Last updated on December 15, 2025
Rublon MFA supports hardware- and software-bound passkeys, allowing a seamless login experience with top security. Refer to this guide to learn how to create a Passkey for your Rublon-integrated services and use it as the second authentication factor during multi-factor authentication.
Initial Passkey Enrollment Steps
These steps are the same for hardware- and software-bound passkeys and must be completed before proceeding to further sections of this guide.
Note
To sign in using your passkey, you must first create the passkey using the Manage Authenticators view or ask your administrator to send you an Enrollment Email.
1. Initiate login to your application.
To check if your application integrated with Rublon supports WebAuthn, refer to the list of supported applications. Note that both passkeys and FIDO2 security keys use WebAuthn, so the preceding list applies to both.
2. Provide your username and password.
3. Rublon Prompt appears.

4. Click Manage Authenticators.
5. To confirm your identity before proceeding, choose one of the available authentication methods.

6. After you confirm your identity with one of the available methods (e.g., Mobile Push), the Rublon Prompt will display the Manage Authenticators view.
7. Click Add Authenticator.

8. Select WebAuthn/U2F Security Key (hardware token) as your authenticator type and click Next.
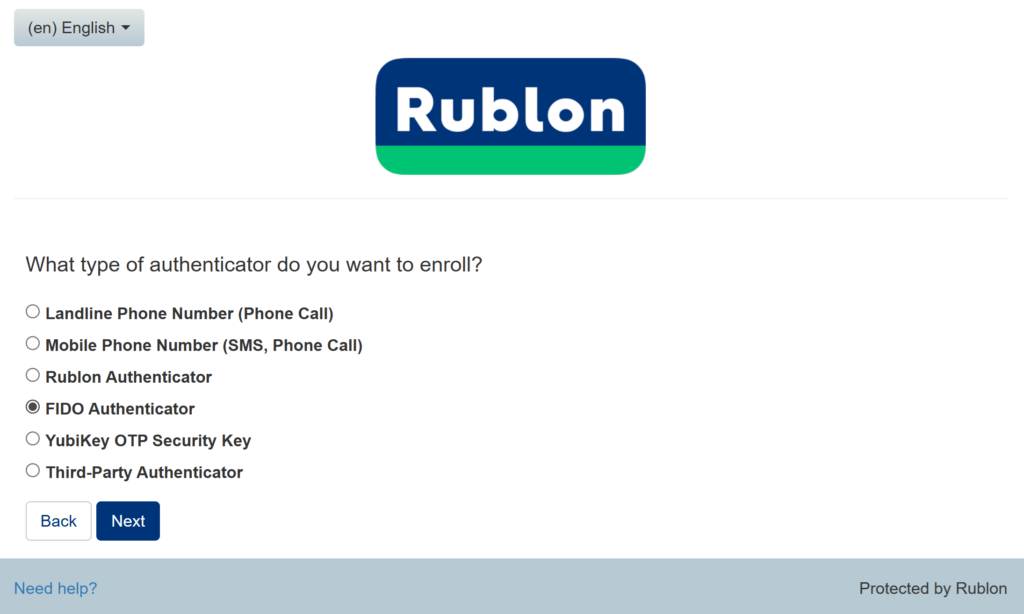
9. The subsequent steps differ depending on whether you want to enroll a software-bound passkey or a hardware-bound passkey.
- A hardware-bound passkey is a passkey you save on your FIDO2 Security Key.
- A software-bound passkey is a passkey you generate using a tool like 1Password or Bitwarden and store in your filesystem.
Enroll a Software-Bound passkey
The following example illustrates creating and enrolling a software-bound passkey with Rublon MFA using 1Password. You can use any other Passkey Manager.
1. Ensure you have completed all steps from the Initial Passkey Enrollments Steps section.
2. After selecting WebAuthn/U2F Security Key (hardware token) as your authenticator type on the previous page of the enrollment wizard, a window should open, asking you to save the passkey. In our case, this is a 1Password window and we click Save.
