Last updated on April 23, 2024
Overview of MFA for Open edX
Multi-Factor Authentication (MFA) for Open edX is an additional security measure that requires users to provide two forms of authentication in order to gain access to Open edX. The first factor requires the user to enter their Active Directory / RADIUS username and password. After entering the correct credentials, the second factor is a secondary authentication process using a Mobile Push or Email Link. Once both steps are completed, the user is granted access to the resource. Enabling MFA for Open edXmakes it more difficult for hackers to gain access even if they are aware of the user’s login credentials.
The purpose of this document is to enable Rublon Two-Factor Authentication (2FA) for users logging in to Open edX. In order to achieve that, you have to use Rublon Access Gateway. All required steps will be described in this document.
Supported Authentication Methods
| Authentication Method | Supported | Comments |
| Mobile Push | ✔ | N/A |
| FIDO | ✔ | N/A |
| Passcode | ✔ | N/A |
| SMS Passcode | ✔ | N/A |
| SMS Link | ✔ | N/A |
| Phone Call | ✔ | N/A |
| QR Code | ✔ | N/A |
| Email Link | ✔ | N/A |
| YubiKey OTP | ✔ | N/A |
| RFID | – | N/A |
Before you start
You need to install and configure Rublon Access Gateway itself before configuring Open edX to work with it. Please read the Rublon Access Gateway documentation and follow the steps in the Installation and Configuration sections. Afterward, follow the appropriate Configuration section in this document.
Configuration of MFA for Open edX
Follow these steps to enable Rublon 2FA in Open edX.
Open edX
1. Log in to the LMS Administration panel as administrator.
2. Navigate to the THIRD-PARTY AUTHENTICATION section.
3. Click Add to the right of Provider Configuration (SAML IdPs) to add a new SAML IdP.
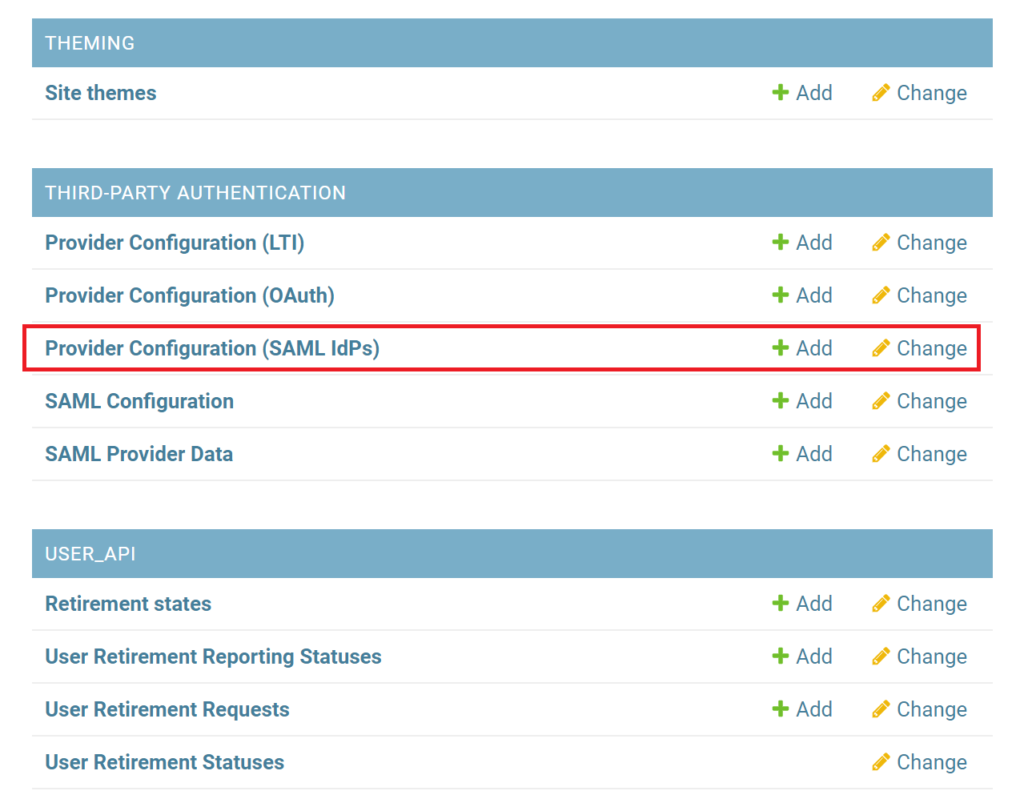
4. Check Enabled.
5. Define a Name for your provider. The name you set here will be displayed as a label for the login button in the login form, so we recommend setting Rublon as the name.
