Last updated on December 16, 2025
Overview of the Rublon MFA for OWA and ECP connector
- Microsoft Exchange Outlook Web App (OWA)
- Exchange Control Panel (ECP) [also called Exchange Admin Center (EAC)]
When OWA MFA is enabled, the user must enter the correct login and password and select an available Authentication Method from the Rublon Prompt. After confirming their identity with the second authentication method, the user gains access to Outlook on the web. If the user fails to complete any authentication factors, Rublon denies access to Outlook Web Access.
The Rublon MFA for OWA connector identifies users by their usernames.
The MFA for Outlook Web App connector determines the username regardless of how the user logs in to Outlook. So, the connector always tries to send the appropriate username to the Rublon API based on information from Active Directory. For example, if the SendUPN parameter is enabled and the user logs in by entering domain\sAMAccountName, the connector still tries to find the UPN and, if successful, sends the UPN to Rublon as the username.
Refer to the description of the SendUPN parameter in the Configuration section of this documentation to learn more.
Supported Authentication Methods
Demo Video
Before You Start
Note
Required Components
Pre-Installation Steps
5. Set Type to Outlook Web App.
6. Click Save to create a new application.
7. Copy and save the values of the System Token and Secret Key. You are going to need them later.
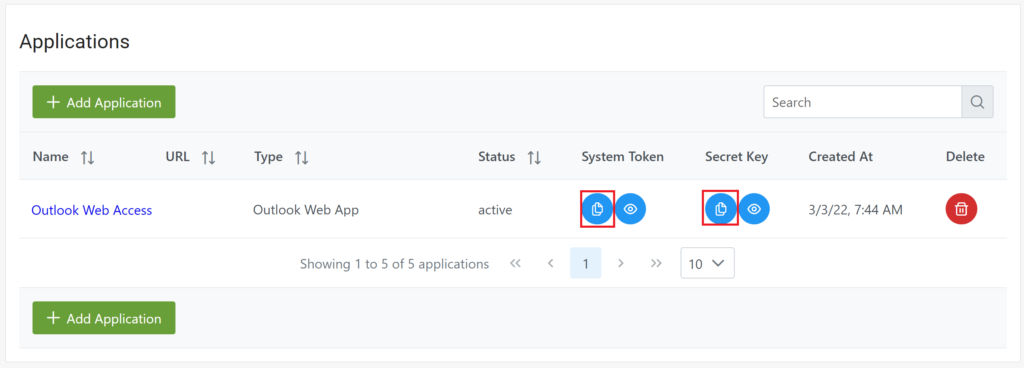
8. Download Rublon MFA for OWA by clicking the following link:
Download the Rublon MFA for Outlook Web Access installer
Installation of Rublon MFA for Outlook Web App (OWA) and Exchange Control Panel (ECP)
1. Run the installer with administrator rights.
2. On the first page of the installer, read about the product you are about to install.
- If this is the first time you are installing the connector, click Next.
If this is not the first time you are installing the connector on this endpoint, you will be able to either update the current installation or do a clean installation.
- Update current installation: If you choose to update the current installation, you will not be able to change any old options in the installer. However, if a new option has been introduced in this version of the installer, you will be able to change its value before the installation begins. The Update current installation option is recommended for those who want to update the connector to a newer version but want to keep all current settings.
- Clean installation: If you choose to do a clean installation, continue with the steps in this section.