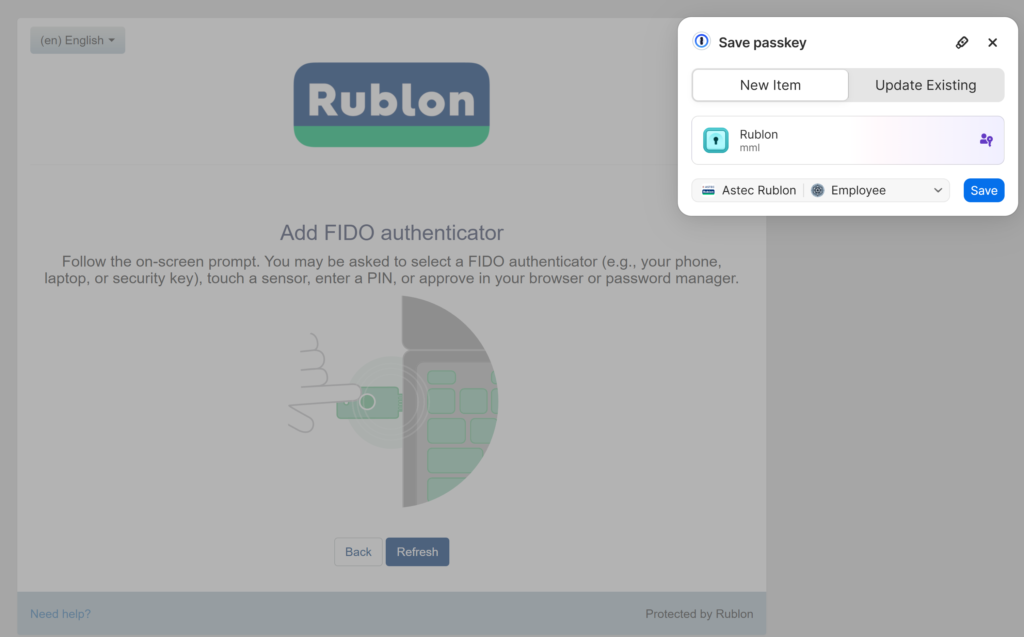
3. After the newly-created passkey is saved, enter a name for your passkey and click Save.
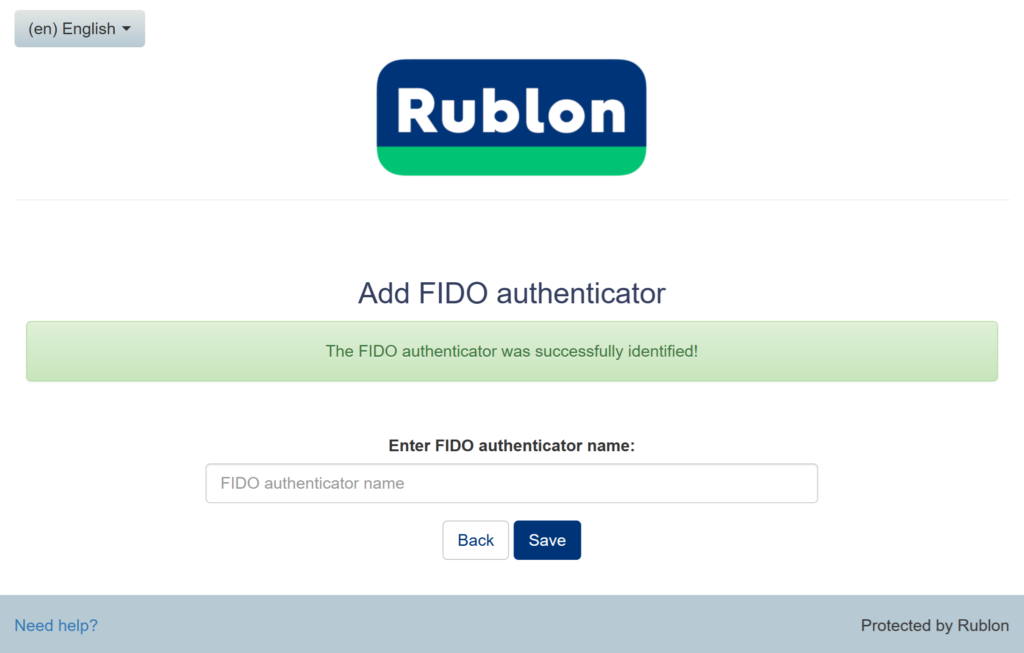
4. You will be redirected to the Rublon Prompt. You can now sign in using your passkey.
Sign in Using a Software-Bound Passkey
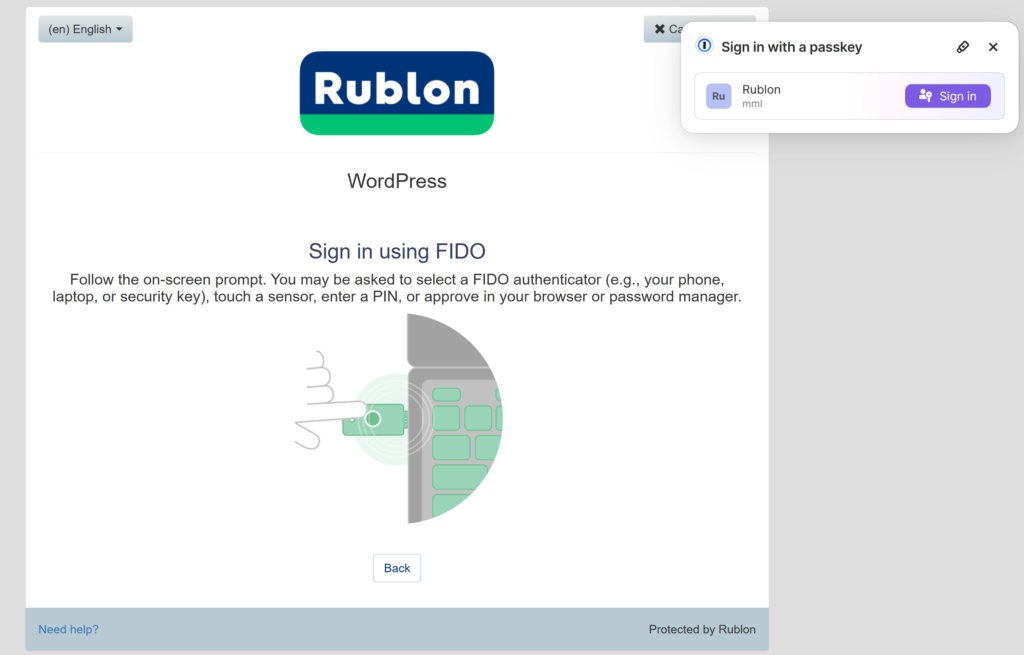
1. To sign in using your software-bound passkey, choose the WebAuthn/U2F Security Key authentication method from the Rublon Prompt.

2. Your Passkey Manager’s sign-in window will appear, giving you the option to sign in using the passkey. In our case, this is a 1Password window and our passkey is stored in the operating system of the device we use to log in, so we click Sign in.
Sign in using a passkey stored on your mobile device
If you have a passkey associated with Rublon stored in an encrypted software vault of your Passcode Manager (e.g., 1Password, Bitwarden) installed on your mobile device, you can use this passkey to sign in during Rublon MFA.
The prerequisite for using a mobile device that stores a passkey is that you complete a software-bound passkey enrollment on your mobile device. This is a mandatory prerequisite because it creates the passkey and stores it in your Passkey Manager’s local vault.
The general login steps for this scenario are as follows:
1. Enable Bluetooth on both your mobile device that stores the passkey and the device you are logging in on.
2. Select the WebAuthn/U2F Security Key authentication method on the Rublon Prompt and then select the iPhone, iPad, or Android device option.
