Last updated on September 15, 2025
Overview
Rublon Admin Console is a management tool for your Rublon Multi-Factor Authentication system, which allows you to configure and manage your company, applications, users, and many more.
The following documentation is going to walk you through the registration and configuration process, pointing out essential features and helpful information regarding Rublon Admin Console.
Rublon Account Registration
Rublon Account Registration creates a new administrator and a new company. The registered administrator becomes the owner of the new company. As the owner, you can manually add new users and administrators to your company. In addition to that, a new user is automatically added to your company when logging in to any of the integrated applications.
You cannot register a new user with an email address already registered in an existing company if that user is an owner or admin in that existing company.
1. Install the Rublon Authenticator if you have not already.
2. Open the Rublon Admin Console.
3. Click Sign Up.
4. Fill in the form. Make sure to read and agree to the Terms of Service and Privacy Policy by checking the checkbox.
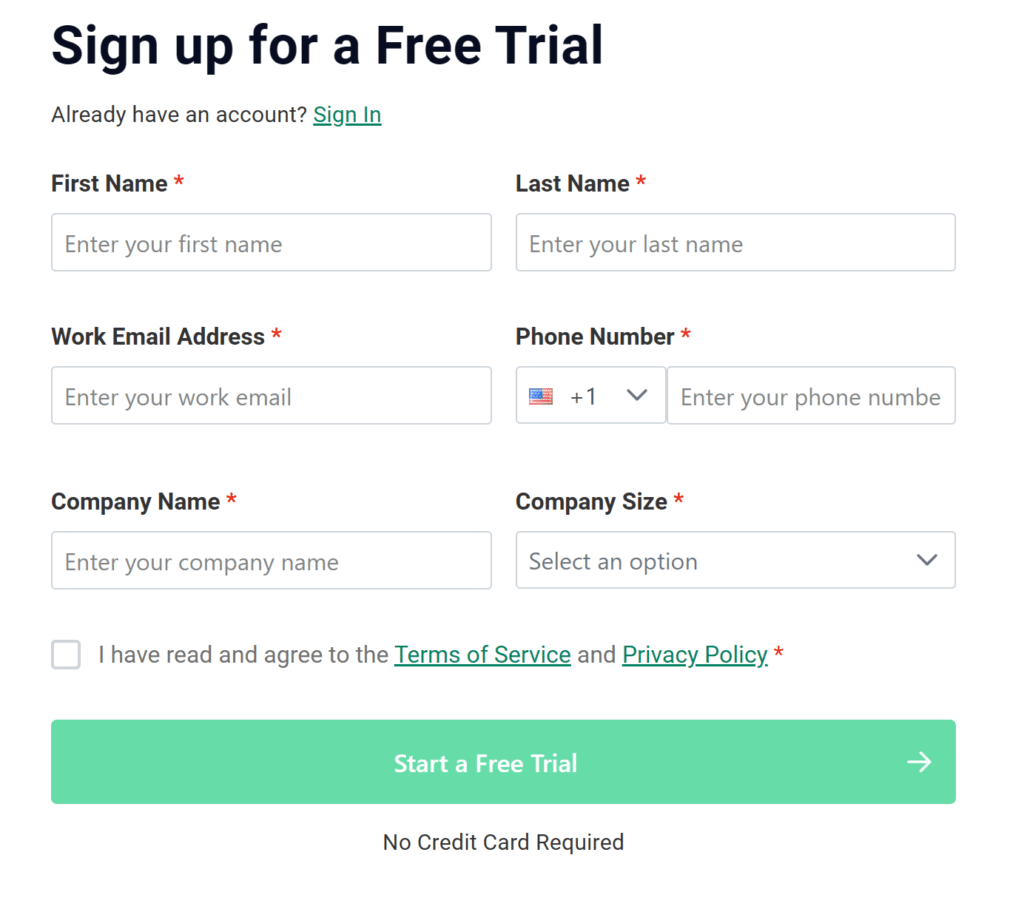
5. Click Start a Free Trial.
6. You will be sent an email with a verification code. Rewrite the code and click Next.
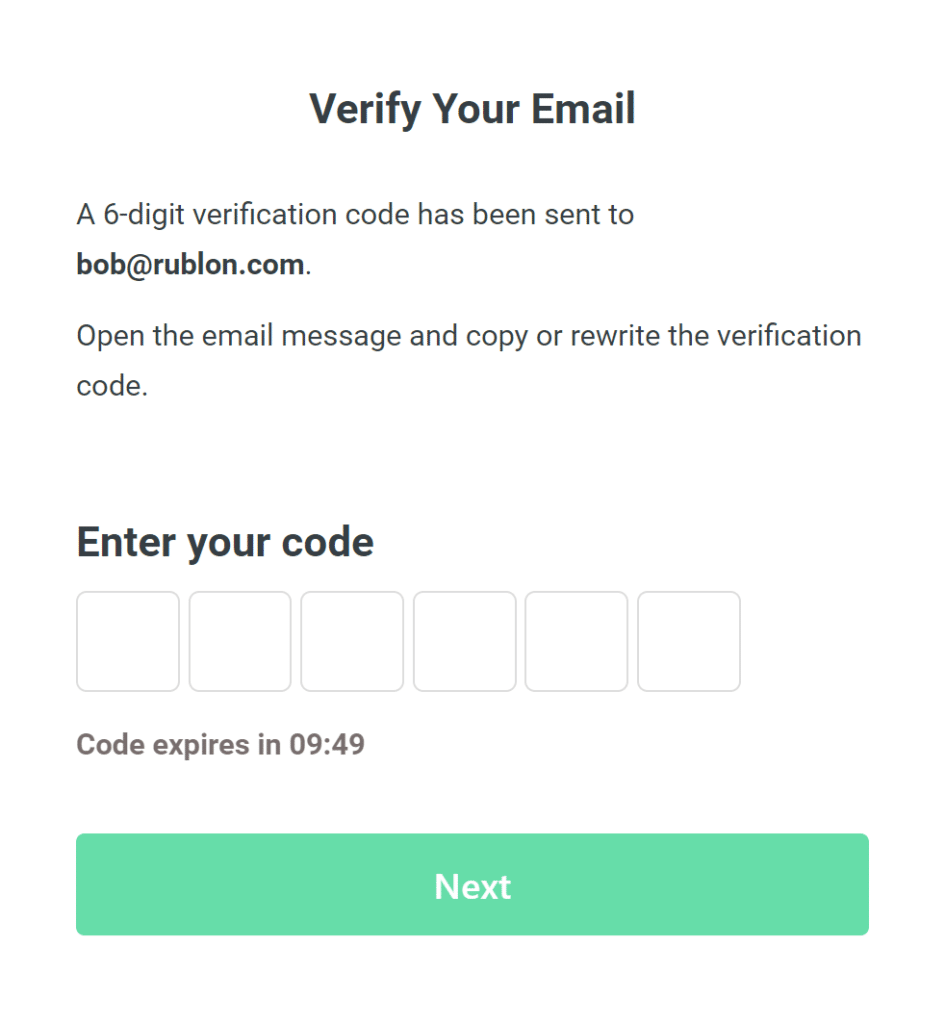
Note
The verification code expires after 10 minutes.
7. You will be asked to create a password. You will be using this password to sign in to the Rublon Admin Console. Specify your password and click Next.

8. Follow the instructions on the screen to activate Rublon Authenticator.

9. You will be asked to verify your identity using one of the available methods of authentication.

10. Once you verify your identity, you will be redirected to the Rublon Admin Console, which completes Rublon Account Registration.
Sign in to Rublon Admin Console
1. Go to the Rublon Admin Console.
2. Provide your email and password, and click Sign In.
3. A window will appear with a selection of various 2FA options from Rublon.

4. Select Mobile Push (the fourth option from the left).
5. You will receive a push notification on your phone. Tap APPROVE.

6. You will be redirected to the Rublon Admin Console.
Password Reset
In case you forgot your password, you can reset it.
1. Go to the Rublon Admin Console.
2. Click Forgot your password?.
3. Enter your email address and click Next.