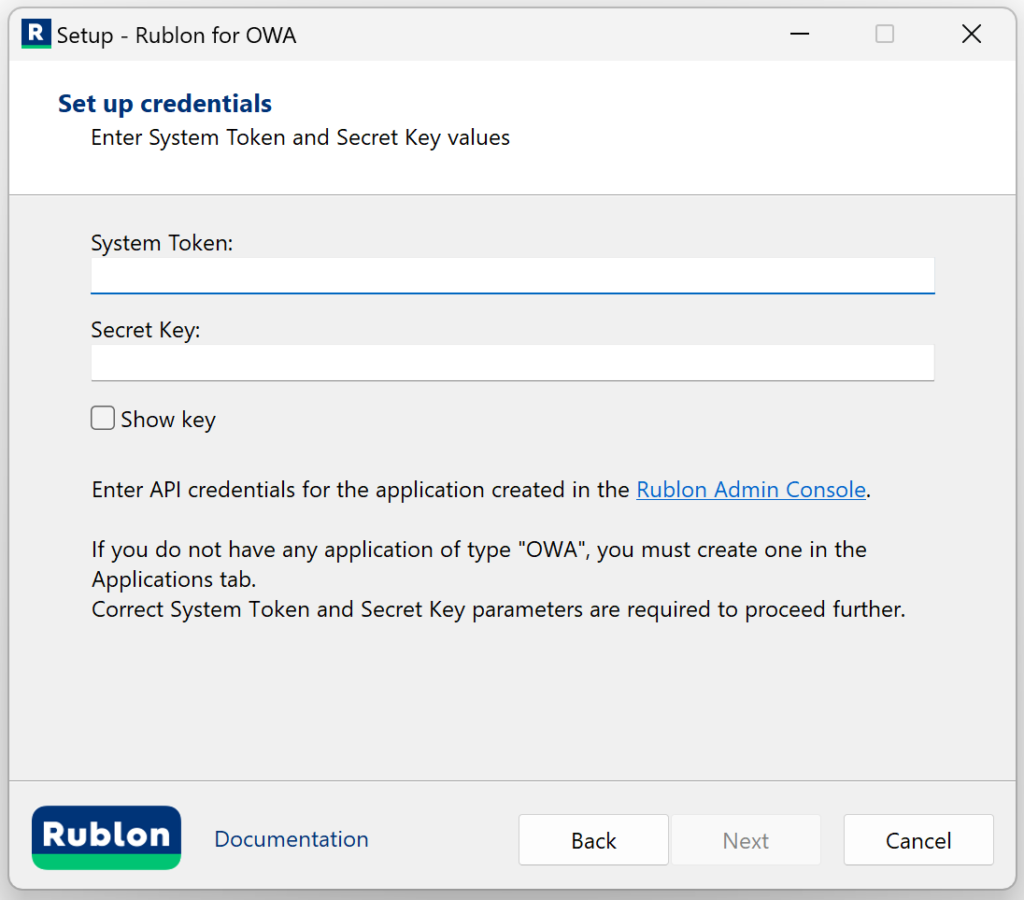
| Parameter | Description |
| System Token | System Token of your application in the Rublon Admin Console. Paste the value you noted down before. |
| Secret Key | Secret Key of your application in the Rublon Admin Console. Paste the value you noted down before. |
4. Check the configuration options you want and click Next. Refer to the following image and table.
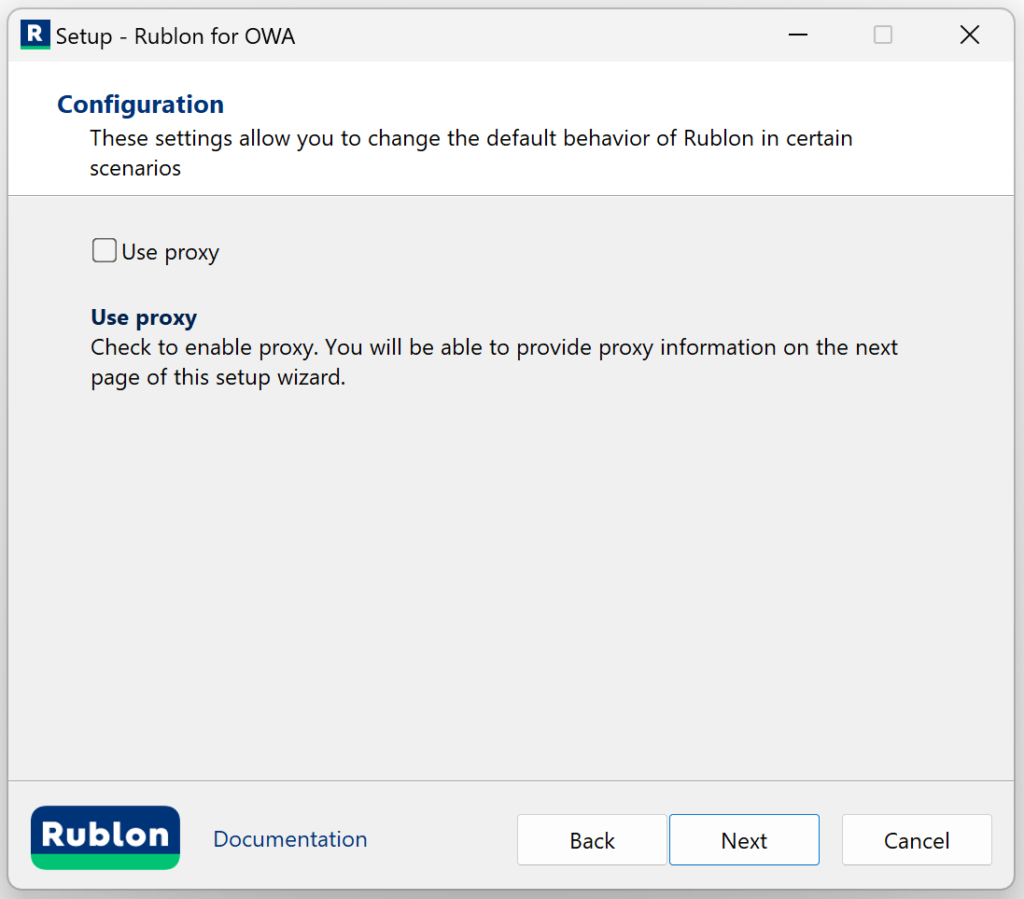
| Option | Description |
| Use proxy | Check this option to enable proxy. When checked, the next page after clicking Next will ask you for more details about the proxy. When unchecked, the page that asks for proxy details will not appear. |
