Last updated on July 8, 2025
Overview of MFA for Moodle
This documentation describes how to integrate Rublon MFA with Moodle using the LDAP protocol to enable multi-factor authentication for logins to this e-learning platform.
Supported Authentication Methods
| Authentication Method | Supported | Comments |
| Mobile Push | ✔ | N/A |
| FIDO | – | N/A |
| Passcode | ✔ | N/A |
| SMS Passcode | – | N/A |
| SMS Link | ✔ | N/A |
| Phone Call | ✔ | N/A |
| QR Code | – | N/A |
| Email Link | ✔ | N/A |
| YubiKey OTP | ✔ | N/A |
| RFID | – | N/A |
Before You Start Configuring MFA for Moodle using LDAP
Before configuring Rublon MFA for Moodle:
- Ensure you have prepared all required components.
- Create an application in the Rublon Admin Console.
- Install the Rublon Authenticator mobile app.
Required Components
1. User Identity Provider (IdP) – You need an external Identity Provider, such as Microsoft Active Directory or OpenLDAP.
2. Rublon Authentication Proxy – Install the Rublon Authentication Proxy if you have not already and configure the Rublon Authentication Proxy as an LDAP proxy.
3. Moodle – A properly installed and configured Moodle server. Make sure the Moodle server is configured with the LDAP extension so that users of the LDAP server can log in to the Moodle service. For more information, see the Moodle documentation (1, 2).
Create an Application in the Rublon Admin Console
1. Sign up for the Rublon Admin Console. Here’s how.
2. In the Rublon Admin Console, go to the Applications tab and click Add Application.
3. Enter a name for your application (e.g., Moodle) and then set the type to Rublon Authentication Proxy.
4. Click Save to add the new application in the Rublon Admin Console.
Install Rublon Authenticator
Some end-users will probably use the Rublon Authenticator mobile app. So, as a person configuring MFA for Moodle, we highly recommend you install the Rublon Authenticator mobile app, too. Thanks to that, you will be able to test MFA for Moodle via Mobile Push.
Download the Rublon Authenticator for:
Configuring Multi-Factor Authentication (MFA) for Moodle using LDAP
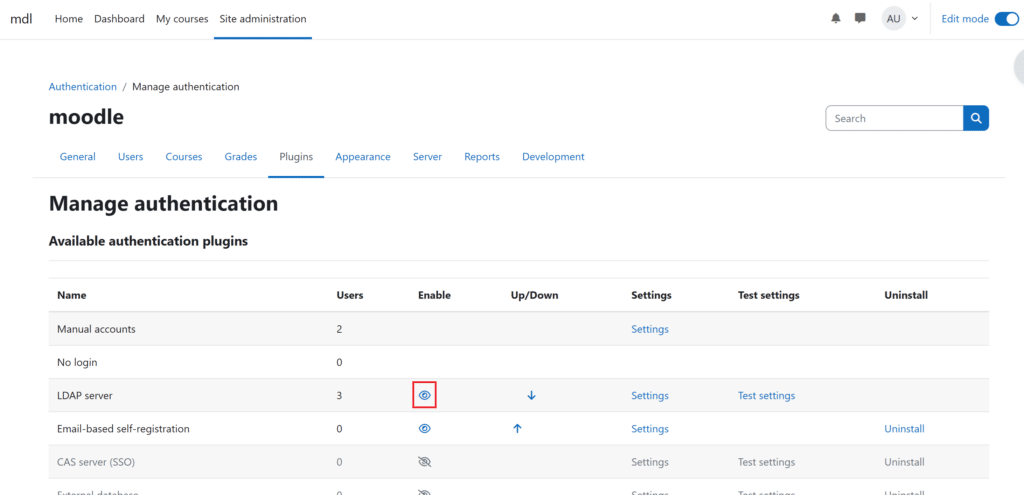
1. Go to Site administration → Plugins → Authentication → Manage authentication and click the eye icon in the LDAP Server row to enable it.
2. Click the Settings link. Now you must fill in the fields in multiple sections and click Save changes. Let’s take it one section at a time.