4. Check your inbox. Copy or rewrite the verification code from the email. Click Next.

5. Set your new password to the Rublon Admin Console and click Next.

6. Confirm your identity by choosing one of the active methods of authentication.

7. You will be redirected to the Rublon Admin Console, which completes Password Reset.
Configuration
Several tabs can be found on the left-hand side of the Rublon Admin Console user interface. You can freely switch between the tabs by clicking them. Click the Billing tab to extend it and show its subtabs. All tabs of Rublon Admin Console correspond to substantial parts of Rublon system management, encompassing various features and means of configuration. Refer to the following list for a short summary of every tab.
- Dashboard – see the summary of your Rublon system management, including users and company stats, authentication history, and logs.
- Applications – manage your applications integrated with Rublon by adding, modifying, and deleting them. Assign Application Policies and Group Policies to applications.
- Users – manage, add, and edit your users. Extends further into:
- Directory Sync – Add and edit Directory Sync configurations to synchronize users and groups from external directories like Entra ID.
- Groups – add, edit, and remove groups.
- Policies – edit the Global Policy and introduce custom policies to your applications; manage remembered devices.
- Phones – manage, edit, remove phones.
- Remembered Devices – review remembered devices to see all devices that users have trusted to bypass multi-factor authentication in your organization.
- WebAuthn & U2F – manage your WebAuthn/U2F/YubiKey OTP security keys.
- Administrators – supervise, edit, and remove administrators. Extends further into:
- Administrative Units – add, edit, and remove administrative units.
- Admin Sign-in Settings – configure administrator sign-in and authentication settings for your organization.
- Reports – extends further into:
- Authentications – review the top authentication methods, applications, application types, denied applications, denied users, unfinished application authentications and unfinished user authentications within the last 30 days.
- Authentication Logs – browse authentication logs of applications integrated with Rublon.
- Audit Logs – browse audit logs of administrator activities within the Admin Console.
- Phone Logs – review phone logs of all events related to phone-based authentication methods in your organization.
- Settings – set, change settings for all applications added in the Applications tab, including company information.
- Billing – extends further into:
- Overview – see the subscription overview and payment history.
- Phone Credits – view and add phone credits.
- Invoice Details – set information to be included on all billing invoices on your account.

Refer to the respective subsections of the Configuration section of this document for more information about every tab.
Dashboard
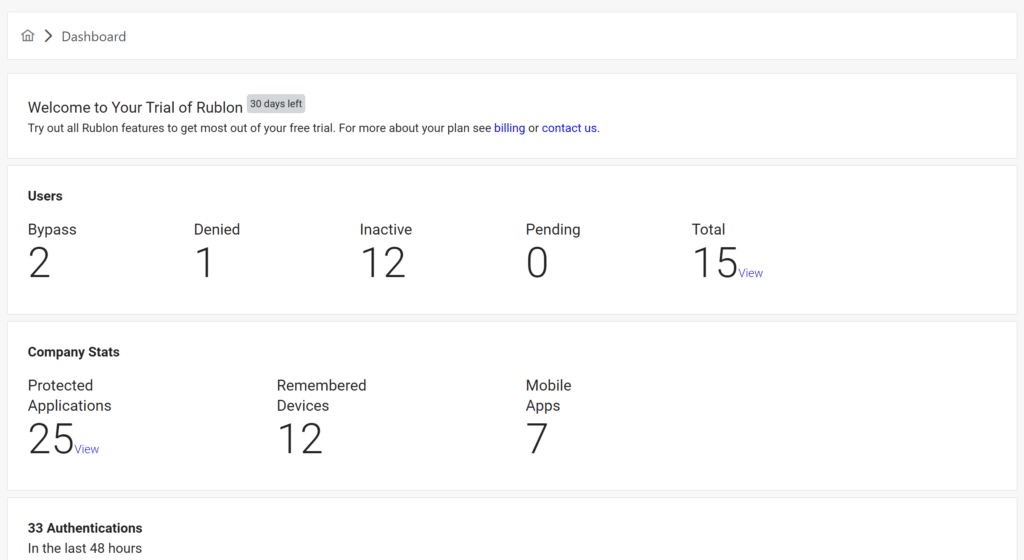
Dashboard is a summary of all activities happening in your Rublon system.
Dashboard comprises the following sections:
- Welcome Section, which shows information about your subscription plan and how many days of Trial you have left. Does not show up if you have a plan different from Trial.
- Users, which shows information about the number of bypassed, denied, inactive, pending, and total users.
- Company Stats, which shows the number of protected applications, trusted devices, and mobile apps.
- Authentication Diagram, which shows granted and denied authentication attempts in the last 48 hours.
- Authentication Logs, which shows detailed information about the last 10 authentication attempts. See the date and time, email address, application, access device, method, and the result of the last authentication attempts.
- Usage of authentication methods within last 30 days, which shows information about the popularity of each authentication method used at least once in the last 30 days.
Applications
Applications allows you to add and manage your applications integrated with Rublon.
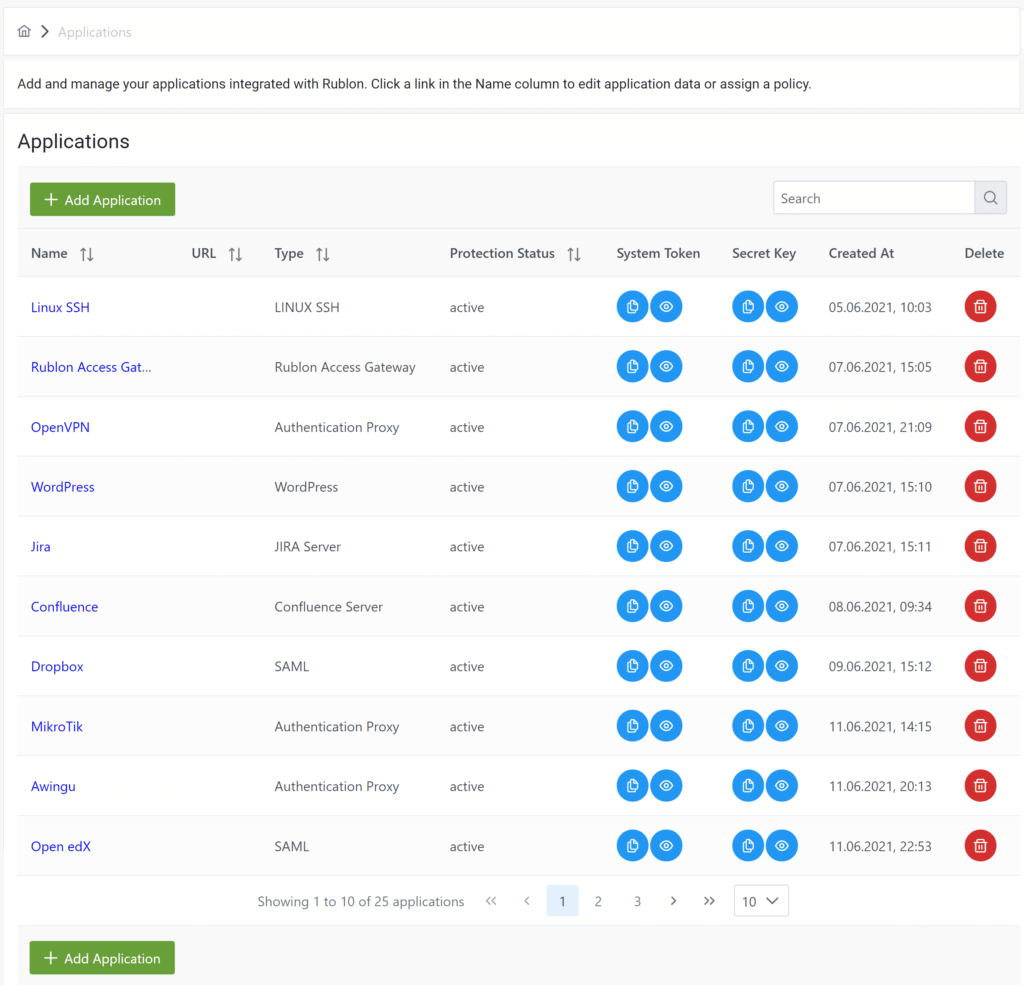
The Applications section depicts all protected applications in the form of a table.
Every application in the table contains the following information:
- Name – the name of your application; click the name to edit the application.
- URL – the URL of your application. Even though this information is optional, we recommend you add the URL whenever possible to keep the Applications table organized and easier to read.
- Type – the Type of your application selected from one of the available types supported by Rublon.
- Status – the current protection status of the application. If active, your application is protected by Rublon.
- System Token – a value often required when you are integrating Rublon with an application. Various applications require this value to be entered during the configuration process to enable Rublon Multi-Factor Authentication. You can copy the value to the clipboard by clicking the first icon, or display the value by clicking the second icon.
- Secret Key – a value often required when you are integrating Rublon with an application. Various applications require this value to be entered during the configuration process to enable Rublon Multi-Factor Authentication. You can copy the value to the clipboard by clicking the first icon, or display the value by clicking the second icon.
- Created At – a creation timestamp.
- Delete – delete the application.
How to add an application
1. Sign in to the Rublon Admin Console.
2. Select the Applications tab.
3. Click Add Application.
4. Navigate to the Details.
4. Set a Name for your application.

