Last updated on July 8, 2025
Overview of MFA for Cisco Meraki Client VPN
Supported Authentication Methods
Before You Start Configuring MFA for Cisco Meraki Client VPN
- Ensure you have prepared all required components.
- Install the Rublon Authenticator mobile app.
Required Components
1. User Identity Provider (IdP) – You need an external Identity Provider, such as Microsoft Active Directory, OpenLDAP, or FreeRADIUS.
2. Rublon Authentication Proxy – Install the Rublon Authentication Proxy if you have not already.
3. Cisco Meraki Device – You need a Cisco Meraki device (physical or virtual in the cloud).
4. Cisco Meraki Dashboard – You need to have an account in Cisco Meraki Dashboard, where you have created a network and added your Cisco Meraki device.
Install Rublon Authenticator
Some end-users will install the Rublon Authenticator mobile app. So, as a person configuring MFA for Check Point Mobile Access VPN, we highly recommend you install the Rublon Authenticator mobile app, too. Thanks to that, you will be able to test MFA for Check Point Mobile Access via Mobile Push.
Download the Rublon Authenticator for:
Configuring Multi-Factor Authentication (MFA) for Cisco Meraki Client VPN
Follow the following instructions to set up MFA for Cisco Meraki Client VPN.
Configuring Rublon Authentication Proxy as RADIUS Server
1. In the Cisco Meraki Dashboard, go to Security & SD-WAN → Client VPN.

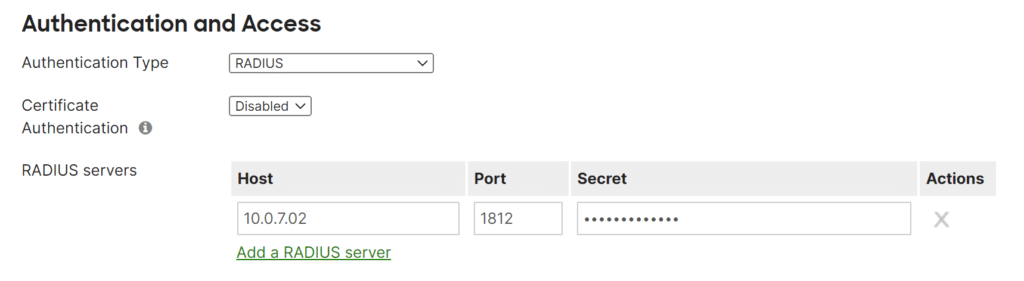
- Authentication Type: RADIUS
- RADIUS servers: The next step describes how to add a RADIUS server
- RADIUS timeout: 60 seconds

3. In RADIUS servers, click Add a RADIUS server and set the following:
- Host: Enter the IP address of your Rublon Authentication Proxy ()
- Port: Enter the port of your Rublon Authentication Proxy (Default: 1812)
- Secret: Enter the RADIUS_SECRET you set in the Rublon Authentication Proxy’s config file.
4. Congratulations. Your integration is complete. You can now test your setup.
Testing Multi-Factor Authentication (MFA) for Cisco Meraki Client VPN
This example shows using the AnyConnect Secure Mobility Client to connect to Cisco Meraki VPN. However, you can use any other VPN client like the built-in Windows VPN client. Mobile Push has been set as the second factor in Rublon Authentication Proxy’s config file (AUTH_METHOD was set to push).
1. The hostname to which you need to connect can be found in the Cisco Meraki Dashboard. Copy the hostname from Security & SD-WAN → Client VPN → AnyConnect Settings → Client Connection Details → Hostname.
(If you do not have the AnyConnect Secure Mobility Client, you can download the Secure Client using one of the links in AnyConnect Client Download Links. The Secure Client includes AnyConnect.)


3. Enter your username and password and click OK.

4. Rublon will send a Mobile Push authentication request to your phone. Tap APPROVE.

