Last updated on August 13, 2025
Overview of MFA for Microsoft RRAS VPN
Supported Authentication Methods
Before you start
Note
Configuration of MFA for Microsoft RRAS VPN
Rublon Authentication Proxy
Use to the following config.yaml snippet as a template for your configuration:
log:
debug: false
rublon:
api_server: https://core.rublon.net
system_token: system_token_obtained_from_rublon_admin_console
secret_key: secret_key_obtained_from_rublon_admin_console
proxy_servers:
- name: RADIUS-Proxy
type: RADIUS
ip: 192.168.1.13
port: 1812
radius_secret: testing1234
mode: standard
auth_source: LDAP_AUTH_SOURCE_1
auth_method: push,email
auth_sources:
- name: LDAP_AUTH_SOURCE_1
type: LDAP
ip: private_ip_of_the_idp
port: 389
transport_type: plain
search_dn: dc=domain,dc=local
access_user_dn: cn=Administrator,cn=users,dc=domain,dc=local
access_user_password: v3ryH@rdpa$$w0rd
Microsoft RRAS
1. Open Routing and Remote Access on your Windows Server machine.
2. Right-click on your server and select Properties.
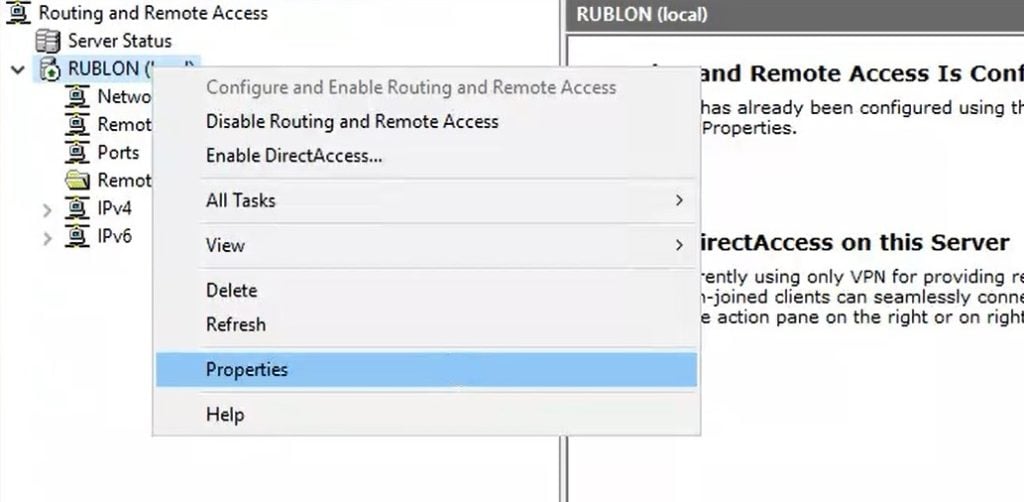
3. Go to the Security tab and locate Authentication provider. Select RADIUS Authentication from the drop-down list.

4. Click Configure….
5. A new window will open. You have to add a new RADIUS server. Click Add….
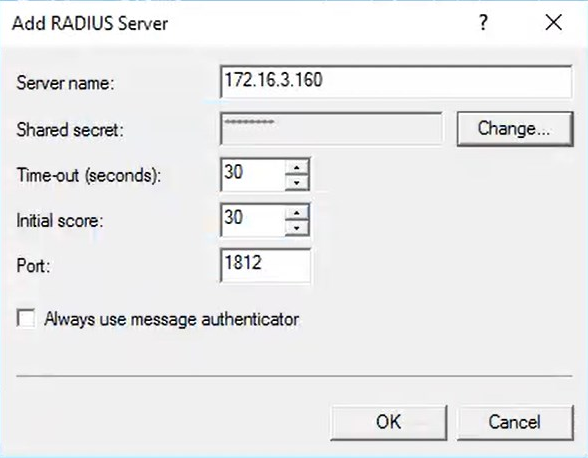
6. Another window will open. Fill in the settings and click OK. Note that your settings should match the settings you have specified in the RADIUS section of Rublon Authentication Proxy’s config.yaml. Refer to the following image and table.