5. Select the Type of your application from the list of types supported by Rublon.
6. Set the URL of your application. This field is not required and may not be displayed for some applications.
7. Decide if you want to enable username normalization.
8. Decide if you want to let users manage authenticators while logging in to this application. Checking this option will allow all users to add, edit, and delete their devices in the Manage Authenticators view accessible from the Rublon Prompt.
Note
The Let Users Manage Authenticators checkbox is not visible for applications that do not support the Rublon Prompt.
9. Click Save to add your application.
How to edit an application
1. Sign in to the Rublon Admin Console.
2. Select the Applications tab.
3. Find an application you would like to edit.
4. Click the name of the application.

5. You can change details about your application. You can also assign a policy to this specific application.
6. You can set one or more Permitted Groups.

7. In the Policies section, you can assign an Application Policy to this specific application (See: How to assign Application Policy to application). You can also set which Custom Policies should be assigned to which user groups in the context of this specific application (See: How to assign Group Policies to groups within application).

8. Click Save to save your changes.
How to assign Application Policy to an application
Refer to Policies to learn more about creating and editing policies.
1. Sign in to the Rublon Admin Console.
2. Select the Applications tab.
3. Find an application you would like to assign a policy to.
4. Click the name of the application.
5. In the Policies section, navigate to Application Policy and click Assign Application Policy. You can create a New Policy or assign an existing one.
6. Once you assign a policy to your application, one or more sections from the global policy will be overridden, depending on the configuration of your custom policy.
Tip
When adding a new application, you can assign a policy right after creating the application. Fill in the Application data form and click Save. You are ready to assign a policy now!
After assigning a policy to an application:
- Click Edit next to your Application Policy to edit its settings.
- Click Replace next to your Application Policy to replace it with another policy
- Click Unassign next to your Application Policy to unassign it.

How to assign Group Policies to groups within application
Refer to Group Policies to learn more about creating and editing group policies.
1. Sign in to the Rublon Admin Console.
2. Select the Applications tab.
3. Find the application you would like to edit.
4. Click the name of the application.
5. In the Policies section, navigate to Group Policies and click Assign Group Policy
6. You can create a New Policy or select an existing one and apply that policy to one or more groups.

7. Click Assign to save your changes.
How to delete an application
1. Sign in to the Rublon Admin Console.
2. Select the Applications tab.
3. Find the application you would like to delete.
4. Click the trash bin icon under Delete.

5. You will be asked to confirm that you would like to delete the application. You cannot revert this.
6. Click Delete to delete the application.
Users
Users allows you to manage your users. Add, edit and delete selected users.
The Users section depicts all users in the form of a table.
Every user in the table contains the following information:
- Username – the username; has to be unique within the organization
- Email – the email address of the user; has to be unique within the organization
- Full Name – the full name of the user; not required
- Status – the status of the user: active, bypass, pending, or denied
- Phones – user’s phones used to log in to integrated applications
- Devices – the devices of the user, for example, Rublon Authenticator or WebAuthn/U2F Security Key
- Last Login – date and time of the last login
Users imported from an external source (like Active Directory) using Directory Sync will have a badge attached to their username. Any changes made to such users will be lost during the next synchronization. To learn more about Directory Sync, take a look at Synchronizing users using Directory Sync.

User Status
A Rublon user’s status can be one of the following:
- Active – The user must complete Multi-Factor Authentication (MFA) to gain access. Active is the default status after creating a new user.
- Bypass – The user gains access after entering their primary credentials. Rublon’s second factor is skipped. Read also: Why are my users getting bypassed?
- Denied – Multi-Factor Authentication (MFA) is not performed and the user is denied access.
- Pending – The user’s account is not yet active and is awaiting approval from an administrator.
- Locked Out – The user’s account is temporarily locked due to exceeding the limit of failed authentications.
Search for users
You can filter the table using the Search feature.
Search filtering works for the following columns:
- Username
- Full Name
- Status
- Last Login
Examples of using Search:
- Enter example.com to find all users with the example.com mail domain.
- Enter a part of a username to find all users whose names contain this part.
How to export users to CSV
You can export your user list to a CSV file.
Click the Export All to CSV button to export all users.

You can select users you want to export using the checkboxes next to each user.
If more than one user is checked, then only these checked users will be exported after clicking the Export Selected to CSV button.
For example, in the following image, only bob and carol will be exported after clicking the Export Selected to CSV button.

How to import users from CSV
You can import users from a CSV file into the Users tab in the Rublon Admin Console. Before importing the users, you need to prepare your CSV file for import. All required steps are described below.
Note
When a user with a given username already exists, the values of status, email, and name (if defined) will be overwritten. The phone number will not be overwritten. Instead, a new phone number will be added next to the old one.
To import users from a CSV file:
1. Prepare your CSV file for import (How to prepare my CSV file for import)
2. Sign in to the Rublon Admin Console.
3. Select the Users tab.
4. Click Import from CSV.

5. Click Choose and select your CSV file from the file system.
6. Click Import to import the users from the CSV file to the Users tab.

Note
If the import fails, none of the users are imported. Refer to Troubleshooting CSV File Import Errors.
7. After successful import, you can now send enrollment emails to the users.
How to add user
1. Sign in to the Rublon Admin Console.
2. Select the Users tab.
3. Click Add User.
4. Set the username. Username has to be unique within the organization.
5. Set the user’s email address. This is not required.
6. Select the status of the user.
7. If you are an administrator with at least one assigned Administrative Unit, you must select at least one group that this user will be added to. If you are an administrator with no assigned Administrative Units, you can leave the Groups field empty.
8. Click Save to add the new user.
How to edit user
1. Sign in to the Rublon Admin Console.
2. Select the Users tab.
3. Click the username of the user you would like to edit.
4. Make changes and click Save. Note that when an administrator with assigned Administrative Units is editing a user, at least one group must be selected to save the changes.

How to change user status
Refer to our dedicated article: How to change user status in Rublon Admin Console?
How to delete user
1. Sign in to the Rublon Admin Console.
2. Select the Users tab.
3. Select a user you would like to delete. Note that you can select more than one user.
4. Click the Delete Selected button.
5. You will be asked to confirm your decision. Note that deleting a user cannot be reverted. Click Delete to delete one or more users you selected.
How to add user phone
Note
If you want to add a phone for a user in an organization that uses applications without Rublon Prompt support, refer to Effective Management of User Phones For Applications That Do Not Support Rublon Prompt.
1. Sign in to the Rublon Admin Console.
2. Select the Users tab.
3. Click the name of a user you would like to add a phone number for.
4. Click Add Phone.
5. Provide the phone number of the user, select the phone type, and click Save.
6. You can set a name for the device. Click Save if you specified the name.
7. Your user must now activate the Rublon Authenticator on the phone you just added. You can send them a Mobile Activation Email.
How to delete user phone
1. Sign in to the Rublon Admin Console.
2. Select the Users tab.
3. Find the user whose phone you want to delete. You can use the search feature to find the user.
4. Click the username of the user whose phone you would like to delete.

