Last updated on February 6, 2025
Overview of MFA for F5 BIG-IP APM VPN
Supported Authentication Methods
Before you start
Configuration of MFA for F5 BIG-IP APM VPN
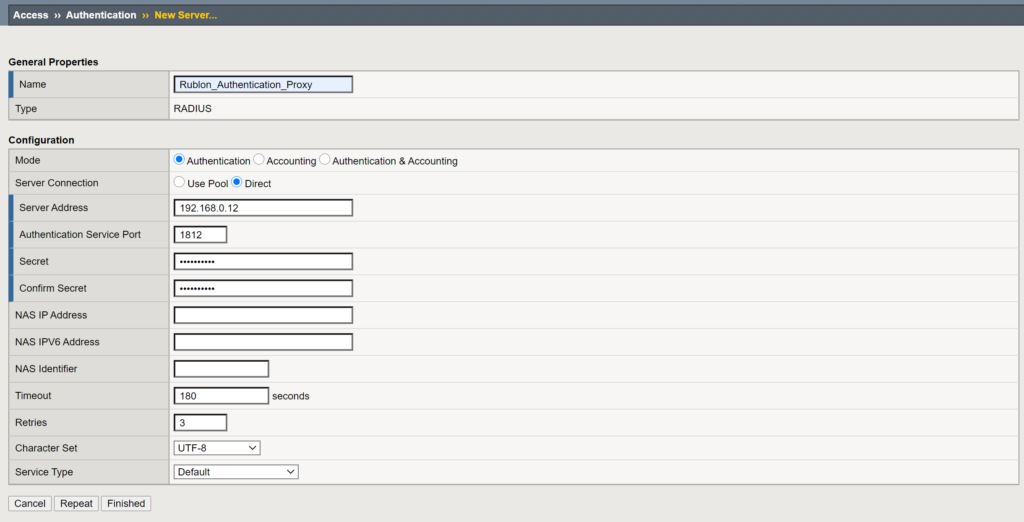
Add your Rublon Authentication Proxy server
3. Click the Create… button to create a new server.
4. Enter a name for your new server.
5. Set Mode to Authentication.
6. Set Server Connection to Direct.