6. Define a Slug for your provider. Slug is a unique name to identify a provider. A slug cannot contain spaces, so replace spaces with dashes, e.g. rublon-idp.
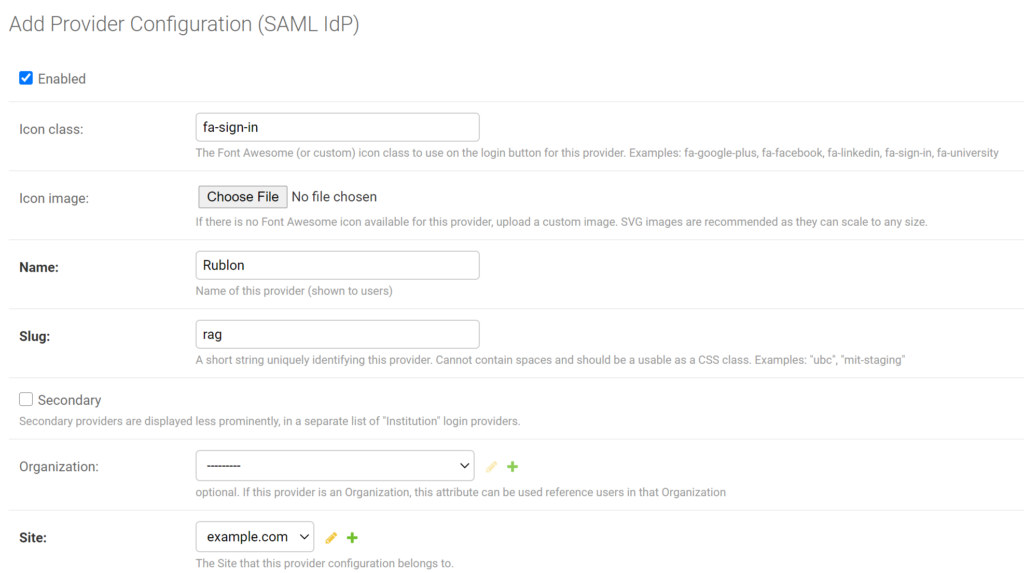
7. Click the green + (plus) button to add the Site this provider configuration will belong to.
8. A new window will open. Set Domain name and Display name. Click SAVE to add the site.
9. Check Visible and Enable sso id verification. Configure the other options as required or leave the default values.
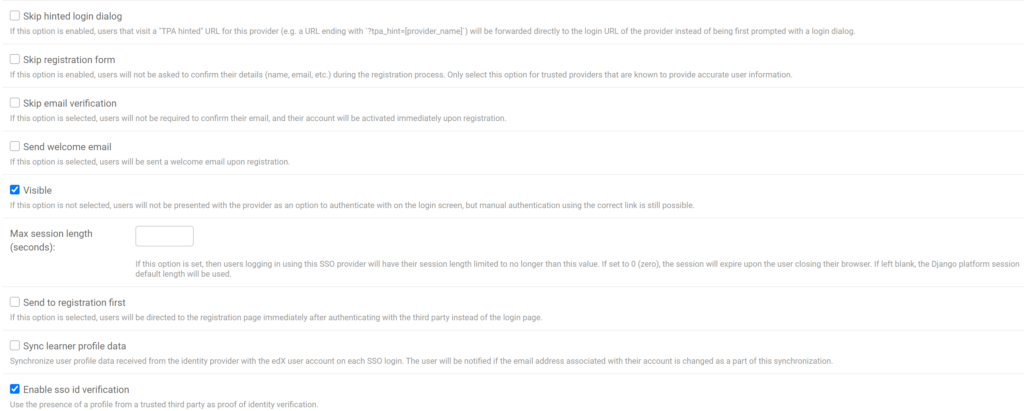
10. Leave the default value in the Backend name field.
11. Enter the value of Entity ID from Rublon Access Gateway (Applications → Information for configuring applications with Rublon Access Gateway) in both Entity ID and Metadata source.
12. The next few fields relate to SAML attribute names and their default values. Define User ID Attribute (for OpenLDAP it will be cn, for Active Directory it will be sAMAccountName). Set Email Attribute to mail.