5. In the Phones section, click the red trash icon next to the device you want to delete.

6. When asked to confirm, click Delete.

7. The old mobile device has been deleted.
Note
You can also delete the user phone in the following way:
1. Select the Phones tab.
2. Find the phone you want to delete and click its name in the Device column.
3. Click Delete Phone.
4. When asked to confirm, click Delete.
How to add user FIDO authenticator
1. Sign in to the Rublon Admin Console.
2. Select the Users tab.
3. Click the name of a user you would like to add a FIDO authenticator for. You can use the search feature to find the user.
4. In Security Keys, click Add Security Key.

5. Enter a name for the key and click Add.

6. Follow the screen prompts to enroll the security key.
Note
Rublon’s admin-side FIDO enrollment supports External authenticators and cloud-synced Built-in authenticators.
Examples of supported FIDO authenticators (admin-enrollable):
• Physical FIDO U2F & FIDO2 security keys (e.g., YubiKey, Google Titan)
• Cloud-synced passkeys with no shared space (e.g., Google Password Manager, iCloud Keychain)
• Cloud-synced passkeys with shared space – Learn more: Deploying Admin-Enrolled Passkeys With Enterprise Password Managers
Examples of unsupported FIDO authenticators (user self-enroll only):
• Windows Hello (TPM-backed passkeys strengthened with PIN, face, or fingerprint)
• On-device Touch ID / Face ID passkeys that never leave the Secure Enclave.
Note
At this time, administrators can enroll security keys for user accounts only. Adding keys for other administrator accounts is not supported.
Note
How to send Enrollment Email
1. Sign in to the Rublon Admin Console.
2. Select the Users tab.
3. Click the name of a user you would like to send an enrollment email to.
4. Click the Send Enrollment Email button.

5. Rublon will send an email message with an enrollment link. A user can use this link to enroll their authenticator.
Note: Enrollment links expire after 48 hours. If you send an Enrollment Email to a user and the user clicks the link after more than 48 hours, they will receive an error message. If this is the case, you have to send them another Enrollment Email.
How to Bulk Enroll User Authenticators
1. Sign in to the Rublon Admin Console.
2. Select the Users tab.
3. Check the names of users you would like to send an enrollment email to.
4. Click the Send Enrollment Emails button.

5. Click Send to confirm.
6. Rublon will send email messages with an enrollment link to all selected users. A user can use this link to enroll their authenticator.
Note
When Rublon detects that one or more selected users will not receive an enrollment link email, it will inform you by displaying an appropriate warning message. Possible reasons for the user not receiving an enrollment email are:
• The user’s email address is not set. To fix that, go to the user’s profile and enter their email address.
• The user has already enrolled their mobile device. You do not have to do anything in this case.
Note
Analogously to sending enrollment emails to just one user, the enrollment link expires after 48 hours. After that time, you have to send another enrollment email.
How to add user to group
1. Sign in to the Rublon Admin Console.
2. Select the Users tab.
3. Click the username of the user you would like to edit.
4. In Groups, click the dropdown and select one or more groups by clicking their names.

5. As you click the group names, they will be added to the list of Groups. You can remove a group from the list by clicking the X next to the name in the list or clicking the name of the group again in the dropdown to uncheck it.
6. Click Save to save the changes.
How to bulk add users to group
1. Sign in to the Rublon Admin Console.
2. Select the Users tab.
3. Check the names of users you would like to add to a group.
4. Click the Add to Group button.

5. Select the group and click Add.

6. Rublon will add the selected users to the group.
How to add, edit, and delete user aliases
1. Sign in to the Rublon Admin Console.
2. Select the Users tab.
3. Click the username of the user you would like to edit.
4. Click Add Username Alias if the user has no aliases or Edit Aliases if there is already one or more aliases assigned to the user.
- To add a new alias, when there is zero right now, simply enter the User Alias name and click Save.
- To add a new alias, when there is one or more right now, click Add Username Alias and then enter the User Alias name and click Save.
- To edit an existing alias, change its name or number and click Save.
- To delete an existing alias, click the trash bin icon and click Save.

How to add a Bypass Code for user
1. Sign in to the Rublon Admin Console.
2. Select the Users tab.
3. Click the username of the user you would like to generate a Bypass Code for.
4. In Bypass Codes, click Add Bypass Code.
5. In the Code Generation section, choose if you prefer Rublon to automatically generate the code, or if you would like to manually input the code yourself.
6. In the Expiration Time section, choose the expiration time for the Bypass Code. You can also set it to never expire.
7. In the Usage Limit section, set the maximum number of uses for this code or set it as unlimited.

8. Click Save to add the Bypass Code for this user.
9. After the Bypass Code has been added, you can:
- In the Bypass Code column, show its value (it is hidden by default) and copy its value
- In the Delete column, delete the code
The Bypass Code will be automatically removed from the Admin Console after it has been used the defined number of times or it has expired.
Directory Sync

Directory Sync allows you to add and edit directory synchronization configuration like Entra ID Connection. You can use this tab to import your users from Microsoft Entra ID into the Users tab in the Rublon Admin Console.
How to synchronize users from Entra ID using Directory Sync?
- If you wish to synchronize users from Entra ID, refer to How to synchronize users from Entra ID using Directory Sync.
How to synchronize users from other directories using Directory Sync?
Synchronizing users from directories other than Entra ID can currently be only performed using the Rublon Authentication Proxy. Synchronization with these other directories via the Directory Sync tab in on our roadmap.
- If you wish to synchronize users from Active Directory, refer to How to synchronize users from Active Directory using Directory Sync.
- If you wish to synchronize users from OpenLDAP, refer to How to synchronize users from OpenLDAP using Directory Sync.
Groups
Groups allows you to manage your groups. Create, view, edit, delete groups, add users to a group and remove users from a group, and set permitted groups per application.
The Groups section shows all groups in the form of a table.
Every group in the table contains the following information:
- Name – the name of the group; has to be unique within the organization
- Status – the status all users belonging to the group will have: active, bypass, or denied
- Description – the optional description of the group.
- Users – the number of users in the group
- Delete – delete the group
Groups imported from an external source (like Active Directory) using Directory Sync will have a badge attached to their name. Any changes made to such groups will be lost during the next synchronization. To learn more about Directory Sync, take a look at Synchronizing users using Directory Sync.

After clicking the name of the group in the Name column, you can edit the group and see a list of users belonging to this group.

Note
Groups is only available for Trial and Business plans. Groups is not available for the Free plan.
Permitted Groups
When editing an application, you can set one or more Permitted Groups for the application.
- If you set one or more Permitted Groups, then only members of these groups will be able to log in to this application. All other users will be denied access to the application.
- If you do not set any Permitted Groups, every user will be able to access the application regardless of which group they are in.

Using Groups to Manage Application Access
Refer to the following table to see what the Effective User Status will be depending on the different values of User Status and Group Status.
- User Status – the user status set for the user in the Users tab
- Group Status – the group status set for the group in the Groups tab
- Effective User Status – the effective user status of the user who belongs to a group with a given status and tries to log in to an application integrated with Rublon
| User Status | Group Status | Effective User Status |
| Denied | Any | Denied |
| Any | Denied | Denied |
| Bypass | Active | Bypass |
| Active | Bypass | Bypass |
| Active | Active | Active |
Refer to the examples below to better understand groups.
Example 1:
This example shows that the group status can sometimes override a user status.
1. Bob’s status on his profile in the Users tab is set to Active.
2. However, Bob belongs to a Bypass Group group that has its status set to Bypass.
3. In the Users tab, an administrator will see BYPASS instead of ACTIVE for Bob in the Status column.
4. Also, both Bob’s user status and their effective status will be displayed on their profile:

Example 2
This example shows that some users will be denied access to an application if they do not belong to any of the lists in Permitted Groups.
1. There are two applications in the Applications tab: Windows Logon and WordPress.
2. There are two users in the Users tab: Bob and Alice.
3. Both Bob and Alice have the status Active, so at this point, they can both log in to both applications.
4. Administrator creates a group called Windows Users with the status Active and adds Alice to the group.