7. Set Server Address and Authentication Service Port. These are the IP address and port of your Rublon Authentication Proxy server.
Modify your Access Policy

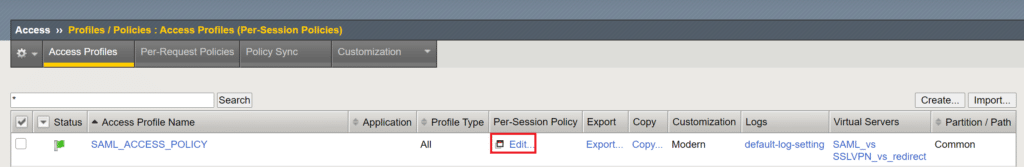
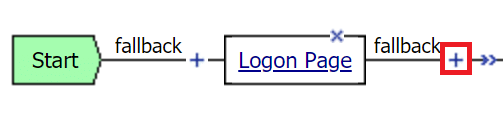
5. Select RADIUS Auth and click Add Item.
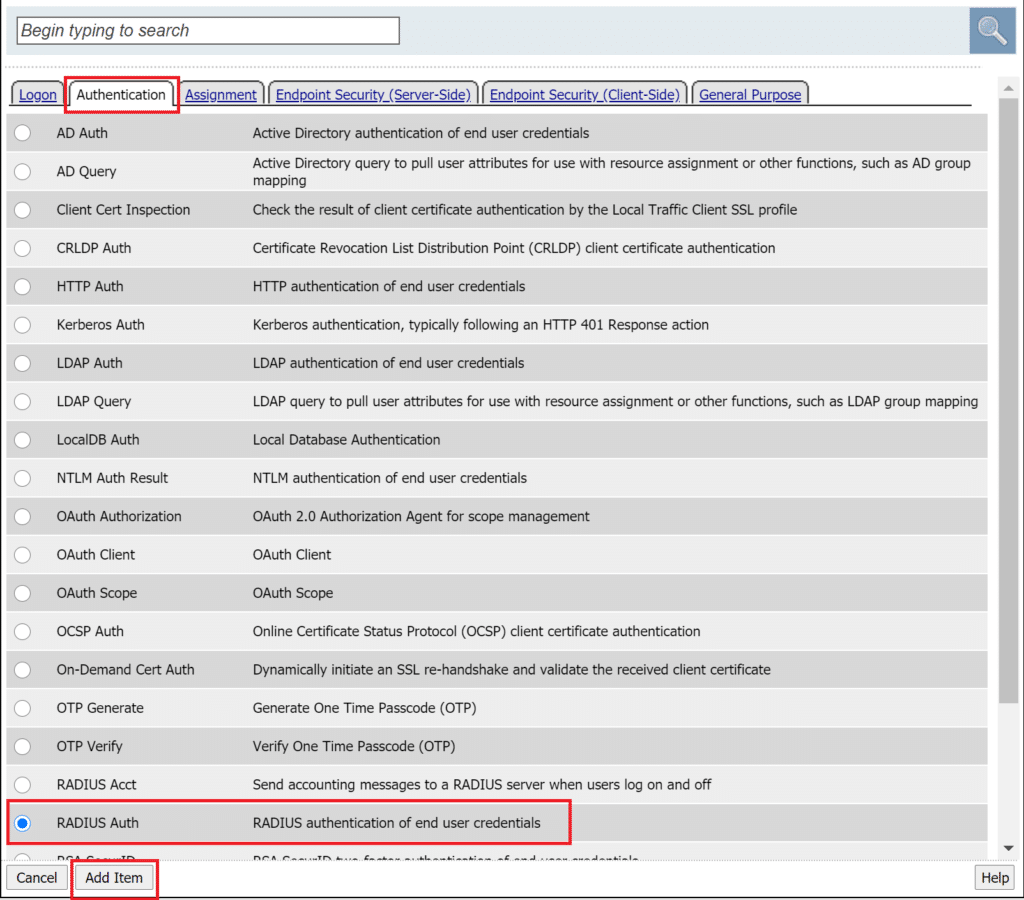
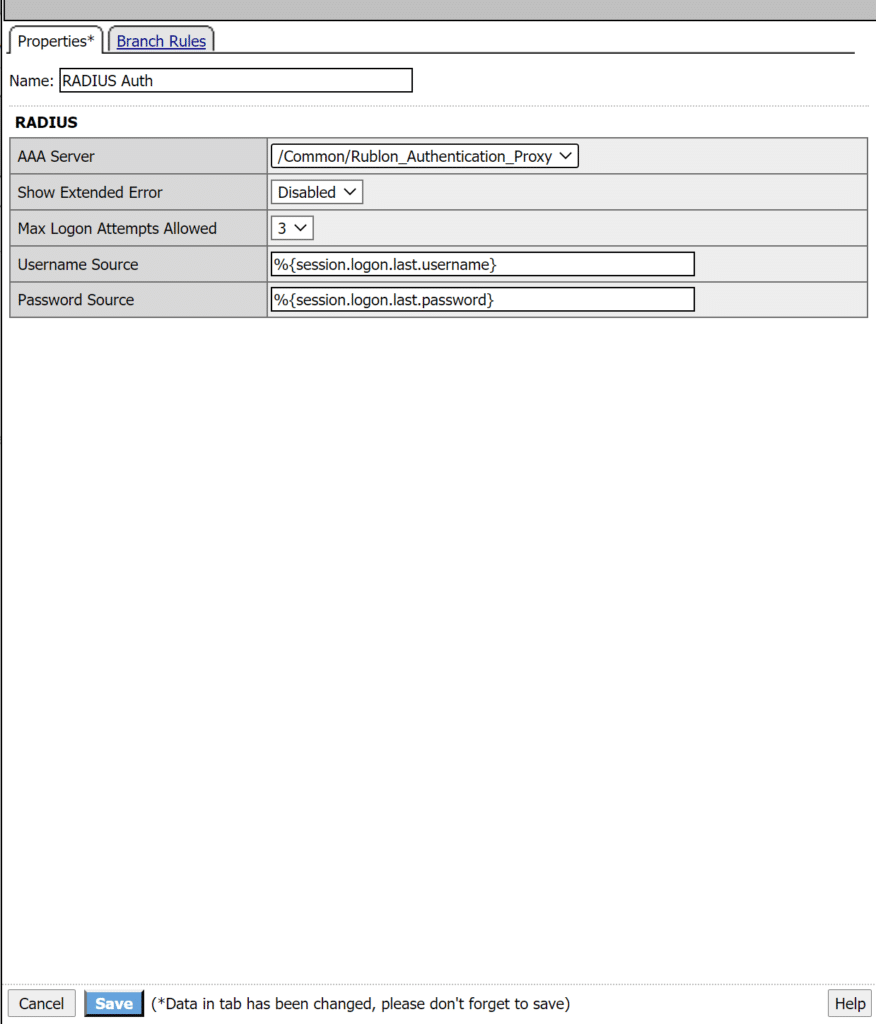
Note
Log in to F5 BIG-IP APM using of MFA for F5 BIG-IP APM VPN

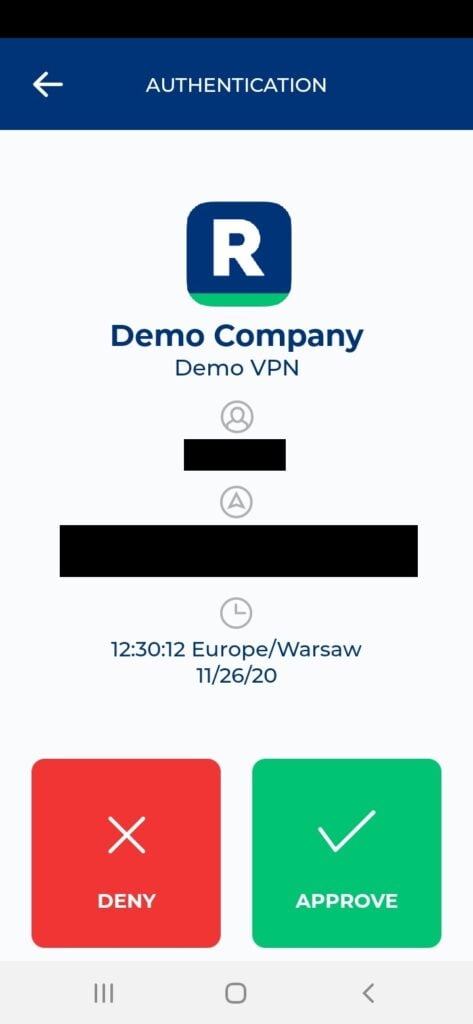
4. Tap APPROVE.
5. You will be logged in to F5 BIG-IP.