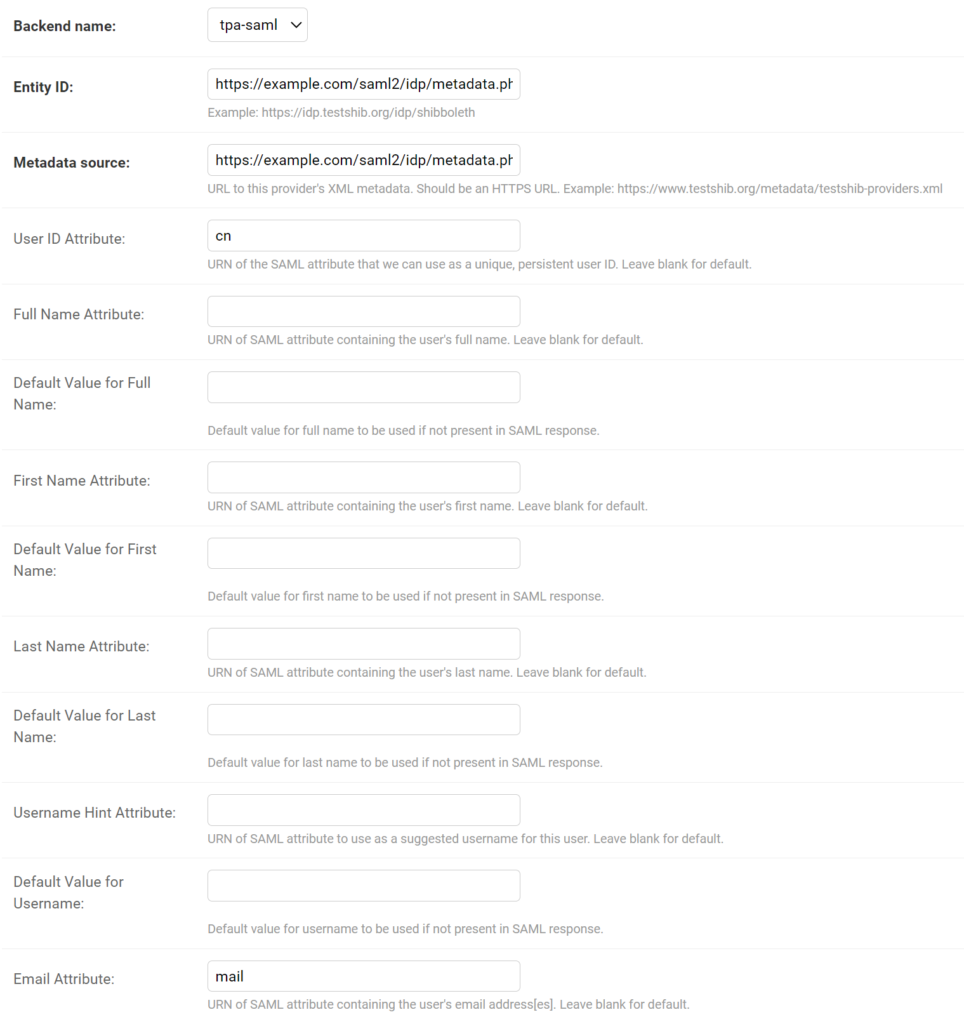
13. Check Enable automatic metadata refresh.
14. Set Standard SAML Provider in Identity Provider Type.
15. Check Debug Mode if you would like to see more information in the logs in case of any problems.
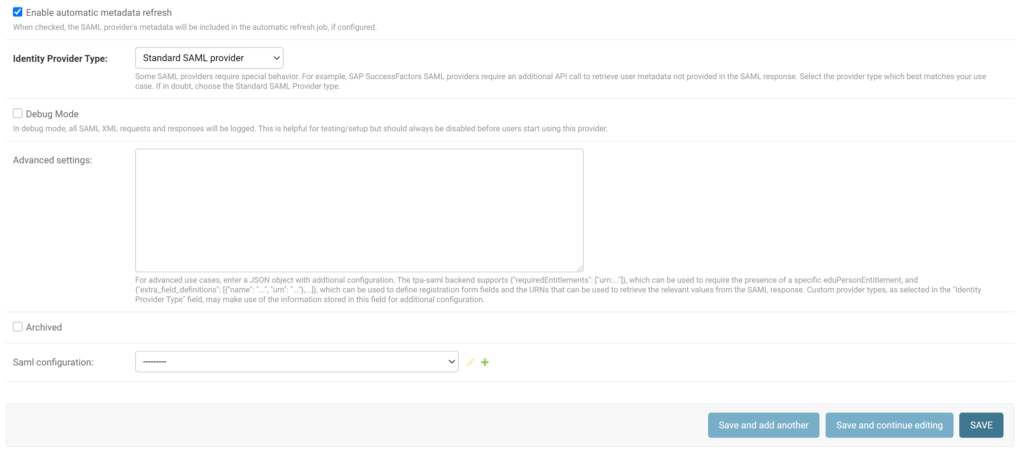
16. Click the green + (plus) button to add a new SAML Configuration.
17. A new window will open. Refer to the following image and table.
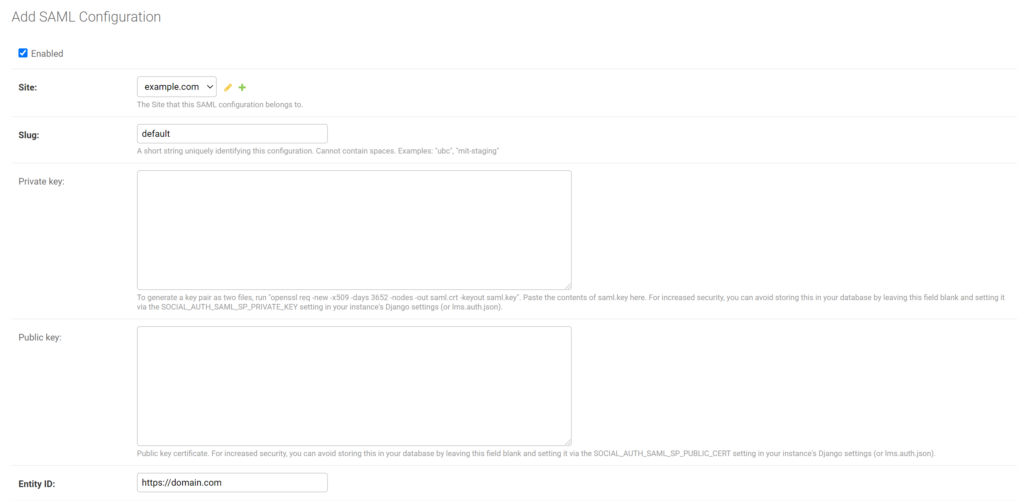
| Enabled | Check. |
| Site | Select the site you have created before. This is the site your provider configuration belongs to. |
| Slug | Define a slug for your Open edX instance or leave as default. |
| Private Key | Generate and add a private key. Read the label for this field to learn how to do it. |
| Public Key | Generate and add a public key. Read the label for this field to learn how to do it. |
| Entity ID | This value will be used as an identifier when adding your integration to Rublon Access Gateway. Set to e.g. the Open edX domain. |
18. Leave the remaining fields unchanged. Click SAVE to add the new SAML configuration. The window will close.
19. Click SAVE to save your Provider Configuration.
20. Go to Provider Configuration (SAML IdPs). If you see a green check mark in the METADATA READY column, then the Rublon Access Gateway metadata has been downloaded correctly.
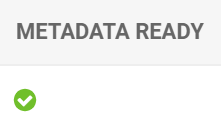
You may have to wait a minute or two for the changes to take effect. If you waited and refreshed the page but the metadata is not ready, you have to add this data manually.
Add SAML Provider Data manually
Perform the steps in this section only if Rublon Access Gateway metadata has not been downloaded correctly, otherwise skip this section and go to the Rublon Access Gateway section.