7. Click OK to close the list of RADIUS servers and get back to your server’s properties.
8. Click Authentication Methods….

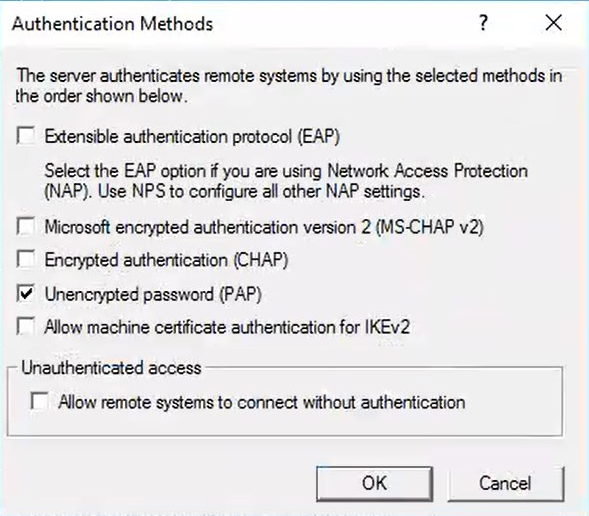
9. A new window will open. Check Unencrypted password (PAP) and uncheck every other checkbox.
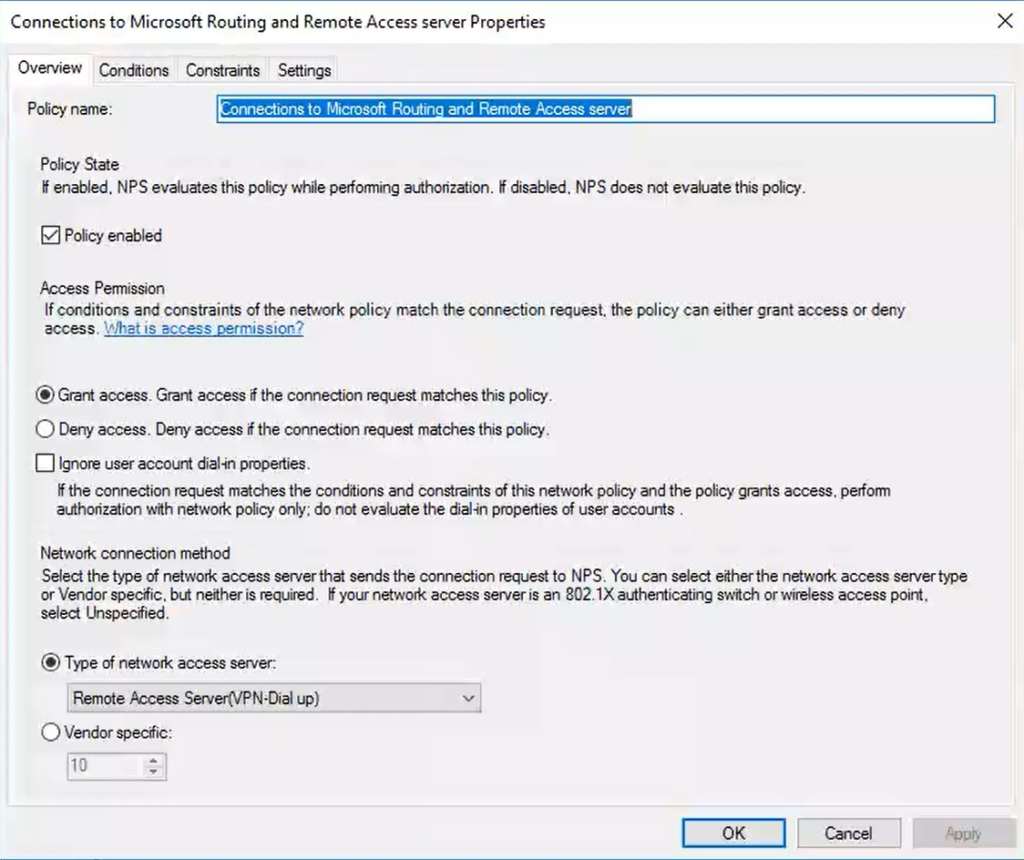
15. A new window will open. Go to the Overview tab. Ensure that:
- Policy enabled is checked.
- Grant access is selected in the Access Permission section.
- Remote Access Server (VPN-Dial up) is selected in Type of network access server.

