.
- Click Enable.
Manual settings:
- In Single sign-on endpoint, enter the value of SSO URL from Rublon Access Gateway (Applications → Information for configuring applications with Rublon Access Gateway).
- In Certificate fingerprint, enter the fingerprint of the certificate (not the entire certificate) from Rublon Access Gateway (Applications → Information for configuring applications with Rublon Access Gateway → Fingerprint).
- Ensure that Certificate fingerprint algorithm is set to SHA256.
- Click Enable.
10. Go to Settings → Account → Users.
11. Click the name of the user who will be using Rublon 2FA.
12. An Edit User window will appear. Set Identity provider to Rublon Access Gateway (or any other name you set for your identity provider in Step 5).
13. Click Save to save the changes and enable Rublon 2FA for that user.
Rublon Access Gateway
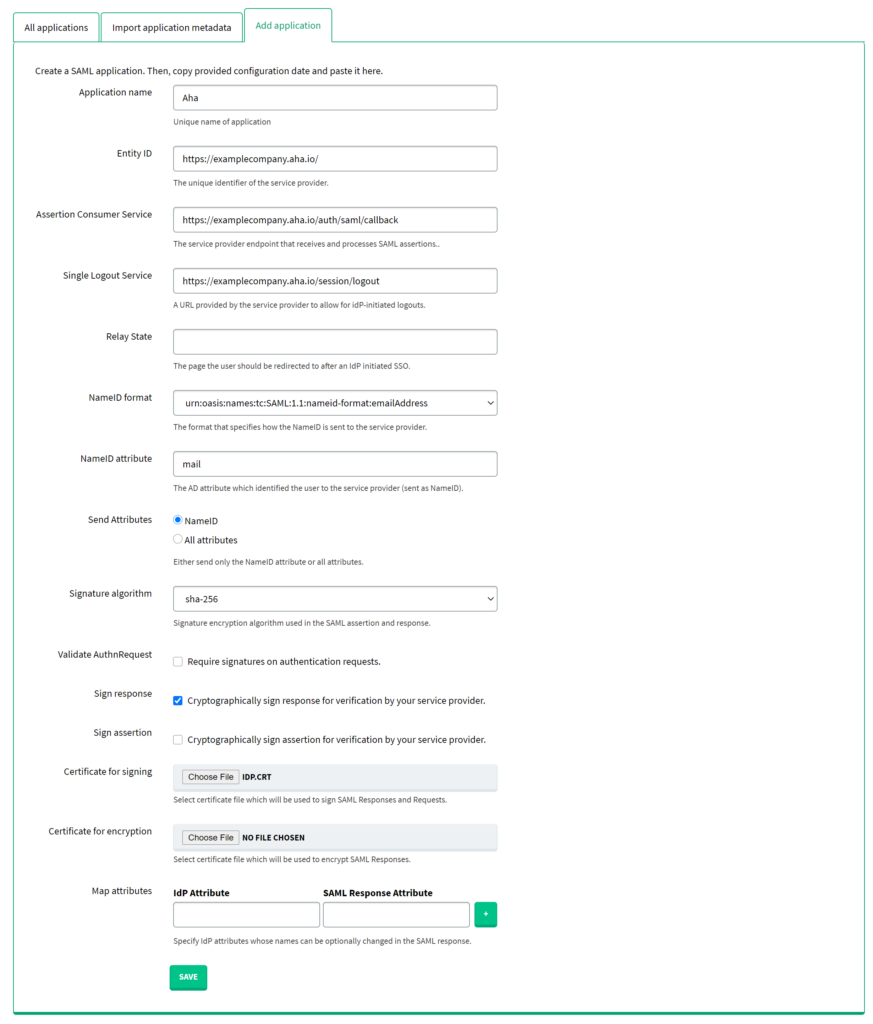
1. In Rublon Access Gateway, go to Applications → Add application.
2. Fill in the form and click SAVE to add a new application. Refer to the following image and table.
Log in to Aha! with Rublon 2FA
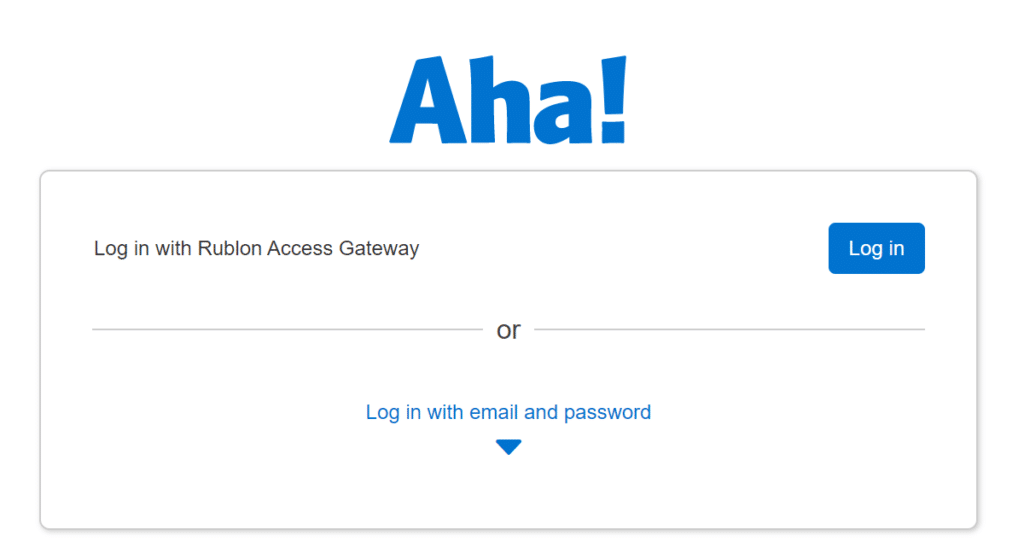

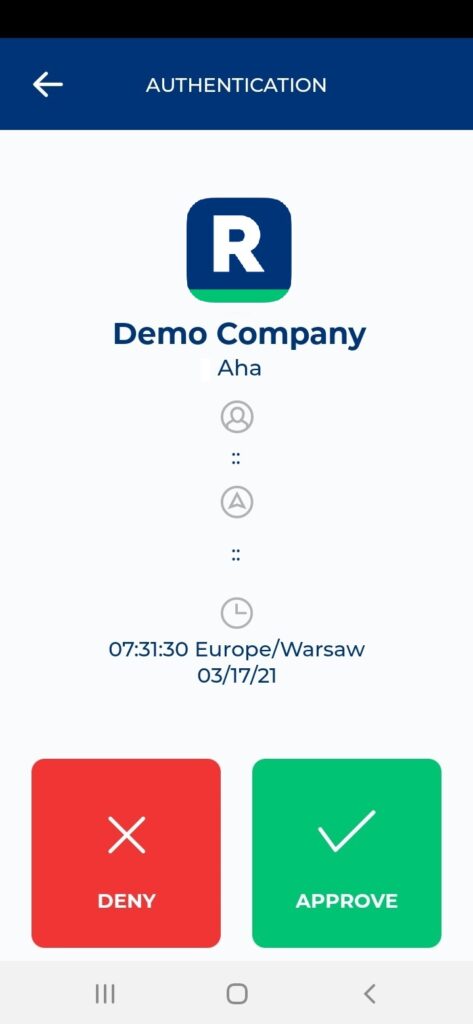
6. You will be successfully logged in to Aha!.
Troubleshooting
If you encounter any issues with your Rublon integration, please contact Rublon Support.