1. Go to Home → Third-party authentication → SAML Provider Data and click Add to add the provider data.
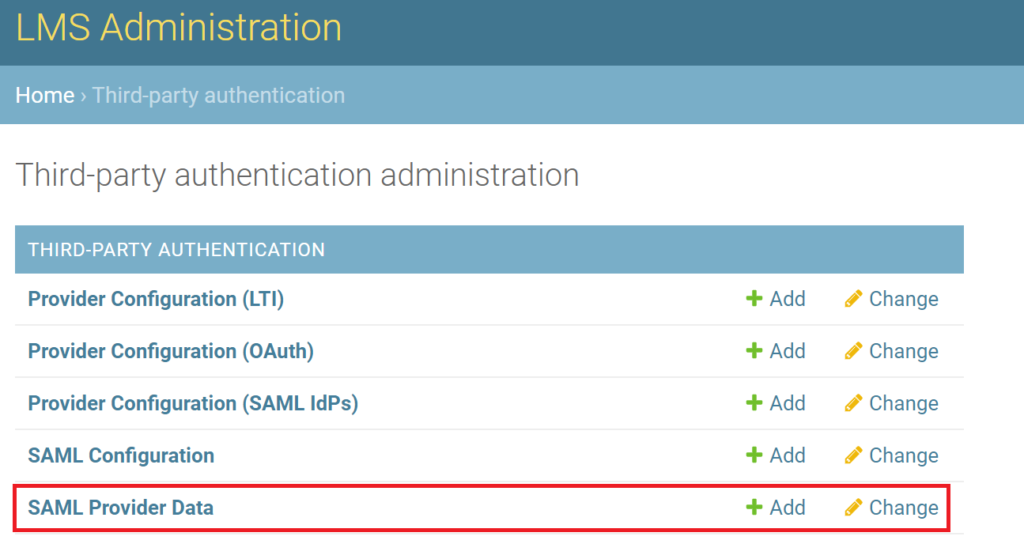
2. Fill in the form. Refer to the following image and table.
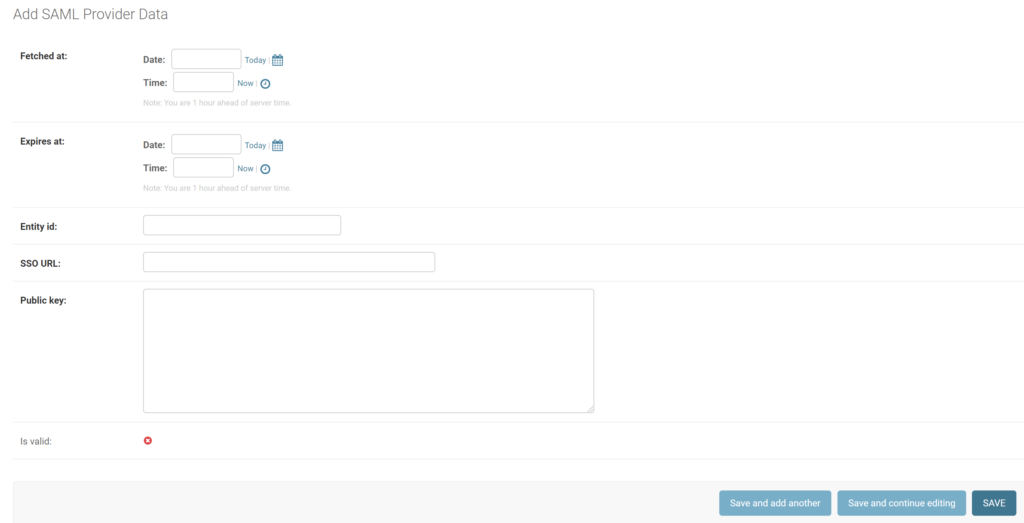
| Fetched at | Set when the provider data is fetched. We recommend you to click Today in Date and Now in Time to set the current datetime. |
| Expires at | Set when the provider data will expire. |
| Entity id | Enter the value of Entity ID from Rublon Access Gateway (Applications → Information for configuring applications with Rublon Access Gateway). |
| SSO URL | Enter the value of SSO URL from Rublon Access Gateway (Applications → Information for configuring applications with Rublon Access Gateway). |
| Public key | The certificate you have downloaded from Rublon Access Gateway (Applications → Information for configuring applications with Rublon Access Gateway → DOWNLOAD CERTIFICATE). Open the downloaded certificate in a text editor. Copy the entire content and paste it into the text field. |