3. Scan the QR code and open the URL.
4. Depending on your mobile device’s settings, you may also be asked for additional security control like scanning your fingerprint before you are logged in.
3. You will be successfully signed in to your application.
Enroll a Hardware-Bound Passkey
The following example illustrates creating a YubiKey-bound passkey and enrolling it with Rublon MFA. You can use any other FIDO2-compliant security key.
1. Ensure you have completed all steps from the Initial Passkey Enrollments Steps section.
2. Choose to save the passkey on your security key. If another device has been chosen automatically, select Change to show more options.
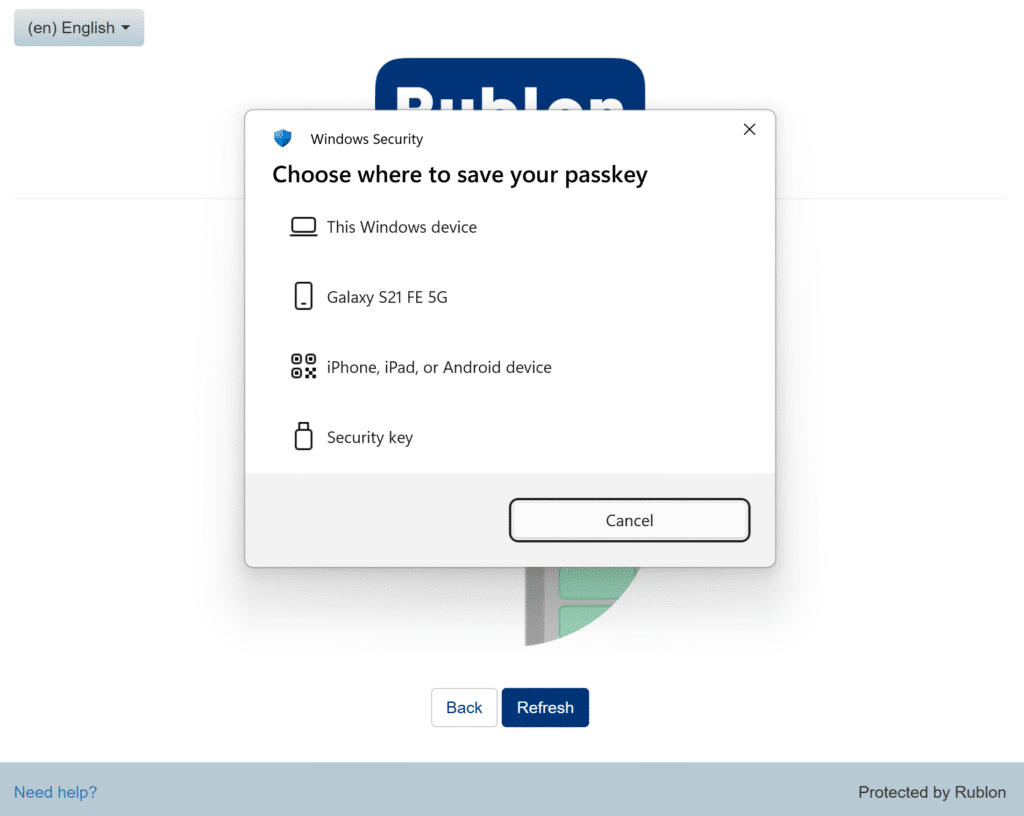
Note
Rublon MFA also supports Windows Hello passkeys. To save the passkey on the current Windows device using Windows Hello, select This Windows device on the Choose where to save your passkey prompt and scan your fingerprint or enter your PIN.
