Last updated on July 8, 2025
Overview of MFA for Cisco FirePower Management using RADIUS
This documentation describes how to integrate Rublon MFA with Cisco FirePower Management using the RADIUS protocol to enable multi-factor authentication for web UI admin interface logins.
Supported Authentication Methods
| Authentication Method | Supported | Comments |
| Mobile Push | ✔ | N/A |
| FIDO | – | N/A |
| Passcode | ✔ | N/A |
| SMS Passcode | – | N/A |
| SMS Link | ✔ | N/A |
| Phone Call | ✔ | N/A |
| QR Code | – | N/A |
| Email Link | ✔ | N/A |
| YubiKey OTP | ✔ | N/A |
| RFID | – | N/A |
Before You Start Configuring MFA for Cisco FirePower Management using RADIUS
Before configuring Rublon MFA for Cisco FirePower Management:
- Ensure you have prepared all required components.
- Create an application in the Rublon Admin Console.
- Install the Rublon Authenticator mobile app.
Required Components
1. User Identity Provider (IdP) – You need an external Identity Provider, such as Microsoft Active Directory, OpenLDAP, or FreeRADIUS.
2. Rublon Authentication Proxy – Install the Rublon Authentication Proxy if you have not already and configure the Rublon Authentication Proxy as a RADIUS proxy.
3. Cisco FirePower Management – Properly installed and configured FirePower Management.
Create an Application in the Rublon Admin Console
1. Sign up for the Rublon Admin Console. Here’s how.
2. In the Rublon Admin Console, go to the Applications tab and click Add Application.
3. Enter a name for your application (e.g., Cisco FirePower Management) and then set the type to Rublon Authentication Proxy.
4. Click Save to add the new application in the Rublon Admin Console.
5. Copy and save the values of the System Token and Secret Key. You are going to need these values later.
Install Rublon Authenticator
Some end-users may install the Rublon Authenticator mobile app. So, as a person configuring MFA for Cisco FirePower Management, we highly recommend you install the Rublon Authenticator mobile app, too. Thanks to that, you will be able to test MFA for Cisco FirePower Management via Mobile Push.
Download the Rublon Authenticator for:
Configuring Multi-Factor Authentication (MFA) for Cisco FirePower Management using RADIUS
Follow the following instructions to set up MFA for Cisco FirePower Management using the RADIUS protocol.
Creating the External Authentication Object
1. Log in to Cisco FirePower Management Web UI.
2. Click the Settings (cog) icon in the upper-right corner and select Users.
3. Select the External Authentication tab.
4. Click + Add External Authentication Object.
5. Create a new External Authentication Object. Refer to the following images and table. The fields not in the table are optional and not required for this integration.
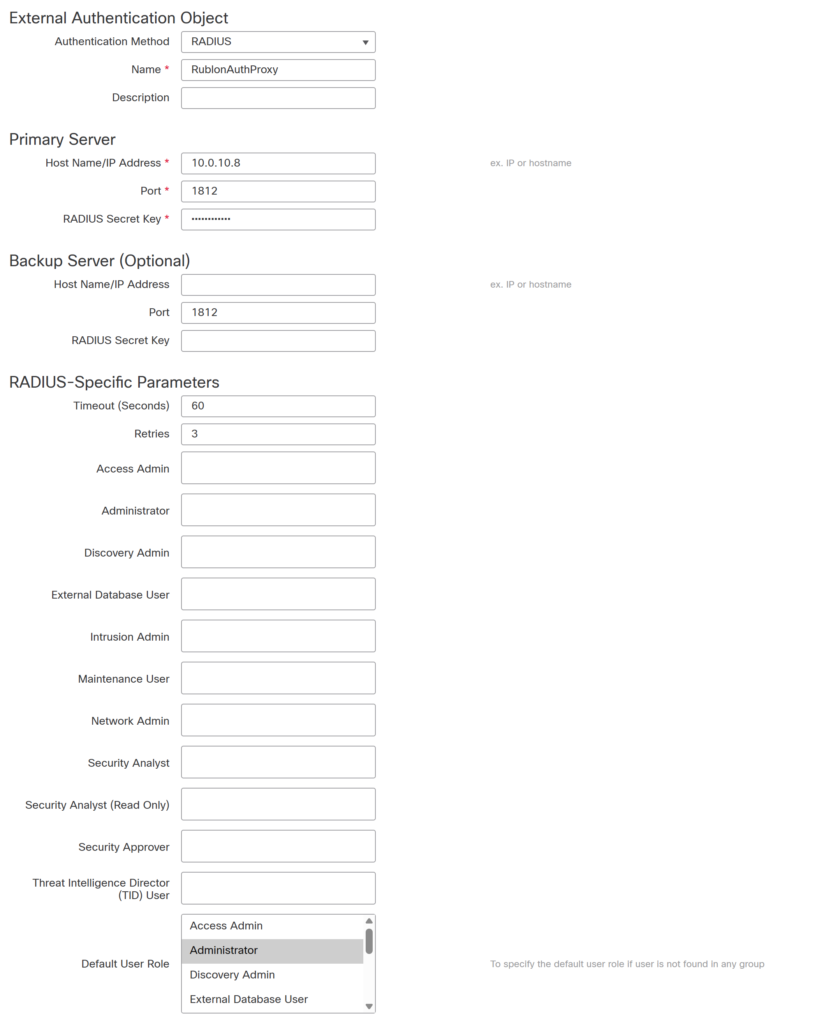
| Authentication Method | Select RADIUS from the dropdown list |
| Name | Enter the name of the RADIUS server (e.g., RublonAuthProxy) |
| Host Name/IP Address | The IP address of the Rublon Auth Proxy server |
| Port | The port of the Rublon Auth Proxy server (1812 is the default RADIUS port) |
| RADIUS Secret Key | RADIUS secret key shared between Cisco FirePower Management and Rublon Auth Proxy |
| Timeout (Seconds) | 60 |
| Retries | 3 |
| Default User Role | Specify the User Role this External Auth method will be available for. |
6. At this stage you can also test and verify your settings by specifying User Name and Password of your user. However, this is optional. Click Save to save and confirm your External Authentication Object.