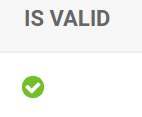
3. Save the SAML Provider Data. IS VALID should change to the green check mark.
Rublon Access Gateway
1. Log in to Rublon Access Gateway.
2. Go to Applications → Add application.
3. Fill in the form and click SAVE to add a new application. Refer to the following image and table.
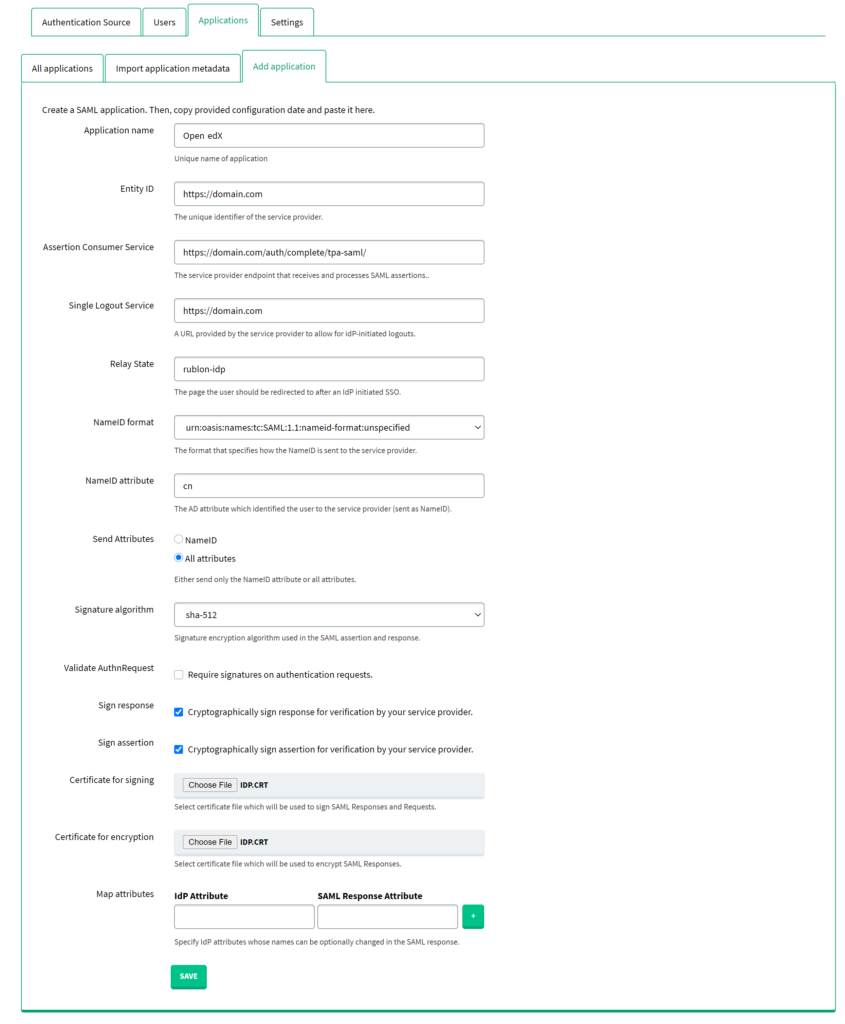
| Application name | Enter a name for the application, e.g. Open edX. The name will be displayed during 2FA. |
| Entity ID | Enter the Entity ID you set in step 17 of the Open edX section. |
| Assertion Consumer Service | Set to https://domain.com/auth/complete/tpa-saml/ where domain.com is your Open edX domain name. |
| Single Logout Service | Unfortunately, Open edX does not support SLO. The field is required, so enter, e.g. the main address of the Open edX domain. |
| Relay State | Enter the Rublon IdP slug you defined for your provider in Step 6 of the Open edX section. If you’re closely following this documentation, it is going to be rublon-idp. |
| NameID format | Set to urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified. |
| NameID attribute | Set to cn if you use OpenLDAP. Set to sAMAccountName if you use Active Directory |
| Send Attributes | Select All attributes. |
| Signature algorithm | Select sha512. |
| Validate AuthnRequest | Uncheck. |
| Sign response | Check. |
| Sign assertion | Check. |
| Certificate for signing | Select the certificate you have downloaded from Applications → Information for configuring applications with Rublon Access Gateway → DOWNLOAD CERTIFICATE. |
| Certificate for encryption | Select the certificate you have downloaded from Applications → Information for configuring applications with Rublon Access Gateway → DOWNLOAD CERTIFICATE. |
4. Your configuration is complete. You should now test your setup by logging in to Open edX.
Note
Remember that in order to use the newly-created provider, a user has to link the Rublon account in the configuration of their account.
If they do not link the Rublon account, they are going to see the following warning:
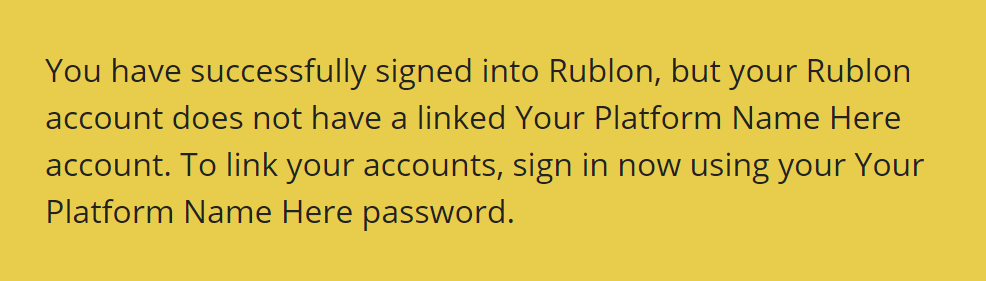
PLATFORM_NAME is the platform name defined during the Open edX installation.