Windows VPN Client
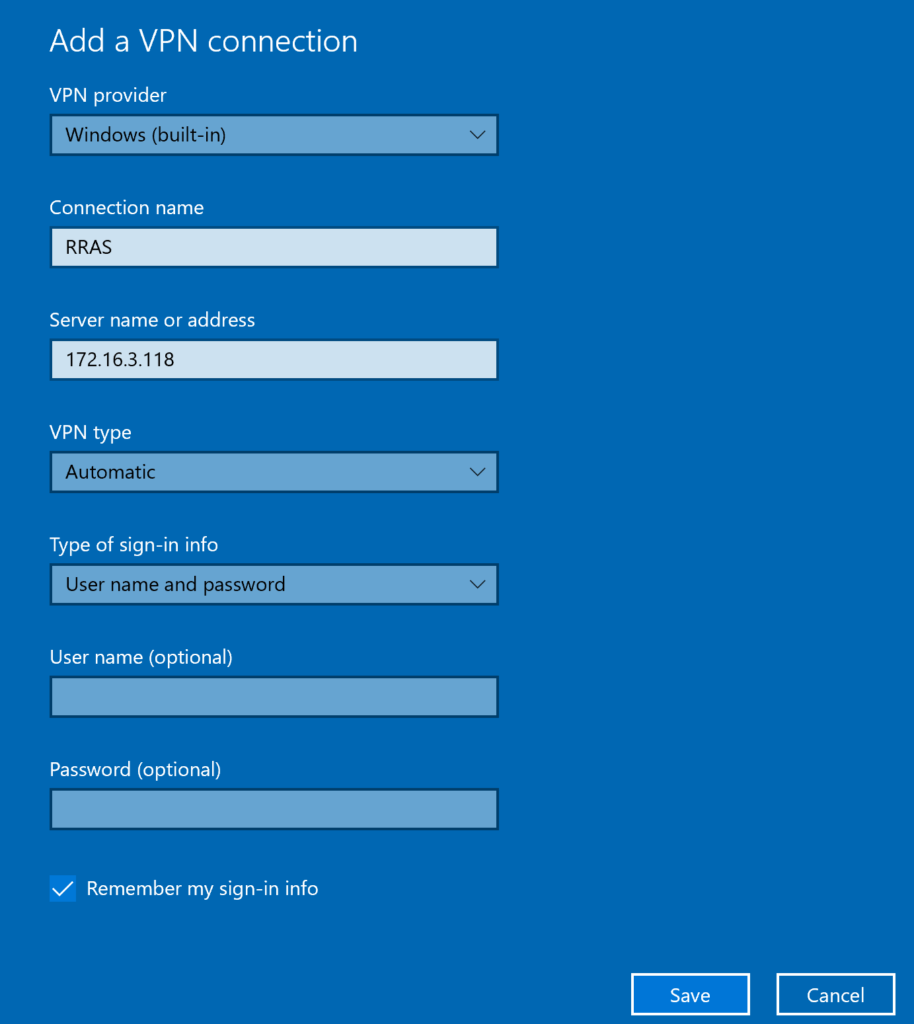
2. Click Save to save your new VPN connection profile.
3. Now you have to edit the VPN connection and specify the authentication protocol.
Go to Control Panel → Network and Sharing Center and select Change adapter settings from the menu on the left.