5. If you checked Use proxy on the previous page, you will see an additional page asking you to enter proxy details. After filling in the details, click Next. Refer to the following image and table.
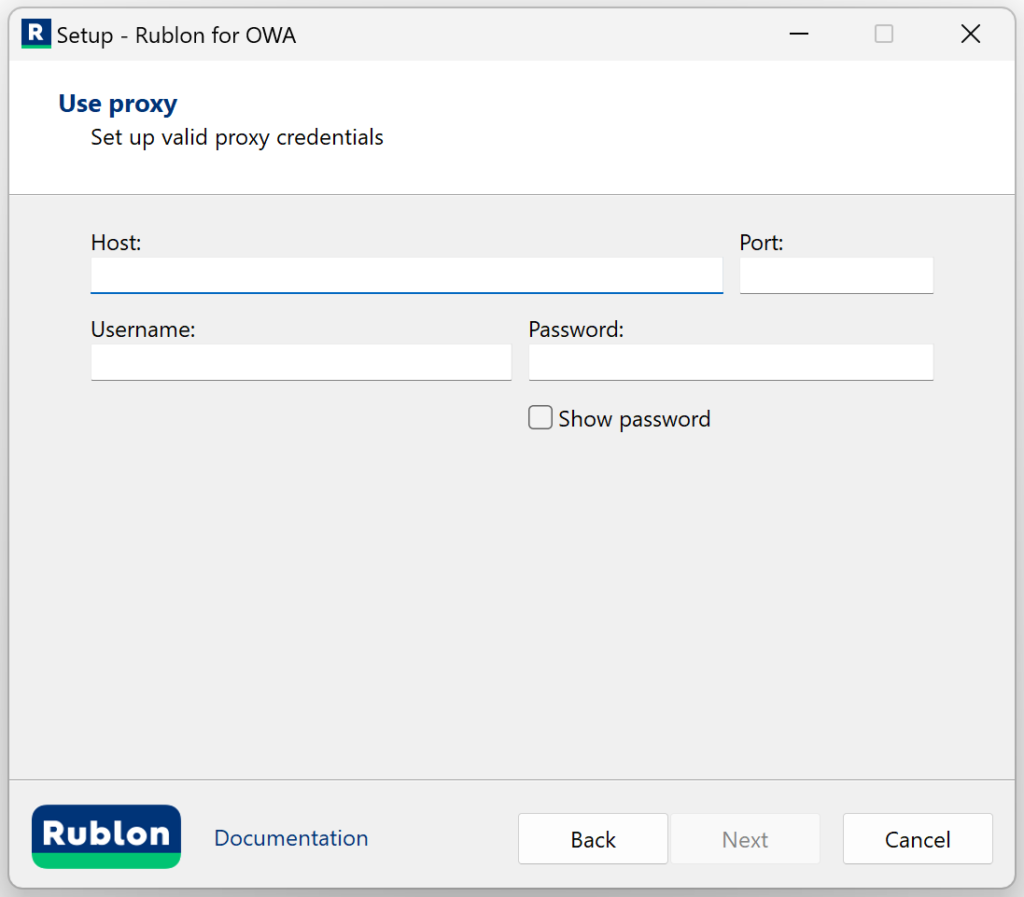
| Option | Description |
| Proxy Host | The address of the proxy server. |
| Proxy Port | The port on which the proxy server is operating. |
| Proxy Username | The username of the HTTP proxy server user. Optional. Fill in if verification by username is required. |
| Proxy Password | The password of the HTTP proxy server user. Optional. Fill in if required for verification. |