7. You will be redirected to the External Authentication tab. Switch the newly created RublonAuthProxy object to Enabled.
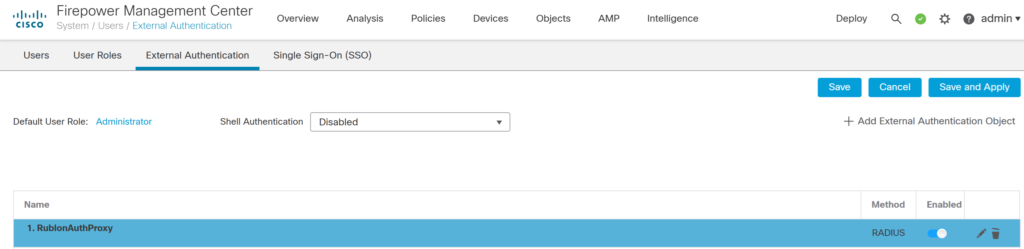
8. Click Save and Apply to finalize your configuration of the new External Authentication Object.
Creating a User and Assigning User Role
1. Select the Users tab and click Create User.

2. In User Configuration, fill in the following:
- User Name: username of the user from your desired IdP (e.g., AD/LDAP User Account). The name has to match the login name from your IdP.
- Authentication: Check Use External Authentication Method
3. In User Role Configuration, fill in the following:
- Default User Roles: The selected Role has to match the Default Role specified in RADIUS External Authentication Object (e.g., Administrator)
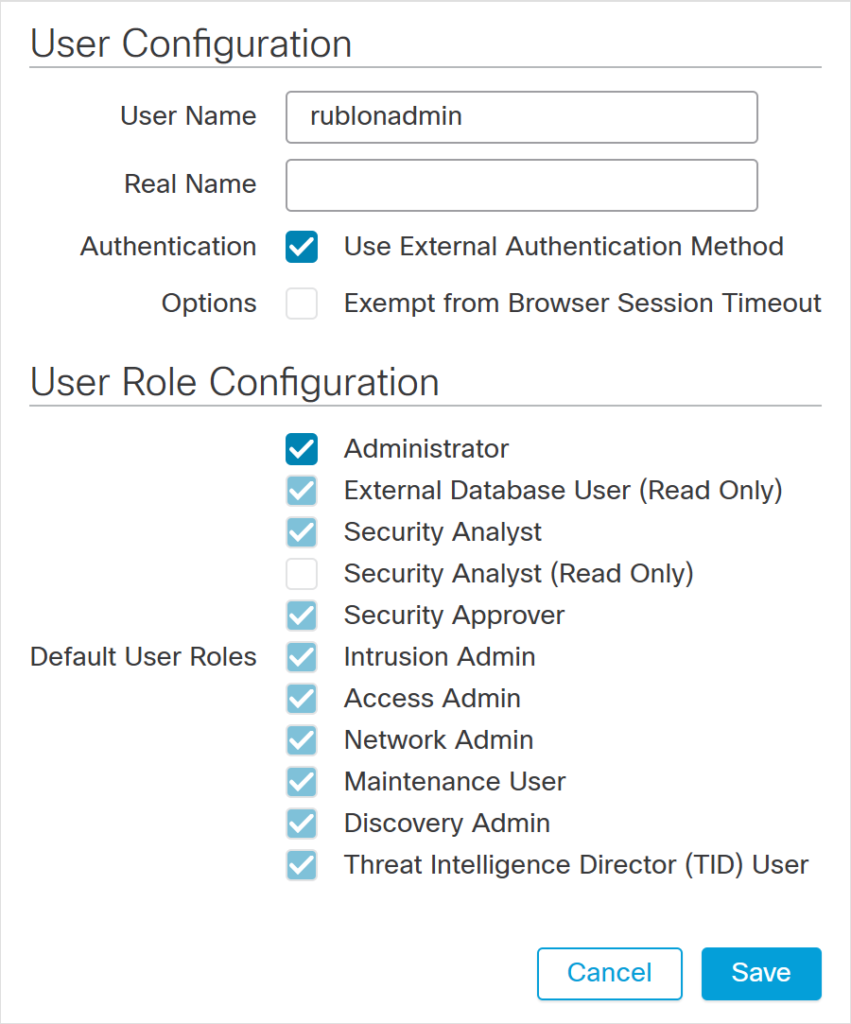
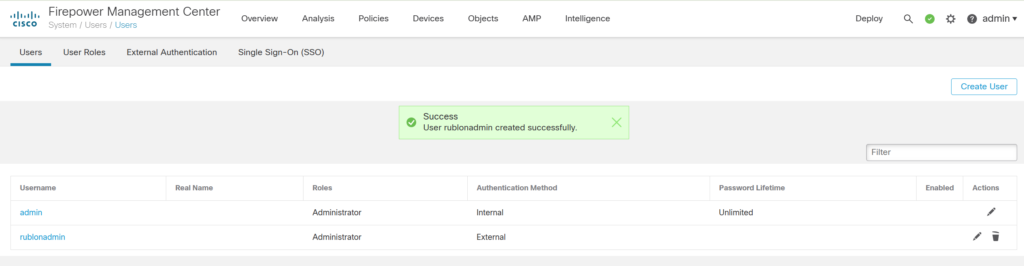
4. Click Save to finish user creation. The new user will appear on the Users list with the Authentication Method specified as External.
Adjusting the Rublon Authentication Proxy Config File
You must include force_message_authenticator: false for your server under proxy_servers like so:
