Last updated on January 7, 2026
Rublon Secures Your RemoteApp
Terminal Services RemoteApp (TS RemoteApp) is a solution that allows users to launch virtual applications that run on a terminal server as if they were installed locally. RemoteApp makes remote applications look and feel like local applications. Administrators can easily set up the in-built RemoteApp and Desktop Connections and then allow users to access remote applications via the Start menu on their machines.
With the recent WannaCry and NotPetya outbreaks, we saw how quickly even a seemingly well-defended organization can fall victim to a sophisticated cyberattack. If you do not already have a Multi-Factor Authentication (MFA) solution in place, now is the perfect time to get one. MFA is an extra layer of security that helps thwart cybercriminals and keep your data safe. Remote Desktop Connection (RDP) has been a major attack vector in the past several years so it is of utmost importance to secure all remote connections with modern MFA.
Rublon seamlessly secures all Microsoft Windows-based devices, including desktops, laptops, tablets, and smartphones. Rublon supports all versions of Microsoft Windows and Microsoft Windows Server, including Windows 10, Windows 11, and Windows Server 2012-2022. Rublon offers a seamless MFA experience for RemoteApp, Windows Logon, RDP, RDG, and RD Web Access.
Secure Your RD Gateway and RDP Connections
Based on your infrastructure, configuration, and requirements, you might want to deploy Rublon MFA on either your RD Gateway or directly on all RDS Session Hosts that users will be connecting to via RDP. Both solutions have their pros and cons. If you are not sure which solution best fits your needs, please contact Rublon Support. We will be happy to advise.
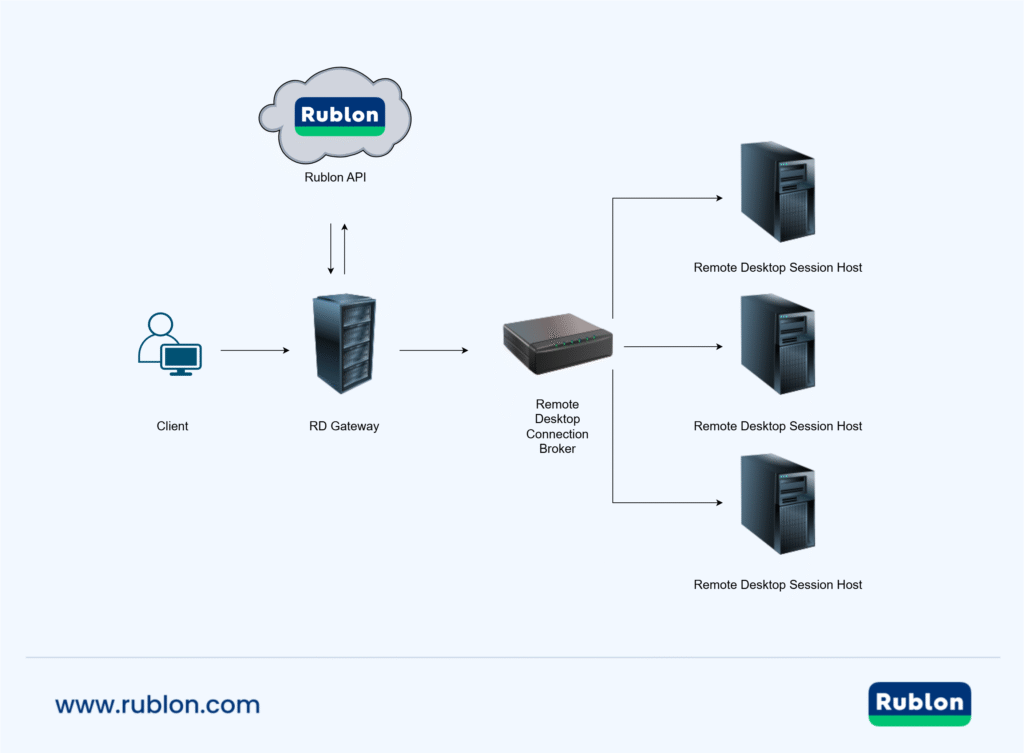
Protect Your RD Gateway
You can deploy Rublon on the RD Gateway level using our Rublon for RD Gateway connector. This process is short and easy. However, Rublon makes Resource Authorization Policies (RAP) and Remote Desktop Connection Authorization Policies (CAP) unreachable. If you want to keep these policies, deploy MFA on all your RDS Session Hosts instead.