6. Check the bypass options you want and click Next. Refer to the following image and table.
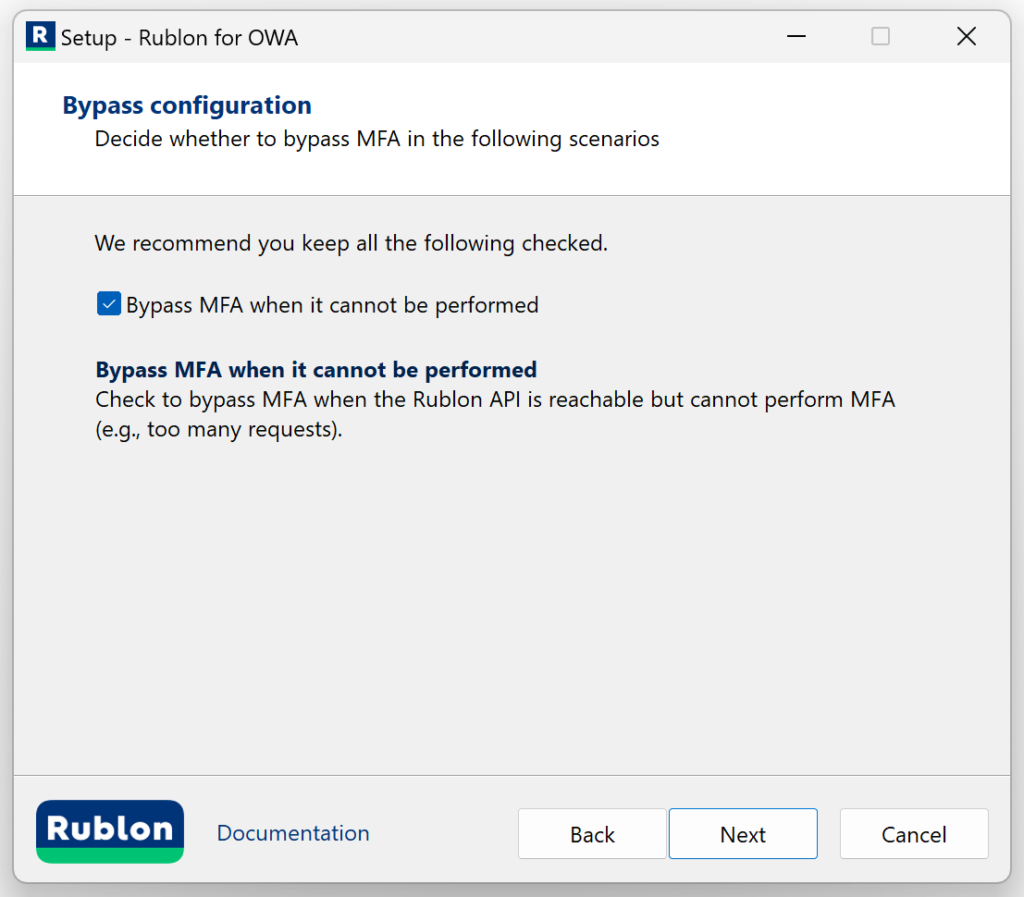
| Option | Description |
| Bypass MFA when it cannot be performed | Check to bypass MFA when the Rublon API is reachable but cannot perform MFA (e..g, too many requests). |
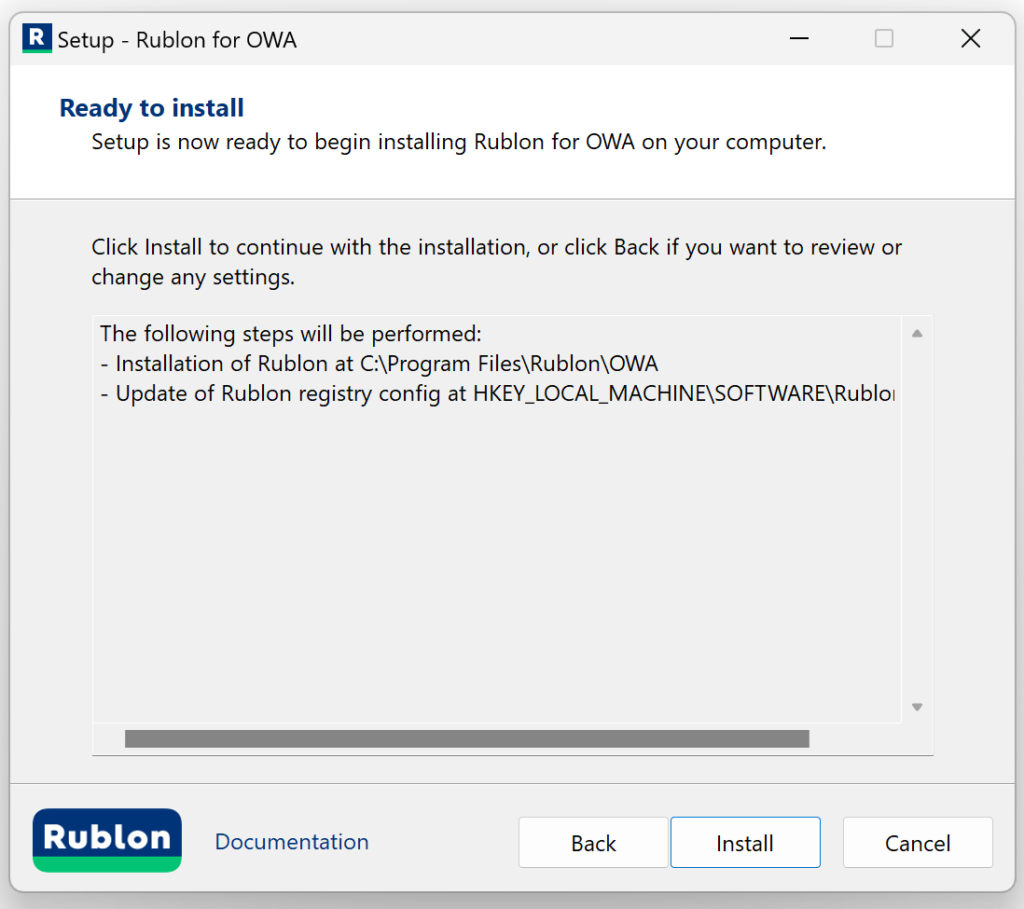
7. Rublon MFA for OWA is ready to install.
Rublon MFA for OWA performs the following steps during installation:
- Adds configuration settings to Windows Registry.
- Installs the application on the system in a defined location. It is not possible to change this path.
- Starts the installer of the required additional packages: Microsoft Visual C++ 2015-2019 Redistributable (x64). Note that Rublon for OWA requires the Microsoft Visual C ++ 2015-2019 Redistributable (x64) package to work. The OWA installer will install this package automatically if it does not exist in the system. If the package exists in the system, the installer will omit this step and will not print info about it on the Ready to install page.
Note
Configuration of MFA for OWA and ECP
Logging
Change the log file path
- Open the log4Net.config file and look for the following line:
<file value=”${SystemDrive}\\Rublon\\OWA\\RublonOWA.log” /> - Replace
${SystemDrive}\\Rublon\\OWA\\RublonOWA.logwith a new path. - From now on, any Rublon authentication process information will be logged to a new file.