3. Insert and touch your security key.
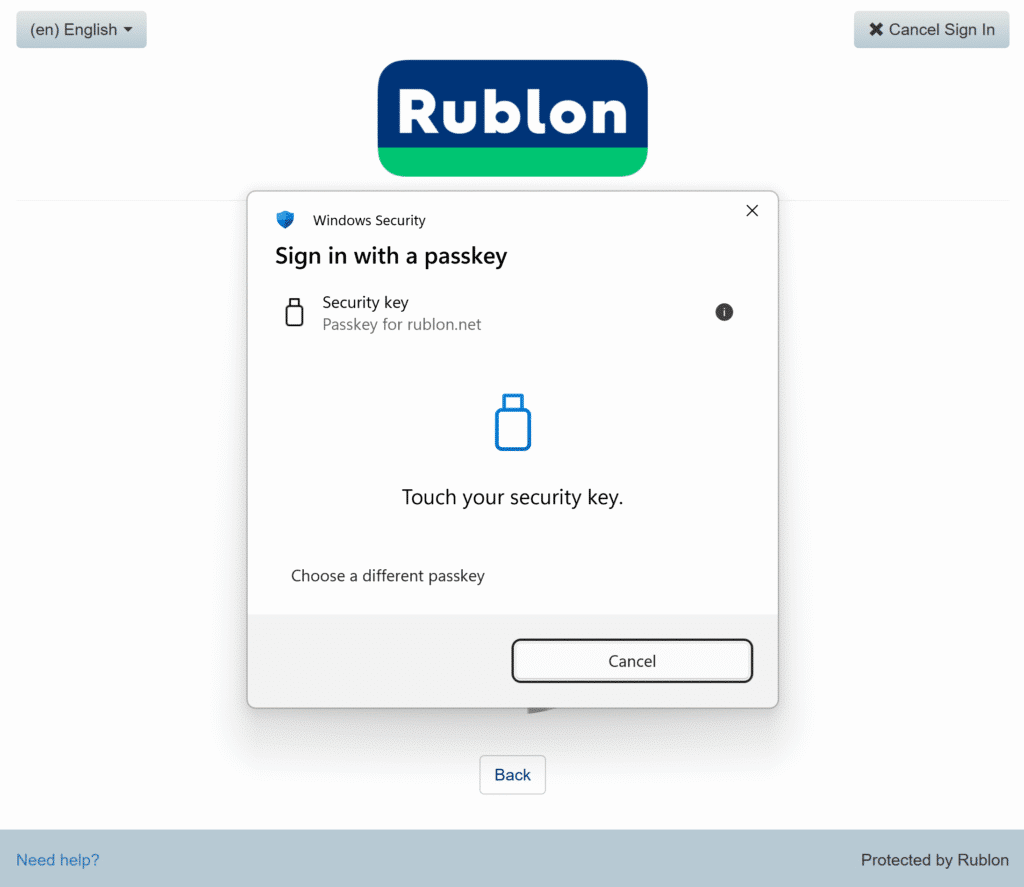
4. Enter a name for your passkey and click Save.
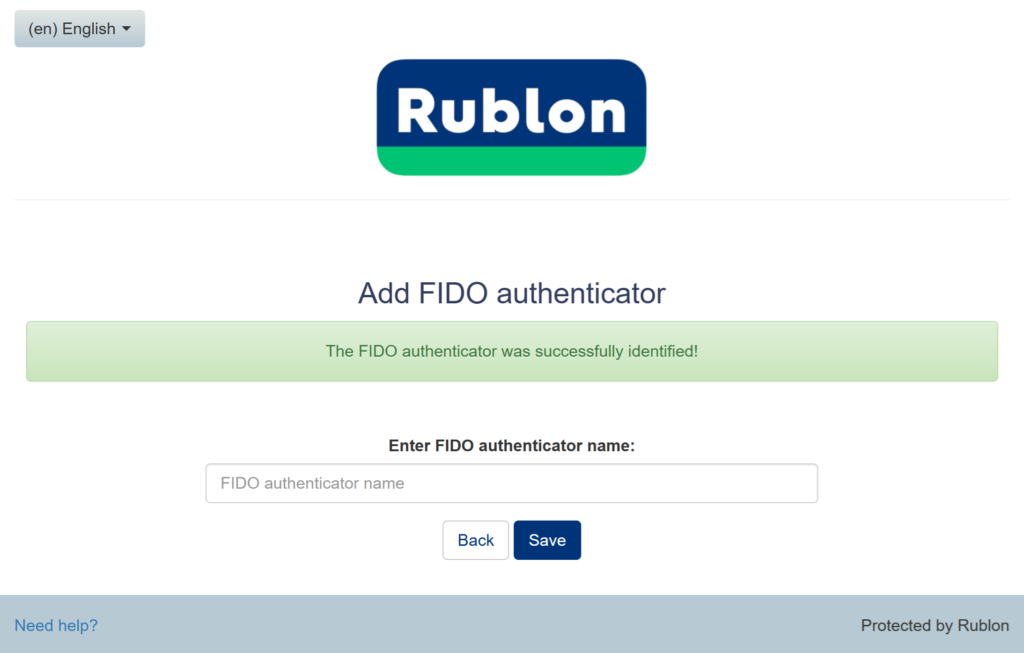
5. You will be redirected to the Rublon Prompt. You can now sign in using your passkey.
Sign in Using a Hardware-Bound Passkey
1. To sign in using your hardware-bound passkey, choose the WebAuthn/U2F Security Key authentication method from the Rublon Prompt.

A window will open, asking you to choose a device with a saved passkey. Choose Security key.
