Last updated on December 8, 2025
Overview
This document explains how to enable Rublon Multi-Factor Authentication (MFA) for users who log in to ParkMyCloud. Rublon integrates with ParkMyCloud using the Rublon Access Gateway. This document describes all required steps.
Supported Authentication Methods
Before you start
You need to install and configure Rublon Access Gateway before configuring ParkMyCloud to work with it. Read the Rublon Access Gateway documentation and follow the steps in the Installation and Configuration sections. Then, follow the Configuration section in this document.
Known Limitations
ParkMyCloud does not provide a link to Single Logout. As a result, the SAML session does not end after you log out of ParkMyCloud. For security reasons, we recommend you always log out of the Rublon SSO Portal after you finish work so that an unauthorized person cannot use the existing SAML session on your browser to log in to ParkMyCloud.
Configuration
Follow these steps to enable Rublon 2FA on ParkMyCloud.
ParkMyCloud
1. Log in to the ParkMyCloud console.
2. Go to Settings → Single Sign-On.
3. Click the SINGLE SIGN-ON WITH SAML toggle slider.
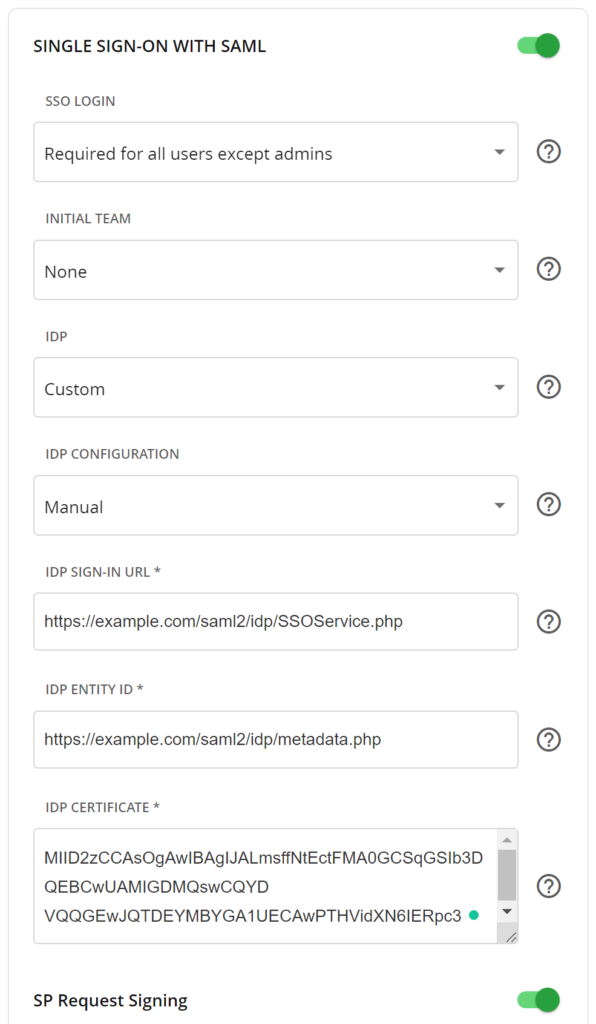
| SSO LOGIN | Required for all users except admins Choosing this option is a safeguard, which ensures that Super Admins can still log in locally if you misconfigure the integration. After you have finished and tested the integration, you can get back to this field and change its value to Allowed for all users to enable Rublon MFA for Super Admins. |
| INITIAL TEAM | None Or the team new users added via SSO will be automatically assigned to after successful authentication. |
| IDP | Custom |