4. Right-click the newly created VPN profile and select Properties.
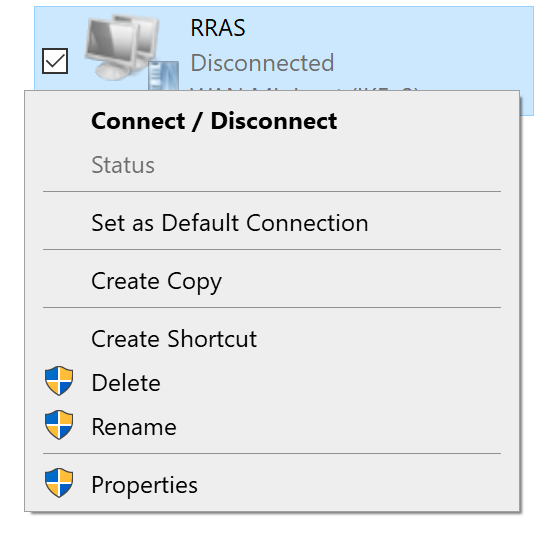
5. A new window with properties for this connection will open.
6. Go to the Security tab and change Authentication to Allow these protocols. Then, check Unencrypted password (PAP).

Testing MFA for Microsoft RRAS VPN
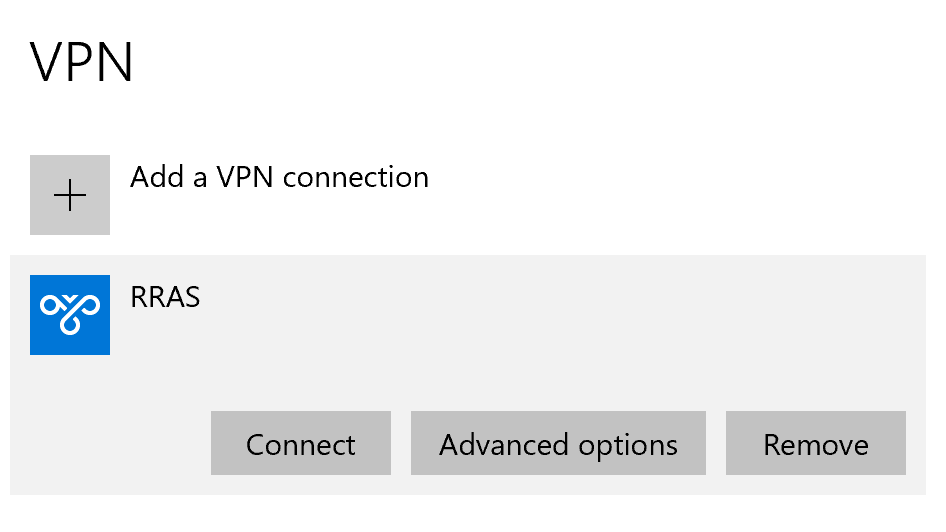
2. If you have not set user name and password while adding your VPN connection, a window will appear for you to provide your credentials. Provide your user name and password and click OK.
3. You will be sent an automatic push notification on your phone.
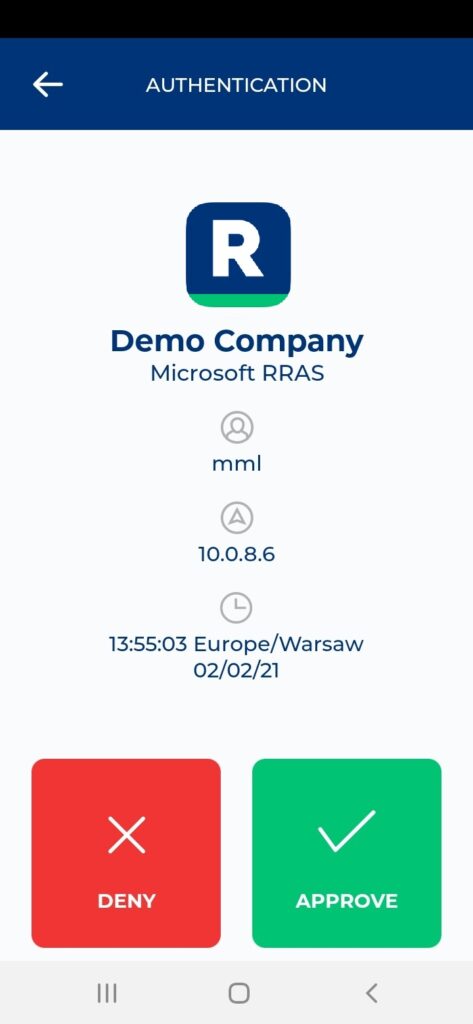
4. Tap APPROVE.
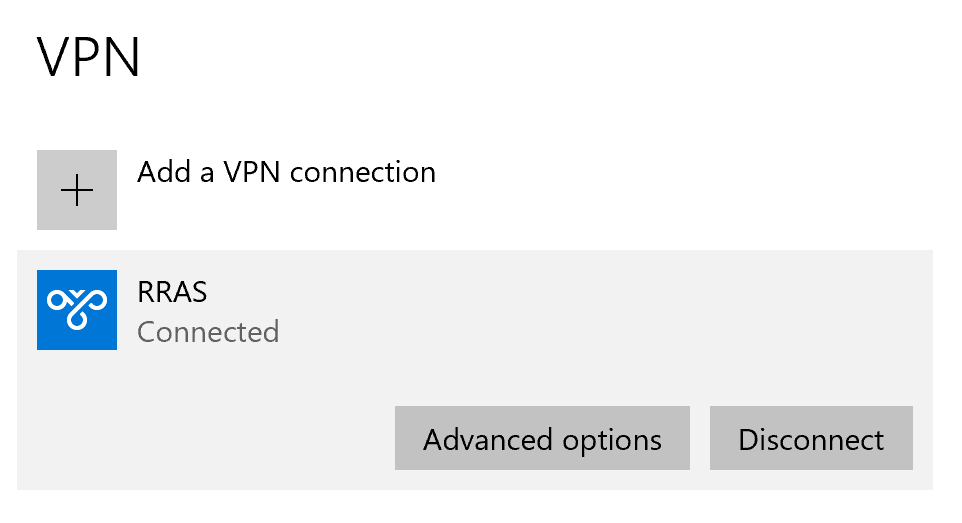
5. You will be successfully connected to Microsoft RRAS.