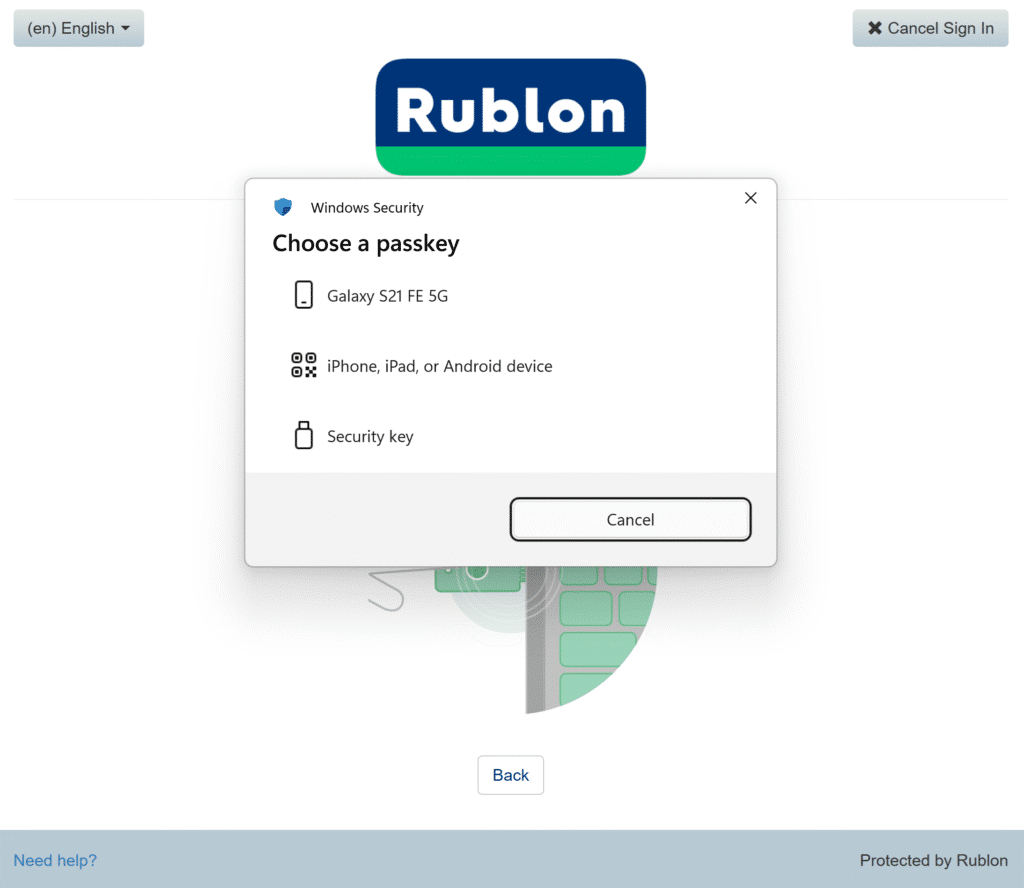
3. Plug in your key if you have not already, and then touch your FIDO2 security key.
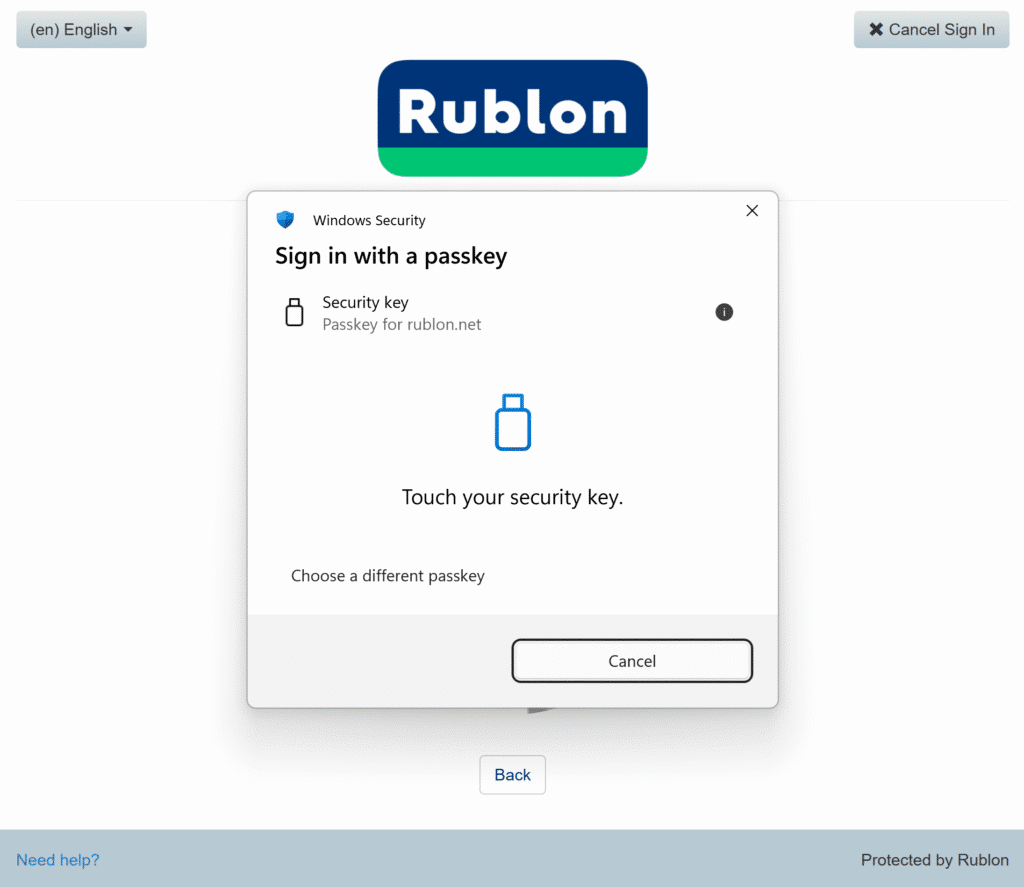
4. You will be successfully signed in to your application.
Related Posts
- Rublon User Guide
- How to enroll a mobile device with Rublon Authenticator?
- How to enroll a third-party authenticator app?
- How to add a WebAuthn/U2F Security Key?
- How to add a YubiKey OTP Security Key?
- How to add an RFID authenticator?
- How to add a mobile phone number?
- How to add a landline phone number?