Last updated on February 6, 2025
Overview of MFA for Barracuda Client-To-Site VPN
Supported Authentication Methods
Before you start
Configuration of MFA for Barracuda Client-To-Site VPN
Note
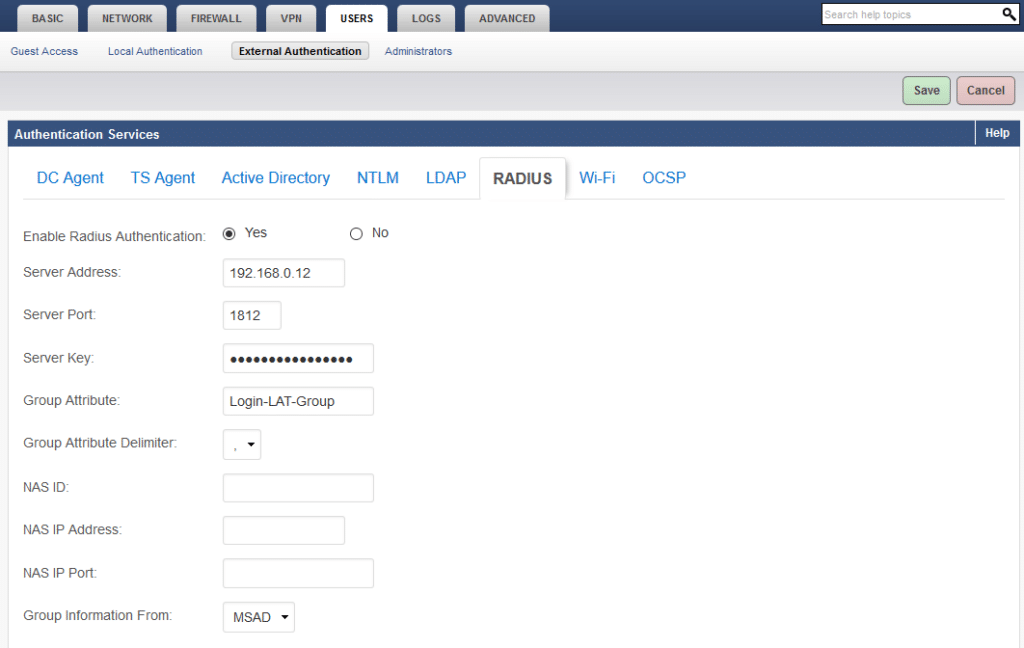
| Server Address | Enter the IP of your Rublon Authentication Proxy server. |
| Server Port | Enter the port of your Rublon Authentication Proxy server. |
| Server Key | Enter the Rublon Authentication Proxy server Secret. |
| Group Attribute | Keep the default value. |
| Group Attribute Delimiter | Keep the default value. |
| NAS ID | If your RADIUS server requires NAS credentials to be set, enter the NAS identifier. |
| NAS IP Address | If your RADIUS server requires NAS credentials to be set, enter the NAS IP Address. |
| NAS IP Port | If your RADIUS server requires NAS credentials to be set, enter the NAS IP Port. |
| Group Information From | Set to MSAD. |
4. Go to VPN → Client-To-Site VPN.
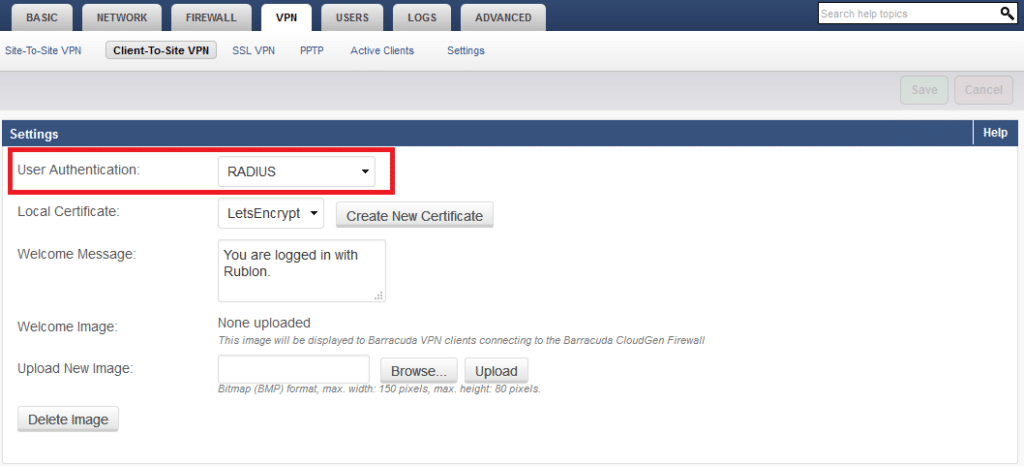
5. Navigate to the Settings section. Select RADIUS in User Authentication. Click Save to save the change.
Log in to Barracuda using MFA for Barracuda Client-To-Site VPN
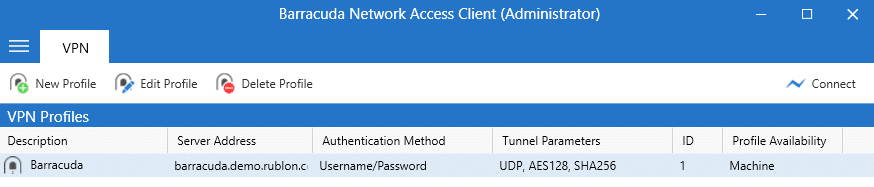
3. Right-click your profile and select Connect.
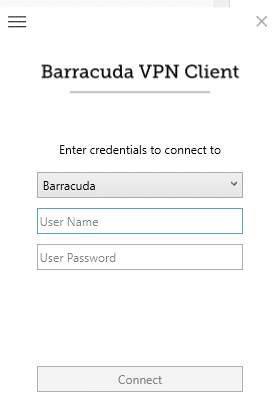
4. Provide your username and password, and click Connect.
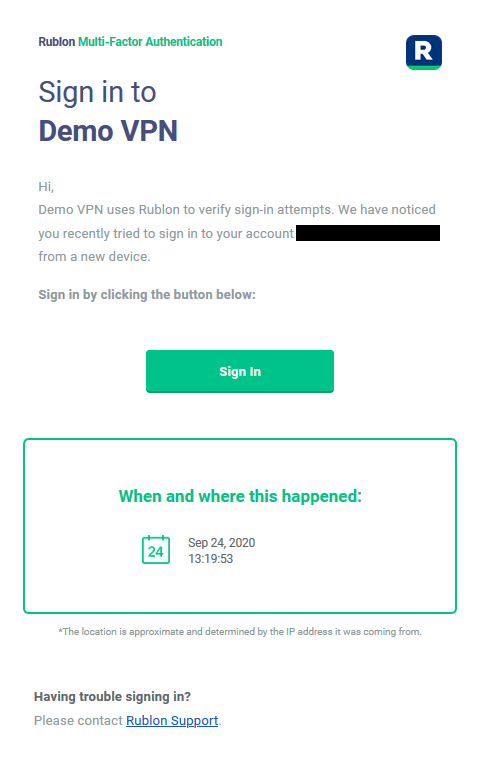
5. Check your mailbox for an email from Rublon. Open the email, and click Sign In.