Enable MFA for Remote Desktop Gateway
Protect Your RDS Session Hosts (RDP)
Since Rublon for RD Gateway makes RD Gateway policies unreachable, you can deploy Rublon on all your RDS Session Hosts instead by using Rublon’s Windows Logon & RDP connector. This way, you can keep the Resource Authorization Policies (RAP) and Remote Desktop Connection Authorization Policies (CAP) in RD Gateway. However, this choice entangles deploying Rublon on each RDS Session Host separately. You can do that manually or automatically via Intune, PDQ Deploy, or SCCM.
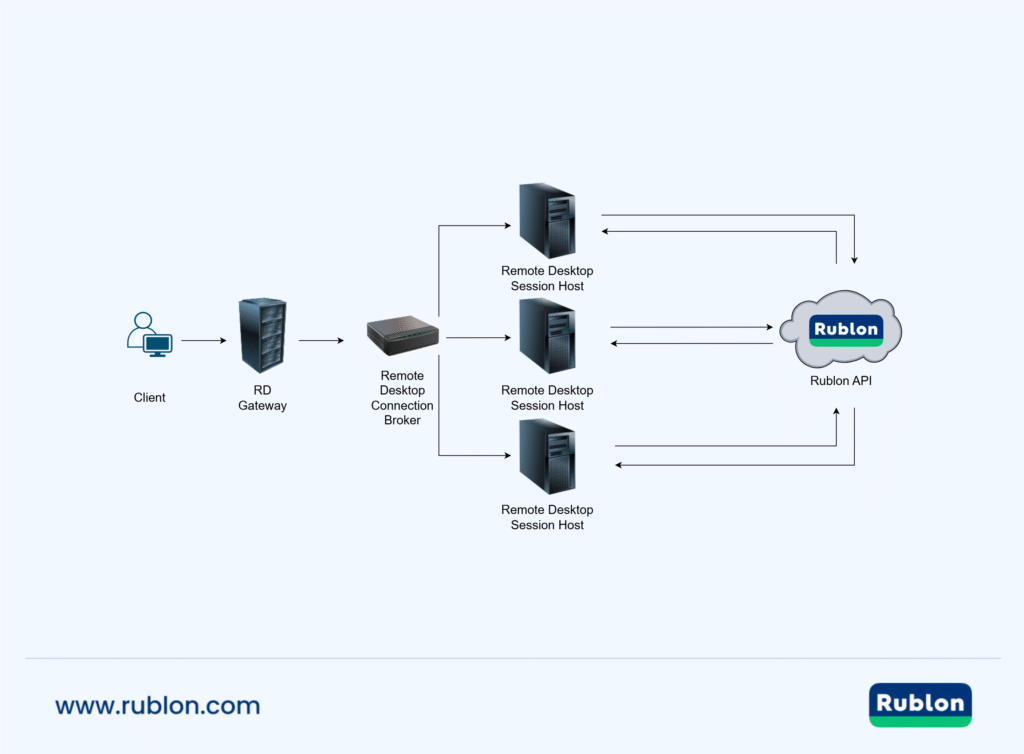
Enable MFA for RDS Session Hosts (RDP)
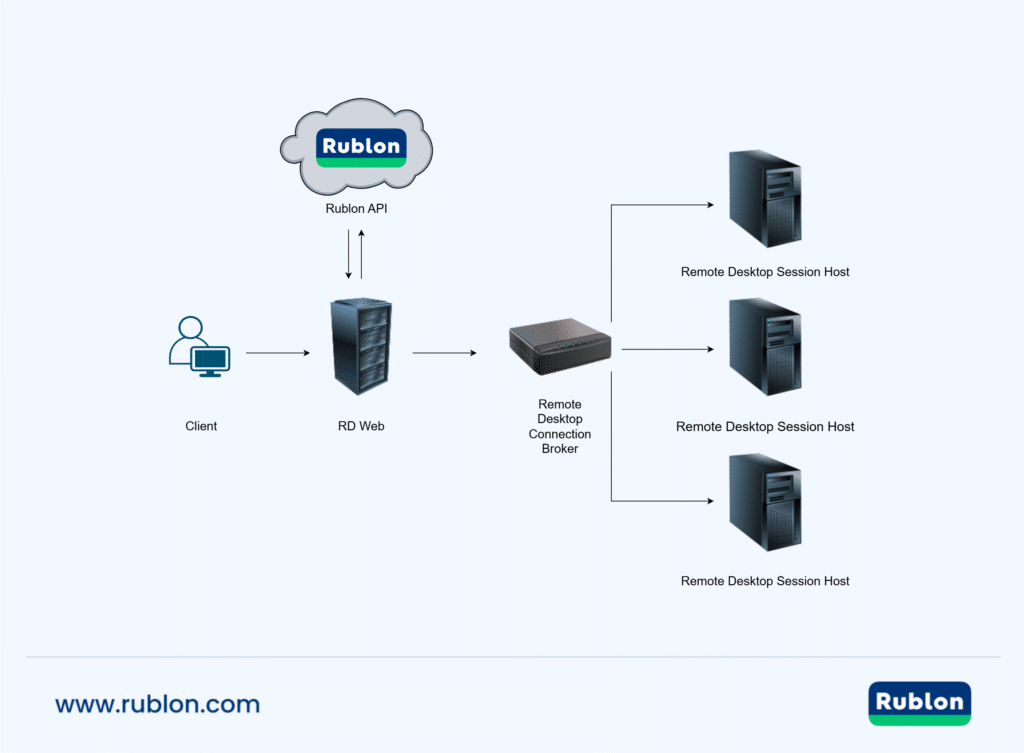
Secure Your RD Web Access
Protecting the actual user connections is crucial. However, before these users will be able to connect to their RemoteApps, they will first have to get a file that will allow them to start such connections.
To use RemoteApp, users must first get a file that contains the settings required to run a Remote Desktop Connection. A common way of getting such a file involves logging in to RD Web Access and downloading the file that has been previously published to RD Web Access. Users access RD Web Access through their browsers and then provide their credentials before they are able to download the aforementioned file.
While in the preceding scenario, a user who once downloaded a file will most likely not log into Web Access anymore (unless they want to download other files), it makes sense to add an extra layer of security to RD Web Access logins. For one, it significantly mitigates the risk of unauthorized access, in which an unauthorized party gains access to all the files published to RD Web Access. Another dangerous consequence of unauthorized access to RD Web Access is that an unauthorized actor now knows the addresses of all your servers. Both of these situations mean that the malicious actor is one step closer to compromising the entire system and gains new means of tampering with the Remote Desktop Connection.
Rublon offers secure Multi-Factor Authentication (MFA) that stops malicious attacks meant to gain unauthorized access to RD Web Access. The Rublon for RD Web Access connector supports all authentication methods and gives users the capability of selecting their favorite or most secure method. Administrators can also create an access policy to enforce the use of a particular set of authentication methods. In a common out-of-the-box scenario, a user logging in to RD Web Access can choose one of the authentication methods on the Rublon Prompt, as the second factor during their authentication. However, administrators can automate the second step by enforcing the Default Authentication Method policy. When Default Authentication Method is enabled, users are automatically challenged for MFA via the method picked by the administrator. For example, they receive a Mobile Push authentication request on their mobile phones with the Rublon Authenticator app installed on them. Mobile Push is one of the most secure authentication methods, which makes the Auto Push scenario an oft-used one among our customers.
Enable MFA for RD Web Access
Related Posts
MFA for Remote Access Software
Rublon for Windows Logon and RDP – Documentation