| IDP CONFIGURATION | Manual |
| IDP SIGN-IN URL | Enter the value of SSO URL from Rublon Access Gateway (Applications → Information for configuring applications with Rublon Access Gateway). |
| IDP ENTITY ID | Enter the value of Entity ID from Rublon Access Gateway (Applications → Information for configuring applications with Rublon Access Gateway). |
| IDP CERTIFICATE | Enter the text value of the certificate you have downloaded from Applications → Information for configuring applications with Rublon Access Gateway → DOWNLOAD CERTIFICATE. Open the downloaded certificate in a text editor. Copy the entire contents and paste it into the text field. IMPORTANT: Remove the opening and closing tags (—–BEGIN CERTIFICATE—–, —–END CERTIFICATE—–) |
| SP Request Signing | Enabled |
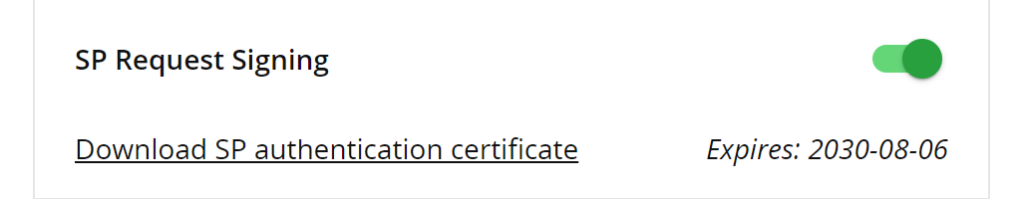
5. In the SP Request Signing section, click Download SP authentication certificate to download the certificate from ParkMyCloud. You are going to need this certificate later when configuring ParkMyCloud in the Rublon Access Gateway.
6. OPTIONAL: You can set a unique name for your URLs, but you do not have to.
If you do not set the unique name, the URLs will have a string of random characters in the place of the name to ensure they are unique.
Setting the unique name makes it clear the URLs refer to your particular configuration or organization.
If you want a unique name in the URLs, click the CHANGE button and then set the unique name to your liking. Note that this name must be unique. We set it to rublon. You can set it to the name of your company.
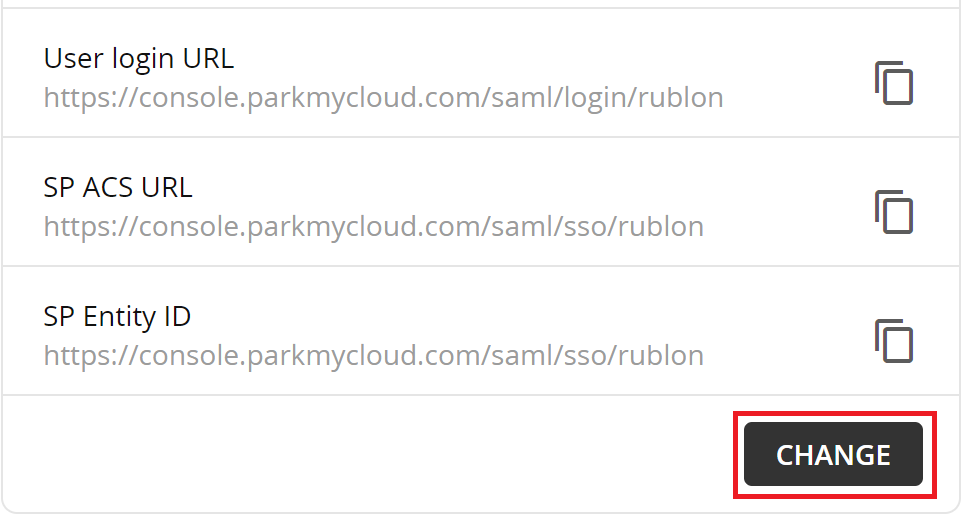
Changing the unique name affects User login URL, SP ACS URL, and SP Entity ID links.
