Last updated on December 8, 2025
Note: If you are looking for a way to integrate Rublon with Cisco FTD Firepower Firewall, refer to MFA for Cisco AnyConnect VPN with Cisco FTD Firepower Firewall – RADIUS and MFA for Cisco AnyConnect VPN with Cisco FTD Firepower Firewall – LDAP(S).
Overview
Demo Video
Supported Authentication Methods
Demo Video
Before you start
You need to install and configure Rublon Access Gateway itself before configuring Cisco AnyConnect VPN with ASA to work with it. Please read the Rublon Access Gateway documentation and follow the steps in the Installation and Configuration sections. Afterward, continue with this document.
Required Components
- Cisco ASA Firewall with firmware, versions from 9.6(22) to 9.6.3-20, or 9.9.1-4 and newer (SAML does not work with versions from 9.6.4-3 to 9.8.2.24).
- ASDM software, version 7.8(2) or higher.
- Rublon Access Gateway
Cisco ASA initial assumptions
- Can communicate with Rublon Access Gateway.
- Has a correctly configured “outside” interface.
- Has its own properly configured SSL certificate (you can check it in: Configuration → Remote Access VPN → Clientless SSL VPN Access → Connection Profiles → Access Certificate → Device Certificate).
- Enables access to its configuration by Cisco ASDM application.
Configuration
This section will guide you on how to integrate Rublon Access Gateway with Cisco AnyConnect VPN with ASA using SAML as the integration protocol.
Prepare Group Policy
If you have already defined Group Policy for Protocol of type Clientless SSL VPN, there is no need to create a new one. You can skip this step and go to the next one.
Sign in to your Cisco ASA firewall with ASDM
1. Go to the Configuration tab.
2. Select Remote Access VPN (at the bottom of the page).
3. Extend Clientless SSL VPN Access.

4. Select Group Policies.

5. If you already have a Group Policy, you can move to the next chapter. Otherwise, click Add in the window on the right side.

6. Give a name to your Group Policy. Expand More Options in the General section, and uncheck Inherit in the Tunneling Protocols section.

Fetch Rublon Access Gateway metadata

Import Rublon certificate to Cisco ASA


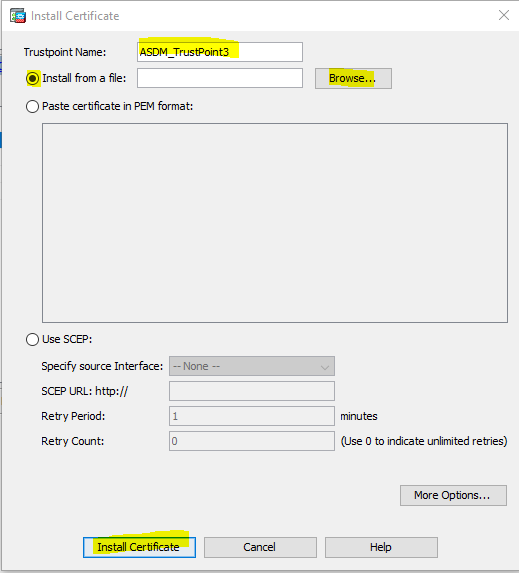
Create a Connection profile
3. Choose the Configuration tab.
4. Choose Remote Access VPN (at the bottom of the page).
5. Extend Clientless SSL VPN Access.
6. Choose Connection Profile and click the Add button.

- Set the Name (e.g.
RublonConnectionProfile). - Set the Alias (e.g.
Rublon). - Choose Authentication Method – Saml.
- Choose the Group Policy you have created before.
- Check Enable Clientless SSL VPN protocol.

- In the IDP Entity ID field, insert Entity ID from Rublon Access Gateway.
- In the Sign in field, insert SSO URL from Rublon Access Gateway.
- In the Sign Out URL field, insert Logout URL from Rublon Access Gateway.
- In the Base URL field, enter the address of the interface “outside Cisco ASA”.
- Identity Provider Certificate – the certificate idP of Rublon Access Gateway which has been imported before (look at Rublon Access Gateway metadata).
- Service Provider Certificate – the certificate configured for Cisco ASA in Connection Profiles → Access Certificate → Device Certificate.
10. Click OK.

IMPORTANT!
Create a new application in Rublon Access Gateway
- Open your web browser and go to the location of the Service Provider Cisco ASA metadata:
PROTOCOL://HOST/saml/sp/metadata/CONNECTIONPROFILE
- Sign In to Rublon Access Gateway.
- Go to the Application tab.
- In the Add Application subtab in the Configuration file field, select the XML file you have downloaded before.

- Click the Upload button.
Manage User Accounts
- Active Directory users’ email addresses must be provided in general settings for each account (General tab, email field)
- User accounts within Cisco ASA must be added for the following elements: Remote Access VPN, AAA Local Users, Local Users. Please use the email address as username.
Log in to ASA VPN with Rublon 2FA



7. Tap APPROVE.
8. After successful authentication, Rublon will redirect you back to the AnyConnect interface and you will be logged in.

Troubleshooting
If you encounter any issues with your Rublon integration, please contact Rublon Support.