To link a Rublon account, a user has to:
1. Expand the list next to the username and select the Account tab.
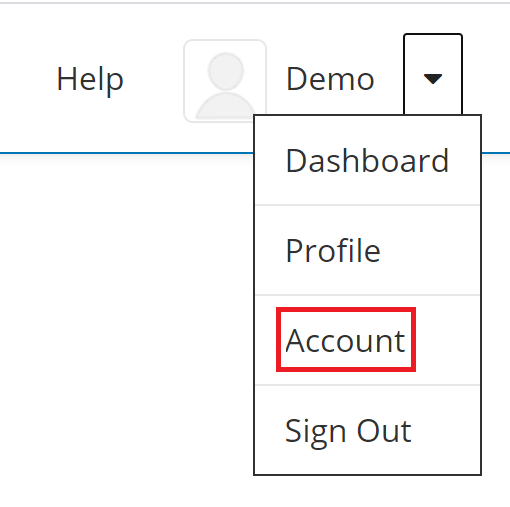
2. Select Linked Accounts and navigate to the Linked Accounts section.
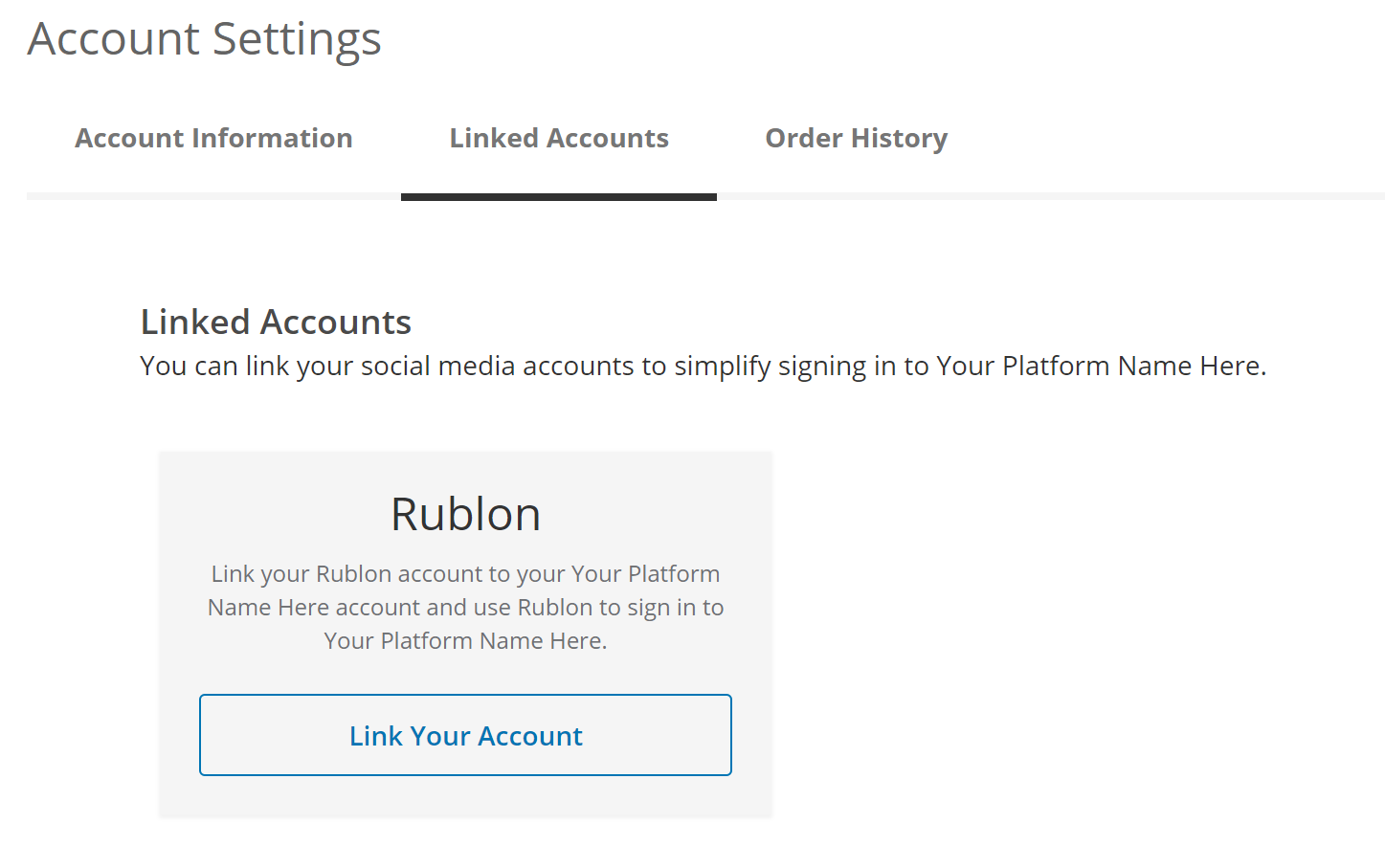
3. Click Link Your Account. From now on, this user will be able to log in using the Rublon provider.
Testing of MFA for Open edX
1. Go to the login page of Open edX.
2. You should see an additional login button. The name of this button depends on the application name you set in Step 5 of the Open edX section. In our case it is Rublon.