5. Administrator edits the Windows Logon application and adds the Windows Users group to the list of Permitted Groups.

6. Now:
- Alice can log in to both Windows Logon and WordPress applications.
- Bob can only log in to WordPress. They will be denied access when trying to log in to Windows Logon. This is because Bob does not belong to any of the Permitted Groups for Windows Logon application.
Example 3
This example is similar to Example 2, but the Windows Users group has the status Bypass instead of Active.
1. There are two applications in the Applications tab: Windows Logon and WordPress.
2. There are two users in the Users tab: Bob and Alice.
3. Both Bob and Alice have the status Active, so at this point, they can both log in to both applications.
4. Administrator creates a group called Windows Users with the status Bypass and adds Alice to the group.
5. Administrator edits the Windows Logon application and adds the Windows Users group to the list of Permitted Groups.
6. Now:
- Alice can log in to both Windows Logon and WordPress applications, but Alice will be bypassed when logging in to Windows Logon. This is because Alice belongs to a group whose status is Bypass.
- Bob can only log in to WordPress. They will be denied access when trying to log in to Windows Logon. This is because Bob does not belong to any of the Permitted Groups for Windows Logon application.
How to add group
1. Sign in to the Rublon Admin Console.
2. Select the Groups tab.
3. Click Add Group.
4. Set the group name. This name must be unique within the organization.
5. Set the group description. This is not required.
6. Select the status of the group.
7. If you are an administrator with at least one assigned Administrative Unit, you must select at least one unit that will be assigned to this group. If you are an administrator with no assigned Administrative Units, you can leave the Administrative Units field empty.
8. Click Save to add the new group.
9. You can now add users to the group you created.
How to add users to group
You can add one user to a group or bulk-add multiple users to a group.
How to assign administrative units to group
You can assign one or more administrative units to a group:
How to edit group
1. Sign in to the Rublon Admin Console.
2. Select the Groups tab.
3. Click the name of the group you would like to edit.
4. You can change the group name, status, description, and administrative units. Note that when an administrator with assigned Administrative Units is editing a group, at least one unit must be selected to save the changes. Click Save to save your changes.
5. Scroll down to see the list of users in the group. You can select one or more users in the group and click Remove from Group to remove these users from this group. Note that after confirming removal, the selected users will be immediately removed. You do not have to confirm this operation with the Save button.
How to delete group
1. Sign in to the Rublon Admin Console.
2. Select the Groups tab.
3. Find a group you would like to delete and click the Delete button for that group.
5. You will be asked to confirm your decision. Note that deleting a group cannot be reverted.
6. Click Delete to delete the group.
Policies
Policies gives you the power to control every step of your users’ authentication and manage their use of remembered devices. Change the Global Policy or define Custom Policies that you can apply in the Applications tab as Application Policies or Group Policies.
Policies consists of two sections:
- Global Policy
- Custom Policies

Global Policy
Global Policy allows you to manage the policy that applies to all applications unless overridden with a Custom Policy.
Click Edit Global Policy to change settings pertaining to the behavior of all integrated applications.
Custom Policies
Custom Policies gives you the power to create and assign Custom Policies to your applications. Custom Policies will override the settings from the Global Policy when assigned to an application. You can assign one Custom Policy to many applications.
How to create new policy
In the Policies tab, click New Policy to create a new custom policy. The form is very similar to the Edit Global Policy form.
- Specify a name for your new policy.
- Click Authorized Networks, Authentication Methods, or Remembered Devices on the left to add them as sections to be overridden. Click the trash bin icon to delete a section to be overridden.
- Configure your new policy. Refer to Policy Sections to learn more about each section.
- Click Save to save your new policy.

You can Edit or Delete a custom policy.
Note
You have to assign a policy to at least one application for the policy to take effect.
Refer to How to assign a policy to an application to learn how to use a custom policy.
Policy Sections
Both the Global Policy and Custom Policy comprise of one or more sections.
Authentication Methods
The Default Authentication Method policy automatically selects the chosen method as the second factor during Rublon Authentication.

Authentication Methods. Check and uncheck to activate or deactivate an authentication method.
You cannot deactivate all authentication methods. At least one authentication method has to be active.
Refer to Authentication Methods to learn more about authentication methods offered by Rublon.

The Hide deactivated authentication methods in the Rublon Prompt. checkbox controls whether authentication methods deactivated in this policy are hidden entirely from the Rublon Prompt or simply shown in a disabled (grayed‑out) state.
- When checked, any method you have deactivated will not appear at all in the Rublon Prompt.
- When unchecked, deactivated methods remain visible but are displayed in a grayed‑out, non‑selectable state.

Authorized Networks
Authorized Networks is a list of networks that will bypass Rublon 2FA.
A list of IP addresses, IP ranges, or CIDRs separated by a comma:
- Use # to add a comment – comments are ignored
- Whitespaces and newlines are allowed and will be ignored
- Use public IP addresses
Example:
# this comment will be ignored
# 192.168.1.1, 10.0.0.2 - these IPs will be ignored
202.201.200.192
17.5.7.8,17.5.100.0-17.5.100.50, 17.5.100.0/24
203.100.100.5

Note
Remembered Devices
Remembered Devices offers your users a way to bypass Rublon MFA during their next logins.
You can either disable this option or allow your users to remember their device for a given number of days or hours.
If you check Do not remember devices, the Remember this device checkbox will not appear on Rublon Prompt and you will not be able to add a remembered device.

Note
For security reasons, a device can only be remembered for a maximum of 90 days.
Note
Remembered Devices Policy is only available for Trial and Business plans. Remembered Devices is not available for the Free plan.
Phones
Phones allows you to supervise users’ and administrators’ phones and tablets.

How to add phone
Refer to How to add user phone or How to add administrator phone.
How to edit phone
1. Sign in to the Rublon Admin Console.
2. Select the Phones tab.
3. Click a link in the Devices column to select the phone you want to edit.
4. You can change the Device Name and Phone Number.
5. Click Save to save the changes you made.

How to delete phone
Refer to How to delete user phone or How to delete administrator phone.
How to send Mobile Activation Email
The Mobile Activation Email feature allows you to send an email message with instructions on how to activate the Rublon Authenticator. This is an alternative way of activating the Rublon Authenticator mobile app.
If your user has already activated Rublon Authenticator, you will not be able to send them a Mobile Activation Email (the Send Mobile Activation Email button will not appear for this phone).
To send Mobile Activate Email:
1. Sign in to the Rublon Admin Console.
2. Select the Users tab.
3. Click the name of a user you would like to send the Mobile Activation Email to.
4. Click Add Phone.

5. Provide the phone number of the user and click Save.
6. You can set a name for the device. Click Save if you specified a name.
7. Click Send Mobile Activation Email.

8. The Send Mobile Activation Email view will appear.

9. Set the expiration time after which the QR Code inside the Mobile Activation Email will expire.
10. Enter the email address to send the Mobile Activation Email to.
11. Click Send Activation Email.
12. Rublon will send an email message with a link to a QR Code. A user can scan this QR code to activate their account on the Rublon Authenticator mobile app.
How to check user’s Rublon Authenticator information
If a user has activated the Rublon Authenticator mobile app on their mobile device, you can check the version of their app as well as the current status of push notification reception.
To check a user’s Rublon Authenticator information:
1. Sign in to the Rublon Admin Console.
2. Select the Users tab.
3. Find and click the name of a user who has a Rublon Authenticator mobile app installed on their mobile device (signified by a phone icon in the Devices column)

4. Click the Device you want to check the information for.

5. Inspect the information in the Rublon Authenticator section:
- App Version – version of Rublon Authenticator that has been installed on this mobile device
- Push Notifications – whether Mobile Push notifications are possible on this phone.