proxy_servers:
- name: RADIUS-Proxy
type: RADIUS
radius_secret: Radius_Secret
ip: 0.0.0.0
port: 1812
mode: standard
force_message_authenticator: false
auth_source: LDAP_SOURCE_1
auth_method: push,emailTesting Multi-Factor Authentication (MFA) for Cisco FirePower Management Integrated Via RADIUS
This example portrays logging in to Cisco FirePower Management via the Cisco FirePower Management Client. Mobile Push has been set as the second factor in Rublon Authentication Proxy configuration (AUTH_METHOD was set to push).
1. Open your browser and navigate to your Cisco FirePower Management web portal.
2. Enter your username and password:
- Enter the username of the user you created in the Users section during configuration.
- Enter the password from your IdP like AD/LDAP.
3. Rublon will send a Mobile Push authentication request to your phone. Tap APPROVE.
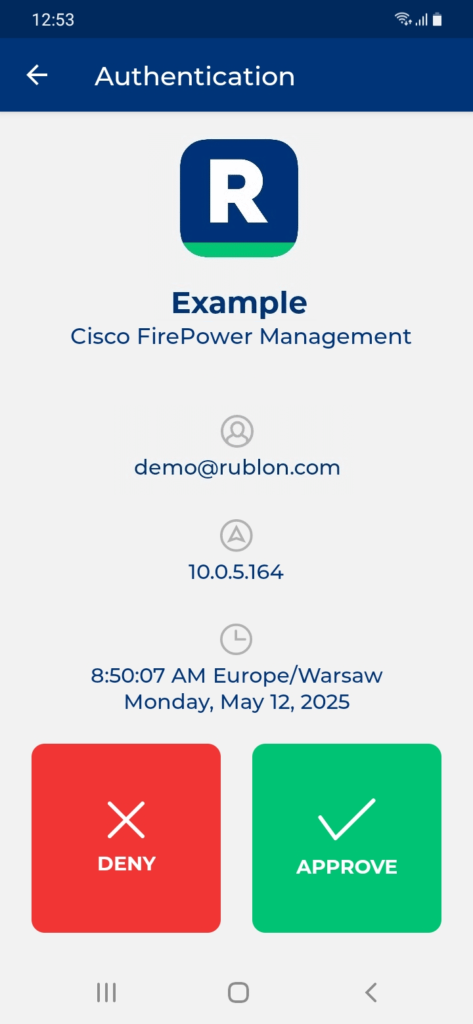
4. You will be connected to the Cisco FirePower Management admin interface.
Troubleshooting of MFA for Cisco FirePower Management using RADIUS
If you encounter any issues with your Rublon integration, please contact Rublon Support.