3. Fill in the fields in the LDAP server settings section. Refer to the following image and table.
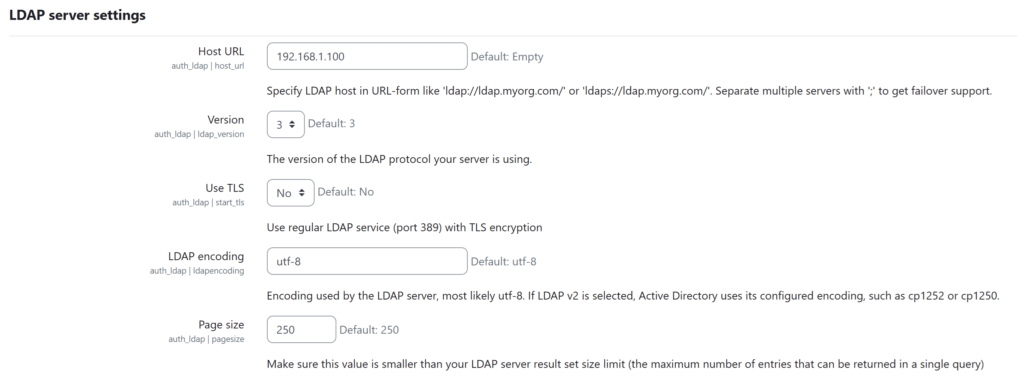
| Host URL | Enter the Rublon Authentication Proxy server’s domain name or IP address. |
| Version | Keep the default version 3 unless you use a very old LDAP server. |
| LDAP Encoding | Keep the default utf-8 encoding unless your LDAP server uses a different one. |
Keep the default values of all other options in this section. If you want to learn more about them or change them, refer to Moodle’s LDAP Server Settings documentation.
4. Fill in the fields in the Bind settings section. Refer to the following image and table.
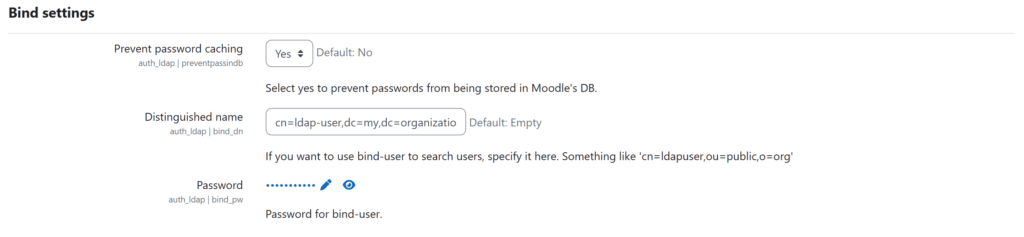
| Don’t cache passwords | Change to Yes so that user passwords are not stored in Moodle’s database. |
| Distinguished Name | Enter the bind user DN that Moodle will use to look up user information in the directory. This will be the same DN as the access_user_dn in the configuration file that Rublon Authentication Proxy uses to connect to its backend LDAP. Use the following form: cn=ldap-user,dc=my,dc=organization,dc=domain |
| Password | Enter the password for the bind user above. |
Keep the default values of all other options in this section. If you want to learn more about them or change them, refer to Moodle’s LDAP Server Settings documentation.
5. Fill in the fields in the User lookup settings section. Refer to the following image and table.
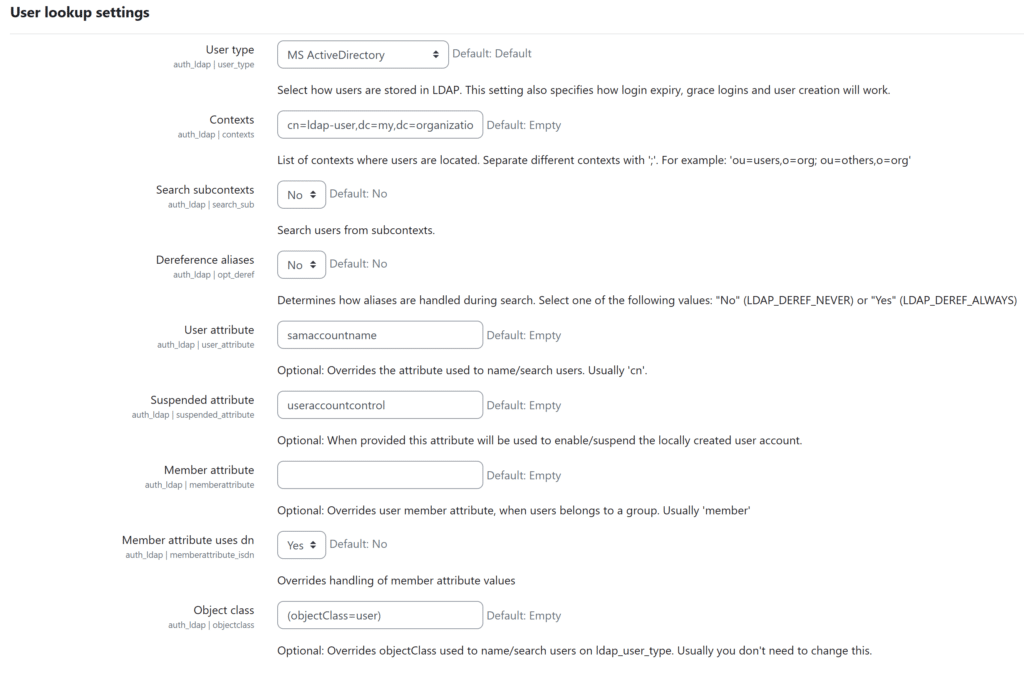
| User type | Choose MS ActiveDirectory if your Identity Provider is Microsoft Active Directory. Choose posixAccount (rfc2307) if your Identity Provider is OpenLDAP. |
| Contexts | Enter the Base DN from which Moodle should start searching for users (e.g., ou=Users,dc=my,dc=organization,dc=domain). This must match what the bind account “sees”. |