Note
Change logging level
- Open the log4Net.config file and look for the following entry:
<root>
<level value="DEBUG" />
- Change the default DEBUG value to one of the following values:
- ALL – logs everything
- DEBUG – logs detailed information about the logging process
- INFO – logs info, warnings, and errors
- WARN – logs warnings and errors
- ERROR – logs errors only
- OFF – turns off logging
High Availability (HA) OWA MFA Installation & Configuration
The Rublon MFA for Outlook Web Access (OWA) connector uses the so-called Rublon session files that allow Rublon to perform MFA. So, if you have a High Availability architecture, e.g., a Load Balancer and several OWA nodes, it is necessary to set the same SecretSessionKey for all OWA nodes.
Refer to the following instructions:
1. Install Rublon MFA for OWA on one OWA node and copy the value of secretStorageKey from Windows Registry.
2. Install the connector on other OWA nodes and set the copied secretStorageKey for all of them.
You can define the secretStorageKey in the installation command by appending the following string:
-secretStorageKey <value>
Testing MFA for Outlook Web App (OWA)
1. Open the Outlook Web App login page.
2. Provide your Domain\user name and Password, and click sign in.


Note
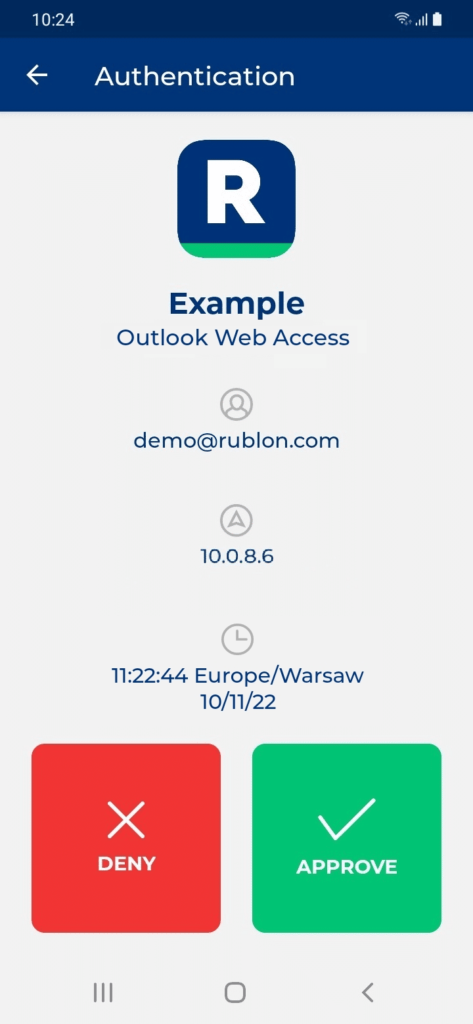
Updating MFA for OWA and ECP
Rublon Prompt Doesn’t Show Up After Update
Updating MFA for OWA by running the installation file without administrator rights might cause the Rublon Prompt to not appear during logins. If this is the case, follow the steps below:
1. Open the IIS Server Manager.
2. Select Sites → owa.
3. Right-click and select Explore.
4. Open the web.config file.
5. Paste this line just above the closing </modules> tag:
<add name="RublonOWAModule" type="Rublon.OWA.OWAModule, RublonOWAModule, Version=<VERSION>, Culture=neutral, PublicKeyToken=be7e75eeb046f1eb" preCondition="" />
where <VERSION> is the version of the connector in the following form: X.X.X.X. For example, if your OWA connector is version 1.1.2, enter Version=1.1.2.0.
6. Save the file. You should now see the Rublon Prompt on your next login to OWA.
If you have the same issue with the Exchange Control Panel (ECP):
1. Open the IIS Server Manager.
2. Select Sites → ecp.
3. Right-click and select Explore.
4. Open the web.config file.
5. Paste this line just above the closing </modules> tag:
<add name="RublonOWAModule" type="Rublon.OWA.ECPModule, RublonOWAModule, Version=<VERSION>, Culture=neutral, PublicKeyToken=be7e75eeb046f1eb" preCondition="" />
where <VERSION> is the version of the connector in the following form: X.X.X.X. For example, if your OWA connector is version 1.1.2, enter Version=1.1.2.0.
6. Save the file. You should now see the Rublon Prompt on your next login to ECP.
Uninstalling MFA for OWA and ECP
INFO