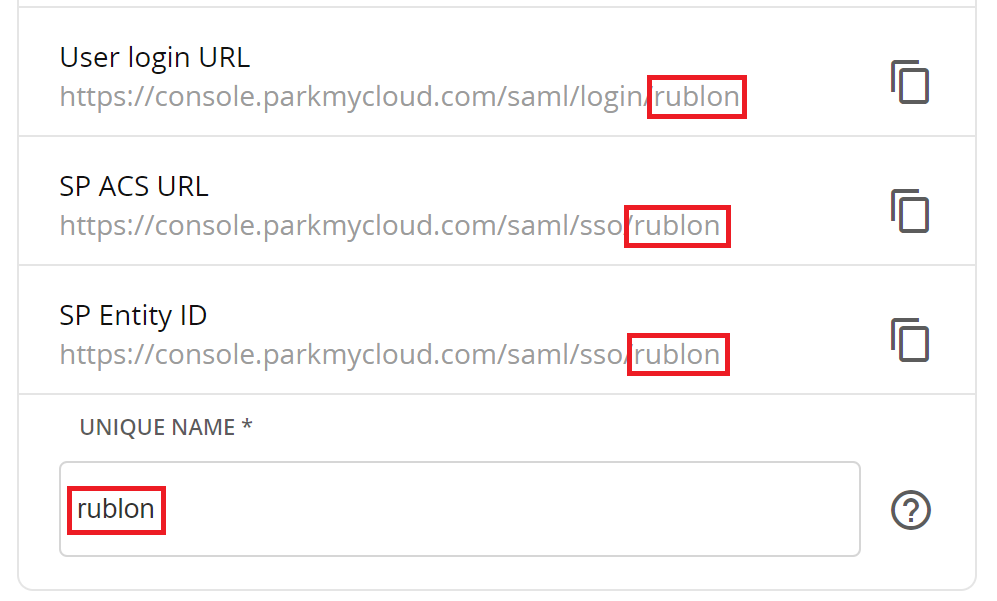
7. Copy and save User login URL, SP ACS URL, and SP Entity ID. You are going to need these values later when configuring ParkMyCloud in the Rublon Access Gateway.
8. Click Save in the upper-right corner to save your configuration.