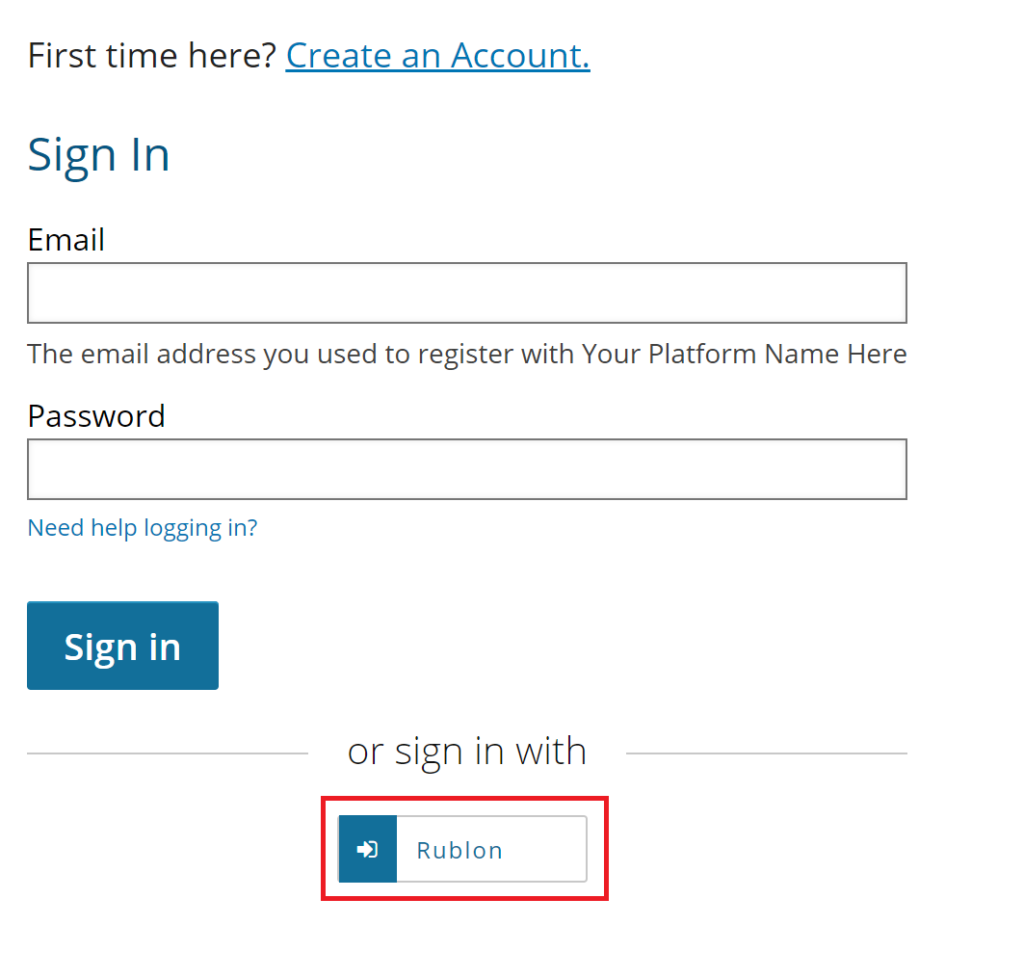
3. Click the button to initiate Rublon 2FA. You will be redirected to Rublon Access Gateway login page.
4. Provide your username and password. Click SIGN IN. A window should appear with a selection of various 2FA options from Rublon. Let’s choose Mobile Push.
5. You will be sent a push notification. Tap APPROVE.

6. You will be successfully logged in to OpenCart.
Troubleshooting of MFA for Open edX
If you encounter any issues with your Rublon integration, please contact Rublon Support.