Note
If the Rublon Authenticator section shows Push Notifications as Not Possible, the user most probably has not enabled notifications on their phone. Refer to How To Solve Push Notification Issues on Rublon Authenticator to learn how to turn on notifications on Android and iOS operating systems.
Remembered Devices
Remembered Devices allows you to review remembered devices to see all devices that users have trusted to bypass multi-factor authentication in your organization.
This view includes both currently remembered devices and historical ones, even if they are no longer set to bypass MFA and require authentication unless the user chooses to trust them again during login. This ensures administrators maintain full visibility of all remembered devices, enhancing their ability to track and manage potential security risks, and ensuring a thorough security audit.

Each remembered device entry contains the following information:
- Browser – the browser on which the device is remembered
- Platform – the operating system on which the device is remembered
- Last IP address – the last known IP address
- User – the user that this log is related to
- Registration – the date and time this device was registered as remembered
- Delete – click the trash bin icon next to a given remembered device to remove that device
The following sorting, filtering, and searching options are available:
- The Remembered Devices table allows sorting by the following columns:
- Browser
- Platform
- Last Use
- Registration
- The Registration From and Registration to fields allow you to narrow down the results to the given date and time range.
- The Remembered Devices table also allows searching by the following data, thus narrowing down the results:
- Browser
- Platform
- Last IP address
- Username (including Administrator name)
Security Keys
Security Keys allows you to see all WebAuthn/U2F and YubiKey OTP security keys in your organization. These keys are used when logging in to applications protected by Rublon.
The Security Keys section depicts all security keys in the form of a table.
Every security key in the table contains the following information:
- Name – the name of the security key.
- Type – the type of the key (WebAuthn or YubiKey OTP)
- User – the user who registered the key.
- Registration – the date and time of key registration.
- Last Use – the date and time of the last key use.
- Authentications – the number of times the user used this security key to log in to any of the integrated applications.
- Delete – click the trash bin icon next to a given security key to remove that security key.

Clicking a link in the Name column will show details of that specific security key.

How to add a new security key
How to add user FIDO authenticator
Learn how a user can self-enroll a new security key.
Administrators
Administrators allows you to add, edit, and remove administrators.

Administrator Roles
Each administrator has one of multiple roles that define their privileges within the Rublon Admin Console.
Learn more about Rublon Administrator Roles.
How to add admin
If you are the owner or an administrator in an organization, you can add new admins to this organization:
1. Sign in to the Rublon Admin Console.
2. Select the Administrators tab.
3. Click Add Administrator.
4. Set the email address, first name, last name, and role. Email address has to be unique.
5. Set the phone number. This is not required.
6. Click Save.
7. An email with a join link to your company will be sent to their mailbox.

8. They have to click Join, set up their password to the Rublon Admin Console, and click Next.

9. They will be asked to scan the QR code.
10. Once they scan the code, they will have to choose one of the available methods of authentication to confirm their identity.
11. Once they confirm their identity, they will be logged in to Rublon Admin Console and granted administrator rights.
Resend Setup Email
If your administrator did not receive the join link email or the link expired, you can resend the join link.
1. Sign in to the Rublon Admin Console.
2. Select the Administrators tab.
3. Click the username of the administrator you wish to resend the join link to.
4. Click the Resend Setup Email button.

How to add admin phone
1. Sign in to the Rublon Admin Console.
2. Select the Administrators tab.
3. Click the name of an admin you would like to add a phone number for.
4. Click Add Phone.
5. Provide the phone number of the admin, set the phone type, and click Save.
6. You can set a name for the device. Click Save if you specified the name.
7. Administrator must now activate the Rublon Authenticator on the phone you just added.
How to delete admin phone
1. Sign in to the Rublon Admin Console.
2. Select the Administrators tab.
3. Find the administrator whose phone you want to delete.
4. Click the email address of the administrator whose phone you would like to delete.
5. In the Phones section, click the red trash icon next to the device you want to delete.
6. When asked to confirm, click Delete.
7. The old mobile device has been deleted.
Note
You can also delete the admin phone in the following way:
1. Select the Phones tab.
2. Find the phone you want to delete and click its name in the Device column.
3. Click Delete Phone.
4. When asked to confirm, click Delete.
How to add admin to administrative unit
1. Sign in to the Rublon Admin Console.
2. Select the Administrators tab.
3. Click the name of the admin you would like to edit.
4. In Administrative Units, click the dropdown and select one or more administrative units by clicking their names.
5. As you click the administrative unit names, they will be added to the list of Administrative Units. You can remove a unit from the list by clicking the X next to the name in the list or clicking the name of the unit again in the dropdown to uncheck it.
6. Click Save to save the changes.
Administrative Units
Administrative Units allows you to manage administrative units in your organization. Create, view, edit, delete administrative units, and add and remove administrators to an administrative unit.
Administrative Units restrict access to particular Groups (hence Users) for specific Administrators. An Administrator must be part of an Administrative Unit that has access to a specific Group if they want to view Users who are part of that Group.
The Administrative Units section shows all administrative units in the form of a table.
Every administrative unit in the table contains the following information:
- Name – the name of the unit; has to be unique within the organization
- Description – the optional description of the unit.
- Administrators – the number of administrators in the group
- Delete – delete the administrative unit

The following sorting, filtering, and searching options are available:
- The Authentication Logs table allows sorting by the following columns:
- Name
- The Authentication Logs table also allows searching by the following data, thus narrowing down the results:
- Name
- Description
After clicking the name of the administrative unit in the Name column, you can edit the unit and see a list of groups this unit can manage.

Using Administrative Units to Manage Admin’s User Management Privileges
An administrator with the Owner role can:
- Create and edit Administrative Units, including the selection of groups this unit can manage.
- Delete Administrative Units.
- List Administrative Units and search for units by name and description.
- Assign Administrative Units from the group edit view.
The following is true for non-Owner administrators:
- A non-Owner administrator with at least one assigned Administrative Unit can only see the users that belong to the group to which one of the Administrative Units this administrator belongs to is assigned.
- Example:
- There’s user bob who belongs to the Windows Users group.
- There are many other users in the Users tab but they either belong to no group or belong to other groups.
- There’s a non-Owner administrator alice who belongs to the Windows Admins administrative unit.
- The Windows Admins administrative unit is assigned to the Windows Users group.
- After admin alice signs in to the Rublon Admin Console and selects the Users tab, they will only see user bob on that tab.
- Admin alice will not see any other user because user bob is the only user in the group to which Alice’s administrative unit is assigned.
- To make alice see more users, an Owner in this organization can either add more users to the Windows Users group or assign more administrative units to alice. For example, assigning a VPN Admins unit to a VPN Users group and then adding VPN Admins to the list of Alice’s administrative units will make her see all users who belong to the VPN Users group. An admin can also choose to remove all administrative units for admin alice. This will make Alice see all users in the Users tab regardless of their group assignment.
- A non-Owner administrator cannot access the Edit User view if the user does not belong to a group associated with an Administrative Unit this administrator belongs to.
- The non-Owner administrator will not see such a user in the Users tab. If they have a link to edit that user’s profile, they will receive a message saying they do not have the necessary privileges to perform this action.
- A non-Owner administrator with an assigned Administrative Unit cannot create or import new users.
- A non-Owner administrator with at least one assigned Administrative Unit can only see the groups, phones, remembered devices, and security keys related to the Administrative Units to which this admin belongs.
- Example:
- There’s a non-Owner administrator alice who belongs to the Windows Admins administrative unit.
- The Windows Admins administrative unit is assigned to the Windows Users group.
- Admin alice will not see any groups other than Windows Users in the Groups tab of the Rublon Admin Console.
- In the Phones tab, alice will only see the phone numbers of users belonging to the Windows Users group.
- In the Security Keys tab, alice will only see the security keys of users belonging to the Windows Users group.
- In the Remembered Devices tab, alice will only see the remembered devices of users belonging to the Windows Users group.
How to add administrative unit
1. Sign in to the Rublon Admin Console.
2. Select the Administrative Units tab.
3. Click Add Administrative Unit.
4. Set the administrative unit name. This name must be unique within the organization.
5. Set the unit description. This is not required.
6. Select the groups to assign this unit to.