Rublon Access Gateway
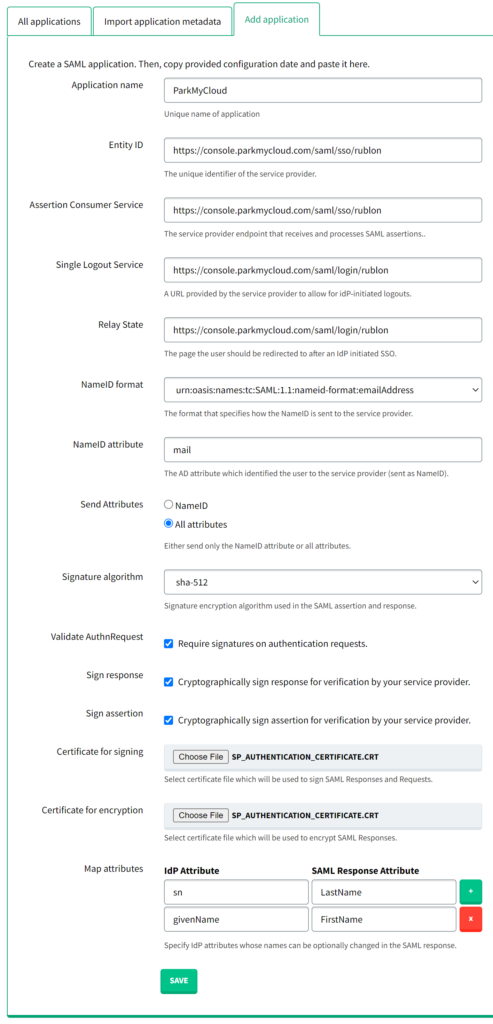
1. In Rublon Access Gateway, go to Applications → Add application.
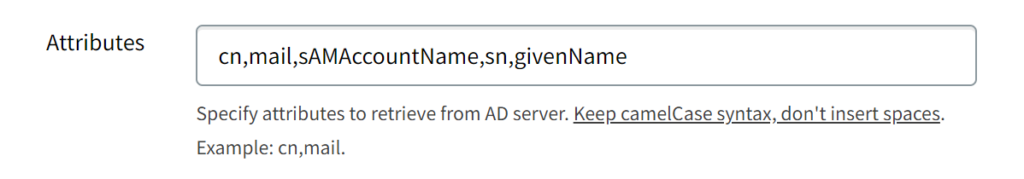
Test Your ParkMyCloud Integration

Note
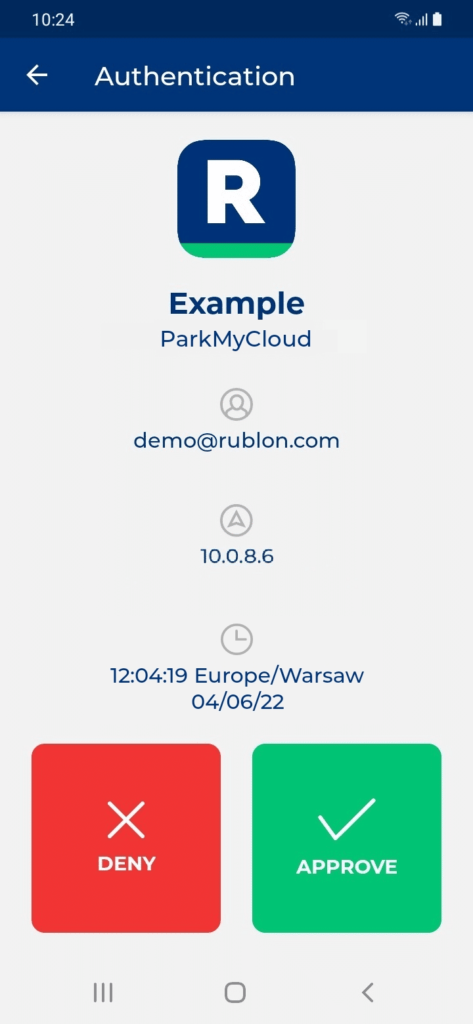
Test Your ParkMyCloud Login via the Rublon SSO Portal

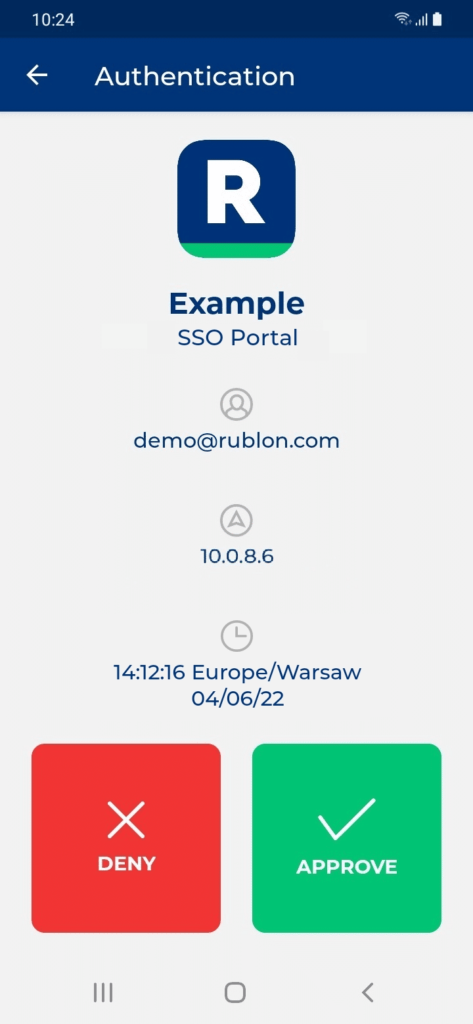

9. You will be successfully logged in to ParkMyCloud.
Troubleshooting
If you encounter any issues with your Rublon integration, please contact Rublon Support.