| Search subcontexts | Set to Yes if you have any sub-organizational units (subcontexts) and you want Moodle to search there too. |
| User attribute | Enter the LDAP attribute that contains the user’s login name (what the user enters into Moodle as their username). For Active Directory, this attribute is most often samaccountname; for OpenLDAP, it’s uid. |
| Suspended attribute | For Active Directory, use useraccountcontrol. |
| Member attribute uses dn | Set to Yes. |
| Object class | For Active Directory, enter: (objectClass=user) For OpenLDAP, enter: (objectClass=posixAccount) |
Keep the default values of all other options in this section. If you want to learn more about those other options, refer to Moodle’s LDAP Server Settings documentation.
6. Keep the default values of options in all other sections. If you want to change them, you can learn about each in Moodle’s LDAP Server Settings documentation.
7. Click Save changes at the bottom of the page to save your changes.
8. Congratulations. You have successfully configured Rublon MFA for Moodle using LDAP. You can now test MFA.
Testing Multi-Factor Authentication (MFA) for Moodle Integrated Via LDAP
This example portrays logging in to Moodle with Rublon Multi-Factor Authentication. Mobile Push has been set as the second factor in Rublon Authentication Proxy configuration (AUTH_METHOD was set to push).
1. Go to http://your.moodle.site/ and log in to Moodle using your username and password.
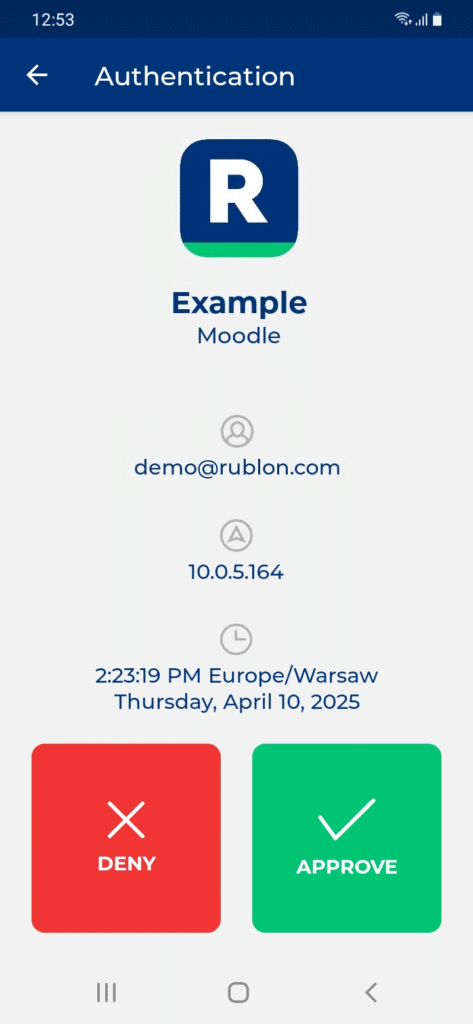
2. Rublon will send a Mobile Push authentication request to your phone. Tap APPROVE.
4. You will be logged in to Moodle.
Troubleshooting MFA for Moodle Using LDAP
If you encounter any issues with your Rublon integration, please contact Rublon Support.