7. Click Save to add the new group.
8. You can now add administrators to the administrative unit you created.
How to add admins to administrative unit
You can add one administrator to an administrative unit or bulk-add multiple administrators to an administrative unit.
How to edit administrative unit
1. Sign in to the Rublon Admin Console.
2. Select the Administrative Units tab.
3. Click the name of the unit you would like to edit.
4. You can change the unit name and description. Click Save to save your changes.
How to delete administrative unit
1. Sign in to the Rublon Admin Console.
2. Select the Administrative Units tab.
3. Find an administrative unit you would like to delete and click the Delete button for that group.
5. You will be asked to confirm your decision. Note that deleting a unit cannot be reverted.
6. Click Delete to delete the unit.
How to assign administrative unit to group
1. Sign in to the Rublon Admin Console.
2. Select the Groups tab.
3. Click the name of the group you would like to edit.
4. Administrative Units is a list of administrative units assigned to this group. You can add one or more administrative units to the group. You must confirm this operation using the Save button.
Admin Sign-in Settings
Admin Sign-in Settings allows you to manage administrator sign-in and authentication settings globally in your organization. Decide which authentication methods administrators can use to sign in to the Rublon Admin Console and set the time limit for Rublon Admin Console sessions to ensure NIST AAL3 or NIST AAL2 compliance.

All settings in the Admin Sign-in Settings tab are global, which means they apply to all administrators regardless of their administrator role. When you edit these settings, make sure you do not lock yourself or other admins out of the Rublon Admin Console. To help prevent that, the console enforces three safeguards:
- An administrator cannot deactivate the authentication method they used to access the Rublon Admin Console on their last sign-in. To deactivate that method, the admin must signs out of the Admin Console and signs in again with a different method.
- If Administrator B deactivated the authentication method that Administrator A last used to access the Rublon Admin Console, and Administrator A is still signed in the console, Administrator A will see a red-box warning about that and will not be able to save changes until they check this method again.
- If an administrator changed the available authentication methods and wants to save the changes, a confirmation window appears, asking them to ensure these changes do not block themselves or other admins from accessing the Rublon Admin Console.
Session Timeout
Set the time limit for Rublon Admin Console sessions. Administrators will be signed out automatically when the time expires.
- 15 min (compliant with AAL3, default)
- 30 min (compliant with AAL2)
Note that regardless of activity, re-authentication is required after 12 hours.
Reports
Click the Reports tab to extend it and show its subtabs. Refer to the following subtabs to learn more about them.
Authentications
Authentications allows you to review the top authentication methods, applications, application types, denied applications, denied users, unfinished application authentications and unfinished user authentications within the last 30 days.

The Authentications tab includes the following subsections:
- Authentication Methods: A diagram of authentication methods used in the organization.
- Applications: A diagram of applications users logged in to in the organization.
- Application Types: A diagram of application types used in the organization.
- Idle User Authentications: A list of the top users whose authentication attempts failed due to inactivity. This happens when a user initiates authentication but does not finish the process before it times out.
- Denied Applications: A list of the top applications where users’ login attempts were denied. This section highlights which applications have the highest number of denied access attempts.
- Denied Users: A list of the top users whose login attempts were denied over the past 30 days. It provides insight into which users are most frequently experiencing access denials.
- Unfinished Application Authentications: A list of the top applications for which authentication attempts failed due to inactivity. This occurs when users start the authentication process for an application but do not complete it before it times out.
- Unfinished User Authentications: A list of the top users whose authentication attempts failed due to inactivity. This happens when a user initiates authentication but does not finish the process before it times out.
Authentication Logs
Authentication Logs allows you to browse authentication logs of applications integrated with Rublon.
The Authentication Logs section depicts all authentication logs in the form of a table. Note that you can change the number of entries shown per page.
Every log entry contains the following information:
- Timestamp – the date and time the authentication attempt occurred.
- Result – whether the authentication was successful or the user has been denied.
- User – the user that initiated the authentication.
- Application – the protected application the user tried to log in to.
- Access Device – information about the access device, may contain the IP address, browser name, OS name, and user-agent information.
- Method – the Authentication Method used during the login process or Trusted Device if the user chose to add their device to trusted devices before.

The following sorting, filtering, and searching options are available:
- The Authentication Logs table allows sorting by the following columns:
- Timestamp
- Result
- User
- Login Used
- Method
- The Timestamp From and Timestamp to fields allow you to narrow down the results to the given date and time range.
- The Result field allows you to narrow down the results to one or more selected authentication results.
- The Method field allows you to narrow down the results to one or more authentication methods used during authentication attempts.
- The Authentication Logs table also allows searching by the following data, thus narrowing down the results:
- Application Name
- Browser Name
- Browser Version
- Email Address
- Username
- OS Name
- City
- Country
- IP Address
In addition to the Authentication Logs table, the Authentication Logs tab also includes the following two sections:
- Top Applications: A list of the top applications sorted by the number of authentications.
- Top Users: A list of the top users sorted by the number of authentications.
The information displayed in the two preceding sections is dependent on the filters and time range selected for the table.

How to export authentication logs
Authentication logs from any point within the last 180 days are available for export. This restriction to 180 days is in place to optimize performance.
1. Sign in to the Rublon Admin Console.
2. Select the Authentication Logs tab.
3. Apply filters to your authentication logs if you wish. If you do not apply any filters, the CSV file will contain all authentication logs.
Note: Every time you access the Authentication Logs tab, a Timestamp From filter automatically selects the last 30 days by default. Make sure to remove this filter if you wish to export all authentication logs.
4. Click Export to CSV to download a CSV file with authentication logs.
Audit Logs
Audit Logs allows you to browse audit logs of administrators’ actions in the Rublon Admin Console.
This tab is only visible to admins with role Owner or Administrator.
The Audit Logs section depicts all activities of administrators in the Rublon Admin Console in the form of a table. Note that you can change the number of entries shown per page.
Each audit log entry contains the following information:
- Timestamp – the date and time the activity occurred.
- Location – the City and IP address of the administrator who performed the activity.
- Actor – the username and email address of the administrator who performed the activity or just the information it was done via the Admin API if the activity was performed via the Rublon Admin API.
- Activity – the name of the activity.
- Affected – the affected entity (user, administrator, policy, organization, etc.)

The following sorting, filtering, and searching options are available:
- The Audit Logs table allows sorting by the Timestamp column.
- The Timestamp From and Timestamp to fields allow you to narrow down the results to the given date and time range.
- The Activity field allows you to narrow down the results to all occurrences of the given activity.
- The Audit Logs table also allows searching by the following data, thus narrowing down the results:
- Admin First Name
- Admin Last Name
- Admin Email
- Application Type
- IP Address
- City
- Affected
Clicking a link in the Activity column will show details of that specific audit log.

Known Audit Logs limitations:
- No ability to search audit logs by the textual content of the Activity.
- No audit logs in each application profile, meaning there is no audit log equivalent of the Recent Activity section, which presents Authentication Logs relating to a given application.
How to export audit logs?
1. Sign in to the Rublon Admin Console.
2. Select the Audit Logs tab.
3. Apply filters to your audit logs if you wish.
- Applying filters like timestamp range or search query tells Rublon to export only the audit logs that fit the selected filters.
- If you do not apply any filters, the CSV file will contain all audit logs.
4. Click Export to CSV to download a CSV file with audit logs.
Note
The Timestamp field in the exported CSV file will be formatted according to the Timezone set in the administrator’s profile. In other words, the contents of the CSV file will be the same as the table displayed for a given administrator who exports the logs.
Phone Logs
Phone Logs allows you to review phone logs of all events related to phone-based authentication methods in your organization.

Each phone log entry contains the following information:
- Timestamp – the date and time the activity occurred
- Phone Number – the phone number that this log is related to
- User – the user that this log is related to; click the username to open this user’s page
- Application – the application that this log is related to; click the application name to open this application’s page
- Context – either enrollment or authentication
- Method – the authentication method that this log is related to
- Status – the status of the phone-related event (sent, delivered, undelivered, completed, failed, accepted, no-answer, queued)
- Credits – the number of Phone Credits consumed by this event
The following sorting, filtering, and searching options are available:
- The Phone Logs table allows sorting by the following columns:
- Timestamp
- Phone Number
- Context
- The Timestamp From and Timestamp to fields allow you to narrow down the results to the given date and time range.
- The Phone Logs table also allows searching by the following data, thus narrowing down the results:
- Application Name
- Username
- Context
- Phone Number
- Status
How to export phone logs?
Phone logs from any point within the last 365 days are available for export. This restriction to 365 days is in place to optimize performance.
1. Sign in to the Rublon Admin Console.
2. Select the Phone Logs tab.
3. Apply filters to your phone logs if you wish.
- Applying filters like timestamp range or search query tells Rublon to export only the phone logs that fit the selected filters.
- If you do not apply any filters, the CSV file will contain all phone logs.
Note: Every time you access the Phone Logs tab, a Timestamp From filter automatically selects the last 30 days by default. Make sure to remove this filter if you wish to export all phone logs.
4. Click Export to CSV to download a CSV file with audit logs.
Settings
Settings allows you to set or change settings related to all applications added in the Applications tab.
Settings can be separated into the following subsections:
- Details
- User Enrollment
- Email Domain Allowlist
- Third-Party Apps
- Customization
- Failed Authentications
- Logo
- API
- Default Language
Click Save to save any changes you made in the Settings section.

Details
Set or change the name of your company, Enter a name of your choice in the Company Name field.
User Enrollment
Select the enrollment type. Three enrollment types are available:
- Automatic – all users who attempt to log in to your protected applications are automatically added to your user list. Users can also be added manually to your user list by administrators. Automatic Enrollment Type enables the Email Domains subsection.
- Manual – users must be manually added to your user list by administrators. Login attempts from other users are denied or bypassed. You can set this behavior by selecting either Deny or Bypass under Handling of unknown users. Bypass is the default behavior.
- Approval – login attempts from users trigger an email request for approval to administrators. A request expires after 24 hours. Users can also be added manually to your user list by administrators.
Email Domain Allowlist
This subsection is only available if the Automatic enrollment type has been selected in User Enrollment. If email domains are defined, then only users whose email addresses belong to such domains are automatically added to your user list. Users using email addresses outside of these domains are denied access. If no domains are defined, users from all domains are accepted.
Only Email Domains such as “rublon.com” are supported. Active Directory Domains such as “domain.local” are not supported.
You can add a new domain by entering its name and clicking the + (plus) button.
Click the trash bin icon to delete a domain.
Third-Party Apps
When checked, users will be able to enroll and use third-party authenticator apps.
Third-party authenticator app enrollment is enabled by default.
Uncheck to remove the ability to enroll third-party authenticators.
Customization
In this subsection, you can disable Rublon Branding, set a Reply-To address for email messages received by users, and customize the help text and links displayed on the Rublon Prompt and in the email messages received by users.
Rublon Branding
When checked, “Protected by Rublon” will appear on the Rublon Prompt.
Uncheck to remove Rublon branding from the Rublon Prompt.
Help Desk Email
A Reply-To address for email messages received by users.
When set, a user who received an email message from Rublon can write a reply, which will be sent to the entered Help Desk Email.
Help Desk Message
Customize the help text displayed on the Rublon Prompt and in the email messages received by users.
The text can have up to 200 characters.
Help Desk Links
Add one or two links displayed under the help text.
These links can, for example, lead to your corporate help pages or help desk support contact form.
The links must start with https:// or http://.
Logo
You can add a logo for your company. This logo will be visible during Rublon Two-Factor Authentication when your users attempt to log in to any of the integrated applications that support the Rublon Prompt. The logo is also displayed on Mobile Push login requests in Rublon Authenticator.
Failed Authentications
Set the user’s status to Locked Out after reaching a certain number of consecutive failed authentications. By default, the Failed Authentications option is unchecked. An administrator can check the checkbox and enter the number of failed authentications in the text field. The number of failed authentications can be any number from 1 to 999.
- Cumulative Counting: The number of consecutive failed login attempts is counted cumulatively for the user, regardless of the application or connector they sign in to during each authentication attempt.
- Reset on Success: A successful user login resets the counter of failed attempts.
- Restore After Time: When enabled, the user will be automatically unlocked after a given time.
After being locked out:
The user will keep seeing an Access Denied! message displayed on the Rublon Prompt every time they try to log in to an application that supports this view.
If they try to log in to an application that does not support the Rublon Prompt, they will also be denied access and a more detailed message will be saved to the log file.
Note: The lock-out mechanism only applies to users, not administrators.
To unlock a locked-out user:
1. An administrator must sign in to the Rublon Admin Console and change the user’s status back to Active.
2. When an administrator unlocks a user’s account by changing their status from Locked Out to Active, the user must successfully sign in on their very next attempt.
- After the user successfully signs in on their first attempt after being unlocked, the normal Failed Authentications setting for failed login attempts resumes, and the user will only be locked out again if they exceed the allowed number of failed attempts.
- If the user fails to sign in right after being unlocked, their account will be immediately locked out again. This security measure ensures that only the legitimate user can regain access.
The automatic unlock mechanism:
The automatic restore mechanism applies the setting at the moment a user is blocked due to failed attempts. Changes made to the restore settings after a user is blocked will not affect the current lockout. Examples:
- If the restore was set to 10 hours when the user was being blocked and the administrator later reduced it to 5 hours, the user will still be unlocked after the originally set 10 minutes.
- If the administrator enables the restore option (e.g., sets it to 1 hour) after the block occurs, the user will remain blocked until manually unlocked.
API
View or copy the value of your Company token. You will need the token in some situations, for example when configuring Rublon Access Gateway.
Default Language
Set the default language for text elements in the Rublon Prompt and emails sent to users from the Admin Console.
Supported languages:
- (bg) Български
- (cs) Čeština
- (da) Dansk
- (de) Deutsch
- (el) Ελληνικά
- (en) English
- (es) Español
- (et) Eesti
- (fi) Suomi
- (fr) Français
- (hr) Hrvatski
- (hu) Magyar
- (it) Italiano
- (lt) Lietuvių
- (lv) Latviešu
- (mt) Malti
- (nb) Bokmål
- (nl) Nederlands
- (pl) Polski
- (pt) Português
- (ro) Română
- (sk) Slovenčina
- (sl) Slovenščina
- (sv) Svenska
Billing
Click the Billing tab to extend it and show its subtabs. Refer to the following subtabs to learn more about them.
Overview
Overview shows the overview of your subscription, that is your Plan (Trial, Business, or Free), your Number of Users, Term, and Cost.
If you select the Business Plan, you can select your number of users up to 7500. If you need more than 7500 users, please contact sales@rublon.com for discounts and invoiced billing.
You can change plans at any time. If downgrading, the downgrade will take effect after the current billing period ends.
If you change your Plan from Business to Free during the billing period, you will not switch to Free immediately, but only after your billing period will have expired.
You can also see Payment History at the bottom of this tab.
Note
Rublon is a company based in Poland. If you’re not a Polish customer, some banks and credit card companies may charge you a small foreign transaction fee. To avoid this fee, you can use a card that doesn’t charge for foreign transactions. Alternatively, you can contact your bank or credit card company to learn more about their fee policies.
How to start a Rublon Business subscription
How do I start a Rublon Business subscription?
Phone Credits
Phone Credits allows you to add credits. Phone credits are used when users authenticate with text messages.

How to buy Phone Credits
Invoice Details
Invoice Details allows you to provide information, which will be included on all billing invoices on your account. Click Save to save your changes.

Profile Page
Every administrator who signs in to the Rublon Admin Console can access their profile page by clicking the Profile icon in the top right corner.
Note

The Profile page allows an administrator to:
- Change their password
- Change their first and last name
- Change their status
- Change their timezone
- Change their phone number
- Add new phones
- Supervise their security keys
An administrator has to click Save to save the changes they made.
Sign out
You can sign out by clicking the Sign out icon in the top right corner.

After a successful signout, you will be redirected to the Rublon Admin Console login page.
Troubleshooting
If you have a problem or question, refer to Rublon Admin Console – FAQ first.
If you encounter any issues with your Rublon integration, please contact Rublon Support.